Comprehensive Guidelines for Hypertension Management in Canada 2020
The Hypertension Canada's 2020 Comprehensive Guidelines provide insights on prevention, diagnosis, risk assessment, and treatment of hypertension in adults and children. The guidelines emphasize standardized blood pressure measurement, risk factors, and the use of out-of-office monitoring for accura
2 views • 62 slides
What Are SEMA Racking Inspection Guidelines?
SEMA racking inspection guidelines are the gold standard of the racking safety industry.\n\nWithout SEMA racking inspection guidelines, guaranteeing the safety of any warehouse would be impossible. The advice laid down by SEMA is often echoed by HSE and \u2014 in some cases \u2014 it becomes law. So
1 views • 2 slides
Ascon: The Lightweight Cryptography Standard for IoT
The November 2023 document IEEE 802.11-23/2069r2 discusses the importance of secure data storage and communication in IoT devices due to the increasing number of connected devices and potential security threats. It introduces Ascon as a lightweight cryptography standard selected by NIST for protecti
0 views • 26 slides
2023 CPG Obesity Guidelines: Application in Primary Care and Impact on Pediatric Health
Application of the 2023 CPG Obesity Guidelines in primary care is crucial due to the increased prevalence of obesity among children, with 19% affected in the US. This guideline update is necessary as the last guidelines were published in 2007 and there is now more data available, including RCTs and
5 views • 23 slides
Lightweight Cryptography Standard for IoT - November 2023 IEEE Presentation
IEEE 802.11-23/2069r1 presents Ascon as a lightweight cryptography standard for IoT devices. With the increasing number of connected devices, protecting data on IoT devices becomes crucial. NIST selects Ascon to safeguard small devices, offering authenticated encryption and hashing efficiently. Asco
3 views • 26 slides
DPI Auditor Insights and State Audit Guidelines Overview
This collection of images and descriptions provides insights into DPI Auditor activities, state audit guidelines, and updates related to state major program determinations. The State Single Audit Guidelines for Wisconsin School Districts are highlighted, along with the State Audit Manual overview an
3 views • 36 slides
Leica Social Media Guidelines Overview
The Leica Social Media Guidelines aim to create a consistent brand image across all social media channels globally, emphasizing key values such as recognition, voice share, and local content support. The guidelines cover the philosophy behind Leica, establishing a social media presence, channel over
2 views • 61 slides
Understanding AES Encryption Algorithm and Its Implementation
Learn about the Advanced Encryption Standard (AES) algorithm - a NSA-approved NIST standard encryption method. Explore how AES works, its key rounds, SubBytes, ShiftRows, MixColumns operations, and its optimization for embedded systems and small memory devices. Discover the importance of secure cryp
0 views • 14 slides
Overview of CMMC 2.0 Cybersecurity Maturity Model Certification
The CMMC 2.0 introduces a streamlined model with three levels, focusing on protecting controlled unclassified information (CUI) with requirements aligned with NIST standards. Assessments vary for each level, including self-assessments for Level 1 and third-party assessments for Level 2. Government o
3 views • 8 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Simulating Basic PNR and PA Systems: A Practical Approach
Explore how to effectively simulate basic Polarized Neutron Reflectometry (PNR) and Polarization Analysis (PA) systems to enhance proposal submissions and experiment success. Learn about the NIST PNR calculator, useful websites for calculations, and key elements in simulating data for analysis.
0 views • 16 slides
Best Practice Guidelines for Saskatchewan Health Authority PowerPoint Presentations
The Saskatchewan Health Authority has specific guidelines for creating PowerPoint presentations to ensure consistent branding. These guidelines include using the correct font, font size, color scheme, and layout. It also emphasizes the proper use of logos, images, and charts while maintaining a prof
1 views • 13 slides
Post-COVID-19 Operational Guide for PCR Inc.
The operational guide outlines safety protocols for PCR Inc. post-COVID-19, emphasizing a 50% capacity limit, presence of a certified food manager on-site, adherence to social distancing guidelines, frequent sanitation of high-touch surfaces, and mandatory mask-wearing. Employees are required to wea
2 views • 7 slides
High-Throughput True Random Number Generation Using QUAC-TRNG
DRAM-based QUAC-TRNG provides high-throughput and low-latency true random number generation by utilizing commodity DRAM devices. By employing Quadruple Row Activation (QUAC), this method outperforms existing TRNGs, achieving a 15.08x improvement in throughput and passing all 15 NIST randomness tests
0 views • 10 slides
Understanding Security Categorization of Information Systems
Explore the concept of security categorization for information and information systems, including its purpose, methodology, key references, and policy statements. Discover how organizations establish protection profiles and assign control settings based on data categories. Learn about the importance
5 views • 10 slides
Comprehensive Airport Cybersecurity Quick Guide and Assessment Tool
This project by the National Safe Skies Alliance aims to provide airports with a comprehensive Cybersecurity Quick Guide and Assessment Tool. The guide helps airport managers understand and address cybersecurity issues while the assessment tool evaluates the maturity of their cybersecurity efforts.
