Algorithm Analysis
Algorithm analysis involves evaluating the efficiency of algorithms through measures such as time and memory complexity. This analysis helps in comparing different algorithms, understanding how time scales with input size, and predicting performance as input size approaches infinity. Scaling analysi
1 views • 30 slides
Understanding Booth's Algorithm for Binary Integer Division
Learn about Booth's Algorithm and how it facilitates binary integer division. Discover key points to remember when using the algorithm, steps to initiate the process, and a detailed example to illustrate the multiplication of two operands using Booth's Algorithm.
1 views • 42 slides
Best service for Boiler Repair in Maida Hill
Vaillant Boiler Service Experts Notting Hill serves the Best service for Boiler Repair in Maida Hill. They provide all types and sizes of central heating systems, replacement boilers, and intelligent gas-firing solutions for your home or business needs. When you need a boiler repair service fast, no
0 views • 6 slides
Mera Peak Climbing
\nMera Peak, standing at 6,476 meters (21,247 feet), is one of the highest trekking peaks in Nepal and offers a non-technical but demanding climb. It is located in the Mahalangur section of the Himalaya, in the Sagarmatha Zone. Mera Peak climbing is a popular choice for mountaineers who want to expe
9 views • 7 slides
Kilimanjaro Climbing Adventure Itineraries
Embark on an unforgettable adventure with our Mount Kilimanjaro Climbing Itineraries! Choose from various routes, each offering unique challenges and rewards. Whether you prefer a leisurely pace or an intense climb, our itineraries accommodate all experience and fitness levels. Explore Mount Kiliman
1 views • 5 slides
Essential Climbing Knots and Techniques for Beginners
Learn the key climbing knots like the Figure Eight Follow Through and the Figure Eight On A Bight, essential for beginner climbers. Follow step-by-step instructions, safety tips, and technical information to enhance your climbing skills and knowledge.
0 views • 38 slides
Granny's Tree Climbing - A Poetic Adventure by Ruskin Bond
In this whimsical poem by Ruskin Bond, we are introduced to Granny, a sprightly sixty-two-year-old who defies convention by indulging in her lifelong passion for tree climbing. Despite admonishments from her family, Granny remains steadfast in her joy as she embarks on a delightful tree-climbing esc
0 views • 19 slides
Understanding Stable Matchings and the Gale-Shapley Algorithm
The concept of stable matchings is explored, along with the Gale-Shapley algorithm for finding them efficiently. Key ideas and steps of the algorithm are explained, supported by visuals. The process, examples, and observations related to the algorithm's effectiveness are discussed, highlighting the
1 views • 29 slides
Ricart and Agrawala's Algorithm for Mutual Exclusion
The Ricart-Agrawala Algorithm is a distributed system algorithm for achieving mutual exclusion without the need for release messages, developed by Glenn Ricart and Ashok Agrawala. The algorithm involves processes sending timestamped requests to enter a critical section, with careful handling of repl
1 views • 16 slides
Understanding Algorithm Efficiency Analysis
In this chapter, Dr. Maram Bani Younes delves into the analysis of algorithm efficiency, focusing on aspects such as order of growth, best case scenarios, and empirical analysis of time efficiency. The dimensions of generality, simplicity, time efficiency, and space efficiency are explored, with a d
1 views • 28 slides
Climber Timer: Innovative Climbing Center Solution by EEE Project Team
Climber Timer is an innovative solution developed by a team of EEE project members to help climbers easily time and log their climbs at climbing centers. The device is designed to retrofit onto existing walls and offers features like ascent time recording, auditory feedback, and data upload capabili
0 views • 24 slides
Understanding Lamport Algorithm for Mutual Exclusion
Lamport Algorithm, presented by Prafulla Santosh Patil, is a permission-based algorithm utilizing timestamps to order critical section requests and resolve conflicts. It employs three types of messages: REQUEST, REPLY, and RELEASE, where each site manages a queue to store requests. By ensuring commu
0 views • 15 slides
Digital Differential Analyzer (DDA) Algorithm in Computer Graphics
In computer graphics, the Digital Differential Analyzer (DDA) Algorithm is utilized as the basic line drawing algorithm. This method involves interpolation of variables between two endpoints to rasterize lines, triangles, and polygons efficiently. The algorithm requires inputting coordinates of two
0 views • 9 slides
Understanding Randomized Hill Climbing Algorithm for Challenging Problem Solving
Randomized Hill Climbing is a versatile approach to solving complex problems by sampling points in the neighborhood of the current best solution. This method is easy to apply, resource-efficient, and usually fast. However, defining the neighborhood and choosing appropriate parameters can pose challe
4 views • 14 slides
Artificial Intelligence Heuristic Search Techniques
Assistant Professor Manimozhi from the Department of Computer Applications at Bon Secours College for Women in Thanjavur is exploring Artificial Intelligence concepts such as weak methods and Generate-and-Test algorithms. The content covers heuristic search techniques like generating and testing, hi
0 views • 7 slides
Aircraft Banking and Turning Techniques Overview
Aircraft banking and turning involve rolling the aircraft to a predetermined angle of bank while maintaining performance and balance for level, climbing, or descending flight to achieve a predetermined heading. The primary methods for banking include using ailerons to turn the airplane, rudder to ba
1 views • 19 slides
Essential Climbing Safety Tips and Techniques
This content provides valuable information on climbing equipment, security measures, belaying techniques, and essential knots for climbers. It emphasizes the importance of safety checks before and during climbing, highlighting key practices to ensure a safe and enjoyable climbing experience. The det
5 views • 10 slides
Grey Wolf Optimizer: A Nature-Inspired Optimization Algorithm
The Grey Wolf Optimizer algorithm is based on the social hierarchy of grey wolves in the wild. Inspired by the pack behavior of grey wolves, this algorithm utilizes alpha, beta, and delta solutions to guide the optimization process. The hunting phases of tracking, pursuing, and attacking prey mimic
3 views • 16 slides
Emergency Paediatric Tracheostomy Management Algorithm
Emergency Paediatric Tracheostomy Management Algorithm provides a structured approach for managing pediatric patients requiring tracheostomy in emergency situations. The algorithm outlines steps for assessing airway patency, performing suction, and changing the tracheostomy tube if necessary. It emp
0 views • 4 slides
Development of Satellite Passive Microwave Snowfall Detection Algorithm
This study focuses on the development of a satellite passive microwave snowfall detection algorithm, highlighting the challenges in accurately determining snowfall using satellite instruments. The algorithm uses data from AMSU/MHS, ATMS, and SSMIS sensors to generate snowfall rate estimates, overcom
0 views • 20 slides
Understanding Hill Area Development Programmes in India
Exploring the significance of Hill Area Development Programmes in India, focusing on the challenges faced by hill areas, the meaning of hills, the Tribal Area Development Programme, and the initiatives undertaken for sustainable development in these regions. The article discusses the fragile ecosyst
0 views • 17 slides
Understanding Euclid's Algorithm: An Ancient Approach to Finding Greatest Common Divisors
Euclid's Algorithm, dating back 2500 years, offers a simpler method to find the greatest common divisor (gcd) of two non-negative integers compared to traditional factorization. By iteratively applying a rule based on the gcd of remainders, it efficiently computes gcd values. The basis of the algori
0 views • 15 slides
Heuristic Search Algorithms in Artificial Intelligence
In the realm of artificial intelligence, heuristic search algorithms play a pivotal role in efficiently navigating large search spaces to find optimal solutions. By leveraging heuristics, these algorithms can significantly reduce the exploration of the search space and guide agents towards the goal
0 views • 14 slides
GPU Accelerated Algorithm for 3D Delaunay Triangulation
Thanh-Tung Cao, Todd Mingcen Gao, Tiow-Seng Tan, and Ashwin Nanjappa from the National University of Singapore's Bioinformatics Institute present a GPU-accelerated algorithm for 3D Delaunay triangulation. Their work explores the background, related works, algorithm implementation, and results of thi
0 views • 24 slides
Understanding Local Search Algorithms for Problem Solving
Dive into the world of local search algorithms for problem solving with a focus on iterative improvement, hill climbing, simulated annealing, and more. Learn how these algorithms are applied to identification, planning, and optimization problems, and explore their completeness and optimality. Discov
0 views • 30 slides
Cuckoo Search: A Nature-Inspired Optimization Algorithm
Cuckoo Search (CS) algorithm, developed in 2009, mimics the brood parasitism of cuckoo species and utilizes Lévy flights for efficient optimization. This algorithm has shown promise in outperforming other traditional methods like PSO and genetic algorithms. The behavior of cuckoos in laying eggs an
0 views • 25 slides
Ford-Fulkerson Algorithm for Maximum Flow in Networks
The Ford-Fulkerson algorithm is used to find the maximum flow in a network by iteratively pushing flow along paths and updating residual capacities until no more augmenting paths are found. This algorithm is crucial for solving flow network problems, such as finding min-cuts and max-flow. By modelin
0 views • 26 slides
