How to Use Blockchain Technology to Secure Your Dating App Data
Discover the transformative power of blockchain technology in securing data for dating app development solutions. Eliminate single points of failure with decentralized storage, boosting redundancy. Ensure immutable integrity, preventing unauthorized modifications to user data. Facilitate secure mess
1 views • 4 slides
Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
Ask On Data for Efficient Data Wrangling in Data Engineering
In today's data-driven world, organizations rely on robust data engineering pipelines to collect, process, and analyze vast amounts of data efficiently. At the heart of these pipelines lies data wrangling, a critical process that involves cleaning, transforming, and preparing raw data for analysis.
2 views • 2 slides
Data Wrangling like Ask On Data Provides Accurate and Reliable Business Intelligence
In current data world, businesses thrive on their ability to harness and interpret vast amounts of data. This data, however, often comes in raw, unstructured forms, riddled with inconsistencies and errors. To transform this chaotic data into meaningful insights, organizations need robust data wrangl
0 views • 2 slides
Fully Homomorphic Encryption: Foundations and Applications
Fully Homomorphic Encryption (FHE) allows computations on encrypted data without decrypting, enabling secure outsourcing of computations to untrusted servers. FHE involves key generation, encryption, homomorphic evaluation, and decryption processes. It ensures correctness, security, and compactness
0 views • 31 slides
Configuring Local Storage and File System in Linux System Administration
This module focuses on LUKS-Encrypted File Systems in Linux, detailing their design, benefits, and how to mount, unmount, and remove them securely. LUKS provides a secure standard for hard disk encryption, supporting multiple keys/passphrases and enabling effective passphrase revocation. Learn how t
0 views • 50 slides
Understanding Data Governance and Data Analytics in Information Management
Data Governance and Data Analytics play crucial roles in transforming data into knowledge and insights for generating positive impacts on various operational systems. They help bring together disparate datasets to glean valuable insights and wisdom to drive informed decision-making. Managing data ma
0 views • 8 slides
Introduction to Cryptography, Cryptanalysis, and Cryptology
Cryptography involves protecting information by encrypting and decrypting data, while cryptanalysis focuses on breaking encryption methods to access hidden messages. Cryptology encompasses both cryptography and cryptanalysis. Encryption encodes messages to prevent unauthorized access, while decrypti
0 views • 12 slides
Exploring Cloud Cryptography for Secure Data Processing
Cloud cryptography is a vital aspect of data security in cloud computing, allowing data to be encrypted and processed securely. This presentation delves into the concepts of cloud cryptography, homomorphic encryption, and the two types of homomorphic encryption - hybrid and partial. It discusses the
8 views • 17 slides
Secure Multiparty Computation for Department of Education Data Sharing
This report discusses the use of Secure Multiparty Computation (SMC) to enable sharing of sensitive Department of Education data across organizational boundaries. The application of SMC allows for joint computation while keeping individual data encrypted, ensuring privacy and security within the Nat
0 views • 15 slides
Secure Memory Encryption Techniques for Virtual Machines across Multiple Hosts
Virtual machines with large memory capacities are common in cloud environments. To enhance security during VM migrations and data transmissions, techniques like split migration, encrypted split migration, and encrypted remote paging are employed. However, challenges such as data leakage, high CPU ut
0 views • 16 slides
Protecting User Privacy in Web-Based Applications through Traffic Padding
Explore a novel approach utilizing knowledge-resistant traffic padding to safeguard user privacy in web-based applications. The study addresses side-channel attacks on encrypted traffic, the challenges of maintaining security in untrusted internet environments, and the potential privacy overhead of
0 views • 31 slides
Evolution and Benefits of Flock Safety Cameras in Law Enforcement
Crime is evolving rapidly, and law enforcement needs to adapt to new technology to combat criminals effectively. Flock Safety Cameras offer advantages such as quicker response times, enhanced preventative measures, and improved crime mapping capabilities. These cameras help in scanning license plate
0 views • 12 slides
Security with Functional Re-Encryption in Cryptography
Exploring the concept of functional re-encryption from the perspective of security in encryption schemes lies between CPA and CCA security levels. The work done by Yevgeniy Dodis, Shai Halevi, and Daniel Wichs delves into how functional re-encryption can enhance the security and privacy of encrypted
0 views • 12 slides
Efficient Rekeying for Encrypted Deduplication Storage
