Java Allocation and C2
Java object allocation and escape analysis play crucial roles in memory management and performance optimization within the Java Virtual Machine (JVM). This comprehensive overview covers topics such as object vs. scalar allocation, object allocation mechanisms, hotspot escape analysis, ideal and conn
3 views • 22 slides
2D Collision Detection in Game Development
Explore the intricacies of 2D collision detection in game development through methods like distance checks, bounding shapes, and optimizing collision tests. Dive into concepts like sprite speed assumptions, square-square collisions, and rectangle testing complexities. Learn about useful Rectangle me
5 views • 29 slides
Wall Object Elijah | Houseofmishka.co.uk
Discover the unique and emotional touch of Houseofmishka.co.uk Wall Object Elijah. Elevate your home decor with our handcrafted pieces.\n\n\/\/houseofmishka.co.uk\/product\/wall-object-elijah\/
3 views • 1 slides
Object-Based Programming in Python: Exploring Classes and Constructors
Understanding object-based programming in Python involves creating classes with attributes and methods to build objects. By utilizing class constructors, you can initialize objects with specific values, allowing for unique instances with distinct characteristics. This tutorial covers the fundamental
2 views • 16 slides
Data Modeling vs Object Modeling
Data modeling involves exploring data-oriented structures, identifying entity types, and assigning attributes similar to class modeling in object-oriented development. Object models should not be solely based on existing data schemas due to impedance mismatches between object and relational paradigm
0 views • 17 slides
Spectrum Sensing for Enhanced Channel Access in Wireless Networks
This document presents a proposal for Spectrum Sensing Based Deferral (SSBD) to improve channel access in wireless networks. SSBD incorporates spectrum sensing with transmission deferral in a time-bound manner to enhance performance, reliability, and latency control. The proposed solution safeguards
4 views • 11 slides
Object Behaviors and Statechart Diagrams in Software Design
Object behaviors and UML statechart diagrams play a crucial role in software requirements and design. State machines, transitions, events, and states are essential concepts in modeling object behavior in response to external events. By utilizing UML statechart diagrams, one can effectively represent
0 views • 23 slides
Advanced Emergency Braking System (AEBS) Definition and Activation Guidelines
The provided content outlines the definition and activation requirements of the Advanced Emergency Braking System (AEBS). It covers the phases involved, including Collision Warning and Emergency Braking, as well as the speed limitations for activation. The system aims to automatically detect potenti
0 views • 12 slides
Object Modeling in Software Development
Object modeling is a crucial concept in software development, capturing the static structure of a system by depicting objects, their relationships, attributes, and operations. This modeling method aids in demonstrating systems to stakeholders and promotes a deeper understanding of real-world entitie
1 views • 65 slides
Object-Oriented Design Principles
Explore the core concepts of object-oriented design, including objects, classes, and the object-oriented paradigm. Learn about the relationship between objects and classes, and how they form the building blocks of software development. Gain insights into class components, attributes, and methods, an
0 views • 18 slides
Momentum and Impulse in Physics
Explore the concepts of momentum and impulse in physics, including the definition of momentum, the impulse-momentum theorem, and how factors affect object motion post-collision. Discover how momentum plays a vital role in describing an object's motion and learn about the relationship between force,
0 views • 30 slides
Configuration Examples for IP SLA with Object Tracking
Learn how to configure and troubleshoot IP SLA with Object Tracking using detailed examples for Static Routing, HSRP, and Policy Based Routing. Find out where Object Tracking can be implemented and when not to use it in various network scenarios. Understand the configuration components, including de
2 views • 17 slides
Physics Collision Problems Explained
Explore various collision scenarios involving bullets, blocks, cars, and people in this physics problem set. Calculate velocities, masses, and recoils to understand the dynamics of collisions and their effects on different objects involved.
