Understanding Memory Allocation in Operating Systems
Memory allocation in operating systems involves fair distribution of physical memory among running processes. The memory management subsystem ensures each process gets its fair share. Shared virtual memory and the efficient use of resources like dynamic libraries contribute to better memory utilizat
1 views • 233 slides
Understanding Memory Organization in Computers
The memory unit is crucial in any digital computer for storing programs and data. It comprises main memory, auxiliary memory, and cache memory, each serving different roles in data storage and retrieval. Main memory directly communicates with the CPU, while cache memory enhances processing speed by
1 views • 37 slides
Understanding Memory Organization in Computers
Delve into the intricate world of memory organization within computer systems, exploring the vital role of memory units, cache memory, main memory, auxiliary memory, and the memory hierarchy. Learn about the different types of memory, such as sequential access memory and random access memory, and ho
0 views • 45 slides
Understanding AARCH64 Linux Kernel Memory Management
Explore the confidential and proprietary details of AARCH64 Linux kernel memory mapping, virtual memory layout, variable configurations, DDR memory layout, and memory allocation techniques. Get insights into the allocation of physically contiguous memory using Continuous Memory Allocator (CMA) integ
0 views • 18 slides
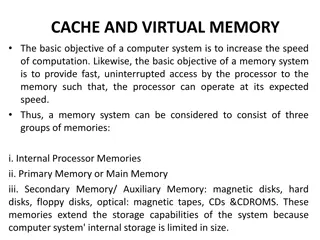
Understanding Cache and Virtual Memory in Computer Systems
A computer's memory system is crucial for ensuring fast and uninterrupted access to data by the processor. This system comprises internal processor memories, primary memory, and secondary memory such as hard drives. The utilization of cache memory helps bridge the speed gap between the CPU and main
1 views • 47 slides
Dynamic Memory Allocation in Computer Systems: An Overview
Dynamic memory allocation in computer systems involves the acquisition of virtual memory at runtime for data structures whose size is only known at runtime. This process is managed by dynamic memory allocators, such as malloc, to handle memory invisible to user code, application kernels, and virtual
0 views • 70 slides
Understanding Garbage Collection in Java Programming
Garbage collection in Java automates the process of managing memory allocation and deallocation, ensuring efficient memory usage and preventing memory leaks and out-of-memory errors. By automatically identifying and removing unused objects from the heap memory, the garbage collector frees up memory
14 views • 22 slides
Understanding Memory Management in Operating Systems
Dive into the world of memory management in operating systems, covering topics such as virtual memory, page replacement algorithms, memory allocation, and more. Explore concepts like memory partitions, fixed partitions, memory allocation mechanisms, base and limit registers, and the trade-offs betwe
1 views • 110 slides
Importance of Timely Verification in Care After Death
Understanding the verification process and importance of timely verification in care after death is crucial for improving the experience of death and dying for families. This session covers the definitions, process, and care after death, emphasizing the significance of timely verification in end-of-
1 views • 15 slides
Understanding Shared Memory Architectures and Cache Coherence
Shared memory architectures involve multiple CPUs accessing a common memory, leading to challenges like the cache coherence problem. This article delves into different types of shared memory architectures, such as UMA and NUMA, and explores the cache coherence issue and protocols. It also highlights
2 views • 27 slides
Understanding Memory Management and Swapping Techniques
Memory management involves techniques like swapping, memory allocation changes, memory compaction, and memory management with bitmaps. Swapping refers to bringing each process into memory entirely, running it for a while, then putting it back on the disk. Memory allocation can change as processes en
0 views • 17 slides
Integrated Verification and Repair in Control Plane
Modern networks face challenges from incorrect configurations affecting millions of users. This presentation discusses the integration of verification and repair processes into the control plane, aiming for consistent and policy-compliant network operations. It explores the complexities of network c
0 views • 16 slides
Formal Verification and Automata Abstraction in Esterel
This content delves into the applications of formal verification and automata abstraction in Esterel, focusing on techniques such as verification by abstraction of automata, boolean verification using BDDs, bounded model checking in SAT/SMT, and more. The work of Gérard Berry at the Collège de Fra
0 views • 38 slides
Enhancing Memory and Concentration Techniques for Academic Success
Explore the fascinating world of memory and concentration through various techniques and processes highlighted in the provided images. Discover how sensory memory, short-term memory, and long-term memory function, along with tips on improving concentration, learning strategies, and the interplay bet
1 views • 34 slides
Program Verification via an Intermediate Verification Language
Dive into the world of program verification through an intermediate verification language with a focus on static program verification, reasoning about programs, and separation of concerns. Explore tools like Dafny and verification architectures like Boogie and Why3, along with key concepts including
0 views • 36 slides
Understanding Memory Encoding and Retention Processes
Memory is the persistence of learning over time, involving encoding, storage, and retrieval of information. Measures of memory retention include recall, recognition, and relearning. Ebbinghaus' retention curve illustrates the relationship between practice and relearning. Psychologists use memory mod
0 views • 22 slides
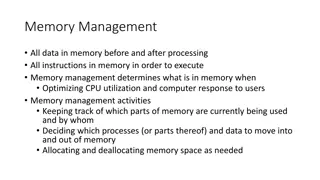
Understanding Memory Management in Computer Systems
Memory management in computer systems involves optimizing CPU utilization, managing data in memory before and after processing, allocating memory space efficiently, and keeping track of memory usage. It determines what is in memory, moves data in and out as needed, and involves caching at various le
1 views • 21 slides
Dynamic Memory Management Overview
Understanding dynamic memory management is crucial in programming to efficiently allocate and deallocate memory during runtime. The memory is divided into the stack and the heap, each serving specific purposes in storing local and dynamic data. Dynamic memory allocators organize the heap for efficie
0 views • 31 slides
Understanding Memory Management in C Programming
The discussion covers various aspects of memory management in C programming, including common memory problems and examples. It delves into memory regions, stack and heap management, and static data. The examples illustrate concepts like static storage, heap allocation, and common pitfalls to avoid.
0 views • 24 slides
Comprehensive Solution for EU Digital COVID Certificate Verification
This solution offers face recognition, temperature monitoring, and verification of EU Digital COVID Certificates for personnel. It includes products like DHI-ASI7213X-V1-T1 and ASF172X-T1, with various unlocking modes and support for certificate verification. The system allows for accurate and fast
0 views • 7 slides
Understanding Your Memory System: A Guide to Enhancing Recall
Learn about the three components of the memory system - sensory memory, short-term memory, and long-term memory. Discover why we forget and how to improve memory retention through techniques like positive attitude, focus, mnemonic devices, and more. Enhance your memory skills to boost learning effic
0 views • 8 slides
Managing Memory Pressure in Data-Parallel Programs
Addressing memory pressure in data-parallel programs is crucial to prevent performance degradation and out-of-memory errors. The solution lies in Interruptible Tasks (ITasks), a new type of data-parallel tasks that can be interrupted and memory reclaimed to optimize system scalability. Current chall
0 views • 24 slides
Enhancing Memory Security with H2ORAM and Secure Memory Techniques
Explore cutting-edge research in memory security with topics such as H2ORAM optimization for hybrid memory systems, secure memory principles, Oblivious-RAM for data protection, Path ORAM storage structures, Ring ORAM for read paths, and the application of ORAM in hybrid memory architectures. These a
0 views • 10 slides
Understanding Memory Basics in Digital Systems
Dive into the world of digital memory systems with a focus on Random Access Memory (RAM), memory capacities, SI prefixes, logical models of memory, and example memory symbols. Learn about word sizes, addresses, data transfer, and capacity calculations to gain a comprehensive understanding of memory
1 views • 12 slides
Optimizing Data Center Costs with Heterogeneous-Reliability Memory
Reducing data center costs while meeting availability targets is the focus of this study on memory error vulnerabilities. By employing a heterogeneous-reliability memory approach, storing error-tolerant data in less reliable memory and error-vulnerable data in more reliable memory, significant savin
0 views • 51 slides
Understanding Different Types of Memory Technologies in Computer Systems
Explore the realm of memory technologies with an overview of ROM, RAM, non-volatile memories, and programmable memory options. Delve into the intricacies of read-only memory, volatile vs. non-volatile memory, and the various types of memory dimensions. Gain insights into the workings of ROM, includi
0 views • 45 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Understanding Virtual Memory Concepts and Benefits
Virtual Memory, instructed by Shmuel Wimer, separates logical memory from physical memory, enabling efficient utilization of memory resources. By using virtual memory, programs can run partially in memory, reducing constraints imposed by physical memory limitations. This also enhances CPU utilizatio
0 views • 41 slides
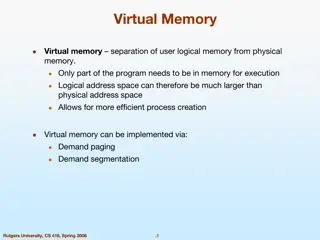
Understanding Virtual Memory and its Implementation
Virtual memory allows for the separation of user logical memory from physical memory, enabling efficient process creation and effective memory management. It helps overcome memory shortage issues by utilizing demand paging and segmentation techniques. Virtual memory mapping ensures only required par
0 views • 20 slides
Understanding Memory: Challenges and Improvement
Delve into the intricacies of memory with discussions on earliest and favorite memories, a memory challenge, how memory works, stages of memory, and tips to enhance memory recall. Explore the significance of memory and practical exercises for memory improvement.
0 views • 16 slides
Understanding Virtual Memory and Memory Management
Virtual memory allows programs to exceed physical memory limits by utilizing disk space, managed by the operating system. By using techniques like paging and page tables, virtual addresses are mapped to physical memory addresses. This article explores the concepts of virtual memory, paging, page tab
0 views • 18 slides
Overview of Program Verification Tools and Techniques
Explore the pillars of program verification, early mechanical verification systems, software quality assurance, and a spectrum of verification tools used for ensuring functional correctness, safety-critical systems, and more. Discover the role of proof assistants and automatic decision procedures in
0 views • 21 slides
Enhanced Virtual Memory Framework for Fine-grained Memory Management
This study introduces Page Overlays, a new virtual memory framework designed to enable fine-grained memory management. By efficiently storing pages with similar data and providing powerful access semantics, Page Overlays improve performance and reduce memory redundancy compared to existing virtual m
0 views • 29 slides
Memory Management Principles in Operating Systems
Memory management in operating systems involves the allocation of memory resources among competing processes to optimize performance with minimal overhead. Techniques such as partitioning, paging, and segmentation are utilized, along with page table management and virtual memory tricks. The concept
0 views • 29 slides
Introduction to UVM: Verification Methodologies Overview
Explore the Universal Verification Methodology (UVM) for writing modular, scalable, and reusable testbenches. Learn about UVM's key technical highlights, its support for migration towards Coverage Driven Verification (CDV), and the advantages of Constrained Random Verification (CRV) in functional ha
0 views • 20 slides
Effective Program Verification for Relaxed Memory Models
Memory model vulnerabilities arise when programmers do not strictly adhere to locking disciplines in performance-critical code, leading to data races that can break on relaxed memory models. This can be challenging to detect and analyze due to the complexities introduced by both compilers and hardwa
0 views • 22 slides
Memory Model Safety of Programs Research
Explore the challenges and vulnerabilities in memory models of programs, emphasizing the importance of maintaining strict locking discipline for performance-critical code. The research discusses issues with relaxed memory models on multicore machines and provides examples of memory model vulnerabili
0 views • 14 slides
Understanding Linux Virtual Memory Management
The memory management subsystem in Linux ensures fair physical memory allocation for running processes, allowing them to share virtual memory when needed. Processes can have separate virtual address spaces or share memory through mechanisms like Unix System V shared memory IPC. Linux uses an abstrac
0 views • 230 slides
Enhancing Memory Bandwidth with Transparent Memory Compression
This research focuses on enabling transparent memory compression for commodity memory systems to address the growing demand for memory bandwidth. By implementing hardware compression without relying on operating system support, the goal is to optimize memory capacity and bandwidth efficiently. The a
0 views • 34 slides
Locality-Aware Caching Policies for Hybrid Memories
Different memory technologies present unique strengths, and a hybrid memory system combining DRAM and PCM aims to leverage the best of both worlds. This research explores the challenge of data placement between these diverse memory devices, highlighting the use of row buffer locality as a key criter
0 views • 34 slides