Proposed Approach for MAC Address Assignment in IEEE 802.11
IEEE 802.1CQ is working on a mechanism to assign local MAC address blocks to end nodes specifically related to IEEE 802.11 standards. The current draft lacks a pre-association mechanism for IEEE 802.11 stations to obtain a local MAC address before association. The proposed remedy suggests specifying
6 views • 7 slides
Proposal for Random Access Efficiency Enhancement in IEEE 802.11be Networks
This document presents a proposal for enhancing random access efficiency in IEEE 802.11be networks through a Random-Access NFRP (RA-NFRP) principle. The proposal addresses the challenges of low efficiency in the current UORA procedure and introduces modifications based on the 802.11ax standard to im
5 views • 16 slides
Understanding Bluetooth Low Energy Addresses in IEEE 802.11-21/1535r0
The document explores the features of resolvable addresses in Bluetooth Low Energy (BLE) within the IEEE 802.11-21/1535r0 standard. It discusses the two types of addresses in BLE, Public and Random, and their usage. The emphasis is on Random addresses due to their popularity and privacy features. Th
2 views • 11 slides
Understanding VA Privacy Issues and Sensitive Information
Explore the complex landscape of VA privacy issues, including data relationships, sensitive personal information (SPI), personally identifiable information (PII), individually identifiable information (III), and individually identifiable health information (IIHI). Learn about the roles and responsib
0 views • 29 slides
Information Security Awareness Training for Personally Identifiable Information at LACCD
This training session by LACCD Office of Information Technology focuses on educating personnel about identifying and handling Personally Identifiable Information (PII) to safeguard student and employee privacy. It covers the definition of PII, laws protecting PII, responsibilities in protecting PII,
0 views • 26 slides
Understanding Random Forests: A Comprehensive Overview
Random Forests, a popular ensemble learning technique, utilize the wisdom of the crowd and diversification to improve prediction accuracy. This method involves building multiple decision trees in randomly selected subspaces of the feature space. By combining the predictions of these trees through a
1 views • 21 slides
Simplifying Random Assignment with The Cambridge Randomizer
The Cambridge Randomizer offers a cost-effective and efficient solution for random assignment in research studies, enabling treatment providers to conduct the process securely. This innovative online portal streamlines the assessment of participant eligibility, provides instant baseline data, and en
0 views • 8 slides
High-Throughput True Random Number Generation Using QUAC-TRNG
DRAM-based QUAC-TRNG provides high-throughput and low-latency true random number generation by utilizing commodity DRAM devices. By employing Quadruple Row Activation (QUAC), this method outperforms existing TRNGs, achieving a 15.08x improvement in throughput and passing all 15 NIST randomness tests
0 views • 10 slides
IEEE 802.11-20/0054r1 MLD MAC Address and WM Address
In the document IEEE 802.11-20/0054r1, the focus is on Multi-Link Framework for MLD address identification and differentiation. It explains the usage of MLD MAC address and STA WM medium address in wireless setups. The document also addresses the need for identifying different MLDs using MAC address
0 views • 16 slides
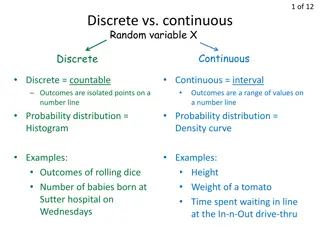
Understanding Random Variables and Their Applications in Various Fields
Random variables play a crucial role in statistics, engineering, and business applications. They can be discrete or continuous, depending on the nature of the outcomes. Discrete random variables have countable values, while continuous random variables can take on any real number. This article explor
0 views • 6 slides
Proposal for OTA MAC Change in IEEE 802.11-23/268r1
This proposal suggests using separate and unrelated random OTA MAC addresses for Source Address (SA) and Destination Address (DA) to enhance privacy and security in IEEE 802.11 networks. By obscuring the relationship between traffic, it aims to improve transmission privacy for multiple STAs associat
0 views • 14 slides
Understanding Random Variables and Probability Distributions
Random variables are variables whose values are unknown and can be discrete or continuous. Probability distributions provide the likelihood of outcomes in a random experiment. Learn how random variables are used in quantifying outcomes and differentiating from algebraic variables. Explore types of r
0 views • 13 slides
Advanced Imputation Methods for Missing Prices in PPI Survey
Explore the innovative techniques for handling missing prices in the Producer Price Index (PPI) survey conducted by the U.S. Bureau of Labor Statistics. The article delves into different imputation methods such as Cell Mean Imputation, Random Forest, Amelia, MICE Predictive Mean Matching, MI Predict
0 views • 22 slides
Enhancing Privacy with Randomized MAC Addresses in 802.11 Networks
This presentation discusses the use of randomized MAC addresses as a privacy-enhancing measure in 802.11 networks. Passive observation of MAC addresses poses privacy risks, and the proposal suggests assigning random MAC addresses to portable devices to mitigate tracking risks. By periodically changi
0 views • 10 slides
Understanding Random Class in Java Programming
The Random class in Java is used to generate pseudo-random numbers. By utilizing methods such as nextInt and nextDouble, you can generate random integers and real numbers within specified ranges. This chapter explores common usage scenarios, such as generating random numbers between specific ranges
2 views • 10 slides
Understanding Random Sampling in Probabilistic System Analysis
In the field of statistical inference, random sampling plays a crucial role in drawing conclusions about populations based on representative samples. This lecture by Dr. Erwin Sitompul at President University delves into the concepts of sampling distributions, unbiased sampling procedures, and impor
0 views • 23 slides
Privacy Issues in IEEE 802.11 Networks: Tracking and MAC Randomization
This presentation delves into the privacy concerns surrounding 802.11 networks, focusing on tracking vulnerabilities and the limitations of MAC randomization in preventing tracking. It discusses the ease of tracking devices, the risk of passive tracking due to MAC addresses being visible in frames,
0 views • 27 slides
IEEE802.15-14-0110-01-0mag MAC Timing Discussion Points for IEEE 802.15.4 Revision
Initial discussion document submitted by Benjamin A. Rolfe from Blind Creek Associates addressing MAC timing issues in the IEEE 802.15.4 standard revision. The document identifies potential problems, provides a list of questions for consideration, and outlines areas for improvement. It includes stat
0 views • 8 slides
Quantum Key Agreements and Random Oracles
This academic paper explores the impossibility of achieving key agreements using quantum random oracles, discussing the challenges and limitations in quantum communication, cryptographic protocols, quantum computation, and classical communication. The study delves into the implications of quantum ra
0 views • 29 slides
Approximate Inference in Bayes Nets: Random vs. Rejection Sampling
Approximate inference methods in Bayes nets, such as random and rejection sampling, utilize Monte Carlo algorithms for stochastic sampling to estimate complex probabilities. Random sampling involves sampling in topological order, while rejection sampling generates samples from hard-to-sample distrib
0 views • 9 slides
Summary of MAC Address Policy Contribution to IEEE 802.11
This document outlines the contribution of MAC address policy to IEEE 802.11, focusing on defining ANQP and Beacon elements to convey information about addressing types supported by the network. It details how specific bits in the ANQP element represent support for various MAC address types includin
0 views • 5 slides
Understanding Random Numbers in Computers
Explore the concept of true random numbers versus pseudorandom numbers in computers. Learn how pseudorandom numbers are generated algorithmically but predictable, while true random numbers are derived from physical phenomena like radioactive decay. Discover the relevance of high-entropy pseudorandom
0 views • 57 slides
Implications of IEEE 802.11 State Machine and MAC Randomization
The document discusses the state machine transitions in IEEE 802.11, focusing on MAC address handling and implications for STA connectivity within an ESS. It explains the scenarios where a STA can use different MAC addresses, emphasizing the binding of state to specific address configurations and th
0 views • 11 slides
IEEE 802.11-21/1585r10: Identifiable Random MAC Address Presentation Summary
This presentation discusses the concept of Identifiable Random MAC (IRM) addresses in the IEEE 802.11-21/1585r10 standard. It covers the purpose of IRM addresses in preventing third-party tracking while allowing trusted parties to identify specific devices. The presentation outlines the use of Ident
0 views • 24 slides
Understanding Laplace Transforms for Continuous Random Variables
The Laplace transform is introduced as a generating function for common continuous random variables, complementing the z-transform for discrete ones. By using the Laplace transform, complex evaluations become simplified, making it easy to analyze different types of transforms. The transform of a con
0 views • 17 slides
Understanding Discrete Random Variables and Variance Relationships
Explore the concepts of independence in random variables, shifting variances, and facts about variance in the context of discrete random variables. Learn about key relationships such as Var(X + Y) = Var(X) + Var(Y) and discover common patterns in the Discrete Random Variable Zoo. Embrace the goal of
