Approaches in Studying Human-Environment Relationship
Explore different approaches to understanding the dynamic relationship between humans and their environment, including deterministic, teleological, possibilistic, and economic deterministic perspectives. These approaches shed light on how human actions and interactions with the environment have evol
1 views • 9 slides
Establishing Safety Standards in Non-Movement Areas at Smith Reynolds Airport
This guide outlines the purpose, definitions, rules, and safety measures for operating vehicles in non-movement areas at Smith Reynolds Airport. It emphasizes standardized ground movement practices to ensure the safety of airport patrons, reduce the risk of injury, and maintain a high level of safet
1 views • 12 slides
Understanding Deterministic Finite Automata (DFA) in Regular Language Theory
An exploration of Deterministic Finite Automata (DFA) in the context of Regular Languages, covering their definition, functioning, application in recognizing input strings, and building a DFA for a specific language. The Chomsky Hierarchy and the significance of Regular Languages are also briefly di
0 views • 41 slides
Understanding Pushdown Automata and Language Acceptance
Pushdown Automata (PDA) provide a theoretical framework for recognizing context-free languages. In PDA, the acceptance of a language depends on reaching a final state or having an empty stack. This concept is illustrated through examples and the distinction between deterministic and non-deterministi
0 views • 10 slides
Understanding Non-Aqueous Solvents: Types and Classification
Inorganic non-aqueous solvents play a crucial role in chemical research and industry. This article by Dr. Princy K.G. delves into the classification of solvents based on protonicity, polarity, and aqueous vs. non-aqueous nature. It explores the types of non-aqueous solvents, such as protonic and non
1 views • 29 slides
Understanding Deterministic Turing Machines
Detailed explanation of Deterministic Turing Machines, their constituents, formal definition, determinism, and special statuses such as Start, Accept, Reject, and Loop. Includes visual representations and key concepts of deterministic Turing machines.
0 views • 14 slides
Carl Rogers and the Self-Concept Theory
Carl Rogers, a prominent figure in personality theory, emphasized individuals' constructive potential and the impact of their subjective experiences on personality development. He viewed individuals as goal-directed and capable of change, with the environment playing a facilitating or inhibiting rol
1 views • 78 slides
Understanding Non-Firm Quantities in Electricity Markets
Non-Firm Quantities in electricity markets involve units with non-firm access not being compensated for their non-firm capacity not getting accommodated on the system. The concept of Firm Access Quantity plays a key role in determining compensation levels for units, with differences in implementatio
0 views • 6 slides
Understanding Non-Compete Agreements: Enforceability and Requirements
Non-compete agreements are commonly used in the United States to protect businesses from competition by former employees. To be enforceable, these agreements must meet certain requirements, including independent consideration, protection of legitimate business interests, and reasonableness in scope,
0 views • 26 slides
Comparison of Trigger-based vs. Non-Trigger-based Sensing Measurement in IEEE 802.11
The document discusses the differences between Trigger-based (TB) and Non-Trigger-based (Non-TB) sensing measurement instances in IEEE 802.11 standards, focusing on who initiates the sensing measurement. TB sensing is initiated by the AP, while Non-TB sensing is initiated by a non-AP STA, enabling o
6 views • 13 slides
Understanding Naive Bayes Classifier in Data Science
Naive Bayes classifier is a probabilistic framework used in data science for classification problems. It leverages Bayes' Theorem to model probabilistic relationships between attributes and class variables. The classifier is particularly useful in scenarios where the relationship between attributes
1 views • 28 slides
Concurrent Revisions: A Deterministic Concurrency Model
Exploring a deterministic concurrency model proposed by Daan Leijen and Sebastian Burckhardt, focusing on concurrent programming, threads, locks, futures, promises, transactions, and the resolution of conflicts in parallel performance.
0 views • 36 slides
Overview of Computational Complexity Theory: Savitch's Theorem, PSPACE, and NL-Completeness
This lecture delves into Savitch's theorem, the complexity classes PSPACE and NL, and their completeness. It explores the relationship between time and space complexity, configuration graphs of Turing machines, and how non-deterministic space relates to deterministic time. The concept of configurati
0 views • 67 slides
Understanding Issues in Context-Free Grammar: Ambiguity, Precedence, Associativity, and More
Delve into the complexities of context-free grammar, exploring concepts such as ambiguity, precedence, associativity, left recursion, and left factoring. Learn about the challenges posed by left recursion and the differences between ambiguous and unambiguous, as well as deterministic and non-determi
0 views • 7 slides
Genetic Programming for User Interface Optimization at EICS 2017
Proposal by Paulo Salem at EICS 2017 introduces Genetic Programming for optimizing user interfaces, addressing limitations of existing solutions. The approach utilizes programmatic specifications, structured representations, and non-deterministic choices to evolve UIs efficiently.
