Computational Physics (Lecture 18)
Neural networks explained with the example of feedforward vs. recurrent networks. Feedforward networks propagate data, while recurrent models allow loops for cascade effects. Recurrent networks are less influential but closer to the brain's function. Introduction to handwritten digit classification
0 views • 55 slides
Understanding Computer Networks: Types and Characteristics
In the realm of computer networks, nodes share resources through digital telecommunications networks. These networks enable lightning-fast data exchange and boast attributes like speed, accuracy, diligence, versatility, and vast storage capabilities. Additionally, various types of networks exist tod
9 views • 12 slides
Asia-Pacific Location-based Services Market
Asia-Pacific Location-based Services Market by Component, Technology (GNSS, GPS), Application (Navigation, Mapping & GIS), Location Type, End-use Industry (Transportation & Logistics, Retail & E-commerce), and Geography -Forecast to 2031
1 views • 5 slides
Proposal for Location Configuration Information (LCI) in IEEE 802.11 Beacons and Probe Responses
This document proposes the inclusion of Location Configuration Information (LCI) data in a standard information element broadcast in Beacons and Probe Responses within IEEE 802.11 networks. By enhancing the accessibility of infrastructure location to non-AP STAs, this proposal aims to simplify locat
1 views • 5 slides
Steering Opinion Dynamics Through Control of Social Networks
Understanding the dynamics of opinion formation and control in social networks is a critical area of research. This study, supervised by Susana Gomes and Marie-Therese Wolfram, explores the manipulation of collective behavior through various models including ODE, agent-based, and stochastic analysis
0 views • 29 slides
Exploring Graph-Based Data Science: Opportunities, Challenges, and Techniques
Graph-based data science offers a powerful approach to analyzing data by leveraging graph structures. This involves using graph representation, analysis algorithms, ML/AI techniques, kernels, embeddings, and neural networks. Real-world examples show the utility of data graphs in various domains like
3 views • 37 slides
Understanding Artificial Neural Networks From Scratch
Learn how to build artificial neural networks from scratch, focusing on multi-level feedforward networks like multi-level perceptrons. Discover how neural networks function, including training large networks in parallel and distributed systems, and grasp concepts such as learning non-linear function
1 views • 33 slides
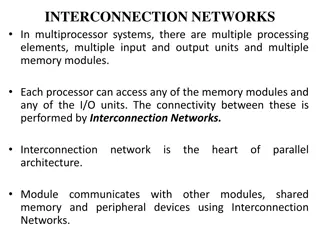
Understanding Interconnection Networks in Multiprocessor Systems
Interconnection networks are essential in multiprocessor systems, linking processing elements, memory modules, and I/O units. They enable data exchange between processors and memory units, determining system performance. Fully connected interconnection networks offer high reliability but require ext
1 views • 19 slides
Trade Area Analysis and Site Selection in Retail Management
This module delves into the importance of selecting a store location in retail management, covering topics such as environmental analysis, data analysis for location selection, and the effects of location choice on planning. It also includes activities like conducting an environmental analysis of a
0 views • 22 slides
Introduction to Neural Networks in IBM SPSS Modeler 14.2
This presentation provides an introduction to neural networks in IBM SPSS Modeler 14.2. It covers the concepts of directed data mining using neural networks, the structure of neural networks, terms associated with neural networks, and the process of inputs and outputs in neural network models. The d
0 views • 18 slides
Social Networks, Privacy, and Freedom of Association in the Digital Age
Explore the intersection of social networks, privacy, and freedom of association through discussions on platforms for political mobilization, privacy concerns, state actions, and the impact on expressive association rights. Learn from historical cases like NAACP v. Alabama and delve into contemporar
0 views • 9 slides
Location-Based Services Market: Emerging Technologies and Their Applications
Location-based Services Market by Component, Technology (GNSS, GPS), Application (Navigation, Tracking), Location Type, End-use Industry (Government and Public Sector, Transportation & Logistics, Smart Cities), and Geography - Global Forecast to 2031
0 views • 4 slides
Understanding Geolocation: What You Need to Know
Geolocation is a built-in browser functionality that allows web applications to be location-aware. It uses geographic latitude/longitude and is supported by all modern browsers, making it an integral part of the HTML5/W3C JavaScript API. With geolocation, you can show users their position on a map,
0 views • 16 slides
Understanding Router Routing Tables in Computer Networks
