The Secure Path_ Implementing Digital Product Keys for Online Businesses (1)
In today's digital landscape, where online businesses reign supreme, safeguarding products and services against piracy and unauthorized access is paramount. Enter the era of digital product keys \u2013 a secure path towards ensuring the integrity of online transactions and protecting intellectual pr
1 views • 3 slides
windows 10 pro OEM kEYS
Windows 10 Pro OEM keys are digital licenses that activate Windows 10 Pro on a device. They're sold at lower prices than retail keys, often to system builders. These keys tie to the original hardware and offer full OS functionality, updates, and support. They're cost-effective for PC builders and in
3 views • 2 slides
Cracking the Code Understanding Windows 10 Pro OEM Keys
Understanding Windows 10 Pro OEM keys is crucial for activating licenses efficiently. OEM keys are linked to specific hardware, like pre-built systems, ensuring affordability but limited to that hardware. They're not transferable between devices. Retail keys, on the other hand, offer flexibility but
1 views • 8 slides
WindowKeys Unlocking the Power of Windows with Genuine License Keys
Windows with Genuine License Keys provide a secure and reliable operating system experience. These keys ensure that your version of Windows is legitimate and allows you to access all features and updates. With a genuine license key, you can activate your copy of Windows, receive support from Microso
4 views • 3 slides
Best Automotive Locksmith In Los Angeles
Need a skilled automotive locksmith in Los Angeles. A skilled locksmith with the ability to create car keys and fix ignition issues is known as an automotive locksmith. This locksmith can also fix your automobile's lock mechanisms and unlock your car. Car locksmith are capable of cutting car keys. W
10 views • 7 slides
Understanding Rank, Select, and Range in Binary Search Trees
Rank, Select, and Range are key operations in Binary Search Trees that help determine the position of a key, find a key based on its rank, and select keys within a specified range. Sedgewick's notes provide detailed insights into the definitions and implementations of these operations, including com
2 views • 8 slides
Divine Turnaround: Keys to Supernatural Transformations
Learn about Divine Turnaround, where God intervenes to bring about sudden, positive changes beyond human understanding. Explore examples from scriptures like Exodus, 1 Samuel, and Luke, illustrating how faith and decisive action can lead to miraculous transformations. Discover the essential keys to
1 views • 12 slides
Understanding Classification Keys for Identifying and Sorting Things
A classification key is a tool with questions and answers, resembling a flow chart, to identify or categorize things. It helps in unlocking the identification of objects or living things. Explore examples like the Liquorice Allsorts Challenge and Minibeast Classification Key. Also, learn how to crea
1 views • 6 slides
Understanding Dictionaries in Python
Dictionaries in Python allow storing elements with keys of various hashable types and values of any data type. Keys must be unique, but values can be duplicated. Dictionaries cannot be concatenated but can be nested. When passed to a function, dictionaries exhibit pass-by-reference behavior due to t
2 views • 14 slides
Understanding VSAM Logical Record Access Methods
VSAM utilizes three primary methods to find logical records - Relative Byte Address, Relative Record Number, and Key field. Relative Byte Address assigns a unique address to each record based on sequential ordering. Relative Record Number is used in RRDS datasets to access records by a numbered sequ
3 views • 35 slides
Understanding Keys and SQL Commands in Database Management Systems
Explore different types of keys used in databases such as Candidate Key, Super Key, Composite Key, Primary Key, Alternate Key, Unique Key, and Foreign Key. Learn about SQL commands categorized into DDL, DML, and DCL and various query languages like Create, Alter, Rename, Drop, Comment, Truncate, Ins
0 views • 11 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Understanding Keys in Relational Databases
Keys play a crucial role in relational databases by uniquely identifying records and establishing relationships between tables. Primary keys are essential for data integrity, ensuring each entity is identified uniquely. Learn about primary keys, types of keys, and examples of creating tables with pr
0 views • 57 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
A Complete Guide About Draft Keys & Lugs
Do you know that in the realm of brewing & beverage dispensing, understanding the components that make equipment crucial for maintaining quality as well as efficiency are draft keys and lugs?
0 views • 5 slides
Understanding the Key Concepts of Relational Databases
Introduction to the fundamental concepts of relational databases including the relational model proposed by Edgar F. Codd, relation schemes, relation instances, keys for a relation, and more. Discover the significance of keys, candidate keys, superkeys, and primary keys in database design.
0 views • 27 slides
Understanding Dictionaries in Python
Dictionaries in Python allow you to store elements with keys of any type and values of any type. They can contain any and different types of elements, have unique keys but can have duplicate values, cannot be concatenated or repeated, can be nested, and are mutable like lists. Dictionaries can be it
0 views • 13 slides
Understanding Database Management Systems and Keys in SQL
This content discusses the importance of organizing data into multiple tables within a database management system, the concept of keys and foreign keys, and the potential issues of data redundancy. It also covers examples of structured data related to products, orders, and manufacturers.
