Abbott Nepro LP Powder Optimal Renal Nutrition for Individuals
Abbott Nepro LP Powder Vanilla Toffe - Complete Renal Nutrition Carb Steady Lower Protein (400 GMS) For People With Kidney Disease (Non-DIALYZED)\n\nEssential Support: Abbott Nepro LP Powder For Renal Nutrition\n\nExperience Essential Support For Individuals With Kidney Disease Through Abbott Nepro
1 views • 4 slides
Abbott Nepro LP Powder Optimal Renal Nutrition for Individuals
Essential Support: Abbott Nepro LP Powder For Renal Nutrition\nExperience Essential Support For Individuals With Kidney Disease Through Abbott Nepro LP Powder. This Vanilla Toffee Variant Is Designed To Provide Complete Renal Nutrition, Ensuring That Those With Specific Dietary Requirements Receive
1 views • 4 slides
Budget Execution Challenges in Somalia's Social Sectors
Addressing malnutrition in Somalia is hindered by low budget execution rates in the health and education sectors. Only a small portion of Official Development Assistance (ODA) is channeled through government systems, impacting service delivery and development financing. Donor-supported budgets for h
0 views • 32 slides
PUMM: Preventing Use-After-Free Using Execution Unit Partitioning
Memory-unsafe languages like C and C++ are prone to Use-After-Free (UAF) vulnerabilities. PUMM introduces execution unit partitioning to efficiently tackle this issue. By segregating and managing execution units, PUMM aims to prevent UAF exploits and enhance software security.
0 views • 31 slides
Graph Neural Networks
Graph Neural Networks (GNNs) are a versatile form of neural networks that encompass various network architectures like NNs, CNNs, and RNNs, as well as unsupervised learning models such as RBM and DBNs. They find applications in diverse fields such as object detection, machine translation, and drug d
2 views • 48 slides
Symbolic Execution Tree for a Program
Generate the complete symbolic execution tree for a given program by annotating nodes with path constraints and line numbers, aiding in understanding program execution flow.
0 views • 26 slides
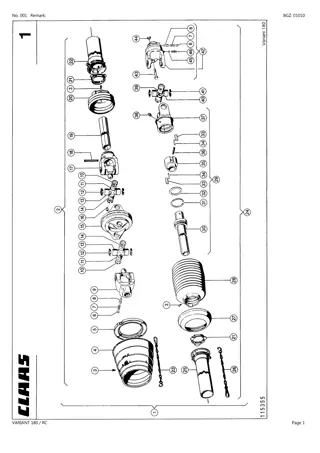
CLAAS VARIANT 180 RC Baler Parts Catalogue Manual Instant Download (SN 04700014-04799999)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
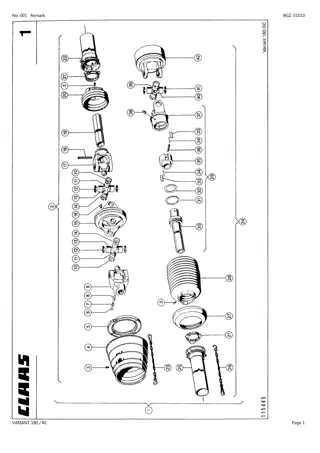
CLAAS VARIANT 180 RC Baler Parts Catalogue Manual Instant Download (SN 04800010-04899999)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
CLAAS VARIANT 180 RC Baler Parts Catalogue Manual Instant Download (SN 04900011-04901496)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
CLAAS VARIANT 180 RC Baler Parts Catalogue Manual Instant Download (SN 04901497-04999999)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
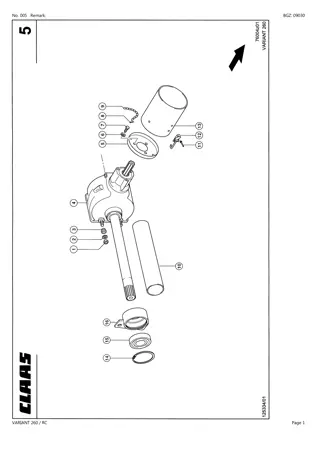
CLAAS VARIANT 260 RC Baler Parts Catalogue Manual Instant Download (SN 73200011-73299999)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
CLAAS VARIANT 280 RC Baler Parts Catalogue Manual Instant Download (SN 73000005-73099999)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
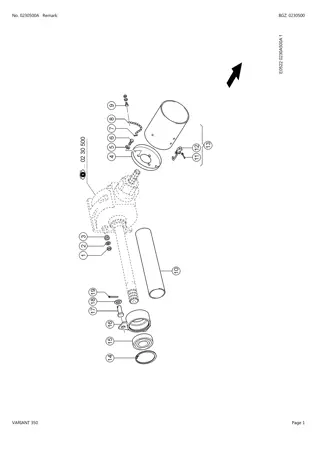
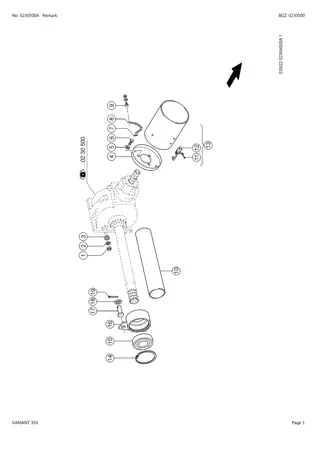
CLAAS VARIANT 350 Baler Parts Catalogue Manual Instant Download (SN 77000011-77000671)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
CLAAS VARIANT 350 Baler Parts Catalogue Manual Instant Download (SN 77000674-77000674)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
CLAAS VARIANT 350 Baler Parts Catalogue Manual Instant Download (SN 77000677-77000684)
