Civil War Causes and Key Figures: Divines of the North and South
Explore the relationships and events leading up to the Civil War, including the disparity between North and South, the Kansas-Nebraska Act, popular sovereignty, the Dred Scott Case, John Brown's Raid, and President Lincoln's efforts to preserve the Union. Dive into economic, political, and social di
0 views • 23 slides
Nuclear Structure Investigations with Resonant Photon Scattering at FRIB-TA Workshop
Explore nuclear structure using resonant photon scattering at the FRIB-TA Workshop. The High Intensity Gamma-ray Source facility enables research on photonuclear reactions, spin and parity determinations, and selective investigation of nuclear states. Learn about the technique's potential impact on
2 views • 33 slides
WW2: Oldham Goes to War Display at Gallery Oldham
Explore the WW2 display at Gallery Oldham showcasing objects from the social history collection, including a radio set, air raid siren, infant respirator, ration books, powdered milk tin, ARP insignia badges, and more. Discover how these artifacts played a crucial role during wartime, from maintaini
2 views • 7 slides
Understanding Forex Parity Relationships and Forecasting Exchange Rates
Discover the intricacies of interest rate parity, purchasing power parity, Fisher effects, and alternative theories in forecasting exchange rates. Delve into examples illustrating covered interest arbitrage and currency carry trade strategies. Explore how these concepts impact the FX market and lear
3 views • 44 slides
Gender Pay Gap Analysis and Parity Initiatives in City of Harare
The City of Harare has sex-disaggregated data on employment showing disparities in earnings between men and women. The average monthly earnings for full-time and casual positions reveal a gender wage gap of 0.96%. Reasons for this gap include job segregation and manual labor preferences, affecting w
1 views • 8 slides
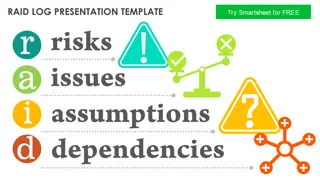
Comprehensive RAID Log Presentation and Management Overview
This comprehensive presentation template provides a detailed overview of a RAID log, including risks, issues, threats, assumptions, dependencies, and reliance factors. It offers insights on tracking and managing different aspects of project planning and execution, categorized by risk levels. The bre
0 views • 6 slides
Analysis of Clocked Sequential Circuits and Parity Checkers
This chapter delves into the analysis of clocked sequential circuits, focusing on topics such as sequential parity checkers, signal tracing, state tables and graphs, and models for sequential circuits. It covers concepts like Mealy and Moore machines, state equations, state graphs, timing charts, an
0 views • 38 slides
Understanding RAID Technology in DBMS: Redundancy and Performance
This content provides insights into RAID technology, discussing the combination of reliability and performance in managing multiple disks through various RAID levels like RAID 0, RAID 1, RAID 2, RAID 3, RAID 4, and RAID 5. It explores the advantages of RAID, such as data striping, mirroring, bit int
0 views • 61 slides
The Impact of John Brown's Raid on Harper's Ferry in 1859
John Brown's raid on Harper's Ferry in 1859 was an attempt to incite a slave rebellion and abolish slavery. Brown believed in the righteousness of his cause, but his actions sparked national debate and differing reactions. While some saw him as a martyr for freedom, others viewed him as a radical ex
2 views • 9 slides
Understanding Erasure Coding in Storage Systems
Erasure Coding is a data storage technique that enhances fault tolerance by breaking files into chunks and generating additional pieces for reconstruction. This technology, exemplified by systems like Ceph, offers more robust data protection than traditional methods like RAID or replication. Erasure
0 views • 10 slides
Parity-Only Caching for Robust Straggler Tolerance in Large-Scale Storage Systems
Addressing the challenge of stragglers in large-scale storage systems, this research introduces a Parity-Only Caching scheme for robust straggler tolerance. By combining caching and erasure coding techniques, the aim is to mitigate latency variations caused by stragglers without the need for accurat
0 views • 29 slides
Overview of Mass Storage Systems in Computer Engineering
Mass storage in computer engineering involves secondary and tertiary storage devices like magnetic disks and tapes, providing permanent storage for large volumes of data. The structure, performance characteristics, and operating system services for mass storage are discussed, including RAID and HSM.