Router routing tables are crucial for directing packets to their destination networks. These tables contain information on directly connected and remote networks, as well as default routes. Routers use this information to determine the best path for packet forwarding based on network/next hop associ
0 views • 48 slides
P-Rank: A Comprehensive Structural Similarity Measure over Information Networks
Analyzing the concept of structural similarity within Information Networks (INs), the study introduces P-Rank as a more advanced alternative to SimRank. By addressing the limitations of SimRank and offering a more efficient computational approach, P-Rank aims to provide a comprehensive measure of si
0 views • 17 slides
Cellular Network Security Threats and Solutions
This article delves into the security aspects of cellular networks, focusing on threats such as charging fraud, unauthorized use, handset cloning, voice interception, location tracking, and network service disruptions. It also explores the security architecture involving Home Location Register (HLR)
0 views • 28 slides
Understanding Centrality Measures in Peer-to-Peer and Social Networks
Centrality measures in networks quantify the importance of nodes based on their influence, accessibility, and role as connectors. Important centrality measures include Degree centrality (based on the number of connections), Closeness centrality (based on short paths to other nodes), and Betweenness
0 views • 27 slides
Fault Location and Detection in Smart Grids
Fast and accurate fault detection and location are crucial in power grid management, especially in smart grids with bidirectional power flow. This study explores various fault location methods including impedance-based and travelling waves-based approaches. It also discusses the use of Intelligent E
0 views • 10 slides
Insights into Mobile Ad Hoc Networks and Location-Based Applications
Explore the intersection of mobile ad hoc networks, location-based applications, and context-based services in a hyper-connected world. Understand the implications of human movement patterns, privacy threats, and the significance of location as identity. Discover strategies for controlling location
0 views • 40 slides
Understanding the Impact of Social Networks on Health and Well-being in Older Adults
Explores the significance of social relationships in influencing health behaviors and longevity among older adults. Discusses the multidimensional nature of social networks and the need to incorporate them into interventions for behavior change. Theoretical perspectives like the Convoy Model shed li
0 views • 14 slides
Innovations in Ropeless Fishing Gear Location Marking
Innovative approaches to marking the location of ropeless fishing gear include using acoustic technology to enable gear to report its position to fishermen. This technology aims to address gear conflicts and improve the efficiency of fisheries by providing accurate location data. Acoustic modems pla
0 views • 20 slides
Using Social Networks to Improve Lifestyles of Health Practitioners
This study implemented an intervention utilizing social networks to enhance the lifestyles of health practitioners (doctors, nurses, nutritionists). Through daily messages or images sent via social networks over an 8-week period, the intervention focused on promoting better diet quality and physical
0 views • 10 slides
Understanding Greedy Distributed Spanning Tree Routing in Wireless Sensor Networks
Wireless sensor networks play a critical role in various applications, and the Greedy Distributed Spanning Tree Routing (GDSTR) protocol, developed by Matthew Hendricks, offers an efficient routing approach. This protocol addresses challenges such as scalability, dynamic topologies, and sensor node
0 views • 34 slides
Social Dynamics in South Africa: Exploring Social Capital, Trust, Networks, and Tolerance
The study delves into social aspects in South Africa, examining social capital, trust levels among different racial groups, social networks patterns, and societal tolerance towards various groups. Through data analysis, it provides insights into the dynamics shaping social interactions and cohesion
0 views • 7 slides
Understanding Social Neuroscience: Exploring Human Sociality and Well-Being
Social neuroscience delves into how the brain processes social interactions and their impact on human well-being. It focuses on the interconnectedness between social connections and overall life satisfaction, suggesting that humans are inherently social beings with a strong need for social belonging
2 views • 21 slides
Social Entrepreneurship and Social Inclusion in Bulgaria
The development and implementation of social entrepreneurship practices in Bulgaria aim to promote social inclusion through the development of the social economy. The focus is on combining economic results with social objectives, managed transparently with measurable, positive financial value. Vario
2 views • 12 slides
Understanding Overlay Networks and Distributed Hash Tables
