Global Game Jam NEXT 2024: Unleashing Creativity and Innovation in Game Development
Dive into the world of game development at Global Game Jam NEXT 2024 in Hong Kong, China. This event brings together passionate individuals to collaborate, design, and prototype video games and non-digital games. Explore workshops, team presentations, and the chance to turn your ideas into reality.
1 views • 14 slides
Update on SWAG Protocols and New NICE TA Progress Report
Kate Gregory leads the SWAG Protocols update for March 2024, with advancements in new protocols and NICE TA updates. A comparison of activities from Oct 2023 to Mar 2024 shows progress in issuing, reviewing, and drafting protocols. The latest NICE TA additions include treatments for advanced cancers
5 views • 13 slides
How can MR game developers ensure accessibility and inclusivity in their game designs
As the world of Mixed Reality (MR) Game Development continues to evolve, developers increasingly recognize the importance of accessibility and inclusivity in their game designs. Creating experiences that are accessible to players of all abilities not only expands the reach of your game but also fost
1 views • 5 slides
What are the essential steps in game design and development for beginners
Embarking on the journey of game design and development can be both exciting and daunting for beginners. Whether you aspire to create captivating games for traditional platforms or explore the immersive realm of Mixed Reality (MR) Game Development, understanding the fundamental steps is crucial. In
0 views • 12 slides
Is Croquet the Ultimate Garden Game? | MegaChess
In the 1860s, croquet as a game kicked up in the United Kingdom, further the years passed when its popularity peaked and this game was adopted by the United States and then it went to other countries. The game of Croquet played in the garden is a fun-to game starting from the afternoon and going thr
2 views • 8 slides
How to Start Your Career in Game Design?
In the digital age, where interactive entertainment holds sway over global audiences, game design stands as a pinnacle of creativity and technical prowess. For those captivated by the idea of crafting virtual worlds, shaping immersive experiences, and pushing the boundaries of technology, a career i
0 views • 6 slides
Understanding Consistency Protocols in Distributed Systems
Today's lecture covers consistency protocols in distributed systems, focusing on primary-based protocols and replicated-write protocols. These protocols play a crucial role in ensuring consistency across multiple replicas. One example discussed is the Remote-Write Protocol, which enforces strict con
0 views • 35 slides
Banatske Ore: A Traditional Shepherd Game in Vojvodina
Banatske Ore is a traditional shepherd game still played in Vojvodina, specifically in the village of Tomaševac. It involves handmade balls hit with a wooden bat, similar to baseball. The game has been played for nineteen years and a world championship is held annually on June 24. The field is 44 m
0 views • 9 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Game Programming Patterns Game Loop Summary
This content discusses the game loop structure in game programming patterns, comparing simple main loops and modern event-driven programs. It covers the continuous movement of a game even without user input, the importance of running at a fixed frame rate, and the implementation of frame rate contro
0 views • 14 slides
Game Clock Operator Guidelines and Responsibilities
Guidelines and responsibilities for game clock operators, including dress code, rules study, pre-game preparations, and in-game conduct. Operators must be qualified, familiar with game timing procedures, and maintain focus on accurate timekeeping. Follows procedures for pre-game, game-time operation
0 views • 19 slides
Understanding Ultimatum Game in Game Theory
Ultimatum game is a fundamental model in game theory where two players engage in bargaining. Player 1 offers a share of money to Player 2, who can either accept or reject the offer. If accepted, Player 1 receives the remainder; otherwise, both get nothing. The formal model, extensive form representa
0 views • 38 slides
MSA Game Day Procedures for Referees: Preparation and Safety Guidelines
Referees preparing for game day should form good habits by developing a routine before each game. This includes checking equipment the night before, ensuring uniforms are clean and ready, and having essential items like whistles, notepads, and assistant referee flags. Additionally, referees must hav
0 views • 17 slides
Innovative Marble Platforming Game Development Project
Development project focusing on creating a mobile marble platforming game with unique features like gyro controls, touch screen support, leaderboards, and social capabilities. Utilizing Unity for game engine and database management for user data security. Emphasis on MVC architecture for game design
0 views • 11 slides
Creating an Engaging Game: Essentials and Milestones
Explore the key elements of game design, such as planning, building sprites, and implementing complex projects. Learn about state-transition diagrams, scoring systems, and multi-state game development. Delve into game design essentials including setting goals, obstacles, and appropriate difficulty l
1 views • 56 slides
- Rust: A Hardcore Survival Game Experience
- Rust, developed by Facepunch Studios and presented by Ben Walker, immerses players in a challenging survival game where they awaken on an island with nothing but a rock. The goal is to gather resources, craft tools, build shelter, and defend against other players. With multiplayer interactions and
0 views • 19 slides
Lacrosse Officials Pre-Game Responsibilities and Preparation Guide
This comprehensive guide outlines the essential pre-game responsibilities for lacrosse officials, including contacting partners and teams, conducting meetings, researching teams, packing essentials, and arriving on time. Non-negotiable tasks, such as pre-game conferences and coach meetings, are high
0 views • 15 slides
Overview of Identification Protocols in CS255 by Dan Boneh
The lecture in CS255 covers various topics related to identification protocols, including signatures from trapdoor functions, certificates, revocation methods, certificate issuance problems, defense mechanisms like certificate transparency (CT), and moving on to protocols. The talk also explores the
