The Secure Path_ Implementing Digital Product Keys for Online Businesses (1)
Implementing digital product keys for online businesses offers a secure path towards protecting valuable software assets and ensuring compliance. By leveraging robust software key management systems, companies can enhance security measures, safeguard against unauthorized distribution, and mitigate p
1 views • 3 slides
The Secure Path_ Implementing Digital Product Keys for Online Businesses (1)
In today's digital landscape, where online businesses reign supreme, safeguarding products and services against piracy and unauthorized access is paramount. Enter the era of digital product keys \u2013 a secure path towards ensuring the integrity of online transactions and protecting intellectual pr
1 views • 3 slides
Effective Fundraising Strategies for Non-Profits: Unveiling the Keys to Success
Elevate your fundraising efforts with the 5 keys to successful fundraising, including building a strong team, choosing the right fundraiser, staying organized, following through, and utilizing raffles. Learn how to recruit volunteers, develop committees, engage sponsors/donors, and choose the right
0 views • 39 slides
Introduction to Components of a Computer System in Home Science
Explore the components of a computer system in Home Science, including input devices like the keyboard, alphanumeric keypads, cursor movement keys, and special keys such as Enter, Ctrl, Esc, and more. Learn about the internal structure of a computer system and the key functions of CPU, ALU, memory,
9 views • 12 slides
Understanding Renal Function Tests: Lecture Insights on Kidney Function and Structure
This lecture delves into the essential aspects of renal function tests, exploring the functional units of the kidney, the role of nephrons in maintaining homeostasis, and the intricate processes of filtration, reabsorption, and secretion within the renal tubules. Key topics include the hormonal and
4 views • 17 slides
windows 10 pro OEM kEYS
Windows 10 Pro OEM keys are digital licenses that activate Windows 10 Pro on a device. They're sold at lower prices than retail keys, often to system builders. These keys tie to the original hardware and offer full OS functionality, updates, and support. They're cost-effective for PC builders and in
3 views • 2 slides
Cracking the Code Understanding Windows 10 Pro OEM Keys
Understanding Windows 10 Pro OEM keys is crucial for activating licenses efficiently. OEM keys are linked to specific hardware, like pre-built systems, ensuring affordability but limited to that hardware. They're not transferable between devices. Retail keys, on the other hand, offer flexibility but
1 views • 8 slides
WindowKeys Unlocking the Power of Windows with Genuine License Keys
Windows with Genuine License Keys provide a secure and reliable operating system experience. These keys ensure that your version of Windows is legitimate and allows you to access all features and updates. With a genuine license key, you can activate your copy of Windows, receive support from Microso
4 views • 3 slides
Best Automotive Locksmith In Los Angeles
Need a skilled automotive locksmith in Los Angeles. A skilled locksmith with the ability to create car keys and fix ignition issues is known as an automotive locksmith. This locksmith can also fix your automobile's lock mechanisms and unlock your car. Car locksmith are capable of cutting car keys. W
10 views • 7 slides
Understanding Function Templates and Generic Programming in C++
Dive into function templates and generic programming in C++, exploring how to create reusable code for multiple data types. Learn about generic function templates, class templates, and how to declare function templates efficiently. Enhance your understanding of type-independent patterns and how to i
1 views • 32 slides
Understanding Renal Function Tests and Kidney Health
Renal function tests are essential for diagnosing and monitoring kidney health. These tests assess functions like glomerular filtration, tubular reabsorption, and endocrine functions of the kidneys. Common indicators include serum urea, creatinine levels, and more. It's crucial to evaluate renal fun
0 views • 34 slides
Understanding Dictionaries in Python
Dictionaries in Python allow storing elements with keys of various hashable types and values of any data type. Keys must be unique, but values can be duplicated. Dictionaries cannot be concatenated but can be nested. When passed to a function, dictionaries exhibit pass-by-reference behavior due to t
2 views • 14 slides
Understanding VSAM Logical Record Access Methods
