Introduction to Biotechnology in Pharmaceutical Sciences: A Comprehensive Overview by Swarnakshi Upadhyay
Biotechnology in pharmaceutical sciences encompasses the application of scientific and engineering principles to utilize biological agents for various services. It includes molecular biology for production of pharmaceuticals like antibiotics, proteins, and enzymes, as well as large-scale production
0 views • 9 slides
Comprehensive Overview of ABE Lab Manual and Foundations of Biotech Package
The ABE Lab Manual, authored by Doreen Osgood, MS, PhD, is a comprehensive resource for biotechnology education, including sequences like Genetic Engineering and Colony PCR. The manual includes teacher and student guides, along with related resources like PowerPoint presentations and lists of labora
1 views • 5 slides
QuickBooks License Error After Cloning A Comprehensive Guide
If you have encountered a license error in QuickBooks after cloning your system, you are not alone. This issue can cause disruptions and inconvenience in your workflow. But don't worry, we have a comprehensive guide that provides effective solutions to help you troubleshoot and resolve this problem
6 views • 3 slides
Exploring Ethical Issues in Animal Cloning and its History
Animal cloning involves creating genetically identical replicas of cells or organisms, with advancements being made in therapeutic cloning and gene cloning. The history of animal cloning dates back to the successful cloning of sheep like Dolly in 1996. The cloning procedure involves collecting cells
0 views • 21 slides
QuickBooks License Error After Cloning_ Causes and Solutions
QuickBooks License Error after cloning typically occurs due to the cloning process duplicating the unique system identifier used by QuickBooks to verify licenses. This results in QuickBooks not recognizing the cloned system as legitimate, leading to the license error.
3 views • 5 slides
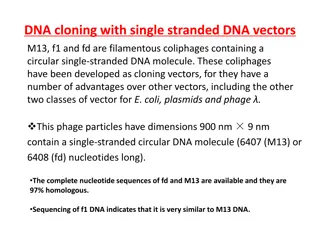
Understanding DNA Cloning with Filamentous Coliphages
Filamentous coliphages M13, f1, and fd are utilized as cloning vectors due to their circular single-stranded DNA molecules and advantages over other vectors. These phages have dimensions of 900 nm x 9 nm and infect bacteria through F pili, releasing up to 1000 phage particles per cell per generation
0 views • 17 slides
Understanding DNA Ligation Techniques for Molecular Biology Applications
DNA ligation involves joining DNA fragments to vectors to create new DNA or plasmids. Methods include DNA ligase, T4 ligase, and terminal deoxynucleotidyl transferase. Linkers and adaptors play a key role in DNA cloning experiments by generating sticky ends for DNA cloning. The use of adaptors allow
1 views • 13 slides
Understanding Recombinant DNA Technology and Cloning Vectors in Genetics Engineering
Exploring the fundamentals of recombinant DNA technology and gene cloning, this content delves into the key concepts and basic steps involved. It covers various cloning vectors such as plasmids, bacteriophages, and artificial chromosomes, highlighting their common features and applications in geneti
0 views • 12 slides
Understanding Keys and SQL Commands in Database Management Systems
Explore different types of keys used in databases such as Candidate Key, Super Key, Composite Key, Primary Key, Alternate Key, Unique Key, and Foreign Key. Learn about SQL commands categorized into DDL, DML, and DCL and various query languages like Create, Alter, Rename, Drop, Comment, Truncate, Ins
0 views • 11 slides
Understanding Genetics: Mutations, Chromosomal Aberrations, and Genetic Engineering
Genetic mutations can be harmless, harmful, or beneficial, leading to variations within a species. Examples of gene mutations and chromosomal aberrations, like Trisomy 21, illustrate genetic abnormalities. The increase in Down Syndrome cases with maternal age highlights a maternal age effect. Geneti
0 views • 17 slides
Human Insulin Gene Expression and Production
The process of cloning and expressing the human insulin gene has revolutionized the production of insulin for treating diabetes. By using genetically engineered bacteria, the human insulin gene is inserted, expressed, and purified to create insulin for therapeutic use. This innovation has overcome c
0 views • 20 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
Developing with Contiki-NG in Code Composer Studio: Step Debugging Guide
Conveniently set up your software development environment for Contiki-NG in Code Composer Studio with step-by-step instructions including cloning the repository, creating a project, adding path variables, adjusting environment variables, and configuring builder settings.