0 views • 43 slides
Towards Practical Generic Zero-Knowledge Protocols
Exploring the evolution of zero-knowledge protocols, this presentation by Claudio Orlandi from Aarhus University delves into the concepts of Zero-Knowledge from Garbled Circuits, Privacy-Free Garbled Circuits, and more. The talk discusses efficient methods for proving statements and touches on relat
0 views • 29 slides
Understanding Two-Player Games and Game AI Evolution
Explore the significance of studying games, origins of game AI algorithms like Minimax, Alpha-beta search, and more. Learn about types of game environments, zero-sum games, strategies in two-player games, and game trees. Delve into the complexity of game theory and the evolving landscape of artifici
0 views • 38 slides
Biology Review: America Says Game Show Overview
America Says, a game show on the Game Show Network, features rounds covering various biology topics such as properties of life, cell structures, and biochemical reactions like cellular respiration. The game includes top seven answers for each round, a bonus round, and a tiebreaker. Images depict key
0 views • 10 slides
The Ultimate Guide to Hiring a Casino Game Development Company
Learn how to choose the best casino game development company, slot game development company, and experienced casino game developers for your project.\n\nsource>>\/\/joripress.com\/the-ultimate-guide-to-hiring-a-casino-game-development-company\n
1 views • 8 slides
PSA 2024 Spring Flag Football Coaches Meeting Overview
The PSA 2024 Spring Flag Football Coaches Meeting covers essential topics such as board members introductions, policies, registration details, game protocols, and more. Updated information supersedes previous rules, emphasized by mandatory coach badges and game reschedule protocols. The season is se
0 views • 18 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Green Protocols for Greener Arbitrations
The Green Protocols introduced by AtLAS aim to guide the arbitration community in committing to environmentally sustainable practices. These protocols suggest ways to reduce carbon emissions, energy consumption, waste generation, and unnecessary travel by utilizing electronic communication, video co
0 views • 14 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Tick Questing Game 1950 - Fun Temperature-based Card Game
Tick Questing Game 1950 is an exciting card game where players draw cards based on temperature conditions. The game involves questing ticks, recording sheets, and bonuses for successful quests. Players must strategize based on temperature ranges to keep their ticks alive and compete with their partn
0 views • 108 slides
Interactive Icebreaker Games for Large Groups
Fun and engaging icebreaker game ideas for large groups, including Shoe ID Game, Snowball Game, Autograph Bingo, Human Knot, ID Guessing Game, and M&M Game. These games are perfect for breaking the ice, team building, and getting to know each other in a lively and interactive way.
0 views • 6 slides
Improving Game Programming Patterns for Better Maintenance
In game development, synchronization with the render cycle is crucial to ensure smooth movement and user experience. The current approach of handling individual entities in the main game loop can lead to a cluttered and difficult-to-maintain codebase. By implementing the Update Pattern, where each e
0 views • 14 slides
Scalable Identity and Key Management for Publish-Subscribe Protocols
This research by Prashant Anantharaman from Dartmouth College focuses on scalable identity and key management for publish-subscribe protocols in Energy Delivery Systems. It discusses the architecture, goals, assumptions, and implementation results in the context of PKI vs. Macaroons protocols. The w
0 views • 37 slides
Insights into Marc Olano's Game Development Journey
Dive into the fascinating world of game development through Marc Olano's experiences, from his background in graphics hardware shading to team collaboration and project challenges. Get a glimpse of the evolution of game programming, customer-focused projects, and industry demos, all shaped by years
0 views • 18 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
Casino Game Development Mastery_ Your Ultimate Guide to Success in Online Gambling
Learn all about casino game development, key trends, and how casino game developers create engaging experiences through casino game development services.\n\nSource>>\/\/ \/casino-game-development-company\n\n
0 views • 5 slides
Unlocking the Casino Game Development Process in 7 Easy Steps
Discover the 7 easy steps to casino game development. Learn how casino game developers and casino game development services shape your platform's success.\n\nSource>>\/\/ \/casino-game-development-company\n\n
0 views • 3 slides
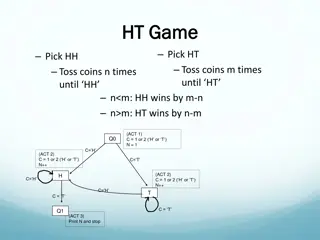
Interactive Coin Toss Game with Scanner Functionality
In this interactive game, players engage in a coin toss scenario where outcomes determine wins or losses based on specific patterns. Additionally, it features a scanner functionality that processes and categorizes input strings. The game mechanics involve making choices based on coin toss results, l
0 views • 8 slides
Casino Game Development company Services_ What to Expect for Your iGaming Platform
Discover what to expect from a casino game development company, including casino game developers, casino game development, and casino game development services.\n\nSource>>\/\/medium.com\/@aistechnolabspvtltd\/casino-game-development-company-services
0 views • 4 slides
Creating a Scratch Maze Game for Educational Use
Dive into the world of coding by learning how to create a maze game using Scratch, a fun and interactive platform for beginners. This activity is perfect for classrooms, small groups, or individual learners in elementary to high school grades. Gain hands-on experience in programming elements, game d
0 views • 8 slides
Improved Merlin-Arthur Protocols for Fine-Grained Complexity Problems
The text discusses Merlin-Arthur proof systems and protocols for central problems in fine-grained complexity, particularly focusing on the time complexity, completeness, and soundness of these protocols. It also touches on recent interest in these protocols and presents new results in areas such as
0 views • 16 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides