Adaptive Tree-based Convergecast Protocol
Adaptive tree-based protocol for managing overlay networks in heterogeneous networks. It proposes improvements to the existing Tree-Based Convergecast Routing (TBCR) protocol by considering additional parameters such as RTT, power consumption, link stability, and link mobility to optimize routing de
32 views • 12 slides
Protecting Your WiFi with an Internet Kill Switch
The possibility of internet outages is quite real in a time when connectivity is essential. The phrase \"internet kill switch\" has gained popularity to describe how governments or other bad actors can restrict or stop people's access to the internet, putting people's lives and businesses at risk of
0 views • 1 slides
Protecting Your WiFi with an Internet Kill Switch
The possibility of internet outages is quite real in a time when connectivity is essential. The phrase \"internet kill switch\" has gained popularity to describe how governments or other bad actors can restrict or stop people's access to the internet, putting people's lives and businesses at risk of
0 views • 1 slides
Tektronix Technologies- Internet of Things (IOT) Across UAE
As our use of Internet of Things (IoT) Applications increases rapidly, so does its associated security risks. With technology quickly developing in our society and daily lives, the Internet of Things (IoT) is rapidly becoming part of everyday life. Tektronix Technologies are specialists in IoT secur
3 views • 1 slides
Hotel Internet Booking Engine
Discover Travelopro's cutting-edge hotel internet booking engine. Elevate your hospitality experience with our tailored services, designed for hotels of all sizes. A hotel Internet booking engine is a software tool on the hotel's own website to ensure that guests can easily book directly with the ho
3 views • 15 slides
OSI Model and TCP/IP Protocol Suite
Explore the concept of layering in data communication, comparing the OSI model and TCP/IP protocol suite. Learn about protocol layers, protocol hierarchies, and the functionality of each layer in these models. Discover the interrelationships between layers and the evolution from OSI to TCP/IP.
6 views • 57 slides
The Basics of the Internet
The internet is a vast network of interconnected computer networks worldwide that use the standard Internet protocol. It has evolved through history from the development of electronic computers in the 1950s to its current state where various entities own different parts of the infrastructure. Differ
1 views • 24 slides
London Homeless Coalition (LHC) Death Communication Protocol
In 2014, the Memorial Committee of the London Homeless Coalition (LHC) established the Death Communication Protocol to acknowledge, share, and address the loss of individuals experiencing homelessness. The protocol aims to inform partnering organizations of confirmed or unconfirmed deaths, support g
2 views • 12 slides
Mobile Computing and TCP/IP Protocol Suite
Mobile computing is crucial for continuous internet connectivity regardless of physical location. The TCP/IP protocol suite, consisting of Transmission Control Protocol (TCP) and Internet Protocol (IP), forms the backbone of internet infrastructure. IP addressing and mobility challenges are addresse
2 views • 51 slides
OSI Model and TCP/IP Protocol Suite in Computer Networking
This chapter explores the OSI model and TCP/IP protocol suite, delving into protocol layers, addressing mechanisms, and network components. It highlights the interface between layers, functions of each layer in the OSI model, and compares TCP/IP protocol suite layers with OSI model layers. The discu
0 views • 30 slides
Evolution of Internet Technology in Tourism: A Comprehensive Study
Exploring the impact of the Internet on tourism, this study delves into topics such as historical evolution, Internet usage by travelers and organizations, search engine optimization, and web development for successful tourism sites. Key concepts like ISPs, servers, domains, and eCommerce are discus
1 views • 23 slides
MAAP Protocol Overview in IEEE 1722: Address Acquisition and Message Format
The MAAP (Multicast Address Acquisition Protocol) is defined in IEEE 1722 for time-sensitive applications in bridged local area networks. It involves acquiring multicast addresses through claiming, probing, and defending messages. MAAP enables dynamic allocation of addresses and defending against co
1 views • 8 slides
IEEE 802.11-20/1761r1 Ranging Protocol for 11bd
This document outlines the ranging protocol proposed for IEEE 802.11-20/1761r1, focusing on RTT-based ranging leveraging multi-channel operation. By integrating the 11az ranging protocol, it enables flexible and low-overhead application in 11bd for improved accuracy in ITS bands. The protocol includ
1 views • 13 slides
Evolution of Internet Protocol: From IPv4 to IPv6
