Information Security – Theory vs. Reality
Exploring the concept of fault attacks in hardware security, this lecture delves into the various techniques used to compromise systems through non-nominal and nominal channels, as well as the potential risks introduced by trojan horses in the IT supply chain. The discussion includes differential fa
1 views • 37 slides
Revisiting LDPC Rate Matching in IEEE 802.11 for Improved Performance
The document discusses revisiting LDPC rate matching in IEEE 802.11, focusing on issues such as performance loss compared to previous standards, power consumption in LDPC decoding/encoding, and over puncturing. It covers preliminary concepts, packet size distribution in various devices like laptops
2 views • 17 slides
Virtualized Evolved Packet Core Market
Explore $19.87 billion Virtualized Evolved Packet Core Market: Get exclusive insights on key market trends, segments, geographical analysis, & competitive analysis!\nDownload Sample Report Here @ \/\/ \/download-sample-report\/cp_id=5201
3 views • 6 slides
Virtualized Evolved Packet Core Market Projected to Reach $19.87 Billion by 2031
Explore $19.87 billion Virtualized Evolved Packet Core Market: Get exclusive insights on key market trends, segments, geographical analysis, & competitive analysis!\n
1 views • 4 slides
Introduction to IEEE 802.11-20 EHT PPE Thresholds Field
IEEE 802.11-20 standard defines the Nominal Packet Padding values and Pre-FEC Padding Factors for PE fields in 11ax. The selection of Nominal Packet Padding values is crucial and can be determined using specific methods, including PPE Thresholds Present subfield. The PPE Thresholds field contains in
0 views • 14 slides
Understanding IMIX in Networking and Testing Tools
IMIX, or Internet Mix, refers to a mixture of packet sizes used to simulate real-world network conditions for testing networking devices. Various tools and methods, such as Genome Reporting, Moongen, T-Rex, and Spirent TestCenter, implement IMIX with specific packet size distributions and characteri
0 views • 8 slides
Insights on Global Governance and Multistakeholderism for Activists
This educational packet provides valuable insights for activists focused on understanding the governance context surrounding UN organizations. It discusses the impact of multistakeholderism on global governance, challenges to multilateralism, and the need for a more equitable system. The packet incl
0 views • 11 slides
Enhancing Network Performance with RoCE Technology
Remote Direct Memory Access (RDMA) benefits, RoCEv2 packet format, resilient RoCE feature progression, optimizing network performance with QoS, and RoCE congestion control convergence analysis are discussed in this proposal. RoCE technology offers low latency, high throughput, and efficient CPU usag
0 views • 19 slides
IEEE 802.11-19/1575r0 Multi-Link BA Operation Overview
Presentation slides from September 2019 discussing the Multi-Link Operation (MLO) in IEEE 802.11-19/1575r0 standard. The slides cover topics such as the benefits of MLO, synchronized/asynchronized rules, terminology, architecture, and common BA sessions. The proposal aims to define an architecture s
0 views • 25 slides
Understanding Sound Card Digital Operation on Winlink Express
Explore the capabilities of utilizing a sound card interface for digital operations on Winlink Express, offering flexibility and performance for various modes, including Packet, ARDOP, Vara HF, and Vara FM. Learn about the benefits of sound card interfaces, sound card operation, and the modes suppor
0 views • 39 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Explore Cisco Packet Tracer for Network Simulation
Discover Cisco Packet Tracer, a powerful network simulation program used for hands-on LAN configuration and managing large-scale distributed systems. Learn about its availability to Networking Academy users and how to download the software for free through Academy Connection.