0 views • 13 slides
Streamlining Image Deployment with Windows Deployment Service and MDT
Utilizing Windows Deployment Service and Microsoft Deployment Toolkit (MDT) can enhance the efficiency of large-scale Windows operating system deployments. The transition from sector-based cloning to file-based imaging brings benefits like reduced storage requirements, increased automation, and flex
0 views • 20 slides
Genetic Manipulation in Environmental Biotechnology
Genetic manipulation strategies in environmental biotechnology involve techniques like gene splicing and molecular cloning to modify genes directly. These methods have various applications such as isolating genes, producing specific molecules, improving biochemical production, creating organisms wit
0 views • 20 slides
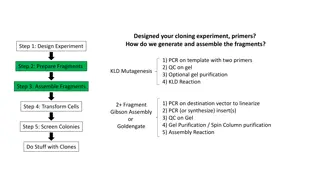
Cloning Experiment Overview and Procedures
The cloning experiment involves designing primers, generating and assembling fragments through PCR, gel purification, and KLD reaction. Further steps include fragment preparation, assembly, cell transformation, colony screening, and working with clones. Detailed instructions for KLD mutagenesis, QC
0 views • 11 slides
Understanding Cloning Vectors and Recombinant DNA Technology
Genetics Engineering Lecture-2 delves into the concept and basic steps of recombinant DNA technology and gene cloning, highlighting different types of cloning vectors like plasmids, bacteriophages, bacterial artificial chromosomes, yeast artificial chromosomes, and mammalian artificial chromosomes.
1 views • 13 slides
Understanding Recombinant DNA Technology and Gene Cloning
Recombinant DNA technology is crucial for developing new vaccines and pharmaceuticals by combining genetic material from various sources to create unique sequences. Techniques like transformation, non-bacterial transformation, and phage introduction are used to make recombinant DNA. Tools like enzym
3 views • 15 slides
Comprehensive Overview of Git and GitHub for CS 4411 Spring 2020
This detailed content provides an in-depth exploration of Git and GitHub for the CS 4411 Spring 2020 semester. It covers Git basics, commands, dealing with conflicts and merges, understanding branches, recovering from errors, making commits, utilizing remote repositories, and collaborating via GitHu
0 views • 40 slides
Understanding Genetic Engineering and Selective Breeding
Genetic engineering involves changing the DNA in living organisms to create new traits, resulting in genetically modified organisms (GMOs). Techniques include artificial selection, cloning, gene splicing, and gel electrophoresis. Selective breeding is a form of artificial selection where animals wit
4 views • 37 slides
Exploring Prenatal Development and Newborn Reflexes
Delve into the wonders of prenatal development from conception to birth, including the societal implications of delayed childbearing and ethical considerations like human cloning. Discover the stages of embryonic growth, the role of the placenta, and the impact of teratogens. Explore reflexes in com
0 views • 10 slides
Cellular Network Security Threats and Solutions
This article delves into the security aspects of cellular networks, focusing on threats such as charging fraud, unauthorized use, handset cloning, voice interception, location tracking, and network service disruptions. It also explores the security architecture involving Home Location Register (HLR)
0 views • 28 slides
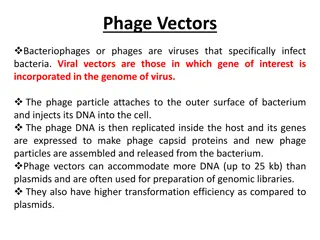
Understanding Phage Vectors in Genetic Engineering
Phage vectors, utilized in genetic engineering, are bacteriophages capable of incorporating genes of interest into their genome. They have a higher DNA capacity compared to plasmids, making them ideal for creating genomic libraries. Bacteriophages like Lambda and M13 are commonly used for cloning ve
0 views • 17 slides
Understanding Recombinant DNA and Gene Cloning
Recombinant DNA is artificially created by combining DNA from multiple sources into a single molecule. This process involves treating DNA with restriction endonucleases, such as BamHI, which cut at specific sites, resulting in sticky ends that can base pair with complementary DNA molecules. DNA liga
0 views • 33 slides
EPC RFID Tag Security Weaknesses and Defenses: Passport Cards, Enhanced Driver's Licenses, and Beyond
Explore the vulnerabilities in EPC RFID tag security related to passport cards, enhanced driver's licenses (EDLs), and more. Learn about cloning risks, defensive strategies, and experimental evaluations of security measures for these identification documents.