0 views • 24 slides
Importance of The Logic Design Tool (LDT) in Medical Device Software Development
The Logic Design Tool (LDT) is a graphical method that helps prevent logical errors in medical device software development, reducing costs and hazardous failures. A study by NIST revealed that logic errors account for a significant percentage of faults in recalled medical devices over a 15-year peri
0 views • 15 slides
Surge Deployment Guidelines and Standard Operating Procedures
Surge Deployment Guidelines and Standard Operating Procedures outline the principles and processes for deploying specialized personnel to support humanitarian operations in various emergencies. The guidelines aim to ensure equal opportunity, transparent processes, and quality responses among Red Cro
0 views • 12 slides
Mainstreaming HIV and AIDS in Uganda: Guidelines and Initiatives
The presentation by Quinto Rwotoyera from Uganda AIDS Commission discusses the national guidelines for mainstreaming HIV and AIDS in all sectors in Uganda. The content covers the existing policy and guidelines, overview of the presidential FastTrack initiative, objectives of the guidelines, users of
0 views • 28 slides
Software Security Principles and Practices: Enhancing Program Code Security
Understanding and addressing critical web application security flaws like unvalidated input, cross-site scripting, buffer overflow, injection flaws, and improper error handling is crucial in enhancing the security of program code. The NIST report NISTIR 8151 provides valuable recommendations to redu
2 views • 44 slides
Understanding Computer Security Principles and Practices
This excerpt delves into the fundamental concepts of computer security, highlighting key principles such as confidentiality, integrity, and availability. It also discusses the NIST's definition of computer security, key security concepts, levels of impact, and challenges faced in the realm of securi
3 views • 26 slides
Understanding Blockchains: Solving Trust Issues in Distributed Systems
Blockchains, as explained by John Kelsey from NIST, are essential for achieving mutual agreement in distributed systems without complete trust among participants. The analogy of chess-by-mail illustrates the need for consensus on the state of the board, similar to how blockchains ensure agreement on
2 views • 34 slides
Overview of AI Definitions and Virginia AI Policies
The content discusses the lack of standardized definitions for artificial intelligence at federal, state, and international levels, highlighting definitions in Virginia and at the federal level by entities like NIST, Congress, and Executive Orders. It also touches on the European Union's approach to
3 views • 15 slides
Analysis of McEliece Vulnerabilities in Escher's World
In this detailed study by Ray Perlner and Dustin Moody from NIST, the vulnerabilities of McEliece in Escher's world are explored. The research covers error sets, commonalities with other variants, private key operations, decoding algorithms, encryption, and more. The findings shed light on potential
0 views • 25 slides
Kompetisi Fungsi Hash NIST (SHA-3): Proses Pemilihan Finalis dan Detail Desain
Seperti sejarah AES, National Institute of Standards and Technology (NIST) menyelenggarakan kompetisi terbuka untuk mengembangkan fungsi hash baru yang disebut SHA-3. Kompetisi ini diadakan dari tahun 2007 hingga Oktober 2012. Proses pemilihan terdiri dari 2 putaran dan babak final dengan total 64 s
0 views • 17 slides
Post-Quantum Cryptography in IEEE 802.11 - Current State and Future Concerns
Submission discusses the potential impact of post-quantum algorithms on IEEE 802.11 networks, highlighting the necessity to prepare for a post-quantum future. It explores the risks posed by quantum computing to existing cryptographic systems and emphasizes the importance of adopting post-quantum sol
0 views • 19 slides
Guidelines on Sale and Packaging of Fresh Produce
Explore methods of sale for fresh fruits and vegetables, from weight to count to pre-packed options. Understand the requirements for pre-packed labels and ready-to-eat packages, ensuring compliance with industry standards such as NIST Handbook 130.