0 views • 15 slides
Subject and Object Pronouns
Learn about subject and object pronouns, their usage in sentences, and examples to differentiate between them. Subject pronouns are used as the subject of a sentence, while object pronouns function as the object of a verb or preposition. Understand when to use pronouns like "I" or "me," "they" or "t
0 views • 13 slides
Direct Objects and Direct Object Pronouns in English and French
Explore the concepts of direct objects and direct object pronouns in English and French languages. Learn how direct objects are used in sentences, the role of direct object pronouns in avoiding repetition, and the differences in sentence structure when using object pronouns in French. Discover commo
1 views • 24 slides
Overview of Object-Oriented Design Patterns in Software Development
In the realm of software development, object-oriented design patterns play a crucial role in structuring code and solving recurring problems efficiently. These patterns, as outlined in various influential books and resources, provide a systematic approach to design, encompassing aspects like object
0 views • 26 slides
The Dynamics of Collision: Bug vs. Windshield
Explore the intriguing physics behind a bug hitting a windshield, delving into concepts like Newton's third law, momentum conservation, and the differences in force, time of impact, and change in velocity. Discover why a bug goes splat while a windshield remains intact in a collision scenario, with
0 views • 19 slides
The Difference Between Aggregation and Composition in Object-Oriented Programming
Aggregation and Composition are two important concepts in object-oriented programming. Aggregation refers to a 'has-a' relationship where the contained object can survive independently, while Composition indicates that the member object is part of the containing class and cannot exist separately. Th
0 views • 15 slides
Drone Collision Avoidance Simulator for Autonomous Maneuvering
Our project focuses on developing a drone collision avoidance simulator using NEAT and Deep Reinforcement Learning techniques. We aim to create a model that can maneuver obstacles in a 2D environment, enhancing performance and survivability. Previous attempts utilizing non-machine learning solutions
0 views • 28 slides
Metrics and Lessons Learned for Object-Oriented Projects
This chapter discusses various metrics and lessons learned for object-oriented projects, including the use of major OO metrics, Lorenz's metrics, IBM's Object Oriented Technology Council recommendations, and the CK metrics suite. The CK metrics suite covers six OO design and complexity measures, suc
0 views • 17 slides
Advanced Techniques in Collider Physics for Enhanced Luminosity
Explore cutting-edge research on beam-beam effects, crab waist colliders, and luminosity optimization in collider physics. Discover how innovative strategies like crab waist technology and bunch crabbing mitigation are revolutionizing particle collision studies. Dive into the complexities of achievi
0 views • 10 slides
Fundamentals of Object-Oriented Programming in Java
Object-Oriented Programming (OOP) is a methodology that simplifies software development by using classes and objects. This paradigm includes concepts like Object, Class, Inheritance, Polymorphism, Abstraction, and Encapsulation. Other terms used in OOP design include Coupling, Cohesion, Association,
0 views • 54 slides
The Relationship between Decisional Second-Preimage Resistance and Preimage Resistance in Cryptographic Hash Functions
This work delves into the subtle question of when Decisional Second-Preimage Resistance (SPR) implies Preimage Resistance (PRE) in hash functions. It presents a tool for enabling tight security proofs for hash-based signatures by exploring the success probability of adversaries against collision res
0 views • 25 slides
Foundations of Cryptography: Digital Signatures and Collision-Resistant Hash Functions
Foundations of Cryptography explores the construction of digital signature schemes and collision-resistant hash function families using one-way functions and safe primes. The content delves into the concept of collision-resistant hash functions and their construction from the discrete logarithm prob
0 views • 31 slides
Foundations of Cryptography: Lecture 12 - Digital Signatures and Collision-Resistant Hash Functions
The lecture covers the construction of collision-resistant hash functions from discrete log, the security behind it, and the implications for digital signature schemes. It delves into the theoretical foundations of cryptography, showcasing the interplay between one-way functions, hash functions, and
0 views • 25 slides
Shy Robot Programming Challenge: Logic-Based Autonomous Robot
The Shy Robot is an autonomous robot equipped with two IR sensors to avoid obstacles. Its behavior is determined by a logical control system - moving backward if both sensors detect an object, turning right if only the left sensor detects an object, turning left if only the right sensor detects an o
0 views • 5 slides
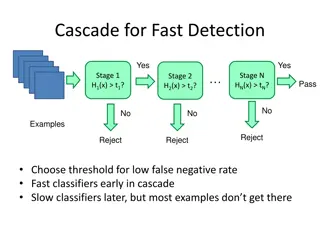
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
Introduction to Object Orientation and OOP Principles
Understanding the basics of Object-Oriented Programming (OOP) is crucial in modern software development. The agenda covers revision, the need for object orientation, principles, classes, and objects. Questions and assignments provide practical scenarios to apply OOP concepts effectively.