0 views • 22 slides
Cloning Other Genes and Recombinant DNA Technology
The recombinant vector with a kanamycin resistance gene can be used to clone other genes by inserting human DNA fragments and selecting transformed E. coli cells. This technique has enabled the production of various human proteins for therapeutic purposes, such as insulin, growth hormones, and clot-
0 views • 6 slides
Overview of EOSC-hub Distributed Operations and Plans
This content provides an overview of the distributed operations and plans of EOSC-hub, detailing key aspects such as the funding received, RCauth operations, high availability setup, tasks overview, changes due to lockdown, and work-from-home adjustments. It outlines the challenges and progress in i
0 views • 17 slides
Next-Gen Context-Aware Computing Solutions: Challenges and Innovations
High data rate sensors and compute-intensive tasks put immense pressure on mobile devices, leading to the need for innovative solutions like cloudlets and stateful cloning of VMs. Swift actions such as fetching state on-demand, utilizing multicasting for parallelism, and optimizing resource usage ar
0 views • 12 slides
Proximity Card Security_ Best Practices for Preventing Cloning and Tampering
Discover effective strategies to prevent cloning and tampering of proximity cards, ensuring your security remains intact.
1 views • 5 slides
Decoding Cloning Extinct Animals: Pros, Cons, and Methods
Delve into the fascinating world of cloning extinct animals presented by Jacob Engen and Joe Bertolini. Explore the reasons for and against reviving these creatures, alongside the challenges and methods involved in the cloning process, including the ethical implications and potential environmental i
0 views • 5 slides
Understanding Recombinant DNA Technology and Plasmid Vectors
Explore the world of recombinant DNA technology through the utilization of plasmids as vectors for gene cloning. Learn about techniques like insertional inactivation and the characteristics of common plasmid vectors such as pBR322. Discover the intricacies of genetic manipulation in bacterial origin
0 views • 26 slides
Basics of Java Arrays and Array Manipulation
Learn about the fundamentals of Java arrays, including initialization, literals, indexing, and the special value of null. Explore how arrays function as reference types and how array cloning can be used to create shallow copies. Understand the implications of passing arrays to methods and how change
0 views • 44 slides
Applications of Transgenic Animals in Biotechnology and Cloning
Cloning in animals offers the advantage of indefinite duplication of elite genotypes without the genetic risks of meiosis. Transgenic animals, genetically modified to carry foreign genes, play a crucial role in genetic research and the development of livestock with desired traits. Methods like DNA m
0 views • 13 slides
Key Exchange and Public-Key Cryptography Overview
Explore the challenges of key management, the use of trusted third parties in generating shared keys, the limitations of toy protocols in secure key exchange, and the evolution of public-key cryptography techniques like Merkle Puzzles, Diffie-Hellman, and RSA. Learn how to achieve secure key exchang
0 views • 36 slides
The Fascinating World of Cloning: From Dolly the Sheep to Genetic Replication Techniques
Cloning is the process of creating genetically identical organisms, either naturally or artificially. This article delves into the various techniques of cloning such as gene cloning, reproductive cloning, and therapeutic cloning. It also highlights the groundbreaking story of Dolly the sheep, the fi
0 views • 17 slides
Understanding CIDAR MoClo Labs in Synthetic Biology Teaching
In CIDAR MoClo Labs, students learn DNA engineering concepts, construction of plasmids, and analysis of fluorescent data. Background knowledge of DNA, proteins, bacterial plasmids, and the LacZ method is required. Skills include pipetting, DNA measurement, bacterial transformation, and plate reader
0 views • 19 slides
Cloning the Cstps-1 Gene from Citrus sinensis for Valencene Production
In this project, the Cstps-1 gene from Citrus sinensis is being cloned to produce the enzyme Citrus Valencene Synthase (CVS) responsible for generating the fragrant valencene compound. The process involves DNA isolation from a Valencia orange, gene amplification, vector transformation, and testing f
0 views • 8 slides
Aggressive Cloning of Jobs for Effective Straggler Mitigation
Small jobs are increasingly important in big data processing systems, but are particularly sensitive to stragglers. Various straggler mitigation techniques like blacklisting and speculation have limitations when it comes to small jobs. A proposed solution is the proactive cloning of jobs to probabil
0 views • 20 slides
Beginner's Guide to DPDK and OVS-DPDK
This presentation by Mark Gray provides a beginner-friendly introduction to DPDK and OVS-DPDK, targeted at those who are new to these technologies. It covers important disclaimers, methodology, software versions, and practical steps such as cloning the DPDK repository, checking out specific versions
0 views • 88 slides
Fast File Clone in ZFS Design Proposal Overview
This document details a proposal for implementing fast file clone functionality in ZFS, allowing for nearly instant file copying through referencing. The motivation behind this proposal includes support for VMware VAAI, NAS Full File Clone, and Fast File Clone to save memory and disk space. The prop
0 views • 29 slides