Welcome to the Coding Adventure, where students thrive through development
Hey there, fellow code enthusiasts! \ud83d\ude80 Ready to embark on a journey of building something truly amazing with Java Full Stack Projects? Whether you\u2019re a seasoned developer or just dipping your toes into the coding world, get ready for an exciting adventure! \n\n \n\"Ever dreamt of crea
1 views • 2 slides
Mern Stack Training Institute in - Hyderabad
Visualpath is one of the best MERN Stack Training Course in - Hyderabad institutes in Hyderabad. We are providing Live Instructor-Led Online Classes delivered by experts from Our Industry. We will provide live project training after course completion. Enroll Now!! Contact us 91-9989971070.\nwhatsAp
1 views • 13 slides
MERN Stack Online Training - Courses - MERN STACK Training - Ameerpet
Visualpath offers the Best MERN STACK Training - Ameerpet by real-time experts for hands-on learning. Our MERN Stack Online Training - Courses is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us on wha
3 views • 13 slides
MERN Stack Training in Hyderabad - MERN Stack Training Course in Hyderabad
\nVisualpath offers the Best MERN Stack Training in Hyderabad by real-time experts for hands-on learning. Our MERN Stack Training Course in Hyderabad is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us
1 views • 13 slides
Stack Based Attacks in Linux (an intro)
Explore the world of stack-based attacks in Linux through an introductory session presented by Bryce L. Meyer at the Saint Louis Linux Users Group. Covering topics from weaknesses to exploits, shellcode, and mitigations like stack canaries and address space randomization, this overview delves into c
7 views • 60 slides
A Safety Expert’s Guide: How to Stack Pallets Safely
In the bustling world of warehouses, logistics, and manufacturing, the proper stacking of pallets is a critical aspect of maintaining a safe and organized workspace. As a safety expert, I\u2019ve seen firsthand the importance of implementing best practices to ensure the secure stacking of pallets. I
14 views • 2 slides
From Code to Career: The Role of Software Development Recruitment Agencies
Discover the pivotal role of software development recruitment agencies in navigating the journey from code enthusiast to established developer. Explore how these agencies specialize in connecting talent with opportunities, providing career guidance, and offering industry insights. Uncover the impact
9 views • 6 slides
Design Your Journey Enroll in the Best Full Stack Java Developer Course in Pune
Java is an extremely adaptable and robust programming language in the wide technology area. Ambitious developers can benefit greatly from having this ability due to its versatility and broad use across other disciplines. Pune has various options to launch your career if you're hoping to enter the fi
0 views • 3 slides
Design Your Journey Enroll in the Best Full Stack Java Developer Course in Pune
Java is an extremely adaptable and robust programming language in the wide technology area. Ambitious developers can benefit greatly from having this ability due to its versatility and broad use across other disciplines. Pune has various options to launch your career if you're hoping to enter the fi
1 views • 3 slides
10 Questions to Ask Before You Hire a Laravel Developer
Building a web application with Laravel? Finding the right developer is key. This post dives into 10 essential questions to uncover the perfect Laravel expert for your project's success. For more information, visit: \/hire-laravel-developer.
0 views • 5 slides
10 Common Mistakes to Avoid When You Hire an AngularJS Developer
Avoid costly mistakes when hiring an AngularJS developer! This guide explores 10 pitfalls to watch out for, ensuring you find the perfect candidate for your project. Learn how to assess technical skills, test for best practices, and uncover red flags. For more information, visit: \/hire-angularjs-d
0 views • 5 slides
10 Essential Skills to Consider When You Hire a PHP Developer
Learn the 10 essential skills you need to consider when hiring a PHP developer. Ensure your developer possesses the expertise required for successful web development projects. For more information, visit: \/hire-wordpress-developer.
