Language Teaching Techniques: GTM, Direct Method & Audio-Lingual Method
Explore the Grammar-Translation Method, Direct Method, and Audio-Lingual Method in language teaching. Understand principles, objectives, and methodologies with insights into language learning approaches. Enhance teaching skills and foster effective communication in language education.
3 views • 82 slides
Understanding AARCH64 Linux Kernel Memory Management
Explore the confidential and proprietary details of AARCH64 Linux kernel memory mapping, virtual memory layout, variable configurations, DDR memory layout, and memory allocation techniques. Get insights into the allocation of physically contiguous memory using Continuous Memory Allocator (CMA) integ
0 views • 18 slides
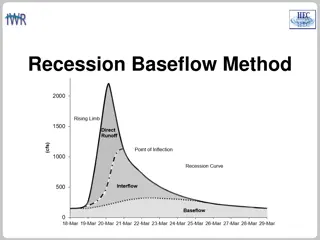
Understanding the Recession Baseflow Method in Hydrology
Recession Baseflow Method is a technique used in hydrology to model hydrographs' recession curve. This method involves parameters like Initial Discharge, Recession Constant, and Threshold for baseflow. By analyzing different recession constants and threshold types such as Ratio to Peak, one can effe
0 views • 8 slides
Understanding the Scientific Method: A Logical Framework for Problem-Solving
The Scientific Method is a systematic approach used to solve problems and seek answers in a logical step-by-step manner. By following key steps such as stating the problem, researching, forming a hypothesis, testing, analyzing data, and drawing conclusions, this method helps clarify uncertainties an
1 views • 18 slides
Introduction to Six Thinking Hats Method for Effective Group Decision Making
Explore the Six Thinking Hats method, a powerful tool for facilitating group discussions and decision-making processes. This method encourages participants to approach problems from various perspectives represented by different colored 'hats'. By simplifying thinking and fostering constructive dialo
1 views • 24 slides
Understanding Corn Growth Stages: Leaf Staging Methods and Considerations
Various leaf staging methods, including the Leaf Collar Method and Droopy Leaf Method, are used to identify corn plant growth stages. The Leaf Collar Method involves counting leaves with visible collars, while the Droopy Leaf Method considers leaves at least 40-50% exposed from the whorl. Factors li
0 views • 9 slides
Understanding Different Emasculation Techniques in Plant Breeding
Learn about the significance of emasculation in plant breeding to prevent self-pollination and facilitate controlled pollination. Explore various methods such as hand emasculation, forced open method, clipping method, emasculation with hot/cold water, alcohol, suction method, chemical emasculation,
2 views • 10 slides
Simple Average Method in Cost Accounting
Simple Average Method, introduced by M. Vijayasekaram, is a technique used for inventory valuation and delivery cost calculation. It involves calculating the average unit cost by multiplying the total unit costs with the number of receiving instances. This method simplifies calculations and reduces
2 views • 5 slides
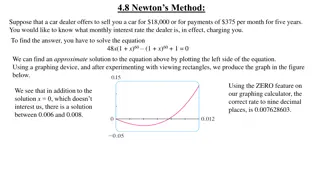
Understanding Newton's Method for Solving Equations
Newton's Method, also known as the Newton-Raphson method, is a powerful tool for approximating roots of equations. By iteratively improving initial guesses using tangent lines, this method converges towards accurate solutions. This method plays a crucial role in modern calculators and computers for
0 views • 12 slides
Understanding Generalized Discriminant Analysis (GDA) in Pattern Recognition
Generalized Discriminant Analysis (GDA) is a nonlinear form of Linear Discriminant Analysis (LDA) that utilizes kernel methods to find discriminatory features for optimal class separability. LDA aims to maximize the between-class covariance matrix while minimizing the within-class covariance matrix.