0 views • 20 slides
Comprehensive Overview of CSE 373 Data Structures and Algorithms Course - Autumn 2018
This document provides detailed information about the CSE 373 Data Structures and Algorithms course in Autumn 2018, presented by Shrirang (Shri) Mare. It covers topics such as hashing, collision strategies, hash tables, design decisions, testing, and more. The content includes announcements, midterm
0 views • 25 slides
Privacy Address Requirements for Wireless Personal Area Networks
This document discusses the privacy address requirements for IEEE P802.15 Working Group's TG4ab standard for Wireless Personal Area Networks (WPANs). It covers the need for 48-bit addresses with collision resistance, the use of different privacy addresses for each frame, and the adequacy of 12-bit c
0 views • 8 slides
TCAS - Traffic Collision Avoidance System
A Traffic Collision Avoidance System (TCAS) is a vital aircraft collision avoidance technology that helps reduce mid-air collisions by monitoring the airspace around an aircraft. TCAS operates independently of ground-based equipment and advises pilots on potential conflicting aircraft. Mandated by t
0 views • 13 slides
Vehicle Safety Protocols: Handling Tire Blows, Brake Failure, and More
Learn essential actions for handling emergencies like tire blowouts, brake failure, stuck accelerator, and steering failure. Additionally, understand off-road recovery, minimizing damage due to potholes, and escaping from a sinking vehicle. Discover collision avoidance techniques and steps to take i
0 views • 9 slides
Start Time Sync Procedures in IEEE 802.11-21/1679r0
In the document authored by Ronny Yongho Kim et al., the focus is on start time sync PPDU medium access considering internal collision in IEEE 802.11-21/1679r0. It discusses the importance of defining a clear rule to resolve internal collision cases during medium access procedures. Specific attentio
0 views • 9 slides
Fabric Interfaces Architecture Overview
This detailed content delves into the fabric interfaces architecture presented by Sean Hefty at Intel Corporation. It covers changes in version 2, object models, architectural semantics, conceptual object hierarchy, object relationships, fabric representation, passive fabric endpoint functionalities
0 views • 39 slides
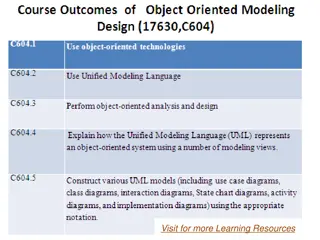
Object-Oriented Systems Analysis and Design (OOSAD) Using Unified Modeling Language (UML)
Explore the fundamentals of object-oriented analysis and design using UML, a powerful tool for constructing and visualizing systems. Learn about object-oriented concepts, classes, inheritance, UML diagrams, use case modeling, activity and sequence diagrams, and more. Discover how UML can enhance the
0 views • 144 slides
Momentum in Physics
Momentum, first introduced by Isaac Newton, is symbolized by the letter p and signifies inertia in motion. It is calculated as mass multiplied by velocity (p = m * v) and has the unit of kg * m/s. The amount of momentum depends on the object's mass and speed. A moving object has more momentum if eit
0 views • 18 slides
Hash Tables and Hashing Concepts in Computer Algorithms
This content delves into the concept of Hash Tables, covering topics such as the support for dictionary operations, achieving constant time through direct address tables, case studies in web server maintenance, and an exploration of hashing functions and collision avoidance. It also touches upon key
0 views • 40 slides
Object Properties and Hierarchy in Excel VBA
Exploring how to activate, manipulate, and work with different Excel object collections such as Workbooks, Worksheets, and Charts in VBA. Learn to navigate object hierarchies, access specific objects, and manage object properties to enhance your Excel macro development skills.
0 views • 16 slides
MitM Attack by Name Collision: Implications and Vulnerability Assessment
In this research study, the authors delve into the risks and vulnerabilities associated with Man-in-the-Middle (MitM) attacks exploiting name collision in the era of new generic Top-Level Domains (gTLDs). The study highlights how attackers can intercept web traffic by manipulating vulnerable domains
0 views • 25 slides
Proposal for IEEE 802.11-24/1172r0 CSD Indication Design
In this proposal authored by Bo Gong, Jian Yu (Ross), and Ming Gan from Huawei, the focus is on the allocation of CSDs by the AP in wireless communications. The document discusses the advantages of this approach, simulation results showing the impact of CSD collision, and the proposed method for CSD
0 views • 11 slides