0 views • 27 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Introduction to IEEE 802c SLAP
IEEE 802c defines Local Medium Access Control (MAC) Address Usage, providing structured approaches through the Structured Local Address Plan (SLAP) in different regions of the local MAC address space. Local MAC addresses are not globally unique, and the assignment is within local administration's sc
0 views • 9 slides
Caseous Mitral Valve Calcification (C-MAC) and Stroke: Overview and Management
Caseous Mitral Valve Calcification (C-MAC) is a rare condition characterized by spectrum liquefaction necrosis of the mitral annular calcification (MAC), potentially leading to cardiovascular complications like strokes and emboli. This article discusses the features, diagnostic aspects, and treatmen
0 views • 7 slides
GUC-Secure Commitments via Random Oracles: New Findings
Exploring the feasibility of GUC-secure commitments using global random oracles, this research delves into the differences between local and global random oracles, outlining motivations and future work. It discusses UC frameworks, zero-knowledge proofs, oblivious transfers, and the GUC framework for
0 views • 18 slides
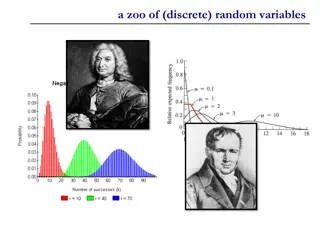
Understanding a Zoo of Discrete Random Variables
Discrete random variables play a crucial role in probability theory and statistics. This content explores three key types: Bernoulli random variable, binomial random variable, and error-correcting codes. From understanding the basics of Bernoulli trials to exploring the application of error correcti
0 views • 27 slides
Enhancing MAC Header Protection in IEEE 802.11 Networks
This document discusses the need for improved protection of MAC headers in IEEE 802.11 networks to address security concerns related to certain fields that are currently not adequately protected. It emphasizes the importance of safeguarding vital information in MAC headers to prevent potential attac
0 views • 12 slides
IEEE 802.11-22/0424r1 - MAAD MAC Protocol Overview
The document discusses the MAAD MAC protocol, where the AP assigns a MAAD MAC address to the STA during association. Key differences from other schemes are highlighted, emphasizing the use of MAAD MAC addresses as identification. Details on support indication, address allocation, and recognition mec
0 views • 7 slides
IEEE 802.11-22/0955r0 TGbh Pre-association Schemes Exploration
The document explores the pre-association schemes NGID, MAAD, and IRM within the IEEE 802.11-22 standard. It discusses how the schemes operate, comparing RRCM to MAAD and IRM, and addresses the use of Probes and MAC addresses in pre-association scenarios. The presentation clarifies the allocation of
0 views • 15 slides
RCM Procedure for Secure Parameter Obfuscation in IEEE 802.11 Networks
The document discusses the RCM procedure within IEEE 802.11 networks, focusing on obfuscating parameters like MAC addresses for enhanced security during CPE Client and CPE AP association. It outlines mechanisms for changing MAC addresses, SN, PN, AID, and TID without connection loss. The proposal su
0 views • 12 slides
Understanding Random Slopes in Data Analysis
Exploring the impact of grand-mean and group-mean centering on intercept interpretation with random slopes, as well as variations in slope/intercept covariance. Differentiating between fixed and random coefficients, and the effects of adding group mean as a Level 2 variable. Delving into within vs.
0 views • 21 slides
Understanding Random Variables and Mean in Statistics
Random variables can be discrete or continuous, with outcomes represented as isolated points or intervals. The Law of Large Numbers shows how the mean of observed values approaches the population mean as the number of trials increases. Calculating the mean of a random variable involves finding the e
0 views • 13 slides
IEEE 802.11-23/0421r1: Understanding the IRM Scheme for MAC Address Privacy
The document discusses the use of the Same MAC Address (SMA) scheme in IEEE 802.11-23/0421r1 and introduces the Improved Randomized MAC (IRM) scheme as a privacy-enhancing solution. It explores the implementation and benefits of IRM over SMA, addressing issues like privacy requirements, device ident
0 views • 7 slides
Enhancement of Rule-based Random and Changing MAC Proposal in IEEE 802.11-22/1802r0
This document details the enhancements proposed for the Rule-based Random and Changing MAC (RRCM) in IEEE 802.11-22/1802r0. The RRCM concept involves generating Random MAC (RMA) addresses locally to increase security and prevent trackability in wireless networks. Key aspects include RMA generation,
0 views • 12 slides
MAC Address Randomization in IEEE 802.11: Privacy Concerns and Solutions
The document discusses the rise of MAC randomization in IEEE 802.11 networks, addressing motivations, benefits, concerns over privacy implications, and real-life scenarios highlighting the risks associated with passive observation of MAC addresses. It emphasizes the importance of safeguarding privac
0 views • 14 slides