The Right to Vote
Join Tom Patterson in this McGraw-Hill webinar on September 15, 2023, as he discusses the conflicting constitutional provisions for the right to vote and the impact on Supreme Court decisions. Explore the politics of ballot access and the historical context of voter suppression. Learn about key poin
2 views • 38 slides
Infrastructure as a Service (IaaS) - Amazon EC2
Capabilities of Infrastructure as a Service (IaaS) with Amazon EC2, including scalable computing resources, on-demand capacity, and self-service access to servers, software, and storage.
4 views • 13 slides
Efficient Key Recovery Attack on SIDH
Efficient key recovery attack on Supersingular Isogeny Diffie-Hellman (SIDH) protocol. It explores the vulnerability of the protocol and proposes a concrete solution. The attack leverages auxiliary points to solve the isogeny problem and reveals instances of the common secret key.
5 views • 22 slides
While waiting for assembly to begin have a think of one thing you are thankful for.
Harvest is a time to celebrate the abundance of food grown on the land. While the world can produce enough food to feed every person twice over, hunger still persists in various parts of the world, including the UK where over 13 million people live below the poverty line, leading to instances where
0 views • 17 slides
Implementation of Discharge Card PHB Pilot for Safe and Early Discharge
Addressing the challenge of patients occupying hospital beds unnecessarily, the report focuses on the implementation of the Discharge Card PHB pilot program aiming to facilitate safe and early discharge in hospitals. Real-world barriers and opportunities for optimal e-wallet use in London are explor
3 views • 37 slides
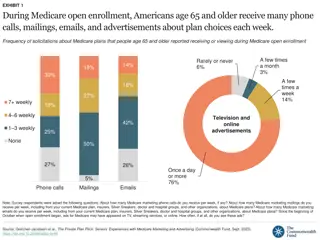
Seniors' Experiences with Medicare Marketing and Fraud
During Medicare open enrollment, seniors age 65 and older receive numerous solicitations about plan choices through phone calls, mailings, emails, and advertisements. The frequency of these marketing efforts varies, with some seniors reporting misleading information and fraudulent practices by marke
1 views • 10 slides
Understanding Amazon EC2: Elastic Compute Cloud Fundamentals
Amazon Elastic Compute Cloud (EC2) is a web service provided by Amazon Web Services (AWS) that offers resizable compute capacity in the cloud. EC2 allows users to rent virtual servers known as instances to run applications. Key features include various instance types, Amazon Machine Images (AMIs), s
11 views • 5 slides
Understanding MPAI's Role in Metaverse Interoperability
MPAI, spearheaded by Leonardo Chiariglione, plays a crucial role in defining standards and technologies for the metaverse, ensuring interoperability between different metaverse instances. This involves functional and prescriptive interoperability, enabling seamless data exchange and operation models
3 views • 38 slides
Understanding Data Use Agreements (DUAs) in Sponsored Projects Office
Data Use Agreements (DUAs) are contractual agreements between data providers and recipients, ensuring proper handling of non-public data, especially data subject to restrictions like HIPAA. DUAs address data use limitations, liability, publication, exchange, storage, and protection protocols. HIPAA
6 views • 19 slides
Understanding Quantified Statements
Explore the logic of quantified statements, including universal instantiation, universal modus ponens, and examples illustrating the application of these concepts using variables, predicates, and symbols. Dive into the reasoning behind statements involving particular instances within a domain, and s
6 views • 22 slides
Understanding Antepartum Haemorrhage and Placenta Praevia
Antepartum haemorrhage, especially in cases of placenta praevia, can present challenges in pregnancy. This condition, where the placenta covers or is near the cervix, requires careful monitoring and may necessitate interventions like ultrasound scans and potential hospital admissions. Risk factors f
7 views • 15 slides
Guidelines for Upholding Rights of LGBTQ
In light of evolving societal norms and the imperative to safeguard the rights and dignity of LGBTQ individuals and inter-faith\/inter-caste couples, the Supreme Court has given guidelines for the handling of habeas corpus petitions and petitions for police protection.\nBackground:\nRecent instance
9 views • 4 slides
Global Identity Verification Market Size & Analysis _ BIS Research