VSAM utilizes three primary methods to find logical records - Relative Byte Address, Relative Record Number, and Key field. Relative Byte Address assigns a unique address to each record based on sequential ordering. Relative Record Number is used in RRDS datasets to access records by a numbered sequ
3 views • 35 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Understanding Keys in Relational Databases
Keys play a crucial role in relational databases by uniquely identifying records and establishing relationships between tables. Primary keys are essential for data integrity, ensuring each entity is identified uniquely. Learn about primary keys, types of keys, and examples of creating tables with pr
0 views • 57 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
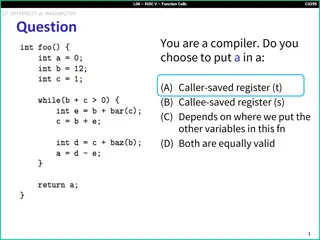
Understanding RISC-V Function Calls
In RISC-V function calls, the decision to place variables in caller-saved or callee-saved registers depends on various factors such as recursion and variable usage within the function. Additionally, understanding how function arguments are passed and stored is crucial for efficient program execution
0 views • 5 slides
Introduction to Gamma Function and Equivalent Integral Forms
The Gamma function is a versatile mathematical function that generalizes the factorial function to non-integer and complex values. It has various integral definitions such as the Euler-integral form. The proof of the factorial property of the Gamma function is demonstrated through analytical continu
1 views • 20 slides
Understanding the Key Concepts of Relational Databases
Introduction to the fundamental concepts of relational databases including the relational model proposed by Edgar F. Codd, relation schemes, relation instances, keys for a relation, and more. Discover the significance of keys, candidate keys, superkeys, and primary keys in database design.
0 views • 27 slides
Understanding Database Management Systems and Keys in SQL
This content discusses the importance of organizing data into multiple tables within a database management system, the concept of keys and foreign keys, and the potential issues of data redundancy. It also covers examples of structured data related to products, orders, and manufacturers.
0 views • 55 slides
Exploring Dichotomous Keys in Biology
Delve into the world of dichotomous keys with lessons on their types and practical application. Learn how to use these keys to identify various organisms and classify them based on specific characteristics. From distinguishing between different cat species to identifying aquatic organisms, this expl
0 views • 17 slides
Exploring Computer Keyboards And Typewriters
Dive into the world of computer keyboards and typewriters to understand their similarities and differences. Learn about the layout of alphabetic keys like QWERTY, utilizing the shift key for capitalization and special characters, the function of the enter key, differences between computer keyboards
0 views • 18 slides
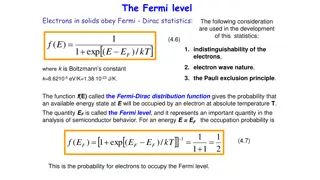
Understanding Fermi-Dirac Statistics in Solids
Electrons in solids obey Fermi-Dirac statistics, governed by the Fermi-Dirac distribution function. This function describes the probability of electron occupation in available energy states, with the Fermi level representing a crucial parameter in analyzing semiconductor behavior. At different tempe
0 views • 9 slides
Understanding the Nervous System: Structure and Function
The nervous system is a complex network divided into the central nervous system (CNS) and peripheral nervous system (PNS). Neuroglia, or supporting cells, play vital roles in maintaining the health and function of neurons. Neurons, the fundamental units of the nervous system, vary in structure and f
1 views • 29 slides
Overview of Graphing Techniques and Functions
Explore graphing techniques including stretching, shrinking, reflecting, symmetry, translations, and various types of functions such as the identity function, square function, cube function, square root function, cube root function, and absolute value function. Understand vertical and horizontal shi
0 views • 25 slides
Monitoring Thyroid Function After Head and Neck Cancer Treatment
This collection of images and data discusses the importance of monitoring thyroid function after head and neck cancer treatment, specifically focusing on post-treatment thyroid function tests, audits of practices in head and neck units, thyroid function post laryngectomy, and the significance of det
0 views • 11 slides
