A Problem: Analysis of Family Honor and Moral Dilemmas in Anton Chekhov's Work
Explores the moral dilemma faced by the Uskov family when dealing with Sasha's forgery and non-repayment, highlighting the differing views of paternal uncles and the eventual realization of Sasha's criminal tendencies despite the family's attempts to spare him from punishment.
0 views • 19 slides
Understanding Handwriting Analysis in Forensic Science
Handwriting analysis plays a crucial role in forensic science, especially in detecting forgery. Experts compare handwriting samples to determine authenticity, relying on distinct characteristics such as line quality, spacing, and pen pressure. Utilizing standards for comparison, they assess unique t
1 views • 11 slides
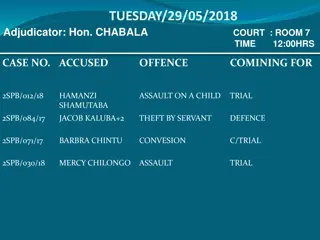
Court Case Schedule for 29th May 2018
On 29th May 2018, several court cases were scheduled with different adjudicators and courtrooms. The cases involved various offences such as assault, theft, forgery, and unlawful possession. Adjudicators included Hon. Chabala, Hon. Kapulo, Hon. Chibanga, Hon. Walusiku, Hon. Chitalu, Hon. Holland, an
0 views • 15 slides
Analysis of McEliece Vulnerabilities in Escher's World
In this detailed study by Ray Perlner and Dustin Moody from NIST, the vulnerabilities of McEliece in Escher's world are explored. The research covers error sets, commonalities with other variants, private key operations, decoding algorithms, encryption, and more. The findings shed light on potential
0 views • 25 slides
Exploring Handwriting Analysis, Forgery & Counterfeiting: An Insightful Guide
Delve into the fascinating world of handwriting analysis, forgery, and counterfeiting in Chapter 10. Explore different handwriting exemplars, understand forensic handwriting analysis goals, learn about technology used in analysis, distinguish between forgery and fraudulence, and discover ways busine
0 views • 26 slides
Decentralized Identity: Enhancing Trust in Web3.0 with DID
The emergence of Decentralized Identity (DID) is set to revolutionize digital identity systems by enhancing end-user trust, solving trust issues in current models, and paving the way for Web3.0. DID prevents forgery, eliminates passwords, and boosts operational efficiency. However, key obstacles lik
0 views • 5 slides
Understanding White Collar Crimes and Their Impacts
White collar crimes involve illegal activities committed by individuals of higher social class in professional settings. These crimes can include bribery, embezzlement, forgery, tax evasion, and fraud. They have significant economic repercussions and can erode investor trust in the market. Various t
2 views • 14 slides
Understanding White Collar Crime and Occupational Crime
White collar crime encompasses various offenses such as fraud, embezzlement, forgery, collusion, and tax evasion. This type of crime can often go undetected due to its complex nature and the difficulty in investigating it. Occupational crime, on the other hand, involves employees stealing from their
0 views • 7 slides
Overview of ASP.NET Tag Helpers in Web Applications
Learn about the usage of Tag Helpers in ASP.NET web applications, how they enable server-side code to create and render HTML elements in Razor files, and the benefits they offer in simplifying common tasks like form creation and asset loading. Explore the construction of forms using Tag Helpers, inc
0 views • 31 slides
Web Security Fundamentals: Understanding the Same Origin Policy
Explore the basic principles of web security focusing on the Same Origin Policy, operating system analogies, isolation of content sources, browser sandboxing, and setting cookies securely by servers. Learn how these concepts help ensure a safe browsing experience and prevent common vulnerabilities l
0 views • 37 slides
Detecting CSRF with Dynamic Analysis and Property Graphs
This content discusses the challenges and techniques involved in detecting Cross-Site Request Forgery (CSRF) through dynamic analysis and property graphs. It emphasizes the importance of understanding application states, request parameters, and state transitions to combat popular security risks like
0 views • 16 slides
Understanding Web Security: Same-Origin Policy in Web Applications
In web development, the Same-Origin Policy plays a crucial role in ensuring the security of web applications by restricting how documents or scripts loaded from one origin can interact with resources from another origin. This policy helps prevent malicious attacks such as Cross-Origin Request Forger
0 views • 25 slides
Web Application Vulnerabilities: A Growing Concern
Web application vulnerabilities like code injection, SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) are becoming more common, posing serious threats to online security. Developers must tackle the complexity of filtering input and ensuring secure code to prevent mali
0 views • 23 slides