The Global Identity Verification Market has witnessed exponential growth in recent years, driven by factors such as increasing instances of identity theft, regulatory compliance requirements, and the growing adoption of digital platforms. According to BIS market research the global identity verifica
10 views • 4 slides
SafePredict: Reducing Errors
Adaptive strategies in machine learning, such as SafePredict and Forgetful Forests, help reduce errors caused by concept drift in various domains like recommender systems and finance. Tools like neural networks and random forests are designed to adapt to changing data over time, enhancing prediction
1 views • 28 slides
Understanding Prohibited Conduct in Title IX Training
This handout provides information on various forms of prohibited conduct under Title IX training for Security Information Officers. It covers topics such as quid pro quo sexual harassment, unwelcome conduct sexual harassment, sexual assault, dating violence, and domestic violence. Examples and defin
1 views • 13 slides
Introduction to Motion Planning in Autonomous Robotics
Explore the concept of motion planning in autonomous robotics through graphical representations called roadmaps. Understand the importance of representation, transformations, and problem instances in motion planning algorithms. Learn about the accessibility and connectivity characteristics of roadma
0 views • 64 slides
CAN YOU BUY COUNTERFEIT MONEY ONLINE - UNDETECTABLECOUNTERFEITBILLS.COM
The term \"counterfeit money\" describes counterfeit money that is created without official government approval and usually is an intentional attempt to mimic real money. The act of creating counterfeit money has a long history; the first instances can be found in ancient Greece and China. Contact:
1 views • 5 slides
Troubleshooting “QuickBooks Already Has a Company File Open” Error
Troubleshooting \u201cQuickBooks Already Has a Company File Open\u201d Error\nEncountering the \"QuickBooks Already Has a Company File Open\" error? This common issue disrupts your workflow but can be fixed. Start by checking for multiple instances of QuickBooks and restarting your computer. Ensure
1 views • 6 slides
Top Things To Look Out For When Choosing A Recruitment Agency
Recruiting teams and HR leads undergo a myriad of challenges when they are faced with specific and pressing hiring demands. There may be instances when the recruiter does not have the bandwidth, capacity, or facility to fulfil an urgent position. At times like these, availing of the services of an e
8 views • 4 slides
Understanding Labial Fusion: Causes, Symptoms, and Treatment
Labial fusion is a medical condition where the labia minora partially or fully fuse together. It is most common in infants and young children, with suggested causes being low estrogen levels and irritative conditions. While often asymptomatic, some cases may lead to urinary issues. Treatment may inv
0 views • 10 slides
Challenges in Philosophy of Science: Explanation and Induction
The field of philosophy of science grapples with various issues, including the Problem of Explanation and the Problem of Induction. Aristotle's views on scientific explanation and the deductive-nomological model are discussed. The reliance on induction in science, drawing general conclusions from li
0 views • 11 slides
Safeguarding Procedures: Reporting Concerns About Adult Abuse
Understanding the duty to report concerns about adult abuse and neglect, the sources of concern, and the importance of recognizing and reporting potential instances of abuse even when evidence may not be clear. The public has a role in reporting as well, and practitioners must take necessary steps t
0 views • 30 slides
Guidance for Medicaid Applications and Processing
Providing insight into the completion of Medicaid applications, addressing issues with the submission of forms, reminders for required documentation, and instructions on handling instances of a 'No Decision Message' in the application process. Trusted users are urged to follow guidelines and avoid f
0 views • 10 slides
Understanding Lexical Relations: Synonyms, Antonyms, Hyponymy, and Prototype
Explore the concepts of synonyms, antonyms, hyponymy, and prototype in lexical relations. Learn how closely related words can be substituted for each other, understand opposites, inclusion in meanings, and characteristic instances in word categories.
0 views • 12 slides
Nurturing Positive Emotions with Rainbow Moments
Explore the concept of Rainbow Moments as lovely instances of joy and positivity in our daily lives. Learn how to train your mind to notice these moments, even on challenging days, and embrace a new perspective on gratitude and well-being. Engage in daily challenges to recognize and appreciate three
2 views • 7 slides
Evolution of Medicine in Colonial South Asia
The evolution of medicine in colonial South Asia witnessed a transition from local traditional practices to the dominance of imported European medicine. This shift, marked by the establishment of imperial institutions and training of local physicians in Western techniques, led to a complex interplay
1 views • 5 slides
Irony, Paradox, Oxymoron, and Parallelism in Frankenstein
Exploring the concepts of irony, paradox, oxymoron, and parallelism in Mary Shelley's "Frankenstein." The discussion covers different types of irony such as situational, verbal, and dramatic, highlighting instances from the novel. Additionally, the concept of paradox is examined, showcasing statemen
0 views • 16 slides
Lessons Learned from Expert Evidence Failures in Family Law Cases
Discussions on the consequences of expert evidence errors in family law cases are presented through real case examples. The importance of considering all material facts, avoiding basic errors, and ensuring experts' competence is emphasized. These instances highlight the impact of inadequate expert r
0 views • 12 slides
Parity-Only Caching for Robust Straggler Tolerance in Large-Scale Storage Systems
Addressing the challenge of stragglers in large-scale storage systems, this research introduces a Parity-Only Caching scheme for robust straggler tolerance. By combining caching and erasure coding techniques, the aim is to mitigate latency variations caused by stragglers without the need for accurat
0 views • 29 slides
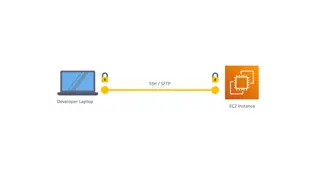
Development Process Using SSH, SFTP, EC2 Instances, and Autoscaling Groups
Exploring the development workflow involving SSH, SFTP, EC2 instances, and Autoscaling Groups for code merging, building, and releasing applications in the cloud environment using technologies like Amazon Elastic Container Service (ECS). The images provide insights into setting up developer laptops,
0 views • 5 slides
Understanding Nearest Neighbor Classification in Data Mining
Classification methods in data mining, like k-nearest neighbor, Naive Bayes, Logistic Regression, and Support Vector Machines, rely on analyzing stored cases to predict the class label of unseen instances. Nearest Neighbor Classifiers use the concept of proximity to categorize data points, making de
0 views • 58 slides
Assertion Collection in DICOM Working Group 07 Radiotherapy
The Assertion Collection IOD addresses the need to collect assertions outside DICOM Instances, providing contextual and identification information. It aims to collect assertions for DICOM Instances during clinical procedures, providing meta information about assertions and allowing for self-containe
0 views • 9 slides
Understanding Information Leakage in Cloud Computing
Explore the threats of multi-tenancy in cloud computing, focusing on determining instance location, co-residency, and potential information exploitation. Research questions investigate these aspects using Amazon EC2 as a case study.
0 views • 28 slides
BabyDayOut Ontology: Describing Picture with Classes, Instances, and Relations
Ontology "BabyDayOut" is developed using RDF/RDFS to describe a picture. It includes classes such as Person, Animal, Baby, Picture, Man, and Gorilla with instances like John, KingKong, Jack, Peter, and Alex. Various relations like hasFriend, hasAnimalFriend, sonOf, depicts, hasEnemy, and hasTitle ar
0 views • 9 slides
Managing Multiple Tomcat Instances Without Containerization
Explore strategies to manage multiple Tomcat instances effectively without transitioning to containerization, discussing deployment methods, script samples, and practical tips for optimizing Tomcat setup in a non-containerized environment.
0 views • 21 slides
Different Types of Linux Installation Methods
This detailed guide covers various methods for installing Linux, including on bare metal/physical hardware, through CD/DVD/USB/network, in a virtual machine, and on cloud services like Amazon EC2. It explains the differences between live image installations and guided installations, as well as provi
0 views • 12 slides
Understanding IRS Form 1099-DIV and Reporting Dividend Payments
Form 1099-DIV is used to report dividend payments, including distributions like capital gains and liquidation distributions. It explains when dividends are included in income, the instances where clarity may be needed, substitute payments in lieu of dividends, and unusual instances such as delayed d
0 views • 24 slides
Introduction to Spark: Lightning-Fast Cluster Computing
Spark is a parallel computing system developed at UC Berkeley that aims to provide lightning-fast cluster computing capabilities. It offers a high-level API in Scala and supports in-memory execution, making it efficient for data analytics tasks. With a focus on scalability and ease of deployment, Sp
0 views • 17 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
Oracle Data Guard: Training Objectives and Far Sync Instances
This content highlights training objectives for Oracle Data Guard, focusing on the new features such as Far Sync Instances and Active Standby Databases. It covers configuring Data Guard Broker, plugging Pluggable Databases, recovering Standby Databases, and achieving a highly available Oracle Databa
0 views • 25 slides