1 views • 4 slides
The ROI of Hiring a Node.js Developer - Stats That Prove It’s Worthwhile
Explore the ROI of hiring a Node.js developer. Learn how Node.js boosts efficiency, scalability, and performance, driving better user experiences and higher conversion rates. Discover why it's a smart investment. For more information, visit: \/hire-node-js-developer. #hirenodejsdeveloper
1 views • 5 slides
The ROI of Hiring a Node.js Developer - Stats That Prove It’s Worthwhile
Explore the ROI of hiring a Node.js developer. Learn how Node.js boosts efficiency, scalability, and performance, driving better user experiences and higher conversion rates. Discover why it's a smart investment. For more information, visit: \/hire-node-js-developer. #hirenodejsdeveloper
0 views • 5 slides
Piezoelectric Stack Actuator Market Analysis, Size, Share, Growth, Trends Foreca
The Global Piezoelectric Stack Actuator market stands at the forefront of technological driving advancements in various industries through its dynamic applications. These actuator systems harness the unique properties of piezoelectric materials, providing precision and versatility in a range of mech
0 views • 8 slides
Efficient Stack Emission Monitoring Procedure for Air Quality Control
Stack emission monitoring is crucial for industries to assess and reduce pollutants in exhaust air. This procedure involves tasks like measurement, testing, and analysis of flue gases. Sampling sites are selected strategically for accurate readings, and molecular weight and gas velocity are determin
1 views • 11 slides
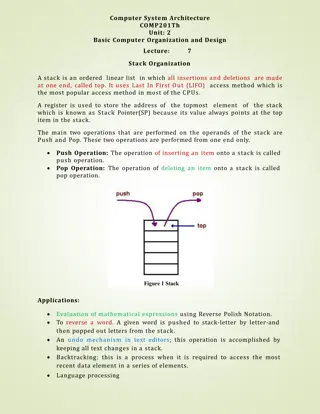
Stack Organization in Computer Systems
A stack is an ordered linear list where insertions and deletions occur at one end, known as the top. It follows the Last In First Out (LIFO) access method and is commonly used in CPUs. Key operations include Push (inserting) and Pop (deleting) items from the stack. Applications include evaluating ma
0 views • 5 slides
The Stack in Embedded Systems Design
The stack plays a crucial role in embedded systems design by providing a last-in, first-out storage structure for dynamic memory allocation. In this chapter, Dr. Brock J. Lameres explores the concept of the stack, its physical implementation in microcontrollers like the MSP430FR2355, and the operati
2 views • 27 slides
Software Processes and Models
This lecture discusses software processes, models, and activities involved in requirements engineering, software development, testing, and evolution. It covers topics such as process models, computer-aided software engineering (CASE) technology, software specification, design, validation, and evolut
2 views • 25 slides
Activation Records and Stack in Assembly Programming
Explore the key concepts of activation records and the stack in assembly programming, including their roles in function calls, memory management, and variable storage. Gain insights into the low-level layout of variables, call conventions in MIPS and x86, and practical examples illustrating stack op
2 views • 66 slides
X-Ray Film Processing Techniques
When a beam of photons exposes an X-ray film, it chemically alters the silver halide crystals, creating a latent image. Film processing involves developer, fixer, and a series of steps to convert the latent image into a visible radiographic image. The developer reduces silver ions in exposed crystal
2 views • 26 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
2 views • 17 slides
Software Measurement and Metrics in Software Engineering
Software measurement plays a crucial role in assessing the size, quantity, and quality of software products and processes. It involves direct and indirect measurement methods to monitor and improve software quality, predict future outcomes, and manage project budgets and schedules. Software metrics
0 views • 8 slides
Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
Software Cost Estimation in Software Engineering
Software cost estimation in software engineering involves predicting the resources required for a software development process. It includes fundamental estimation questions, software cost components, costing and pricing considerations, software pricing factors, and programmer productivity assessment
0 views • 30 slides
The Cost of Hiring a Node.js Developer What You Need to Know
The result of every software project depends on hiring the right people. The right developer is key when you use Node.js, the powerful and popular runtime for developing scalable apps. Although you can always find the right developer, evaluating the cost of their services will be one of the most cha
0 views • 6 slides
Top 10 Qualities to Look for When Hiring a WordPress Developer
In developing or maintaining a WordPress website, finding the perfect developer is the key. Whether it's advanced feature integration, theme adjustment, or building a whole new site, expert knowledge is required from a WordPress developer.