0 views • 55 slides
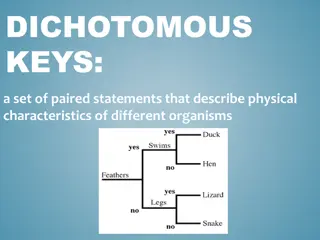
Exploring Dichotomous Keys in Biology
Delve into the world of dichotomous keys with lessons on their types and practical application. Learn how to use these keys to identify various organisms and classify them based on specific characteristics. From distinguishing between different cat species to identifying aquatic organisms, this expl
0 views • 17 slides
Exploring Computer Keyboards And Typewriters
Dive into the world of computer keyboards and typewriters to understand their similarities and differences. Learn about the layout of alphabetic keys like QWERTY, utilizing the shift key for capitalization and special characters, the function of the enter key, differences between computer keyboards
0 views • 18 slides
Understanding Ecosystems and Habitat Identification Through Practical Activities
Explore the dynamic interaction between organisms and the environment in various ecosystems through practical activities like identifying habitats, fauna, and flora using simple keys. Learn how to use collection apparatus for ecological studies and create keys to classify different objects and organ
0 views • 14 slides
Understanding Public-Key Cryptography and Its Applications
Public-Key Cryptography revolutionized secure communication by introducing the concept of using separate keys for encryption and decryption. Initially explored by researchers like Diffie, Hellman, and Merkle in the 70s, it addressed key distribution challenges faced by symmetric cryptography. This m
0 views • 34 slides
Understanding Distributed Hash Tables in Peer-to-Peer Systems
Distributed Hash Tables (DHTs) are a fundamental component in organizing nodes in peer-to-peer networks. By using hash functions to assign keys to peers, DHTs enable efficient storage and retrieval of objects. Peers in a DHT are responsible for storing and managing key-value pairs, with each key bei
0 views • 31 slides
Understanding Encryption: Keys, Algorithms, and Applications
Encryption plays a crucial role in securing data transmission and storage. It involves using keys and algorithms to convert plaintext information into a cipher that can only be deciphered with the correct key. This article explores different encryption methods, such as private and public key encrypt
0 views • 62 slides
Unveiling the Revelation: Keys to Understanding
Delve into the book of Revelation unveiling the symbolic meanings and messages revealed to the seven churches in Asia. Explore the significance of the seals opening, the role of John as the witness, and the impending events signified through divine visions. Discover the four keys essential to interp
0 views • 53 slides
Understanding Matching Keys in Database Systems
Matching keys play a crucial role in identifying the same real-world entities in database systems. They specify which attributes to compare and how to compare them, helping minimize redundancy and improve data accuracy. This summary discusses relative candidate keys, minimal matching keys, and relia
0 views • 13 slides
Understanding the Relational Data Model and Database Concepts
Delve into the world of relational data modeling, database integrity rules, and structure. Explore how a university database in MS Access utilizes relational tables and fields to store information. Learn about the key terminology associated with relational databases, such as primary keys, foreign ke
0 views • 69 slides
Understanding SQL Constraints and Triggers in Database Systems
SQL (Structured Query Language) provides a high-level approach to database management by focusing on what needs to be done rather than how. Constraints and triggers play vital roles in ensuring data integrity and enforcing specific actions. Keys, foreign keys, value-based constraints, tuple-based co
0 views • 130 slides
Overlay Networks and Consistent Hashing in Distributed Systems
Understanding the concept of overlay networks and consistent hashing in distributed systems is crucial for scalability and efficient data storage. Overlay networks like P2P DHT via KBR offer a decentralized approach for managing data while consistent hashing provides a balanced and deterministic way
0 views • 36 slides
Key and Splines Design at Minia University
Key and splines design play a crucial role in connecting mechanical elements like shafts and hubs to transmit power efficiently. This article covers the types of keys, principles of work, and various classifications of keys such as sunk keys, saddle keys, tangent keys, round keys, and splines. It de
0 views • 20 slides
Importance of Describing Soil Profiles for Soil Suitability Analysis
Proper classification and interpretation of soil properties through describing soil profiles are essential in determining soil suitability for various uses. Soil classification involves describing, classifying, and interpreting soil properties to understand the best uses and limitations of the soil.
0 views • 5 slides
Understanding Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Understanding Dichotomous Keys and Cladograms in Evolutionary Biology
Dichotomous keys are utilized to classify different organisms based on their physical characteristics, while cladograms depict evolutionary relationships. Derived traits play a crucial role in understanding evolutionary history, indicating features present in later organisms but not earlier ones. Pr
0 views • 16 slides
Understanding Hash Tables and Handling Collisions
This content covers the concepts of hash tables, handling collisions, and efficient implementation of dictionary operations. It explores methods like direct-access tables, converting keys to non-negative integers, and using functions to work with non-integer keys. The discussion includes approaches
0 views • 32 slides
The Case of the Missing Keys
In this amusing tale, Kylee Goodwin narrates the comical ordeal of her mum losing her keys yet again. The family embarks on a frantic search through various rooms, only for the keys to be found hanging safely on their hook by Dad in the end. A lighthearted story of everyday mishaps and the relief of
0 views • 13 slides
Advanced SQL Concepts and Queries Overview
Today's lecture highlights advanced SQL topics such as multi-table queries, set operators, joins, primary keys, foreign keys, and more. The session covers practical activities and fundamental concepts in database management. Explore the nuances of SQL semantics and understand the importance of keys
0 views • 55 slides
Understanding Dichotomous Keys in Biology
A dichotomous key is an essential tool for biologists to identify plants and animals based on specific characteristics. This key methodically presents pairs of contrasting descriptions to guide the user towards accurate identification. Through visual and descriptive examples, the concept of dichotom
0 views • 10 slides
Understanding Database Constraints, Keys, and Triggers
Explore the concepts of constraints, foreign keys, local and global constraints, and triggers in the context of database management systems. Delve into topics such as types of constraints, keys, and expressing foreign keys with examples. Enhance your understanding of database integrity and data rela
0 views • 40 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
Understanding Computer Input Devices and Keystrokes
The system box of a computer contains essential components like the CPU, motherboard, and memory chips. Character keys, action keys, and application-dependent keys on a keyboard serve different functions, from typing letters to performing actions. Key combinations and shortcuts provide efficient way
0 views • 10 slides