The evolution of Internet Protocol (IP) from IPv4 to IPv6 has been crucial for adapting to new technologies and addressing specific networking challenges. IPv6 offers a 128-bit address space, improved header format, extensibility, and support for a wide range of services including video, voice, and
0 views • 23 slides
EIGRP: A Comprehensive Overview
Enhanced Interior Gateway Routing Protocol (EIGRP) is a dynamic routing protocol providing various advantages to network administrators. It is a classless routing protocol supporting VLSM and is considered an Interior Gateway Protocol (IGP). EIGRP uses advanced distance vector routing and is known f
1 views • 5 slides
Internet Basics and Web Browsers
This content covers the basics of the Internet and World Wide Web, including the differences between the two, the functions of web browsers, components of Internet Explorer, parts of the World Wide Web, conducting effective Internet searches, understanding search results, evaluating websites, and di
0 views • 49 slides
SFTP Server Functionality with ACS 5.x by Mohammad Azharuddin AAA Team
SFTP (SSH File Transfer Protocol) is a secure network protocol for file access, transfer, and management over reliable data streams. It enhances security by extending the SSH protocol and can be implemented using a reliable 8-bit byte stream protocol. SFTP commands are sent as 4 ASCII letters follow
4 views • 23 slides
Enhanced Family Court Police Disclosure Protocol for 2024
The 2024 Family Court Police Disclosure Protocol addresses key issues identified in the 2013 protocol, emphasizing timely and proportionate requests for material. Changes include a new checklist for the judiciary, guidance notes, and revised processes for litigants in person. The protocol provides c
1 views • 19 slides
Essential Elements of Clinical Trial Protocols
Understanding the key components of a clinical trial research protocol is essential for conducting successful studies. This includes identifying session objectives, discussing trial protocol contents, exploring observational study elements, and learning about reporting guidelines. Study objectives f
2 views • 25 slides
Internet Society 2024 Action Plan Overview
In 2024, the Internet Society aims to defend the Internet, enhance its resilience, scale impact through mobilization, and ensure organizational sustainability. Initiatives include advocating for Internet rights, building infrastructure, mobilizing communities, and shaping Internet policies.
2 views • 19 slides
Trends in Internet Governance and National Sovereignization in Russia
The discussion revolves around the trend of aligning cyberspace with national borders, emphasizing national security concerns in the context of internet governance in Russia. It covers topics such as reframing cybersecurity as a national security issue, militarization of cyberspace, territorializati
0 views • 11 slides
Coping Behavior Variances in Adolescents with Varying Degrees of Internet Addiction
Adolescence is a critical period for personal development where coping behavior plays a significant role. This study by Irina Petrochenko focuses on exploring coping behavior features in adolescents with different levels of internet addiction. Research methods involved testing 75 individuals aged 14
0 views • 10 slides
Internet Overview in the Arab Region by ARISPA
The Arab Internet & Telecom Union (ARISPA) provides a detailed overview of internet penetration rates in the Arab region, focusing on global and regional comparisons, as well as the future IPv4 situation. Founded in 2006, ARISPA works under the Arab Economic Union Council, with 20 members representi
0 views • 17 slides
Enhancing Internet Telephony Quality Through Predictive Relay Selection
Examining the quality of Internet telephony in relation to network performance, this research explores the use of Managed Overlay to improve call quality for services like Skype. Analysis of 430 million Skype calls reveals that a significant portion experience poor network performance, emphasizing t
1 views • 26 slides
The Evolution of TCP and Internet Traffic Trends
The Internet landscape has seen significant changes with over 90% of traffic using encrypted payloads, a majority originating from cloud servers, and a notable shift towards QUIC protocol. The role of TCP as a reliable transport protocol is explored, highlighting its adaptive streaming capabilities
1 views • 38 slides
Sync HotStuff: Practical Synchronous State Machine Replication
Sync HotStuff is a practical synchronous protocol that tolerates Byzantine replicas and handles weaker synchrony models. It overcomes issues of requiring a large number of rounds and lock-step execution. The protocol ensures safety by committing blocks and guarantees liveness by continuing to commit
0 views • 15 slides
BGP Basics and Routing Security
Border Gateway Protocol (BGP) is a crucial protocol used by routers to exchange routing information and make routing decisions. This protocol plays a key role in how the Internet functions, with over 76,000 Autonomous Systems and millions of routes being advertised. Research and Education (R&E) netw
0 views • 33 slides
Evolved Addressing and Forwarding in Information-Centric Networks
The content discusses Evolved Addressing and Forwarding in Information-Centric Networks, focusing on an accountable Internet protocol (AIP) that addresses vulnerabilities at the IP level, such as source spoofing, DoS attacks, and route hijacking. AIP utilizes a hierarchy of self-certifying addresses
0 views • 16 slides
Insights into Computer and Internet Usage in Schools
This data collection provides statistics on the usage of computer units and internet connections in schools, frequency of internet browsing, strength of mobile phone and broadband signals, and the percentage of internet users per week. It gives an overview of the technology environment in educationa
1 views • 16 slides
The Basics of the Internet and World Wide Web
The internet, a vast network of networks, connects billions of users globally. Learn how the internet operates, who owns it, and the distinction between the internet and the World Wide Web. Discover the origins of the WWW and how web pages function to deliver information through browsers. Explore th
1 views • 29 slides
Internet Safety Guide for Children
In this animated presentation, children are introduced to the Internet, its uses, and safety measures. The content explains the concept of the Internet, its purpose, and highlights the importance of adult supervision while browsing. Tips on safe Internet usage and what to do when encountering unfami
0 views • 14 slides
The Internet: A Comprehensive Overview
The internet is a globally connected network system that allows worldwide communication and access to data resources. It is governed by agencies like IANA, and connecting a computer to the internet enables access to information, communication globally, and more. The internet is a global wide area ne
1 views • 17 slides
Protocol Deviations in Clinical Trials
Protocol deviations are expected occurrences in clinical trials that may arise from site or participant actions. It is crucial for research teams to identify, report, and learn from these deviations to ensure the integrity and safety of the study. Mechanisms for identifying and reporting deviations,
0 views • 16 slides
Advancing Internet Measurement Research: IMR Program Overview
The Internet Measurement Research (IMR) program aims to enhance Internet measurement methodologies, tools, and infrastructure for a comprehensive understanding of wired and wireless networks. It promotes the development of new data collection methods, measurement tools, and related infrastructure. T
1 views • 23 slides
OSI Model and TCP/IP Protocol Suite in Computer Networking
This content delves into the OSI model and TCP/IP protocol suite, highlighting the protocol layers, addressing mechanisms, and communication scenarios. It explores the functions of each layer, the interface between layers, and compares the TCP/IP layers with the OSI model. Through examples and illus
0 views • 46 slides
Regional Internet Registries (RIRs) and NRO in Internet Governance
Regional Internet Registries (RIRs) manage the allocation and registration of Internet number resources such as IP addresses and autonomous system numbers. They operate as not-for-profit organizations providing core services like resource distribution, maintaining directories, and facilitating polic
0 views • 11 slides
Protocol Layers in Computer Networking
Explore the concept of protocol layers in computer networks for organizing the structure of complex systems. Learn about the organization of network functionality similar to air travel processes and the benefits of layering in dealing with complex systems. Delve into the Internet Protocol Stack, hig
0 views • 29 slides
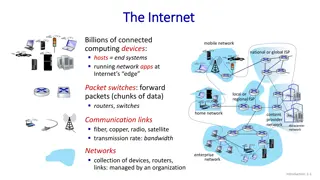
The Basics of the Internet and Network Structure
Billions of connected computing devices make up the Internet, with hosts, packet switches, routers, and communication links facilitating data transmission. The Internet functions as a network of networks, enabling various services like web browsing, video streaming, and online communication. Differe
0 views • 17 slides
Seeking a General-Purpose CCSDS Link Layer Protocol: Next-Generation Data Link Protocol (NGDLP)
This document discusses the proposed Universal Frame Format for a next-generation data link protocol, focusing on major questions about transfer frames, Protocol Link Transmission Unit (PLTU), and Universal Transfer Frame Structure. It explores topics such as frame formats, telemetry transfer frames
0 views • 24 slides
NT Awake Proning Protocol for Non-Intubated Patients
This protocol outlines the benefits and procedure for prone positioning in non-intubated patients experiencing mild to moderate hypoxemia. It highlights patient eligibility criteria, equipment required, and considerations for nursing care. The protocol emphasizes improving oxygenation by promoting a
0 views • 11 slides