2 views • 17 slides
Understanding the Conjugate Beam Method in Structural Analysis
The Conjugate Beam Method is a powerful technique in structural engineering, derived from moment-area theorems and statical procedures. By applying an equivalent load magnitude to the beam, the method allows for the analysis of deflections and rotations in a more straightforward manner. This article
1 views • 11 slides
Understanding Roots of Equations in Engineering: Methods and Techniques
Roots of equations are values of x where f(x) = 0. This chapter explores various techniques to find roots, such as graphical methods, bisection method, false position method, fixed-point iteration, Newton-Raphson method, and secant method. Graphical techniques provide rough estimates, while numerica
0 views • 13 slides
Binary Basic Block Similarity Metric Method in Cross-Instruction Set Architecture
The similarity metric method for binary basic blocks is crucial in various applications like malware classification, vulnerability detection, and authorship analysis. This method involves two steps: sub-ldr operations and similarity score calculation. Different methods, both manual and automatic, ha
0 views • 20 slides
Exploring the Audio-Lingual Method in Language Teaching
The Audio-Lingual Method is an oral-based approach that focuses on drilling students in grammatical sentence patterns through behavioral psychology principles. This method, also known as the Michigan Method, emphasizes habit formation and uses techniques like dialogues, repetition drills, and role-p
1 views • 16 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Understanding the Kinetics of Fast Reactions in Chemistry
Kinetic methods involve measuring analytical signals under dynamic conditions to study fast reactions in chemistry. This study explores the various methods used, such as Flow Method and Stopped Flow Method, to determine reaction rates accurately. Advantages of the Stopped Flow Method over Continuous
0 views • 18 slides
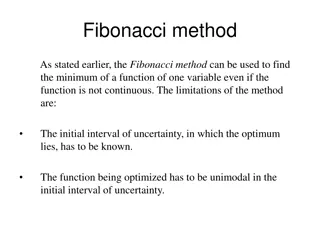
Understanding the Fibonacci Method for Function Optimization
The Fibonacci method offers a systematic approach to finding the minimum of a function even if it's not continuous. By utilizing a sequence of Fibonacci numbers, this method helps in narrowing down the interval of uncertainty to determine the optimal solution through a series of experiments. Despite
1 views • 19 slides
Understanding Kernel Tricks in Machine Learning
Kernel tricks in machine learning involve transforming inputs into higher-dimensional spaces to make linear models work for nonlinear data. Kernels can be applied to various algorithms like SVM, ridge regression, and more, allowing for better model performance with complex datasets.
0 views • 15 slides
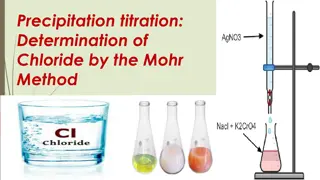
Determination of Chloride by Mohr Method
Precipitation titration is a volumetric method used for determining chloride ions. Mohr's method involves reacting alkaline or alkaline earth chlorides with silver nitrate in the presence of a potassium chromate indicator. The endpoint of the titration is signaled by the appearance of red silver chr
0 views • 9 slides
Fundamentals of Operating Systems Explained
Explore the core concepts of operating systems, including kernel-userspace interactions, system calls, context switching, and virtual memory management. Delve into x86 assembly for system calls, hardware interrupts, and the flow of control during system call invocations. Gain insights into key compo
7 views • 19 slides
Determination of Dipole Moment in Chemistry
The determination of dipole moment in chemistry involves methods such as the Temperature Method (Vapour Density Method) and Refractivity Method. These methods rely on measuring various parameters like dielectric constants and polarizations at different temperatures to calculate the dipole moment of
1 views • 15 slides
Accounting Entries in Hire Purchase System for Credit Purchase with Interest Method
In the Credit Purchase with Interest Method of Hire Purchase System, assets acquired on hire purchase basis are treated as acquired on outright credit basis with interest. This method involves initial entries for recording the asset acquisition, down payments, interest on outstanding balance, instal
0 views • 10 slides
Understanding Singular Value Decomposition and the Conjugate Gradient Method
Singular Value Decomposition (SVD) is a powerful method that decomposes a matrix into orthogonal matrices and diagonal matrices. It helps in understanding the range, rank, nullity, and goal of matrix transformations. The method involves decomposing a matrix into basis vectors that span its range, id
0 views • 21 slides
Understanding Scatter Diagram Method for Correlation Analysis
Scatter Diagram Method is a simple and effective way to study the correlation between two variables. By plotting data points on a graph, it helps determine the degree of correlation between the variables. Perfect positive and negative correlations, as well as high and low degrees of correlation, can
0 views • 11 slides
Subnational Population Projections Using Ratio Method: Advantages and Variations
The ratio method, particularly the constant share and shift-share variations, is commonly used for projecting small area populations when data for the component method are lacking. It involves holding the smaller area's share of the parent population constant or allowing for changes over time. Care
