Entry Requirements for Higher National Diploma & Bachelor Degree Programmes at UNISSA
Applications are open for admission to UNISSA's programmes, with applicants required to meet general and specific entry requirements. Equivalents like Higher National Diploma are considered, but meeting requirements does not guarantee entry. Various criteria apply, including qualifications, health s
2 views • 25 slides
Overcome Denied Entry to Canada
Experience the expertise of Northvistaimmigration.com and overcome the heartache of being Denied Entry to Canada. Let us help you navigate the immigration process with compassion and success.\n\n\n\/\/northvistaimmigration.com\/denied-entry-to-canada\/
4 views • 1 slides
Understanding Single Entry System in Financial Accounting
Single Entry System is a simplified method used by small businesses to track their financial transactions. It lacks the rigor of double-entry bookkeeping and focuses on recording cash transactions and personal accounts. This system presents challenges in accurately determining profits and financial
0 views • 14 slides
Religious Resources for Deterrence of Male Abusiveness in Intimate Relationships
This research project, conducted in collaboration with various organizations and experts, delves into the role of religion in deterring male abusiveness within intimate relationships. Findings suggest that religion can serve as a deterrent at both individual and normative levels, emphasizing faith-b
0 views • 9 slides
Understanding Trust in Contemporary Leadership
Trust is the foundation of effective leadership, comprising elements like integrity, competence, consistency, loyalty, and openness. Trust plays a crucial role in leadership, impacting team performance and cooperation. Different types of trust - deterrence-based, knowledge-based, and identification-
0 views • 9 slides
Understanding Coordinated Entry System (CES) in Homeless Services
Coordinated Entry is a strategic approach focusing on housing and service coordination to link individuals experiencing homelessness to appropriate resources. With a primary goal of quick identification and prevention of homelessness, the system assesses consumer needs and connects them to housing a
0 views • 12 slides
Understanding Entry-Level Driver Training (ELDT) Requirements
Entry-Level Driver Training (ELDT) is mandatory for entry-level commercial motor vehicle (CMV) operators in interstate and intrastate commerce who are obtaining a Class A or Class B CDL for the first time, upgrading their CDL, or adding specific endorsements. ELDT must be completed from a provider l
0 views • 9 slides
Understanding Double Entry Accounting System in Finance
There are two commonly known systems of accounting - single entry system and double entry system. Double entry system is the basis of modern day accounting and ensures accuracy by recording every transaction with dual aspects of debit and credit. By maintaining personal and impersonal accounts, it h
1 views • 7 slides
Understanding Entry and Exit Barriers in Industries
Entry and exit barriers play a significant role in shaping industry attractiveness and competitiveness. High entry barriers can deter new entrants, leading to stable returns but also higher risks. Conversely, low entry barriers may attract new players during economic upturns but result in intense ri
1 views • 15 slides
Comprehensive Confined Space Entry Training Guide
This training guide covers all aspects of confined space entry, including employee proficiency, safe performance, permit requirements, authorized entrants' duties, emergency services, and more. You'll learn about OSHA regulations, confined space definitions, examples, hazards, and general requiremen
0 views • 41 slides
Evolution of Police Methods in Criminal Justice
Traditional police methods in America primarily involved patrol officers and investigators, with a focus on deterrence, crime prevention, and solving crimes. However, proactive policing strategies emerged in the 1990s to address the limitations of traditional methods. Patrol remains a crucial aspect
5 views • 32 slides
Understanding Globalization and the Evolving Entrepreneurial Environment
Globalization is the increasing economic interdependence among countries worldwide, leading to cross-border transactions, technology diffusion, and international capital flows. It facilitates business expansion, erases market differences, and encourages global strategic orientations. Factors influen
0 views • 9 slides
New UCAS Tariff for Higher Education Entry Overview
UCAS has introduced a new Tariff for higher education entry starting from September 2017. This toolkit is designed to assist teachers and advisers in understanding the changes, timeline, points system, university examples, myth debunking, and available resources. The aim is to prepare educators and
0 views • 32 slides
Evolution of Punishment: From Brutality to Modern Criminal Justice System
Punishment for crime has evolved over time from brutal public spectacles to more civilized forms of discipline in modern society, reflecting changes in ruling class interests. The Criminal Justice System (CJS) focuses on deterrence, public protection, retribution, and rehabilitation. There has been
1 views • 25 slides
Wildlife Crime and Criminal Law: Understanding Concepts and Elements
Explore the intricate world of wildlife crime and criminal law in this module, covering topics such as defining wildlife crime, compliance approaches, the importance of addressing wildlife crime, motivations behind committing such crimes, and the international and regional dimensions of the issue. G
0 views • 57 slides
Impact of Rating-Based Platform Screening on New Complementor Entry
This study explores the effects of a platform design that ranks incumbent complementors based on review ratings on new complementor entry and overall complementor quality. The findings suggest that the rating-based platform screening reduces new complementor entry but enhances complementors' overall
1 views • 9 slides
Unpacking Self-Reinforcing Corruption Patterns
Delve into the complex dynamics of self-reinforcing corruption cycles and their implications for reform strategies. Explore how widespread corruption weakens deterrence, strengthens individual incentives for corruption, and impacts social norms against corrupt practices.