9 views • 77 slides
World War II in the Pacific: Unfolding of Events Post Pearl Harbor Attack
The war in the Pacific escalated post the Pearl Harbor attack with Japan's domination over various territories, including the Philippines leading to significant battles like the Japanese Invasion of the Philippines and Doolittle's Raid. American strategy, led by figures like Gen. MacArthur, played a
0 views • 12 slides
Understanding Storage Systems Dependability
This content discusses storage systems dependability, covering topics such as data reliability, fault-tolerant techniques, error detection and correction, component levels, disk protection techniques, types of disk faults, and protection mechanisms like RAID and ECC. It provides insights into ensuri
1 views • 25 slides
Robust Parity Test for Extracting Parallel Vectors in 3D
Fundamental primitives for visualizing 3D data include line features like ridges and valleys of a scalar field, stream lines of a vector field, vortices of a velocity field, and extremal curves of a tensor field. Parallel Vectors (PV) provide a unified representation of 3D line features, forming con
0 views • 27 slides
The Impact of John Brown's Raid on Harper's Ferry
John Brown's raid on Harper's Ferry in 1859 was a pivotal event that escalated tensions between the North and South in the lead-up to the Civil War. Brown's failed attempt to arm enslaved individuals and spark a revolt had far-reaching consequences, leading to heightened sectional tensions and a gre
0 views • 7 slides
Understanding Reliable Transmission in Computer Networks
Explore the essentials of reliable transmission in computer networks, including error detection methods like parity, checksums, and error-correcting codes. Learn about clock-based framing, SONET links, and synchronization techniques for data integrity. Dive into topics such as two-dimensional parity
0 views • 39 slides
John Brown's Role in Escalating Tensions Towards the Civil War
Explore John Brown's pivotal role in the lead-up to the Civil War through his radical abolitionist actions, including the violent events in Bleeding Kansas and his infamous raid on Harper's Ferry. Brown's staunch anti-slavery stance and militant tactics further polarized the nation on the issue of s
0 views • 9 slides
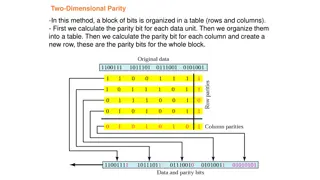
Data Error Detection Techniques Overview
Two-dimensional parity and Cyclic Redundancy Check (CRC) are data error detection methods used to ensure data integrity during transmission. Two-dimensional parity involves organizing bits in a table to calculate parity bits for data units and columns, while CRC appends a string of zeros to the data
0 views • 20 slides
Addressing Insurance Barriers in Eating Disorder Treatment: A Call for Change
Kentucky faces significant challenges in providing adequate care for individuals with eating disorders due to insurance barriers, lack of trained professionals, and limited treatment options within the state. The high mortality rate, chronic nature, and costly treatment of eating disorders exacerbat
0 views • 28 slides
Practical Strategies for Digital Preservation at IWU
Explore digital preservation strategies in practice at Illinois Wesleyan University. Learn from Meg Miner, the University Archivist, about preservation philosophy, local-centric decisions, and the importance of prioritizing digital collections inventory. Gain insights into updates on processing acti
0 views • 33 slides
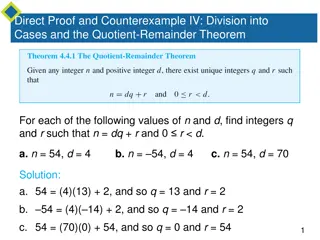
Understanding Integer Division, Modulus, and Parity
Explore the concepts of integer division, modulus, and the parity of integers through the quotient-remainder theorem. Learn how to compute div and mod manually and understand the representation of integers as even or odd. Discover how these principles apply in computer languages and the unique prope
0 views • 18 slides
Comprehensive RAID Log Presentation Template
This comprehensive presentation template includes a RAID log with risks, assumptions, issues, and dependencies structured in a professional layout. Utilize this template to effectively manage project risks and dependencies. The template also features a simple RAID log slide template for a clear over
0 views • 7 slides
Understanding Redundant Arrays of Inexpensive Disks (RAID)
This informative material discusses the concept of RAID, its various levels such as RAID 0, 1, and 2, their advantages and disadvantages, and the motivation behind implementing RAID systems. It highlights the need for data redundancy, disk throughput optimization, and reliable storage solutions usin
0 views • 30 slides
Elastic Parity Logging for SSD RAID Arrays
SSDs are widely used for their performance and efficiency, but face challenges like flash errors and poor random write performance. The paper introduces EPLog, a new RAID design for SSD arrays, enhancing reliability, endurance, and performance through elastic parity logging. The solution redirects w
0 views • 23 slides
Evolution of Indian-White Relations: Raid or Trade?
