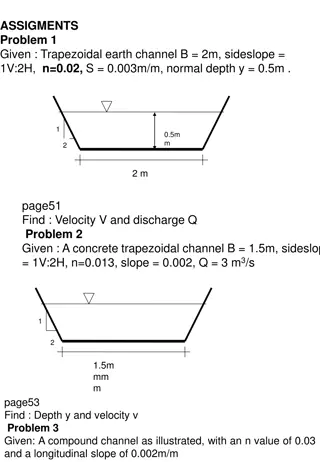
Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
6 views • 5 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
9 views • 11 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
0 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Understanding Amazon EC2: Elastic Compute Cloud Fundamentals
Amazon Elastic Compute Cloud (EC2) is a web service provided by Amazon Web Services (AWS) that offers resizable compute capacity in the cloud. EC2 allows users to rent virtual servers known as instances to run applications. Key features include various instance types, Amazon Machine Images (AMIs), s
11 views • 5 slides
Understanding Water Hammer Phenomenon in Fluid Systems
Water hammer is a significant issue caused by sudden changes in fluid velocity, commonly encountered in hydraulic systems when valves are closed rapidly. This phenomenon, also known as hydraulic shock, can have serious consequences if not managed properly. The content discusses the time of pressure
3 views • 5 slides
Understanding Transition States and Nudged Elastic Band in Applied Physics
Description of transition states, potential energy surfaces, saddle points, minimum energy paths, and the Nudged Elastic Band method in the context of applied physics. The content explains key concepts such as transition states along reaction coordinates, the significance of potential energy surface
0 views • 9 slides
Understanding Stress-Strain Behavior in Mechanical Engineering
The article explores the concepts of strain, stress, and the stress-strain diagram in mechanical engineering. It covers topics such as Hooke's Law, elastic limit, and the elastic and plastic ranges in materials. Various diagrams and explanations offer insights into the behavior of materials under di
1 views • 11 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
Understanding Price Elasticity of Supply: Degrees and Concepts
Explore the concept of Price Elasticity of Supply (PES) through definitions, descriptions of elasticity degrees, and examples like perfectly inelastic, fairly elastic, and unitary elastic. Engage in an activity to deepen your understanding.
0 views • 5 slides
Understanding Elastic Potential Energy Concepts
Explore the concepts of elastic potential energy, kinetic energy calculations, storing energy, and rearranging equations with practical examples and self-assessment tasks to deepen your understanding of the topic.
0 views • 11 slides
Understanding Monetary Policy Effectiveness in the IS-LM Framework
The relative effectiveness of monetary policy in influencing investment, employment, output, and income depends on the shape of the LM curve and the IS curve. A steeper LM curve signifies higher effectiveness as it indicates less interest elastic demand for money, resulting in significant changes in
0 views • 24 slides
Insights on Price Elasticity of Demand and Consumer Behavior
Understanding the concept of price elasticity of demand, this content explores how changes in price affect consumers' buying behavior. It covers the Veblen effect, Giffen goods, Marshall's example on staple foods, and the responsiveness of demand to price fluctuations. The content also explains elas
5 views • 31 slides
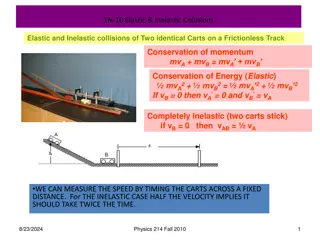
Understanding Elastic and Inelastic Collisions in Physics
Exploring the concepts of elastic and inelastic collisions, momentum, impulse, and energy conservation in physics. Topics include measuring speed, advantages of airbags, impact of catching objects, and understanding forces in collisions. Images and explanations demonstrate key principles in physics.
1 views • 25 slides
Understanding Elastic Wave Equations in Seismology
Explore the fundamentals of elastic wave equations for seismology, including topics such as plane wave propagation, reflection coefficients, and wavefield simplifications using curl and div operators. Learn about P-waves, shear waves, and elastodynamic potentials in the context of infinite homogeneo
0 views • 31 slides
Understanding Federalism in the United States
Federalism in the United States involves the relationship between the federal government and state governments, with terms such as delegated powers, reserved powers, concurrent powers, and the Elastic Clause playing key roles. The aftermath of events like Hurricane Katrina and policies such as No Ch
0 views • 30 slides
Overview of Special Connective Tissue: Cartilage - Histology by Dr. Ammar Ismail
Cartilage is a specialized connective tissue with chondrocytes in lacunae, lacking vasculature and nerves. Hyaline cartilage is common in the body, while elastic cartilage contains elastic fibers, and fibrocartilage is associated with dense connective tissue. Cartilage growth occurs through chondroc
0 views • 20 slides
Elastic Parity Logging for SSD RAID Arrays
SSDs are widely used for their performance and efficiency, but face challenges like flash errors and poor random write performance. The paper introduces EPLog, a new RAID design for SSD arrays, enhancing reliability, endurance, and performance through elastic parity logging. The solution redirects w
0 views • 23 slides
Impulse Excitation Technique for Monitoring Green Ceramics During Firing
The Impulse Excitation Technique (IET) is a nondestructive testing method employed to monitor the elastic properties of green ceramics as they undergo firing processes. This technique allows for the analysis of phase changes and material behavior at high temperatures, providing valuable insights int
0 views • 6 slides
Experimental Setup at IP5 for Inelastic Events and Particle Detection
Experimental setup at IP5 involves inelastic telescopes for charged particle detection and vertex reconstruction. The setup includes T1 and T2 telescopes, HF and CASTOR detectors, as well as Roman Pots for measuring elastic and diffractive protons. The TOTEM experiment focuses on proton-proton inter
0 views • 27 slides
Mixed Elastic Scattering Format Proposal
This proposal focuses on introducing a Mixed Elastic Scattering format to address the need for a more rigorous treatment of thermal elastic scattering effects in selected nuclides. The format extension, compatible with ENDF-6, supports advanced moderator development without impacting existing TSL ev
0 views • 6 slides
Understanding Elastic Pendulum: Observing Changes in Spring Forces
In this activity, students analyze variations in the periodicity of the elastic force of a spring acting as a pendulum. The objective is to estimate approximate values for pendulum and elastic oscillation periods and establish a relation between them. The theory explains the behavior of oscillatory
0 views • 21 slides
Understanding Elastic Potential Energy and Energy Conservation Principles
Elastic potential energy is stored in elastic bodies like springs and is vital in understanding energy conservation principles. This energy can be calculated using the work done by an ideal spring on a block. By applying elastic potential energy concepts, one can analyze scenarios where a spring sys
0 views • 9 slides
Analysis of Torsion in Isotropic Cosserat Elastic Cylinder using COMSOL
Explore the extension of linear elastic material model to a Cosserat material, including microrotation degrees of freedom, with a focus on a cylindrical bar under pure torsion. Investigate the impact of Cosserat length scale parameter on the system response, analyzing different zones of behavior. Re
0 views • 8 slides
Understanding Elasticity of Demand and Factors Affecting It
Identify the characteristics of elastic and inelastic demand, define terms like Elasticity, Elastic Demand, and Inelastic Demand. Explore why we still buy gas despite rising prices, the concept of elastic and inelastic demand using examples like pants and apple juice. Learn about factors influencing
0 views • 16 slides
Understanding Price Elasticity of Demand in Economics
Price elasticity of demand is a crucial concept in economics that measures how much the quantity demanded of a good changes in response to a change in its price. Factors influencing own-price elasticity, cross-price elasticity, income elasticity, and supply elasticity are explained and illustrated u
0 views • 19 slides
Elastic Execution with CloneCloud: Enhancing Mobile Applications
The CloneCloud system introduces elastic execution capabilities, enabling the seamless offloading of resource-intensive tasks from mobile devices to the cloud. Byung-Gon Chun, Mayur Naik, Sunghwan Ihm, Petros Maniatis, and Ashwin Patti present a flexible architecture that optimizes application perfo
0 views • 28 slides
Challenges and Solutions in Elastic Cloud Security
Elastic clouds bring benefits like rapid scalability, but also pose security challenges. These include issues with data storage, processing, virtual networks, and overall cloud security. Key challenges involve multi-tenancy, data mobility, and privacy. Solutions entail easy deployment, secure key ma
0 views • 22 slides
Investigation of Spin Observables in Elastic pp and p(bar)p Scattering at SPASCHARM Program
Measurements of spin observables in elastic pp and p(bar)p scattering at 16 GeV will be conducted at the SPASCHARM program using a unique setup with polarized proton and antiproton beams. The experiment aims to extend the energy range for spin studies and compare elastic scattering in pp and p(bar)p
0 views • 24 slides
Understanding Elasticity in Economics
Elasticity in economics refers to the responsiveness of demand to price changes. A more elastic curve results in larger quantity changes for small price changes, while a less elastic curve requires larger price changes to affect quantity consumed. The elasticity of demand can be measured by calculat
1 views • 13 slides
Understanding Price Elasticity of Supply in Economics
Price elasticity of supply measures how much the quantity supplied responds to changes in price. It can be inelastic (quantity supplied responds slightly), elastic (quantity supplied responds substantially), or unit-elastic (price elasticity of supply equals 1). Various determinants like the passage
0 views • 16 slides
Understanding Degrees of Elasticity of Demand
Elasticity of demand refers to the responsiveness of quantity demanded to changes in price. Perfectly elastic demand occurs when there is an infinite demand at a particular price and demand becomes zero with a slight rise in price. Conversely, perfectly inelastic demand occurs when there is no chang
0 views • 11 slides
Mechanical Behavior of Structures: Stress-Strain Diagrams and Elastic Properties
Understanding the mechanical behavior of structures involves analyzing stress-strain diagrams, distinguishing between ductile and brittle materials, exploring linear and non-linear elastic properties, studying plastic deformation, yield strength, ultimate tensile strength, and toughness. Elastic beh
0 views • 32 slides
Enhancing Scrub Seal Emulsions for Asphalt Mix Rejuvenation
Activities of the Spray Group involve developing effective materials specifications for scrub seal emulsions with rejuvenators to properly rejuvenate cracked asphalt mixes. The purpose is to ensure successful applications with the most effective products. Consideration of elastic polymers, non-elast
0 views • 4 slides
Elastic Security Virtualization with vNIDS
Explore the concept of Elastic Security through Safe and Efficient Virtualization of Network Intrusion Detection Systems using vNIDS. This study delves into the challenges of traditional NIDSes, the requirements for virtualized environments, traffic volume variations, new trends in network function
0 views • 36 slides
Elastic Net Regularized Matrix Factorization for Recommender Systems
This research paper presents an elastic net regularized matrix factorization technique for recommender systems, focusing on reducing the dimensionality of the problem and utilizing features to describe item characteristics and user preferences. The approach combines existing algorithms and applies e
0 views • 27 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Understanding Elastic Properties of Solids: Stress, Strain, and Modulus
Explore the concept of elasticity in solids through stress and strain analysis, defining elastic moduli such as Young's modulus, shear modulus, and bulk modulus. Discover how these properties describe the behavior of various materials under deformation. Quick quizzes demonstrate application scenario
0 views • 16 slides