0 views • 45 slides
Enhancing Security Through Whole-of-Society Approach
United States European Command (USEUCOM) and ECJ9 are working to integrate interagency, private sector, NGOs, and local government partners to strengthen defense, deterrence, and resilience. Their focus is on countering hybrid threats, enhancing interoperability, and promoting full spectrum resilien
0 views • 8 slides
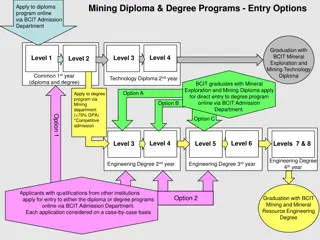
BCIT Mining Diploma & Degree Programs Entry Options
Explore the entry options for BCIT's Mining Diploma and Degree programs, including pathways for graduates to transition from the diploma to the degree program. Applicants can choose between diploma or degree programs based on their goals, with competitive admission criteria in place for direct entry
0 views • 10 slides
Understanding Entry and Exit Dynamics in Industries
Explore the fascinating world of entry and exit in industries, from the facts and barriers to Bain's typology of entry conditions and structural entry barriers. Learn about entry deterring strategies such as limit pricing, predatory pricing, and strategic bundling, and how they impact the market lan
0 views • 8 slides
Exploring Multi-Modal Text Entry and Selection on Mobile Devices
This study delves into the exploration of various input methods on mobile devices for text entry and selection. It compares traditional touch input with alternative methods such as tilt, speech recognition, and foot tapping. Through experiments, the study evaluates the performance benefits, expressi
0 views • 31 slides
Effective Strategies for Data Entry Integrity and Minimizing Errors
The chapter and subchapter discuss the importance of data integrity in the data management process, specifically focusing on data entry procedures, authenticity, and minimizing errors. It covers traditional manual data entry methods versus newer automated technologies, such as CAPI, and offers strat
0 views • 31 slides
U.S. Nuclear Weapons Budget for FY24 & Advocacy for Nuclear Threat Reduction Overview
The Fiscal Year 2024 budget for U.S. nuclear weapons activities is $56.6 billion, up by 11% from the FY23 request. The budget includes allocations for the Energy Department, Defense Department, and National Nuclear Security Administration for various nuclear weapon delivery systems and warheads. The
2 views • 5 slides
Understanding Comparative Property Law in the Contemporary Legal Landscape
Comparative Property Law explores the common challenges and fundamental questions of contemporary tort law, covering topics such as tort liability, legal positions protected by tort law, criteria for attributing liability, compensatory, deterrence, and punitive functions of tort law, and more. The i
0 views • 37 slides
Effective Double-Entry Journaling for Deeper Reading Engagement
Double-Entry Journaling is a powerful method to engage actively with reading, promote deeper comprehension, and facilitate effective study guides. This technique involves dividing a document into two columns, where the left column contains quotes, main ideas, and confusing passages, while the right
0 views • 12 slides
Enhancing Cyber Deterrence Strategies in the Modern Age
The current state of cyberspace reveals persistent threats targeting the U.S., emphasizing the need for effective deterrence strategies. Calls for a comprehensive cyber deterrence framework have been made by key committees, highlighting the urgency to develop response options, denial strategies, and
0 views • 33 slides
Retroactive Security Approach by Butler Lampson in January 2017
Retroactive security proposed by Butler Lampson addresses the limitations of traditional access control mechanisms. Emphasizing a focus on events that have actually occurred, this approach aims to improve real-world security by enabling accountability, blame assignment, and selective undo capabiliti
0 views • 20 slides
How to Fill Out the Junior Duck Stamp Program Entry Form
Properly fill out your child's Junior Duck Stamp Program entry form by providing group and student information, entry details, conservation message, supervising adult/teacher information, authenticity statement, submission guidelines, and deadline. Ensure original artwork, signatures, and mailing in
0 views • 7 slides
Exploring the Features and Structure of a Diary Entry
Dive into the features and structure of a diary entry, understand key elements such as past tense, writer's feelings, and informal language. Discover when to use different text styles and embark on a task to analyze a diary entry by highlighting grammatical and structural features. Plus, explore the
0 views • 6 slides
Understanding Threats and Responses in the Mobile App Market
The study explores the impact of platform-owner entry on complementors in the mobile app market, examining evidence from platforms like Facebook, Uber, Android, Alibaba, iOS, and WeChat. Concerns from complementors about imitation by platform owners are discussed, along with views from platform owne
1 views • 19 slides
Oligopoly Behavior: Excess Capacity Models and Entry Deterrence Strategies
Examine the concept of excess capacity models in oligopoly behavior, where a monopolist may strategically deter entry by either building excess capacity or expanding current production facilities in response to potential entrants. Explore scenarios involving sunk costs, marginal costs, pricing strat
0 views • 37 slides
Future Growth and Economic Impacts of GBSD Program in Northern Utah
Ground Based Strategic Deterrence program is set to bring substantial growth opportunities to Northern Utah, with an influx of jobs, economic impacts, and community development. The program's current situation at Hill AFB shows stability and promising future prospects, with significant contracts awa
0 views • 12 slides
Single Firefighter Forcible Entry through Inward Swinging Door
Follow these steps for a single firefighter forcible entry through an inward swinging door: assess the door size and shock the door jamb, insert the adz end for mechanical advantage, use an axe as a wedge, create a gap using the butt of the axe, advance the halligan tool to force entry efficiently.
0 views • 6 slides
Insights on Entry and Exit Dynamics in Industries
Exploration of the entry and exit dynamics in industries, covering factors influencing the establishment of new firms, barriers to entry, Bain's typology of entry conditions, structural entry barriers, and entry-deterring strategies employed by incumbents. Insights include the impact on the market l
0 views • 7 slides
Understanding Deterrence Theory and Classical Criminology
The content provides an overview of deterrence theory, focusing on key figures, assumptions, general and specific deterrence, research, and policy implications. It also delves into classical criminology, discussing key figures like Jeremy Bentham and Cesare Beccaria, concepts such as felicity calcul
0 views • 21 slides
Understanding the Aims of Punishment and Evaluating Deterrence as an Effective Aim
Explore the aims of punishment and the reasons behind punishing criminals in different ways through a series of tasks. Match descriptions to aims, identify and explain key aims of punishment, and evaluate the effectiveness of deterrence as a primary aim. Provide reasoned arguments, consider religiou
0 views • 4 slides
Understanding Sequential Games in Game Theory
Explore the concept of sequential games in game theory through an entry deterrence game involving an incumbent monopolist and a potential entrant. The game tree depicts various outcomes based on choices made by players, leading to discussions on Nash Equilibrium, credible commitments, and backward i
0 views • 17 slides
BioLock Biometric Home Entry System Overview
BioLock is a biometric home entry system developed by Mavis Chan, Brent Erickson, and Sydney Bitner of Group 9. It features a fingerprint-enabled lock for secure home access, allowing homeowners to check access history remotely and receive alerts for unauthorized entry attempts. The system utilizes
0 views • 12 slides
Naval Nuclear Dynamics in the Indian Ocean: Implications for South Asia and the United States
Delve into the complexities of naval nuclear dynamics in the Indian Ocean, exploring strategic developments, India's sea-based deterrence efforts, and the geopolitical implications for South Asia and the United States. Assess the simultaneous rise of China and India, the influence of major chokepoin
0 views • 14 slides
Stress Ulcer Prophylaxis in ICU Data Entry System - SUP-ICU Overview
Dive into the Stress Ulcer Prophylaxis in the Intensive Care Unit (SUP-ICU) data entry system led by Dr. Soeren Marker Jensen. Explore screening, randomization, site overview, and data entry processes. Access participant details, edit submitted data, and learn about data entry guidelines. Enter the
0 views • 28 slides