The article discusses how Indian-White relations transitioned from cooperation to conflict over time, exploring the factors influencing negotiation outcomes versus violent confrontations. The model presented highlights the role of property rights, informational asymmetry, military technology, and th
0 views • 4 slides
Overview of Distributed Systems, RAID, Lustre, MogileFS, and HDFS
Distributed systems encompass a range of technologies aimed at improving storage efficiency and reliability. This includes RAID (Redundant Array of Inexpensive Disks) strategies such as RAID levels, Lustre Linux Cluster for high-performance clusters, MogileFS for fast content delivery, and HDFS (Had
0 views • 23 slides
Enhancing Data Storage Reliability with High-Parity GPU-Based RAID
The research discusses the challenges faced by traditional RAID systems in maintaining data reliability and proposes a solution using High-Parity GPU-Based RAID. It highlights the limitations of current technologies in fault tolerance, the inaccuracies in disk failure statistics, and the significanc
0 views • 13 slides
Understanding RAID: A Case for Redundant Arrays of Inexpensive Disks
Delve into the world of Redundant Arrays of Inexpensive Disks (RAID) exploring its evolution, motivation, and various RAID levels like RAID 1, RAID 2, RAID 3, and RAID 4. Discover the importance of data redundancy and fault tolerance in storage systems.
0 views • 17 slides
Ecuadorian Diplomatic Crisis: The Raid on Mexico's Embassy and Its Global Impact
Ecuadorian police raid Mexico's embassy in Quito, arresting former Vice-President Jorge Glas. Mexico grants him asylum, leading to a diplomatic standoff. The incident reflects political tensions between the countries and raises concerns about adherence to diplomatic norms. Regional powers condemn Ec
0 views • 5 slides
Understanding RAID 5 Technology: Fault Tolerance and Degraded Mode
RAID 5 is a popular technology for managing multiple storage devices within a single array, providing fault tolerance through data striping and parity blocks. This article discusses the principles of fault tolerance in RAID 5, the calculation of parity blocks, handling degraded mode in case of disk
0 views • 12 slides
Understanding Storage Devices in Computer Systems
This content provides an in-depth look at storage devices used in computer systems, covering topics such as hard drives, RAID, SSDs, addressing and geometry of hard drives, disk interfaces, types of delays with disks, and how to calculate transfer time. It explores the components, functionalities, a
0 views • 62 slides
NVDIMM High-Level Use Cases Overview
Explore various high-level use cases for NVDIMM technology, including local NVDIMM kernel access, SW RAID configurations, and NVDIMM utilization in both public and private cloud environments. These scenarios involve accessing, caching, and replicating data using NVDIMMs to enhance memory performance
0 views • 10 slides
Family Planning Method Discontinuation/Switch/Continuation Among Young Low Parity Couples in Bihar
Family planning is crucial for individuals and couples to achieve their desired number of children and birth spacing. This study explores the distribution and determinants of family planning method discontinuation, switch, and continuation among young low parity couples in Bihar. The research delves
0 views • 12 slides
Understanding the Mental Health Parity Final Rule of May 18, 2016
The Mental Health Parity Final Rule of May 18, 2016 aims to ensure that financial and treatment limitations on Mental Health and Substance Use Disorder benefits are no more restrictive than those applied to Medical/Surgical benefits. This includes analysis of financial and treatment limitations, qua
0 views • 11 slides
Understanding Reed-Solomon Encoding: Basics and Applications
Messages consist of symbols from an alphabet and can face erasures and errors during transmission/storage. Redundancy is introduced in codewords to handle these faults, with schemes like 2x and 3x redundancy. Parity bits help detect/correct errors in binary messages efficiently, offering a cost-effe
0 views • 130 slides
Satellite Products for Aviation Remote Sensing Needs in High Latitudes
Addressing the specific needs of aviation remote sensing in high latitudes, this content explores the importance of satellite products, variations in equipment requirements, data expectations, and the significance of cloud products for aviation safety. Feedback from aircraft operators emphasizes the
0 views • 8 slides
Evaluation of Fairness Trade-offs in Predicting Student Success
This study delves into fairness concerns in predicting student success, examining trade-offs between different measures of fairness in course success prediction models. It explores statistical fairness measures like demographic parity, equality of opportunity, and positive predictive parity. Through
0 views • 11 slides
I/O-Efficient Protection Against Silent Data Corruptions in RAID Arrays
This paper discusses the risks of silent data corruptions in RAID arrays, which are challenging to detect and can lead to serious consequences. It presents the concept of integrity protection to enhance RAID systems' ability to detect and recover from such corruptions efficiently. The paper investig
0 views • 26 slides
Social Security Parity in Northern Ireland: Constitutional Principles and Devolution
Exploring the development of constitutional principles in Northern Ireland through the lens of social security parity, touching upon historical perspectives, devolution settlement, the parity principle's significance, and consultations between the Secretary of State and Northern Ireland Minister. Th
0 views • 14 slides