Cloud storage outsourcing is common today, presenting challenges like security and storage efficiency. Encryption and deduplication play crucial roles in addressing these challenges. However, traditional encryption methods inhibit deduplication. Rekeying offers a solution by renewing security protec
0 views • 27 slides
Secure Multiparty Computation: Enhancing Privacy in Data Sharing
Secure multiparty computation (SMC) enables parties with private inputs to compute joint functions without revealing individual data, ensuring privacy and correctness. This involves computations on encrypted data using techniques like homomorphic encryption for scenarios like e-voting. SMC serves as
2 views • 27 slides
A New Approach to TLS Inspection
This article explores a new approach called IA2-TLS for inspecting Transport Layer Security (TLS) anytime and anywhere. It discusses the primary goals of TLS, the increasing importance of data encryption over networks, and the need for TLS inspection to enhance security controls. The challenges of i
1 views • 46 slides
WhatsApp End-to-End Encrypted Backup Protocol Security Analysis
This security analysis delves into the WhatsApp end-to-end encrypted backup protocol, highlighting the potential risks associated with chat history backups. It discusses the dangers of password guessing, the vulnerabilities of cloud providers, and proposes solutions for a more secure backup system t
0 views • 20 slides
Mitigating Conflict-Based Attacks in Modern Systems
CEASER presents a solution to protect Last-Level Cache (LLC) from conflict-based cache attacks using encrypted address space and remapping techniques. By avoiding traditional table-based randomization and instead employing encryption for cache mapping, CEASER aims to provide enhanced security with n
1 views • 21 slides
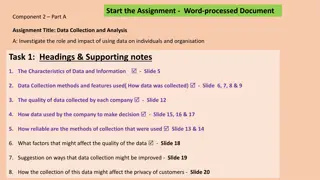
Understanding Data Collection and Analysis for Businesses
Explore the impact and role of data utilization in organizations through the investigation of data collection methods, data quality, decision-making processes, reliability of collection methods, factors affecting data quality, and privacy considerations. Two scenarios are presented: data collection
1 views • 24 slides
Encrypted Deduplication for Secure Cloud Storage
Encrypted deduplication enhances data storage efficiency by eliminating duplicate chunks and encrypting outsourced data to protect against cloud service providers. This approach uses message-locked encryption and metadata management to store unique data and key mappings securely. By leveraging encry
0 views • 24 slides
Homomorphic Encryption Overview
Homomorphic encryption allows computation on encrypted data without revealing the underlying information. It enables secure delegation of data processing to a server while maintaining privacy. The process involves key generation, encryption, decryption, and evaluation of functions on encrypted data.
0 views • 40 slides
Securing Protocols with Fully Encrypted Protocols (FEPs)
In this research presented at the Cryptographic Applications Workshop, Ellis Fenske and Aaron Johnson address the challenges of Fully Encrypted Protocols (FEPs). They highlight the lack of precise understanding, formalized goals, and proven security in existing FEPs. The work introduces new security
0 views • 29 slides
Bootstrapping in Fully Homomorphic Encryption
Fully Homomorphic Encryption (FHE) allows evaluation of unbounded-depth circuits without being limited by specific parameters. Bootstrapping is a critical technique to achieve full homomorphism by refreshing ciphertexts, enabling decryption functionalities within the encryption scheme. This process
0 views • 38 slides
Microsoft BizTalk - Connecting Line-of-Business Applications
Paul Larsen, Principal Program Manager at Microsoft, leads the BizTalk initiative to seamlessly connect line-of-business applications across enterprises. BizTalk Services and Tools offer production deployment to Azure VMs, SQL Server 2016 integration, advanced adapters, logic app integration, and en
0 views • 10 slides
Homomorphic Encryption and RLWE Schemes Overview
Homomorphic encryption allows computation on encrypted data, enabling privacy in outsourced computing services and applications like spam filters for encrypted mail. The Ring Learning With Errors (RLWE) scheme and its properties are discussed, along with symmetric encryption from RLWE and fully homo
0 views • 16 slides
Advancements in Multi-Key Homomorphic Encryption Using TFHE
Revolutionary research has led to the development of Multi-Key Homomorphic Encryption (MKHE) from TFHE, enabling secure and efficient computations on encrypted data. This technology offers advantages such as dynamic operability, stronger security, and minimized interaction, making it an ideal soluti
0 views • 20 slides
User Workgroups FAQs on Case Mix Questions and Data Handling
Explore common user questions on case mix data, including the differences between single and multiple use, adding new users to projects, fee payment procedures, calculation methods, and guidelines regarding encrypted hard drives for MA APCD and Case Mix data delivery.