0 views • 18 slides
Enhancing Usability and Accessibility in Next-Generation Elections: NIST Workshop Insights
Preliminary notes from a workshop held by NIST focusing on developing guidance for improving usability and accessibility in next-generation voting systems. The workshop aimed to identify gaps in research, explore new ideas, and outline steps to ensure all voters can vote independently. Participants
1 views • 37 slides
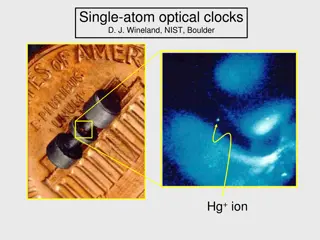
The Importance of Atomic Clocks in Modern Technology
Explore the significance of precise timekeeping provided by atomic clocks, the fundamentals of atomic clocks, the advancements in single-atom optical clocks by experts like D. J. Wineland from NIST Boulder, the role of atomic energy state superpositions, and the practical operation of atomic clocks.
0 views • 33 slides
Enhancing Usability and Accessibility in Next Generation Elections: NIST Roadmap Workshop Insights
This document reflects the proceedings of a NIST workshop focused on developing usability and accessibility guidelines for modern voting systems. The workshop aimed to address challenges, identify opportunities, and discuss the applicability of existing standards. Despite progress made since the VVS
0 views • 25 slides
SPHINCS+ Approach Overview
SPHINCS+ is a post-quantum cryptography approach submitted to the NIST project. It utilizes a hyper-tree structure with specific parameters to enhance security and reduce the tree height. The approach involves picking indices randomly to sign messages efficiently and incorporates modifications to re
0 views • 18 slides
Evaluation of Dynamic Sensitivity Control in Enterprise Scenario
Simulation-based evaluation conducted by Tanguy Ropitault from NIST on Dynamic Sensitivity Control (DSC) in an enterprise scenario using IEEE 802.11 standards. The study investigates the impact of DSC on per-user throughput and fairness in dense scenarios. Recommendations on DSC parameters are provi
0 views • 16 slides
Lightweight Cryptography: Key-Reduced Variants and Beyond-Birthday-Bound Security
Lightweight cryptography has emerged as a hot research topic in the past two decades, with over 60 ciphers proposed. This includes examples like PRESENT, GIFT, SIMON/SPECK, and more. Authenticated encryption through CAESAR and NIST LWC plays a vital role, with ASCON and ACORN leading the lightweight
0 views • 25 slides
A Comparison of AI Risk Management in EU and U.S.
A detailed analysis of AI risk management practices in the EU and U.S., showcasing key differences in regulatory approaches and implications for technology transfer and commercial applications. The comparison covers subfields such as AI for human processes, socioeconomic decisions, consumer products
0 views • 10 slides
Healthcare Security Posture at Centura Health in Southern California
Centura Health in Southern California has a robust healthcare security posture overseen by Scott Raymond, encompassing five hospitals, 350 employed physicians, 400 specialists, and various affiliated centers. The approach covers best practices, breach prevention, threats, NIST, HIPAA compliance, and
0 views • 18 slides
BIKE Cryptosystem: Failure Analysis and Bit-Flipping Decoder
The BIKE cryptosystem is a code-based KEM in the NIST PQC standardization process, utilizing the Niederreiter variant of the McEliece Construction with a QC-MDPC code. It ensures security against IND-CPA, and efforts are made to further confirm or disconfirm its estimates for IND-CCA security requir
0 views • 14 slides
Recent Advancements in Neutron Standards Evaluation
Recent work by Allan D. Carlson, a NIST associate under contract with BNL, was presented at the CSEWG meeting discussing possible changes to neutron standards and showcasing important measurements, such as H(n,n)H angular distribution data by Jiang et al. and 6Li(n,t) reaction measurements by Bai et
0 views • 15 slides
Understanding Medical Guidelines and Their Impact on Healthcare Practices
Medical guidelines play a crucial role in guiding decisions related to diagnosis, management, and treatment in healthcare. They are generated through a structured process involving data collection, evidence prioritization, and consensus among experts. These guidelines, whether at national, regional,
0 views • 16 slides
Exploring Cloud SUTs: Characteristics, Metrics & Potential Workloads
Delve into the world of Cloud SUTs with a focus on understanding the diverse characteristics, key metrics, and potential workloads/use cases. Uncover the challenges of defining SUTs in cloud offerings and explore various classifications such as virtualized, non-virtualized, and mixed environments. G
0 views • 15 slides
Framework Roadmap Overview - July 2018
The Framework Roadmap draft highlights key areas of development relevant to the Framework, including Confidence Mechanisms, Cyber Attack Lifecycle, Cybersecurity Workforce, Cyber Supply Chain Risk Management, Federal Agency Cybersecurity Alignment, Governance and Enterprise Risk Management, Identity
0 views • 7 slides