0 views • 18 slides
Contemporary Challenges in Nuclear Disarmament and Non-Proliferation Regime
The international regime for nuclear disarmament and non-proliferation faces challenges from states within and outside the regime, as well as non-state actors. Various approaches are being utilized to address these challenges, including strengthening multilateral institutions, non-treaty-based multi
0 views • 12 slides
Enhancing Replay Interface Efficiency in System Debugging
Efforts by researchers at Microsoft Research Asia and MIT focus on enhancing replay interface efficiency for system debugging. The motivation stems from the non-determinism challenges caused by time, user input, network I/O, and thread interleaving. The study observes that only certain parts of a pr
0 views • 26 slides
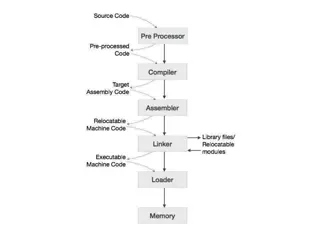
Compiler Data Structures and NFA to DFA Conversion
Compiler data structures play a crucial role in the compilation process, handling lexical analysis to code generation. Understanding the conversion from non-deterministic finite automata (NFA) to deterministic finite automata (DFA) is essential for efficient language processing and optimization.
0 views • 10 slides
Understanding P vs. NP: A Comprehensive Overview
Delve into the complexities of computational problem-solving with insights on P, NP, NP-complete, determinism, and non-determinism. Explore the distinctions between deterministic and non-deterministic algorithms and the implications they have on problem-solving capabilities. Gain a deeper understand
0 views • 22 slides
Improving Attainment and Progress of Disadvantaged Pupils in Sheffield
Attainment and progress of disadvantaged pupils in Sheffield show an improving trend across key stages, although the gaps between disadvantaged and non-disadvantaged students are not closing fast enough. Data suggests that disadvantaged pupils with low prior attainment are making better progress in
0 views • 29 slides
Understanding Non-Profit Accounting Essentials
Learn the basics of non-profit accounting, including what defines a non-profit organization, common types of non-profits, governance structures, and legal responsibilities. Discover key insights on IRS and state requirements for non-profits in this informative presentation by Jessica Sayles, CPA fro
0 views • 55 slides
Further Discussion on Non-primary Channel Access in IEEE 802.11
This contribution delves into the utilization of non-primary channels for access in IEEE 802.11 networks, focusing on enhancing frequency reuse, adhering to ETSI standards, evaluating CCA capability types, and analyzing non-ideal deployment scenarios. It discusses the complexity and benefits of non-
0 views • 26 slides
IEEE 802.11-18/1951r0 ETSI CAM Generation Rules
ETSI EN 302.637.2 defines the structure and generation rules of Cooperative Awareness Messages (CAMs) for Intelligent Transportation Systems (ITS). CAMs are essential for a variety of ITS use cases and must be backward compatible in NGV systems. The CAM messages are non-deterministic in time and siz
0 views • 7 slides
Understanding Runtime Recovery of Web Applications under Zero-Day ReDoS Attacks
This detailed content discusses the critical issue of Runtime Recovery of Web Applications facing Zero-Day ReDoS Attacks. It delves into the significance of regular expressions (regex) in handling HTTP requests, highlighting vulnerabilities and real-world impacts. The research emphasizes the severit
0 views • 31 slides
Efficient Hardware Support for Disciplined Non-Determinism in Shared Memory Systems
DeNovoND presents a holistic approach to rethinking memory hierarchy, aiming to enhance hardware efficiency for disciplined non-determinism in shared memory systems. The work addresses limitations in deterministic programming, offering strong safety properties and simplified coherence and consistenc
0 views • 28 slides
Non-Negative Tensor Factorization with RESCAL
This article discusses non-negative tensor factorization with RESCAL, covering topics such as Non-Negative Matrix Factorization, Multiplicative Updates, RESCAL for Relational Learning, and Non-Negative Constraint for RESCAL. It explores how factorizing matrices/tensors into non-negative factors can
0 views • 11 slides
Introduction to High-Level Petri Nets for Software Engineering
High-Level Petri Nets, an extension of classical Petri nets, offer a structured approach to system modeling with attributes, time considerations, and hierarchy. Sebastian Coope, a lecturer at Liverpool University, explores the practical applications and advantages of Petri Nets in software engineeri
0 views • 49 slides
Systematic Testing of Reactive Software - A Case Study on LG Electric Oven
Overview of a case study conducted on LG Electric Oven using systematic testing of reactive software with non-deterministic events. The study focused on detecting concurrency bugs in the software controller of the oven through an automated testing framework that generates event timing sequences. It
0 views • 32 slides
Understanding Cross-Device Tracking for Better Engagement
Delve into the world of cross-device tracking with insights on probabilistic vs. deterministic matching models, limitations of third-party cookies, reasons to engage in cross-device tracking, and the distinctions between probabilistic and deterministic matching methods. Explore how tracking across m
0 views • 41 slides
Time Distribution System R&D Update for Hyper-Kamiokande Experiment
In the February 2020 update, Stefano Russo from LPNHE Paris presented the progress on the time distribution system R&D for the Hyper-Kamiokande experiment. The focus is on implementing a bidirectional data exchange link with a large bandwidth capacity for synchronous, phase-deterministic protocol. T
0 views • 17 slides
Understanding Pushdown Automata (PDA) in Computer Science
Pushdown Automata (PDA) are essential in theoretical computer science, serving as an extension of non-deterministic finite automata (NFA). PDAs incorporate a stack, enabling them to recognize non-regular languages. They are described by transitions involving input symbols, state changes, and stack m
0 views • 46 slides
Understanding P, NP, NP-Hard, NP-Complete Problems and Amortized Analysis
This comprehensive study covers P, NP, NP-Hard, NP-Complete Problems, and Amortized Analysis, including examples and concepts like Reduction, Vertex Cover, Max-Clique, 3-SAT, and Hamiltonian Cycle. It delves into Polynomial versus Non-Polynomial problems, outlining the difficulties and unsolvability
0 views • 32 slides
Concurrent Revisions: A Model for Deterministic Concurrency
This content discusses a deterministic concurrency model called Concurrent Revisions, focusing on interactive applications with large shared data structures. It covers the challenges of conflicting tasks, conventional concurrency control methods, and proposes a programming model based on revisions a
0 views • 41 slides
Overview of Nested Data Parallelism in Haskell
The paper by Simon Peyton Jones, Manuel Chakravarty, Gabriele Keller, and Roman Leshchinskiy explores nested data parallelism in Haskell, focusing on harnessing multicore processors. It discusses the challenges of parallel programming, comparing sequential and parallel computational fabrics. The evo
0 views • 55 slides
Quantum Mechanics and Geometric Interpretations in Weyl Space
The discussion explores Weyl quantum mechanics, Bohm's interpretation of quantum potential, and geometric formulations in Euclidean-Weyl space. It delves into the implications of nonlocal quantum potentials and the nature of metric spaces in shaping quantum phenomena. Concluding with alternative vie
0 views • 30 slides
Concurrency and Memory Sharing in Java Programming
Understanding concurrency and memory sharing in Java programming is crucial for managing shared resources efficiently. This includes concepts like ForkJoin, shared queues, and synchronized situations in examples like bank accounts. Proper synchronization is essential to prevent simultaneous access i
0 views • 59 slides
Ensuring Orthogonal Security in Data Encryption Processes
Addressing the challenge of data confidentiality in untrusted server environments through the use of encryption techniques such as deterministic and non-deterministic encryption. The goal is to achieve full functionality independently of data encryption, allowing for secure processing of data querie
0 views • 21 slides
Shadow: Scalable and Deterministic Network Experimentation in Cybersecurity
The presentation discusses the concept of deterministic experimentation in cybersecurity, emphasizing the importance of experimental control and scalability in large distributed systems like Tor. It introduces Shadow, a network simulator designed to achieve repeatable and realistic experiments for r
0 views • 15 slides
Understanding Prolog: A Declarative Approach through the Years
Delve into the evolution of Prolog over the past 50 years, from its origins in natural language processing to its implementation and various features like tabling and negation. Explore the foundational concepts, syntax, and execution of Prolog, including its non-deterministic nature and recursive de
1 views • 21 slides
Understanding Memoryless Determinacy of Parity Games
Explore the intricacies of memoryless determinacy in parity games through a comprehensive walkthrough of concepts such as complexity results, sub-games, attractors, and the determinacy theorem. Learn about the partitioning of vertices into 0-paradise and 1-paradise, alongside insights on non-determi
0 views • 42 slides