Please open the website below to get the complete manual\n\n\/\/ \n
0 views • 24 slides
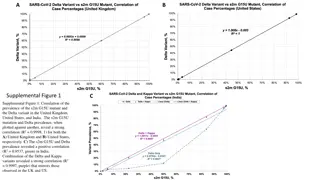
Correlation of s2m G15U Mutant and Delta Variant Prevalence
The correlation between the prevalence of the s2m G15U mutant and the Delta variant in the UK, US, and India was analyzed, showing strong correlations in the UK and US, and a positive correlation in India. Analysis of the s2m phenotype in the Alpha, Delta, and Kappa variants was also conducted. Addi
3 views • 4 slides
Understanding the Neglected Provisions of Order XXI CPC, 1908
Explore the overlooked aspects of Order XXI CPC, 1908, focusing on the definitions, types of decrees, modes of execution, procedures for executing decrees, reasons for neglect, impact, recommendations, and conclusion. Learn about neglected provisions like summary execution, execution against legal r
0 views • 14 slides
Understanding Software Testing: Test Cases, Selection, and Execution
Software testing plays a crucial role in identifying and resolving issues within software products. Test cases, selection, and execution are fundamental aspects of the testing process. Test cases define conditions for testing software functionality, with a focus on repeatability and data specificity
2 views • 36 slides
Polymorphism and Variant Analysis Lab Exercise Overview
This document outlines a lab exercise on polymorphism and variant analysis, covering tasks such as running Quality Control analysis, Genome Wide Association Test (GWAS), and variant calling. Participants will gain familiarity with PLINK toolkit and explore genotype data of two ethnic groups. Instruc
0 views • 43 slides
Enhancing Literature Search for Sequence Variant Analysis
Enhance your literature search skills for sequence variant analysis with tips on effective use of variant nomenclature, sources for finding articles for ACMG criteria application, and tools like HGMD, ClinVar, MasterMind, Google, and Google Scholar. Discover the importance of functional studies, cas
0 views • 21 slides
BioCuration Variant Curation Guidelines and Recommendations
BioCuration Working Group's variant curation guidelines by Steven Harrison provide critical flexibility in variant classification, allowing criteria weights to be adjusted based on professional judgment. Recommendations include harmonizing ACMG/AMP guidelines and documenting strength-modified eviden
3 views • 42 slides
Ensuring Security in Persistent Key-Value Stores using Shielded Execution
This content discusses the challenges and solutions for securing LSM-based Key-Value stores in untrusted computing environments using Shielded Execution. It addresses the need for confidentiality, integrity, and freshness of data in persistent storage systems. The research explores Trusted Execution
0 views • 32 slides
Modes of Execution of Decree in Civil Law
The lecture discusses the various modes of execution of decree in civil law, such as execution against a person through arrest and detention, and execution against property. It explains the procedures involved in arrest and detention, including the conditions for release, restrictions on arrest, and
0 views • 9 slides
Understanding Java Memory Management
Explore how memory is managed in Java programs, including memory allocation for code, objects, and execution stack. Learn about memory areas like the execution stack and heap, and understand the concept of activation records in method execution.