0 views • 5 slides
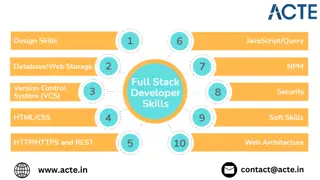
The Ultimate Guide to Becoming a Full Stack Developer: What You Need to Know
In the dynamic world of web development, the role of a full stack developer is highly sought after. These versatile professionals are capable of handling both the front-end and back-end aspects of web applications, making them invaluable assets to an
0 views • 1 slides
Yocto Project Developer Day - Advanced Class Summary
Explore the agenda, activities, and key details of the Yocto Project Developer Day Advanced Class. Learn about CROPS, containers for Yocto Project, available SDKs, Docker setup, and more. Discover how CROPS provides a consistent developer experience across different operating systems through the use
1 views • 145 slides
Protective Measures Against Stack Overflows
Host-based defenses such as Canaries, DEP, ASLR, and CFI play a crucial role in safeguarding systems against malicious attacks. Canaries act as early warning systems, alerting to stack overflows by monitoring changes in sensitive data. By implementing stack canaries, developers can prevent buffer ov
0 views • 51 slides
x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
1 views • 44 slides
Memory Stack and Variable Scope in Computer Architecture
This content delves into the scope of variables, the stack in memory architecture, automatic and global variables, and the concept of constant types. It explains the functioning of the stack, how function calls are managed, and the allocation of variables within stack frames. The relationship betwee
0 views • 18 slides
Best Full Stack Developer in United States
Recognized as the Best Full Stack Developer in the United States, I offer comprehensive expertise in both front-end and back-end technologies. I deliver robust, scalable solutions that drive innovation and performance for your web and mobile applicat
0 views • 5 slides
Insights from NATO Software Engineering Conferences and The Software Crisis of the Seventies
Exploring the challenges faced in software engineering during the 1970s, including issues such as project delays, inefficiencies, and the critical need for reliable, high-quality software. Insights from the NATO Software Engineering Conferences shed light on the struggle to meet increasing modern so
0 views • 46 slides
Stack Protection and Exploitation Techniques
Delve into the world of stack protection and exploitation, covering topics like exploiting arbitrary write, issues with stack canaries, and shadow stack usage. Explore defense mechanisms like Stack Cookie and learn about the power of exploiting vulnerabilities to write arbitrary memory. Discover met
0 views • 23 slides
Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
The Essence of Software Development Process
Software is a vital component in today's technology-driven world. It consists of instructions, data structures, and descriptive information that enable the functioning of computer programs. Unlike hardware manufacturing, software development is an engineering process that undergoes changes and deter
0 views • 74 slides
Software Engineering and Development Processes
Explore the key concepts of software engineering, including misconceptions, legacy software, and development phases. Learn about professional responsibilities, the need for software processes, the ETVX model, and different properties of software processes. Discover the components of software process
1 views • 57 slides
Neutral Gas Dynamics in the Edge: EIRENE Licence and Developer Code of Conduct
Task 5 discusses the licensing and developer code of conduct for EIRENE related to neutral gas dynamics in the edge. It encompasses the history, motivations, and feedback received, focusing on licensing agreements, developer groups, and ethical considerations. Various stakeholders are involved in sh
0 views • 6 slides
Hire Full Stack Developers for Tailored Web and App Development
Hire full stack developers for tailored solutions. Work with the best full stack development company in India to meet your business needs efficiently.\n\nSource>>\/\/ \/hire-full-stack-developers\n\n
0 views • 4 slides