3GPP Voting Rights Algorithm: Contiguous-3 Solution Evaluation
This evaluation delves into the advantages and disadvantages of the 3 Contiguous-3 solution within the 3GPP voting rights algorithm. It explores scenarios to test the algorithm's effectiveness in granting and revoking voting rights based on meeting attendance types. The evaluation includes diverse h
0 views • 10 slides
Introduction to Algorithm Analysis and Complexity in Computer Science
Algorithm analysis is crucial in determining the efficiency of programs by analyzing resource usage such as time and space. This involves comparing programs, understanding data structures, and evaluating algorithm performance. Efficiency is key as program execution time depends on various factors be
0 views • 66 slides
Bresenham Line Drawing Algorithm Explained with Examples
Bresenham Line Drawing Algorithm is a method used to generate points between starting and ending coordinates to draw lines efficiently. This algorithm involves calculating parameters, decision parameters, and iteratively finding points along the line. Two example problems are provided with step-by-s
0 views • 8 slides
Algorithm Strategies: Greedy Algorithms and the Coin-changing Problem
This topic delves into general algorithm strategies, focusing on the concept of greedy algorithms where locally optimal choices are made with the hope of finding a globally optimal solution. The discussion includes the nature of greedy algorithms, examples such as Dijkstra's algorithm and Prim's alg
0 views • 91 slides
Stable Matching Problem and Gale-Shapley Algorithm Overview
The content provides information on the stable matching problem and the Gale-Shapley algorithm. It covers the definition of stable matching, the workings of the Gale-Shapley algorithm, tips for algorithm implementation, and common questions related to the topic. The content also includes a summary o
0 views • 16 slides
Tower Safety Awareness and Rescue Team Overview
South Hills Area Council of Governments (SHACOG) Technical Rescue Team is a dedicated group serving 22 municipalities across a 220+ square mile area with 40+ public safety agencies. With a focus on tower safety awareness, the team provides crucial information on common tower types, hazards, personal
0 views • 16 slides
Understanding Deutsch's Algorithm in Quantum Computing
Deutsch's Algorithm is a fundamental quantum algorithm designed to solve the problem of determining if a given function is constant or balanced. This algorithm leverages quantum principles such as superposition and entanglement to provide a more efficient solution compared to classical methods. By e
0 views • 17 slides
Algorithm for Determining Endpoints in Speech Recognition
This article discusses an algorithm proposed by L.R. Rabiner and M.R. Sambur in 1975 for determining endpoints in isolated utterances. The algorithm focuses on detecting word boundaries in speech through the recognition of silence, which can lead to reduced processing load and increased convenience,
0 views • 22 slides
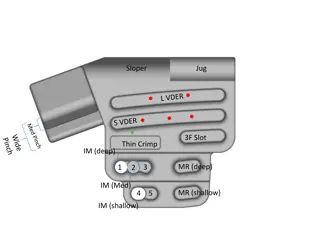
Advanced Climbing Holds: Sloper, Jug, Slot, Thin, Crimp - Positions and Descriptions
Explore the various types of climbing holds such as slopers, jugs, slots, thin holds, and crimps with detailed position descriptions. Dive into the world of indoor climbing and enhance your skills with these challenging holds.
0 views • 4 slides
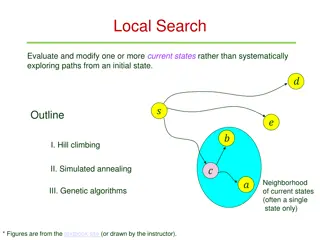
Understanding Local Search Algorithms for Optimization
Local search methods like hill climbing and simulated annealing focus on evaluating and modifying current states to find optimal solutions efficiently, making them suitable for complex state spaces. Hill climbing involves iteratively moving towards higher value states, while simulated annealing uses
0 views • 17 slides
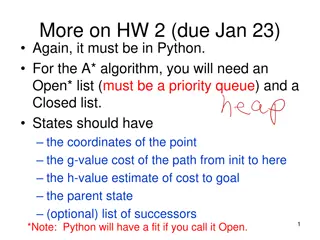
Introduction to A* Algorithm and Local Search Techniques in Python
Explore the implementation of the A* algorithm in Python for solving pathfinding problems, including the use of a priority queue for the Open list. Additionally, delve into local search algorithms such as Hill Climbing and Simulated Annealing for optimization problems. Design custom data sets, run a
0 views • 27 slides
Techniques in Beyond Classical Search and Local Search Algorithms
The chapter discusses search problems that consider the entire search space and lead to a sequence of actions towards a goal. Chapter 4 explores techniques, including Hill Climbing, Simulated Annealing, and Genetic Search, focusing solely on the goal state rather than the entire space. These methods
0 views • 51 slides
Time-space Tradeoffs and Optimizations in BKW Algorithm
Time-space tradeoffs and optimizations play a crucial role in the BKW algorithm, particularly in scenarios like learning parity with noise (LPN) and BKW algorithm iterations. The non-heuristic approach in addressing these tradeoffs is discussed in relation to the hardness of the LPN problem and the
0 views • 14 slides