Understanding Alterations in Genitourinary Function: An Overview
The genitourinary system comprises the urinary and reproductive organs, with the kidneys, ureters, bladder, and urethra playing crucial roles. Maintaining proper function involves factors like renal blood flow, glomerular filtration, tubular function, and urine flow. Nephrons are the functional unit
0 views • 58 slides
Understanding Matching Keys in Database Systems
Matching keys play a crucial role in identifying the same real-world entities in database systems. They specify which attributes to compare and how to compare them, helping minimize redundancy and improve data accuracy. This summary discusses relative candidate keys, minimal matching keys, and relia
0 views • 13 slides
Understanding Memory Management in Computer Systems
Dive into the intricacies of memory management with Chapter 5 by Mooly Sagiv. Explore topics such as heap allocation, limitations of stack frames, currying functions, browser events in JavaScript, static scope for function arguments, result of function calls, closures, and more. Gain insights into m
0 views • 86 slides
Key and Splines Design at Minia University
Key and splines design play a crucial role in connecting mechanical elements like shafts and hubs to transmit power efficiently. This article covers the types of keys, principles of work, and various classifications of keys such as sunk keys, saddle keys, tangent keys, round keys, and splines. It de
0 views • 20 slides
Understanding C++ Templates: Generic Programming and Function Templates
Exploring the concepts of C++ templates including type-independent patterns for working with various data types, generic class patterns, function templates, and their usage. The reading covers examples of function templates for finding maximum values in vectors and highlights the importance of clear
0 views • 12 slides
Understanding Liver Function Tests and Their Significance
The liver carries out essential metabolic, excretory, protective, synthetic, and storage functions in the body. Liver function tests play a crucial role in screening for liver dysfunction, recognizing patterns of liver disease, assessing patient prognosis, monitoring disease progression, and evaluat
0 views • 48 slides
Understanding Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Analysis of WLAN Sensing Sequence Design Using Ambiguity Function and Range-Doppler Map
In this document, the authors from Huawei discuss the analysis of employing the ambiguity function for WLAN sensing sequence design. They delve into the ambiguity function's definition, analysis, and its comparison with the range-Doppler map. The document highlights the importance of ambiguity funct
0 views • 15 slides
Function-Based Behavior Support Plans: A Comprehensive Guide
Explore the process of developing Function-Based Behavior Support Plans (BSP) using Functional Behavioral Assessment (FBA). Understand the concepts of function and functional behavior assessment, learn how FBA/BSP fits within a multi-tiered support system, and practice developing BSP for students. D
0 views • 74 slides
The Case of the Missing Keys
In this amusing tale, Kylee Goodwin narrates the comical ordeal of her mum losing her keys yet again. The family embarks on a frantic search through various rooms, only for the keys to be found hanging safely on their hook by Dad in the end. A lighthearted story of everyday mishaps and the relief of
0 views • 13 slides
Advanced SQL Concepts and Queries Overview
Today's lecture highlights advanced SQL topics such as multi-table queries, set operators, joins, primary keys, foreign keys, and more. The session covers practical activities and fundamental concepts in database management. Explore the nuances of SQL semantics and understand the importance of keys
0 views • 55 slides
Understanding Database Constraints, Keys, and Triggers
Explore the concepts of constraints, foreign keys, local and global constraints, and triggers in the context of database management systems. Delve into topics such as types of constraints, keys, and expressing foreign keys with examples. Enhance your understanding of database integrity and data rela
0 views • 40 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
Understanding Computer Input Devices and Keystrokes
The system box of a computer contains essential components like the CPU, motherboard, and memory chips. Character keys, action keys, and application-dependent keys on a keyboard serve different functions, from typing letters to performing actions. Key combinations and shortcuts provide efficient way
0 views • 10 slides