0 views • 8 slides
Understanding Singular Value Decomposition (SVD) in Linear Algebra
Singular Value Decomposition (SVD) is a powerful technique in linear algebra that breaks down any matrix into orthogonal stretching followed by rotation. It reveals insights into transformations, basis vectors, eigenvalues, and eigenvectors, aiding in understanding linear transformations in a geomet
3 views • 18 slides
Protecting User Privacy in Web-Based Applications through Traffic Padding
Explore a novel approach utilizing knowledge-resistant traffic padding to safeguard user privacy in web-based applications. The study addresses side-channel attacks on encrypted traffic, the challenges of maintaining security in untrusted internet environments, and the potential privacy overhead of
0 views • 31 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
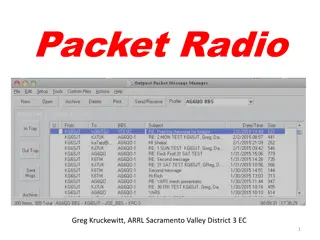
Understanding Packet Radio: A Comprehensive Guide
Packet radio, utilizing VHF FM technology, is a digital mode allowing keyboard-to-keyboard communication, messaging, mailboxes, bulletins, and more. It uses the AX.25 protocol and operates at varying data rates on VHF and HF bands. The system comprises basic stations and automated nodes, each requir
0 views • 20 slides
Understanding Cryptography: Basics of Encryption and Padding
Cryptography is essential for secure communication between parties, ensuring confidentiality and integrity of data. This overview covers basic math concepts, block ciphers, encryption modes like ECB and CBC, and the importance of padding in securing plaintext data.
0 views • 21 slides
Understanding Internet Architecture and Networking Principles
The content explores the architecture and goals of the Internet, focusing on its original objectives, survivability in the face of failure, and evolving requirements. It delves into how networks function, describing behaviors and packet handling. Additionally, it discusses the framework for describi
0 views • 15 slides
Understanding CSS Basics and Best Practices
Exploring the fundamentals of CSS including the Box Model, Border, Margin, Padding, Inline styling, Classes, IDs, and more. Dive into the world of Cascading Style Sheets and learn about their relationship with HTML, supported media types, and limitations on various browsers. The slides cover a range
0 views • 41 slides
Understanding the Impact of 1% Packet Loss on TCP and the Cubic Congestion Avoidance Algorithm
Delve into the surprising effects of even 1% packet loss on network flows, the methods TCP uses to mitigate loss, and how the CUBIC congestion avoidance algorithm works. Explore the researched but not quantified problem of packet loss and learn about a test methodology using Ubuntu hosts to measure
0 views • 24 slides
FY25 Title III Consortium Packet Overview
FY25 Title III Consortium Packet provides information on English Language Proficiency allocations, consortium formation, grant management, board approval requirements, and responsibilities of the lead fiscal agent. English Learner counts determine funding eligibility, with consortiums formed to reac
0 views • 15 slides
Understanding Hammer Toe: Causes, Symptoms, Diagnosis, and Management
Hammer toe is a flexion deformity of a toe that can cause discomfort and pain, often worsened by ill-fitting footwear or weight-bearing activity. The condition can be caused by factors like bunions, trauma, or toe joint instability. Symptoms may include pain at the joint of the affected toe and seco
0 views • 12 slides
Understanding Exchange Rate Behavior with Negative Interest Rates: Early Observations by Andrew K. Rose
In this study, Andrew K. Rose examines the exchange rate behavior in economies with negative nominal interest rates, focusing on the impact and implications of such rates on exchange rates. The findings suggest limited observable consequences on exchange rate behavior, with similarities in shocks dr
0 views • 42 slides
Bandwidth and Packet Type Detection Schemes for 40-50GHz Millimeter Wave Communication Systems
The document discusses bandwidth and packet type detection schemes for 40-50GHz millimeter wave communication systems in IEEE 802.11aj specifications. It proposes a preamble design for auto-detection of bandwidth and packet type to improve channel estimation and decoding efficiency. By utilizing dif
0 views • 27 slides
Enhancing Power Save Mechanisms in IEEE 802.11 for Non-AP STAs
The document discusses improving power save mechanisms for non-AP STAs in IEEE 802.11 by focusing on reducing power consumption during listen mode, enhancing flexibility in transitions between power states, and proposing solutions to enable reception on smaller bandwidths. It emphasizes the importan
0 views • 11 slides
English Grammar Final Exam Review
Subordinate clauses, nominal phrases, and noun clauses are identified within the context of adjectival, adverbial, or nominal functions. The exercise covers recognizing nominal clauses following prepositions as noun phrases, pronouns, gerunds, or nominal clauses. Additionally, combining sentences us
0 views • 17 slides
Enhancing Network Security Through Multi-Core Packet Scattering and Deep Packet Inspection
Explore the use of multi-core systems to tackle performance bottlenecks in network intrusion detection systems, specifically focusing on deep packet inspection. Techniques such as load balancing and pattern subset scanning are discussed to optimize DPI processes and improve overall network security
0 views • 43 slides
Exploring the Evolution of Data Communications: A Brief Overview
Delve into the progression of data communications from Morse code to modern radio email systems like Winlink. Discover the history of protocols, technologies, and the impact of the internet on amateur packet radio. Unravel the development of ARQ data protocols, X.25 packet switching, and the transit
0 views • 51 slides
Understanding Slavic Nominal Case Morphology & Stems
Uncover the intricacies of consonant-stem nominal case morphology in Slavic languages, from the introduction to the case system to the classification of consonant stems into major groups such as *u-stems, *n-stems, *s-stems, *nt-stems, and *r-stems. Explore the unique characteristics of *-stems, *o-
0 views • 11 slides
Improving Padding Efficiency in HE SU PPDU with BCC
IEEE 802.11-16/0080r2 proposes a method to enhance padding efficiency in High Efficiency Spatially Multiplexed (HE SU) PPDU with Block Concatenation Coding (BCC) in 20MHz transmission. By adjusting the duration of the last OFDM symbol based on the excess information bits, this method aims to reduce
0 views • 17 slides
Impact of Negative Nominal Interest Rates on Bank Performance: Cross-Country Insights
Examining the effects of negative nominal interest rates on bank performance reveals challenges in maintaining profitability, with concerns around reduced interest rate margins and disruptions to monetary transmission mechanisms. Empirical evidence suggests a reluctance among banks to impose negativ
0 views • 43 slides
IEEE 802.11-20/1317r1 EHT-SIG Proposal Discussion
The document discusses EHT-SIG for single-user and sounding NDP in IEEE 802.11-20/1317r1, focusing on overflow bits, user fields, CRC, and tail formats. It covers the format details, subfields, and overhead compared to HE sounding, proposing specific bit allocations for different elements. The EHT-S
0 views • 16 slides
Impact of Negative Nominal Interest Rates on Bank Performance
Negative nominal interest rates, implemented following the financial crisis, have had a limited effect on bank performance globally. While low rates reduce profitability, banks have shown resilience through adjustments in funding allocations and non-interest income sources. Studies suggest that resp
0 views • 34 slides
Understanding the Basics of Packet Radio for Amateur Communication
Explore the world of packet radio, a digital mode used by amateur radio operators to build wireless computer networks. Learn about its benefits, how it works using the AX.25 protocol, making connections, advantages such as error checking, and building a packet station with the necessary components.
0 views • 19 slides
Understanding Asynchronous Transfer Mode (ATM) in Data and Computer Communications
Asynchronous Transfer Mode (ATM) is a packet transfer technology that supports multiple logical connections over a single physical interface. It uses fixed-sized packets called cells for data transfer. ATM bears similarities to packet switching and offers streamlined packet transfer with minimal err
0 views • 46 slides
Enhancing Data Center Network Performance through Packet Scheduling and ECN
Explore the advancements in data center network performance improvement through techniques like packet scheduling, Explicit Congestion Notification (ECN), and strict priority for different types of flows. The research discusses the requirements of low latency for short messages and high throughput f
0 views • 48 slides
Understanding Wireshark Filters for Efficient Packet Analysis
Learn how to leverage Wireshark capture filters to customize packet analysis, enhance traffic visibility, and optimize network monitoring. Capture only the data you need, create custom filters, and streamline intrusion detection analysis with Berkeley Packet Filters (BPF). Discover the power of disp
0 views • 17 slides
i-LEAD Results and Recommendations Overview
This document provides insights into the results and recommendations of the i-LEAD project led by Patrick Padding for the Netherlands Police and Polish Platform for Homeland Security. It discusses the role of ENLETS as an initiator of EU projects, the funding of i-LEAD by the European Union's Horizo
0 views • 10 slides
Considerations on PHY Padding and Packet Extension in 11ax
The document discusses the proposed PHY padding and packet extension for IEEE 802.11ax, focusing on considerations for processing data within SIFS duration and relaxation of LDPC decoding processing time. It outlines the overview of the proposed padding scheme, considerations for LDPC implementation
0 views • 15 slides
Innovative Application Packet for ACE Solutions - Explore the Visual Journey
Dive into the visually captivating world of ACE Solutions with their cutting-edge application packet. From stunning visuals to advanced functionality, this packet showcases the power and versatility of ACE Solutions for modern applications. Discover the seamless navigation, engaging content, and ric
0 views • 59 slides