0 views • 27 slides
Exploring Instruction Level Parallel Architectures in Embedded Computer Architecture
Delve into the intricacies of Instruction Level Parallel Architectures, including topics such as Out-Of-Order execution, Hardware speculation, Branch prediction, and more. Understand the concept of Speculation in Hardware-based execution and the role of Reorder Buffer in managing instruction results
0 views • 51 slides
Evolution of Execution Methods in Modern Society
Explore the historical and modern methods of execution, from hanging to lethal injection, and the transition towards more civilized approaches. Learn about the contributions of prominent figures like Elbridge Gerry in advocating for humane execution methods. Delve into the commercial rivalry between
0 views • 13 slides
Secure and Efficient Multi-Variant Execution in Distributed Settings
This paper discusses dMVX, a system for secure multi-variant execution in distributed settings to mitigate memory errors and protect against attacks. Using leader and follower variants, diversified program variants run in lockstep to ensure security. The system monitors and replicates I/O results, e
0 views • 35 slides
Hardware-Assisted Task Scheduler for OS Intensive Applications
A hardware-assisted task scheduler called SchedTask is proposed to address the issue of instruction cache pollution in OS intensive applications. By utilizing SuperFunction characterization and a specialized scheduler, the system aims to optimize task execution on different cores for improved perfor
0 views • 28 slides
Understanding Code Execution Graphs and Superblocks in Software Analysis
Explore the concepts of Static Execution Graphs, Dynamic Execution Graphs, Superblocks, hot-path detection, and memory arithmetic in software analysis. Learn about the grouping of blocks, violation tracking, control dependencies, and code behaviors across time through these graphical representations
0 views • 9 slides
Understanding Processes in Operating Systems - ECE344 Lecture 3 Summary
This lecture delves into the essential concepts of processes, threads, and synchronization in operating systems. Key topics covered include units of execution, representation of units of execution in the OS, process execution states, and state transitions. Users, programs, and the role of processes
0 views • 45 slides
InvisiSpec: Making Speculative Execution Invisible
InvisiSpec presents a novel defense mechanism to address speculative execution attacks in the cache hierarchy. By making speculative execution invisible to potential attackers, this holistic approach aims to mitigate the risks associated with exploiting side effects on incorrect paths, such as Spect
0 views • 18 slides
Multicycle Datapath and Execution Steps Overview
This content provides a detailed explanation of a multicycle datapath and the execution steps involved in processing instructions. It covers key elements such as instruction fetching, decoding, memory referencing, ALU operations, branch and jump instructions, as well as memory access for read and wr
0 views • 11 slides
Understanding Symbolic Execution and Directed Automated Random Testing
Symbolic Execution is a method used for analyzing programs to determine inputs causing each part to execute, vital in program testing. However, limitations arise in cases without code availability, hindering definitive path conditions. Directed Automated Random Testing (DART) overcomes this through
0 views • 20 slides
Secure Cloud Applications with Intel SGX - OSDI 2014 Presentation Summary
This presentation discusses the challenges of trusting cloud environments and proposes solutions utilizing Intel SGX technology. It explores the need for secure execution of applications on untrusted cloud platforms, presents existing solutions, and introduces the concept of Haven for private execut
0 views • 33 slides
Rethinking Processes with Threads in Operating Systems
Processes in operating systems traditionally include various resources and execution states, leading to inefficiencies in communication and parallel program execution. By separating the concept of a process from its execution state, modern OSes like Mac, Windows, and Unix introduce threads as lightw
0 views • 29 slides
Python Programming Essentials: Basics, Operators, Expressions, and Control Flow
This segment delves into the fundamentals of Python programming with a focus on essential concepts such as comments, numbers, strings, variables, arithmetic operators, logical operators, order of execution, expressions, and control flow statements like conditional execution and looping. Learn about
0 views • 12 slides
N-Variant Execution for Improved Security Measures
N-Variant Execution (NVX) is a technique used to enhance security measures by running diversified program variants in parallel and comparing their outputs for transparency. NVX systems can protect against attacks relying on knowledge of virtual address spaces but have limitations against attacks bas
0 views • 48 slides
Understanding Operating System Concepts: Multiprogramming, Multiprocessing, Multitasking, and Multithreading
In the realm of operating systems, terms like multiprogramming, multiprocessing, multitasking, and multithreading can often be confusing due to their similar appearance but distinct meanings. These concepts play a crucial role in efficiently managing resources in a computing system, particularly in
0 views • 6 slides
Memory Allocation and Program Execution Overview
Understanding memory allocation is crucial for efficient program execution. This content delves into the importance of memory allocation, considerations for storing data during program execution, and the requirements for allocating memory efficiently. It also explores solutions for managing memory s
0 views • 35 slides
Understanding CPU Virtualization and Execution Control in Operating Systems
Explore the concepts of CPU virtualization, direct execution, and control mechanisms in operating systems illustrated through a series of descriptive images. Learn about efficient CPU virtualization techniques, managing restricted operations, system calls, and a limited direct execution protocol for
0 views • 18 slides