Types Cyber Attacks: Cyber Security Training Workshop
Join our Cyber Security Training Workshop to learn about different types of cyber attacks such as social engineering attacks, DDoS attacks, malware attacks, MitM attacks, APTs, and password attacks. Enhance your knowledge and skills in cyber security.
15 views • 45 slides
Adversarial Machine Learning
Evasion attacks on black-box machine learning models, including query-based attacks, transfer-based attacks, and zero queries attacks. Explore various attack methods and their effectiveness against different defenses.
21 views • 60 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Principles of Cyber Security
Threat actors prioritize targeting networks to exploit vulnerabilities, leading to various attacks such as interception, DNS attacks, and MITM attacks. MITM attacks involve eavesdropping on communications or impersonating parties, with techniques like session replay to steal credentials. Implementin
0 views • 7 slides
Annual Disposal/Injection Well Monitoring Report Workshop Overview
Discover the key aspects of UIC Form UIC-10 and its instructions for reporting, monitoring, inspection, and compliance in the Injection and Mining Division. Learn about the annual submission requirements, community well information, and the Source Fluid Attachment process. Get insights into handling
0 views • 32 slides
Security Breach: Detecting and Exploiting SQL Injection in Contact Groups
Suspect a potential SQL injection in the macros used in Contact groups? Learn how to identify and exploit it through blind SQL injection techniques. Follow step-by-step instructions to execute a payload that alters user data and gain unauthorized access. Stay vigilant and proactively safeguard your
3 views • 27 slides
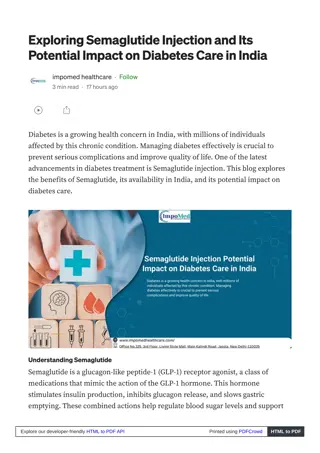
Semaglutide Injection: Pioneering Diabetes Treatment Now in India
Semaglutide Injection is pioneering diabetes treatment in India, offering a groundbreaking solution for patients grappling with the condition. As a cutting-edge GLP-1 receptor agonist, it effectively manages blood sugar levels, facilitates weight loss, and lowers the risk of cardiovascular complicat
0 views • 10 slides
Managing Covid-19 Cyber and Data Protection Risks
Exploring the risks and challenges related to cyber attacks and data protection amidst the Covid-19 pandemic. The agenda covers an overview of cyber-attacks, recent developments, protections against cyber attacks, data protection concerns during lockdown, compliance steps, and employee rights issues
1 views • 35 slides
Mitigation of DMA-based Rowhammer Attacks on ARM
Practical strategies are presented in "GuardION: Practical Mitigation of DMA-based Rowhammer Attacks on ARM" to defend against Rowhammer attacks on ARM architecture. The paper discusses Rowhammer defenses, RAMPAGE attacks on Android OS, and introduces GuardION as a lightweight mitigation approach. I
0 views • 48 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Understanding Denial-of-Service Attacks and Defense Strategies
Denial-of-Service attacks pose a serious threat where attackers flood networks with traffic, leading to system crashes and slowdowns. Explore the impact, expected results, and various categories of DoS attacks such as bandwidth attacks, protocol exceptions, and logic attacks. Learn how to defend aga
0 views • 61 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
An Overview of Evading Anomaly Detection using Variance Injection Attacks on PCA
This presentation discusses evading anomaly detection through variance injection attacks on Principal Component Analysis (PCA) in the context of security. It covers the background of machine learning and PCA, related work, motivation, main ideas, evaluation, conclusion, and future work. The content
1 views • 19 slides
Understanding Control Hijacking Attacks in Software Systems
Control hijacking attacks, such as buffer overflows and format string vulnerabilities, allow attackers to take over a target machine by manipulating application control flow. Knowledge of C functions, system calls, CPU, and OS used is crucial for executing these attacks successfully. This summary pr
1 views • 55 slides
Comprehensive Guide to Semaglutide Injection in India for Diabetes Management
This PDF offers an in-depth look at Semaglutide Injection in India, a powerful GLP-1 receptor agonist in type 2 diabetes treatment. Learn how Semaglutide injection in India improves glycemic control, promotes weight loss, and provides cardiovascular
0 views • 4 slides
Strategies to Protect School Systems from Cyber Attacks
Schools are increasingly becoming targets of cyber attacks, making cybersecurity measures crucial. The article discusses the importance of responding to cyber attacks, creating incident response plans, and being vigilant against interception attacks. It outlines the steps to detect, document, and mi
0 views • 21 slides
Injection Process in Particle Accelerators
The injection process in particle accelerators involves transferring beams efficiently with minimal loss and emittance dilution. It includes on-axis injection onto the reference orbit using septum magnets and fast kickers to maintain beam trajectory accuracy. The design aims to achieve precise beam
0 views • 22 slides
Understanding Common Injection Attacks in Windows and Linux Systems
Dive into the world of injection attacks, exploring the differences between DLL injection in Windows and Linux, the risks of command injection, and the nuances of code injection. Learn about attack scenarios, code examples, and mitigation strategies.
1 views • 104 slides
Insights into Beam Injection Dynamics for Ultra Low Emittance Rings
Delve into the critical aspects of beam injection dynamics for ultra low emittance rings, focusing on top-up injection principles, various injection schemes, and key parameters essential for maximizing beam performance and stability in high-energy physics applications.
0 views • 21 slides
Understanding Beam Lifetime and Injection Considerations at CEPC
Delve into the intricacies of beam lifetime and injection considerations at the CEPC, exploring topics such as beam-gas scattering, quantum lifetime, Touschek lifetime, and injection modes. Discover the crucial factors affecting beam stability and injection efficiency in particle accelerators.
0 views • 20 slides
Overview of Electron/Positron Injector Linac Upgrades at KEK
The recent status of the Electron/Positron Injector Linac at KEK, presented by Kazuro Furukawa, highlights the mission to achieve 40 times higher luminosity in the SuperKEKB collider. The upgrades include low emittance, low energy spread injection beams with higher beam current, new high-current pho
0 views • 23 slides
Longitudinal Top-Up Injection for Small Aperture Storage Rings
In 3rd generation light sources, achieving lower emittances requires smaller physical apertures. Top-up injection is essential for stable photon beam flux, but introduces beam disturbances in transversely on-axis injection chicanes. Various injection schemes like conventional, multipole kicker, swap
0 views • 19 slides
Understanding Plastic Injection Molding for Optical Components
Plastic injection molding is a cost-effective method for mass-producing optical components, offering an economical alternative to glass. This process involves designing molds, considering factors like shrinkage and surface equations, ensuring smooth mold flow, and regulating fluid flow through gates
0 views • 12 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Understanding Network Interference in CS590B/690B Lecture
Delve into the realm of network interference through the CS590B/690B lecture with Phillipa Gill at UMass Amherst. Explore topics such as Internet routing, timing attacks, BGP hijacks, Tor network functionality, relay selection, collusion scenarios, use of guards, web site fingerprinting attacks, tra
0 views • 11 slides
Machine Learning for Cybersecurity Challenges: Addressing Adversarial Attacks and Interpretable Models
In the realm of cybersecurity, the perpetual battle between security analysts and adversaries intensifies with the increasing complexity of cyber attacks. Machine learning (ML) is increasingly utilized to combat these challenges, but vulnerable to adversarial attacks. Investigating defenses against
0 views • 41 slides
Two-Color Ionization Injection Experiment Using CO2 Laser-Plasma Accelerator
This experiment conducted at ATF II focused on generating beams with ultra-low transverse emittance utilizing two-color ionization injection with a CO2 laser-plasma accelerator. The technique involves using a pump laser pulse in circular polarization and an injection laser pulse in linear polarizati
0 views • 15 slides
Intracytoplasmic Sperm Injection (ICSI) Procedure Overview
This detailed guide outlines the step-by-step process of performing an Intracytoplasmic Sperm Injection (ICSI) procedure, including sperm selection, oocyte injection, and fertilization confirmation. It covers essential techniques such as micromanipulation station setup, sperm immobilization, and emb
0 views • 8 slides
Semaglutide 2 mg/3 mL Injection in India for better Diabetes Outcomes
Semaglutide 2 mg\/3 mL injection is transforming diabetes care by helping patients achieve better outcomes, including improved blood sugar control and weight management. Semaglutide Injection in India offers long-lasting effects and reduces the risk
0 views • 1 slides
Comprehensive Guide to Semaglutide Injection in India
This PDF provides an in-depth overview of Semaglutide Injection, highlighting its benefits for diabetes management and weight loss. Semaglutide Injection in India Supplied by Impomed Healthcare, is a GLP-1 receptor agonist that helps control blood su
0 views • 11 slides
Virtual Intracavernosal Injection Training During COVID Pandemic
Sexual health clinician, Christine Zarowski, RN BSN, implemented virtual intracavernosal injection training during the COVID-19 pandemic at the Sexual Rehabilitation Clinic. The program provided web-based training on penile injections, resulting in high patient satisfaction and confidence levels. Vi
0 views • 8 slides
Understanding Injection Molding: Techniques and Applications
Injection molding is a versatile manufacturing process that involves injecting material into a mold to produce various parts. This process is crucial in creating products like switches, couplings, and more using different fabrication techniques such as molding and foaming processes. The method is wi
0 views • 23 slides
Web Application Security: Uncovering Common Attacks and Countermeasures
Explore common web application attacks such as eavesdropping and injection, along with effective countermeasures like encryption through SSL. Learn how to prevent attacks and secure your web apps.
0 views • 29 slides
Understanding DDoS Attacks: Simulation, Analysis & Defense
Delve into the world of Distributed Denial of Service (DDoS) attacks with this comprehensive study covering the architecture, advantages, bot installation phases, attack methods, defenses, and simulation. Learn about the detrimental impact of DDoS attacks on servers, their multi-tiered structure, an
0 views • 20 slides
Overview of DoS and DDoS Attacks in Cybersecurity
This content provides an in-depth overview of Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks in cybersecurity. It covers the types of attacks, including volumetric, reflected, and stealthy, along with detailed explanations and examples. Additionally, it discusses how DoS at
0 views • 8 slides
Challenges and Design of High-Intensity Accumulator for Neutrino Experiments
The presentation discusses the challenges faced in designing an accumulator for high-intensity particle beams in neutrino experiments at ESS Lund, with a focus on beam loss management, injection efficiency, and intense beam physics issues. The design considerations include beam holding capacity, bea
0 views • 30 slides
Understanding PHP Object Injection Vulnerability
Delve into the potential risks associated with PHP Object Injection, a type of application-level vulnerability that can lead to various malicious attacks such as Code Injection, SQL Injection, and more. Learn how inadequate sanitization of user input can pave the way for attackers to inject arbitrar
0 views • 28 slides