Overlay networks are logical networks built on top of lower-layer networks, allowing for efficient data lookup and reliable communication. They come in unstructured and structured forms, with examples like Gnutella and BitTorrent. Distributed Hash Tables (DHTs) are used in real-world applications li
0 views • 45 slides
Understanding Networks: An Introduction to the World of Connections
Networks define the structure of interactions between agents, portraying relationships as ties or links. Various examples such as the 9/11 terrorists network, international trade network, biological networks, and historical marriage alliances in Florence illustrate the power dynamics within differen
0 views • 46 slides
Enhancing Engagement Through Social Networks in Higher Education
Exploring the use of social networks, specifically Instagram, to improve student engagement and implement a research-led curriculum in higher education. The discussion covers the shift to blended learning post-COVID-19, the relationship between student satisfaction and research intensity, and the be
0 views • 14 slides
Diverse Social Entities Mining from Linked Data in Social Networks
This research focuses on mining diverse social entities from linked data in social networks using a DF-tree structure and DF-growth mining algorithm. The study explores the extraction of important linked data in social networks and the mining of various social entities such as friends. Prominence va
0 views • 13 slides
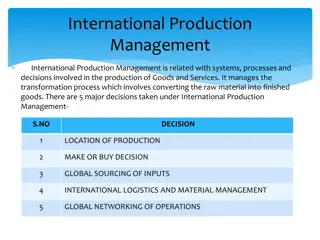
International Production Management: Location Strategy and Decision Making
International Production Management involves systems, processes, and decisions related to the production of goods and services. Key decisions include plant location, make or buy choices, global sourcing, logistics, and networking. Factors influencing location strategy include customer preferences, p
0 views • 12 slides
Location-Based Reminder Android Application
Presenting an Android application that utilizes GPS to determine a user's location and trigger alerts set up by the user. Discussing the design of the UI, code, work methods, tools, technologies used in the project, testing methods, motivation, and impact. The application aims to improve user effici
0 views • 14 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Understanding Strong and Weak Ties in Social Networks
Explore the concepts of strong and weak ties in social networks based on Easley and Kleinberg's theories. Delve into the flow of information, structural differences among nodes, and the evolution of networks over time. Discover the significance of triadic closure principle and clustering coefficient
0 views • 60 slides
Understanding Individual Life Patterns through Location History Mining
GPS-enabled devices have made it possible to track human location history, offering insight into individual behaviors and preferences. This paradigm explores modeling techniques, challenges, and motivations for mining location data to predict and personalize user experiences. The framework presented
0 views • 24 slides
Evolution of Networking: Embracing Software-Defined Networks
Embrace the future of networking by transitioning to Software-Defined Networks (SDN), overcoming drawbacks of current paradigms. Explore SDN's motivation, OpenFlow API, challenges, and use-cases. Compare the complexities of today's distributed, error-prone networks with the simplicity and efficiency
0 views • 36 slides
Impact of Geographical Location on Educational Attainment
The geographical location plays a significant role in educational success, with certain areas experiencing lower quality facilities and reputation. Factors like social class and deprivation impact education outcomes, as seen in performance indicators and school statistics. Patterns reveal failing sc
0 views • 21 slides
Understanding Interconnection Networks in Embedded Computer Architecture
Explore the intricacies of interconnection networks in embedded computer architecture, covering topics such as connecting multiple processors, topologies, routing, deadlock, switching, and performance considerations. Learn about parallel computer systems, cache interconnections, network-on-chip, sha
0 views • 43 slides
Top 5 Key Features of ONEMONITAR's Location Tracker App
ONEMONITAR Location Tracker Key Features: Monitor real-time movements, set geofencing alerts, view location history, track multiple devices, and receive instant customizable notifications\u2014all in one powerful app.\n\/\/onemonitar.com\/location-tr
2 views • 1 slides
Understanding Deep Generative Bayesian Networks in Machine Learning
Exploring the differences between Neural Networks and Bayesian Neural Networks, the advantages of the latter including robustness and adaptation capabilities, the Bayesian theory behind these networks, and insights into the comparison with regular neural network theory. Dive into the complexities, u
0 views • 22 slides