0 views • 6 slides
EGI Installation Check-in Updates and Support Activities
The EGI foundation, funded by the European Commission, has implemented various updates in their Installation Check-in process. These updates include adding support for AES-GCM encrypted attribute assertions, enabling expiration policies, improving user notifications, and deploying a new Federation R
0 views • 15 slides
Data Protection Best Practices for Secure Storage and File Encryption
Safeguarding data is crucial to prevent potential risks such as lost or stolen laptops, data breaches, and unauthorized access. This involves strategies like secure storage, encryption of file systems, and sharing encrypted files with authorized users. Implementing strong password-based file encrypt
0 views • 24 slides
Encrypted Data Deletion for Cloud Storage Servers
Explore the concept of software with certified deletion for private cloud storage servers. Discover how data recoverability is influenced by secret key leaks and encryption scheme vulnerabilities. Learn about techniques for computing on encrypted data and ensuring provable deletion, with a focus on
0 views • 29 slides
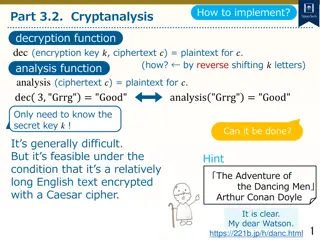
Understanding Cryptanalysis: Key Concepts and Techniques
Cryptanalysis is a fundamental aspect of cryptography that involves decoding encrypted communications and messages. This topic delves into the basic cryptographic tools, such as the Caesar cipher, and explores how encryption and decryption functions work. By understanding cryptanalysis, you can anal
0 views • 12 slides
Cryptanalysis and Decryption Techniques for Caesar Cipher
Learn how to decrypt Caesar cipher text using cryptanalysis techniques by analyzing letter frequencies and determining the secret key through character analysis. Explore methods to count character frequencies and find the most common letter to decipher encrypted messages.
0 views • 11 slides
Optical Security with Double Random Fractional Fourier Domain Encoding
Utilizing double random fractional Fourier domain encoding for optical security involves encryption and decryption methods based on the fractional Fourier transform of various orders, involving specific mathematical operations and notations. The process includes transforming the input function, encr
0 views • 13 slides
Client Privacy Preservation through Secured DNS - Feisty Forwarders
Feisty Forwarders, led by Dr. Amrita Mishra, is a team dedicated to client privacy preservation via secured DNS. They focus on developing protocols that hide IP addresses and encrypt all incoming and outgoing traffic to protect users from potential spies on the internet. With expertise in programmin
0 views • 11 slides
Enhancing Messaging and Network Security Beyond Email
Today's session with Joe St. Sauver covers cryptographic privacy protection for messaging beyond email and securing high-speed internal links. The discussion emphasizes the importance of safeguarding mobile voice communication, highlighting various use cases and addressing concerns about the impact
0 views • 65 slides
Oblivious RAM and Software Protection: An Overview
Oblivious RAM (ORAM) and software protection against piracy involve securing hardware and encrypted programs to prevent unauthorized access. With a focus on achieving security through encryption and indistinguishability, concepts like access patterns and data request sequences play a crucial role. T
0 views • 26 slides
Secure Out-of-Band Remote Management Using Encrypted Virtual Serial Consoles in IaaS Clouds
IaaS clouds provide virtual machines for users to manage through SSH. In scenarios where in-band remote management is not feasible, out-of-band remote management using Virtual Serial Consoles (VSC) offers a secure solution. However, challenges such as untrusted admins and potential attacks exist, wh
0 views • 22 slides
Data Encryption and File Security Overview
Explore the complexities and challenges of encrypting stored data, file encryption, and ensuring secure systems. Learn about the scenarios where data encryption is crucial, the limitations of file encryption, and the importance of secure data wiping practices for maintaining confidentiality. Delve i
0 views • 30 slides
Crack the Code: The Fascinating World of Cryptography
Discover the intriguing world of cryptography through a journey into the history and methods of code-making and code-breaking. Uncover the importance of codes in everyday life, from book ISBNs to encrypted internet data, and learn about classic techniques like Caesar shifts. Test your skills by deco
0 views • 4 slides