1 views • 12 slides
Measurement of Flow Velocity on Frozen and Non-Frozen Slopes of Black Soil Using Leading Edge Method
This study presented a detailed methodology for measuring flow velocity on frozen and non-frozen slopes of black soil, focusing on the Leading Edge method. The significance of shallow water flow velocity in soil erosion processes was emphasized. Various methods for measuring flow velocity were compa
0 views • 23 slides
Improving the Reliability of Commodity Operating Systems
This research paper discusses the challenges and solutions in enhancing the reliability of commodity operating systems by addressing system failures caused by kernel extensions. The Nooks approach isolates extensions within protection domains, allowing them to reside in the kernel address space with
0 views • 40 slides
Raspberry Pi 2 Boot Process Overview
Raspberry Pi 2's boot process involves a series of stages initiated by the GPU, loading essential firmware and enabling hardware components gradually, leading to the activation of the CPU and the kernel's entry point. The system transitions through various low-level processes before reaching a stabl
0 views • 9 slides
Multi-phase System Call Filtering for Container Security Enhancement
This tutorial discusses the importance of multi-phase system call filtering for reducing the attack surface of containers. It covers the benefits of containerization, OS virtualization, and the differences between OS and hardware virtualization. The tutorial emphasizes the need to reduce the kernel
0 views • 32 slides
Understanding User Mode, Kernel Mode, Interrupts, and System Calls in Computer Architecture
In modern computers following Von Newman Architecture, programs and data are stored in RAM. The CPU, RAM, ROM, and devices communicate via address and data buses. The system operates in both kernel and user modes, where kernel mode allows full system control, while user mode restricts access for sec
0 views • 29 slides
Tracing Network Packets in Linux Kernel with eBPF
This presentation discusses the challenges of troubleshooting modern networking systems and proposes a solution using eBPF technology to trace the path of network packets in the Linux kernel. The goal is to develop a tool that provides detailed information about how network packets are processed in
0 views • 16 slides
Analyzing Multimodality in Density Distributions Using JMP Scripting
Explore variability sources hidden in density distributions through JMP scripting. The analysis focuses on identifying and filtering distribution modes in semiconductor fab electrical measurements using kernel estimation and empirical rules. Antonio D'Angelo and Felice Russo from Lfoundry S.r.l. Ita
0 views • 6 slides
Understanding Remote Procedure Call (RPC) in Different Kernel Environments
Communication through Remote Procedure Call (RPC) plays a crucial role in facilitating seamless interaction between server and client processes, whether on the same machine or across different kernels. This technology streamlines local and cross-domain communication, optimizing performance while ens
0 views • 9 slides
Overview of the Pintos Instructional Operating System Kernel Project
Description of the Pintos Operating System Kernel project, including its use in educational settings at institutions such as Stanford University and Virginia Tech. The project aims to provide students with a hands-on experience in OS design, focusing on the internal workings of the kernel. Pintos fe
0 views • 33 slides
Understanding Pipes in Process Communication
Pipes in process communication allow for high-throughput data transfer between parent and child processes. The kernel creates a communication stream through file descriptors, enabling one process to send data to another. Processes can use pipes for efficient inter-process communication, with the ker
1 views • 15 slides
Understanding the Shoe Lace Method for Finding Polygon Areas
The Shoe Lace Method is a mathematical process used to determine the area of any polygon by employing coordinate geometry. By following specific steps, including organizing coordinates, multiplying diagonally, and adding columns in a certain manner, the method allows for a straightforward calculatio
0 views • 8 slides
Understanding User and Kernel Modes in Operating Systems
The content provided discusses various aspects of user and kernel modes in operating systems through a set of true/false questions related to user programs, CPU interrupts, heap management, and process behavior in different modes. It touches on the role of the kernel in managing virtual memory, hand
0 views • 10 slides
Hyper-Parameter Tuning for Graph Kernels via Multiple Kernel Learning
This research focuses on hyper-parameter tuning for graph kernels using Multiple Kernel Learning, emphasizing the importance of kernel methods in learning on structured data like graphs. It explores techniques applicable to various domains and discusses different graph kernels and their sub-structur
0 views • 20 slides
Overview of UNIX and Linux Operating Systems
The UNIX brand encompasses a range of powerful multitasking, multiuser operating systems used by various organizations to develop IT technologies. UNIX internals consist of kernel space and user space, with programs accessing system services rather than hardware directly. The Unix filesystem is a ke
0 views • 36 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides