Revisiting LDPC Rate Matching in IEEE 802.11 for Improved Performance
The document discusses revisiting LDPC rate matching in IEEE 802.11, focusing on issues such as performance loss compared to previous standards, power consumption in LDPC decoding/encoding, and over puncturing. It covers preliminary concepts, packet size distribution in various devices like laptops
2 views • 17 slides
Shopify Traffic Filtering Service in Europe
Utilize advanced Shopify traffic filtering service in Europe for tailored European markets, which guarantees safe and focused online traffic management. This strong solution will secure your site from harmful activity and improve its performance. It is made to comply with local data protection laws
0 views • 5 slides
Ensuring Compliance with Prevent Duty in Higher Education
Statutory guidance emphasizes the importance of integrating the Prevent duty into ICT policies in Higher Education. Key points include the need for Acceptable Use Policies (AUPs) to reference the Prevent duty, effective communication of AUPs, and the consideration of web filtering. While filtering i
1 views • 13 slides
Being a Dynamic Social Citizen: Start with Hello Week 2019-2020
Why is being a dynamic citizen important? Learn how connectedness can positively impact behavior and success in school. Explore key definitions like "Connectedness," "Dynamic," "Social Citizen," and "Inclusive," and discover a three-step guide on becoming a dynamic citizen by recognizing when peers
1 views • 17 slides
Understanding Different Types of Recommender Systems
Recommender systems play a crucial role in providing personalized recommendations to users. This article delves into various types of recommender systems including Collaborative Filtering, Content-Based, Knowledge-Based, and Group Recommender Systems. Collaborative Filtering involves making predicti
0 views • 7 slides
Exploring Proteomics Data Analysis Workflows in Perseus
This content provides a detailed walkthrough of utilizing Perseus interface/functions for analyzing label-free and SILAC datasets in the field of proteomics. It covers loading, filtering, visualization, log transformation, rearrangement of columns, and advanced analysis techniques such as scatter pl
2 views • 4 slides
Collaborative Filtering in Data Mining: Techniques and Methods
Collaborative filtering is a key aspect of data mining, focusing on producing recommendations based on user-item interactions. This technique does not require external information about items or users, instead relying on patterns of ratings or usage. Two main approaches are the neighborhood method a
0 views • 23 slides
Ethics in IT-Configured Societies: Google's Controversy and Plagiarism Detection
In Chapter 3 of 'Ethics in IT-Configured Societies', various scenarios are explored such as Google's filtering practices in China and France, the ethical implications of filtering hate speech and political speech, questioning the need to know if a respondent is human or computer in instant messaging
0 views • 31 slides
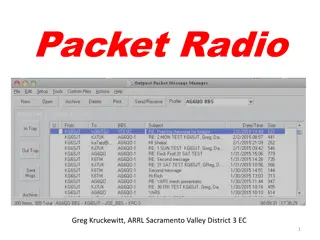
Understanding Packet Radio: A Comprehensive Guide
Packet radio, utilizing VHF FM technology, is a digital mode allowing keyboard-to-keyboard communication, messaging, mailboxes, bulletins, and more. It uses the AX.25 protocol and operates at varying data rates on VHF and HF bands. The system comprises basic stations and automated nodes, each requir
0 views • 20 slides
Personalized Spam Filtering for Gray Mail Analysis
This work delves into the concept of gray mail - messages that some users want while others don't. It explores the challenges posed by gray mail and presents a large-scale personalization algorithm to address these issues. The study leverages data from Hotmail Feedback Loop, focusing on user prefere
3 views • 22 slides
Distance-Based Suspicion Score for Audit Selection
Nuriddin Tojiboyev presented a method for audit selection based on distance measures, risk filtering, and exception sorting. The approach involves selecting representative samples from a population of records, using risk-based filtering to prioritize records for review. Various filters and exception
0 views • 19 slides
Understanding Internet Architecture and Networking Principles
The content explores the architecture and goals of the Internet, focusing on its original objectives, survivability in the face of failure, and evolving requirements. It delves into how networks function, describing behaviors and packet handling. Additionally, it discusses the framework for describi
0 views • 15 slides
Understanding BGP Protocol and Configuration for Routing Policy Filtering
Explore the terminology, reasons, and methods behind routing policy filtering in the context of BGP protocol configuration. Learn how to control traffic routing preferences, filter routes based on AS or prefix, and use regular expressions for complex filtering rules. Discover the importance of AS-Pa
0 views • 29 slides
Understanding the Impact of 1% Packet Loss on TCP and the Cubic Congestion Avoidance Algorithm
Delve into the surprising effects of even 1% packet loss on network flows, the methods TCP uses to mitigate loss, and how the CUBIC congestion avoidance algorithm works. Explore the researched but not quantified problem of packet loss and learn about a test methodology using Ubuntu hosts to measure
0 views • 24 slides
FY25 Title III Consortium Packet Overview
FY25 Title III Consortium Packet provides information on English Language Proficiency allocations, consortium formation, grant management, board approval requirements, and responsibilities of the lead fiscal agent. English Learner counts determine funding eligibility, with consortiums formed to reac
0 views • 15 slides
Understanding Enterprise Network Security and Firewalls
Exploring key aspects of enterprise network security, this presentation delves into topics such as perimeter control, host-based security, intrusion detection, and various types of firewalls. It highlights filtering rulesets, requirements for outbound traffic, and the importance of dynamic packet fi
0 views • 19 slides
High-Resolution 3D Seafloor Topography Enhancement Using Kalman Filtering
Proposing a Kalman Filter approach to refine seafloor topography estimation by integrating various geophysical data types. The method allows for producing regional bathymetry with higher resolution, truncating unnecessary observations, and reducing the matrix dimensions in the inverse problem. Inclu
0 views • 9 slides
Understanding Shuttling and Filtering of Multiple Ion Species in Segmented Linear Trap
This content delves into the intricate processes of shuttling and filtering multiple ion species within a segmented linear trap. It explores techniques such as RF filtering, DC potentials, mass filtering, and trap depths in the context of ion manipulation. Discussions also touch on ion crystal phase
0 views • 13 slides
Multi-phase System Call Filtering for Container Security Enhancement
This tutorial discusses the importance of multi-phase system call filtering for reducing the attack surface of containers. It covers the benefits of containerization, OS virtualization, and the differences between OS and hardware virtualization. The tutorial emphasizes the need to reduce the kernel
0 views • 32 slides
Collaborative Bayesian Filtering in Online Recommendation Systems
COBAFI: COLLABORATIVE BAYESIAN FILTERING is a model developed by Alex Beutel and collaborators to predict user preferences in online recommendation systems. The model aims to fit user ratings data, understand user behavior, and detect spam. It utilizes Bayesian probabilistic matrix factorization and
0 views • 49 slides
Fast High-Dimensional Filtering and Inference in Fully-Connected CRF
This work discusses fast high-dimensional filtering techniques in Fully-Connected Conditional Random Fields (CRF) through methods like Gaussian filtering, bilateral filtering, and the use of permutohedral lattice. It explores efficient inference in CRFs with Gaussian edge potentials and accelerated
0 views • 25 slides
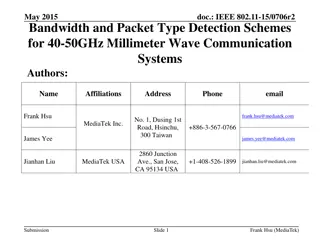
Bandwidth and Packet Type Detection Schemes for 40-50GHz Millimeter Wave Communication Systems
The document discusses bandwidth and packet type detection schemes for 40-50GHz millimeter wave communication systems in IEEE 802.11aj specifications. It proposes a preamble design for auto-detection of bandwidth and packet type to improve channel estimation and decoding efficiency. By utilizing dif
0 views • 27 slides
Evolution of User Authentication Practices: Moving Beyond IP Filtering
The article explores the obsolescence of IP filtering in user authentication, highlighting the challenges posed by evolving technology and the limitations of IP-based authentication methods. It discusses the shift towards improving user experience and addressing security concerns by focusing on user
0 views • 22 slides
Understanding Mixtures and Separation Methods
A mixture is a combination of ingredients that can be separated by various methods like sieving, filtering, and evaporation. Magnets are also used to separate magnetic objects. Sieving separates solid particles by size, while filtering separates tiny particles from liquids. Evaporation is used for s
0 views • 14 slides
Enhancing Network Security Through Multi-Core Packet Scattering and Deep Packet Inspection
Explore the use of multi-core systems to tackle performance bottlenecks in network intrusion detection systems, specifically focusing on deep packet inspection. Techniques such as load balancing and pattern subset scanning are discussed to optimize DPI processes and improve overall network security
0 views • 43 slides
Exploring the Evolution of Data Communications: A Brief Overview
Delve into the progression of data communications from Morse code to modern radio email systems like Winlink. Discover the history of protocols, technologies, and the impact of the internet on amateur packet radio. Unravel the development of ARQ data protocols, X.25 packet switching, and the transit
0 views • 51 slides
Insights from Mars and Earth for Predictability with Ensemble Kalman Filtering
A collaborative effort between Penn State University and various teams explores the predictability of Martian and Earth weather phenomena using ensemble Kalman filtering. A comparison of key characteristics between Earth and Mars is provided, shedding light on their variable atmospheres and climates
0 views • 31 slides
Real-Time Digital Signal Processing Lab: Matched Filtering and Digital Pulse Amplitude Modulation
Explore the concepts of transmitting one bit at a time, matched filtering, PAM systems, intersymbol interference, communication performance, and prevention of intersymbol interference in a two-level digital PAM system. The presentation covers topics like bit error probability, symbol error probabili
0 views • 32 slides
Understanding the Basics of Packet Radio for Amateur Communication
Explore the world of packet radio, a digital mode used by amateur radio operators to build wireless computer networks. Learn about its benefits, how it works using the AX.25 protocol, making connections, advantages such as error checking, and building a packet station with the necessary components.
0 views • 19 slides
Understanding Asynchronous Transfer Mode (ATM) in Data and Computer Communications
Asynchronous Transfer Mode (ATM) is a packet transfer technology that supports multiple logical connections over a single physical interface. It uses fixed-sized packets called cells for data transfer. ATM bears similarities to packet switching and offers streamlined packet transfer with minimal err
0 views • 46 slides
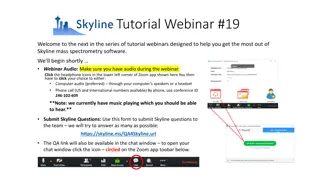
Tutorial Webinar #19: Ion Mobility Spectrum Filtering in Skyline
Welcome to Tutorial Webinar #19 focusing on Ion Mobility Spectrum Filtering in Skyline software. Join experts Brendan MacLean, Erin Baker, and Nat Brace to enhance your understanding and usage of Skyline for mass spectrometry. Learn about agenda, upcoming events, and how to submit questions. Don't m
0 views • 8 slides
Understanding Finite Impulse Response Filtering in Digital Signal Processing
Explore the concepts of Finite Impulse Response (FIR) filtering in digital signal processing, including filter specifications for low-pass, high-pass, band-pass, and band-stop filters. Learn about frequency normalization, specifications for different filter types, and the transfer function of FIR fi
0 views • 26 slides
Decontamination and Reuse of N95 Filtering Facepiece Respirators
This presentation discusses the decontamination and reuse of N95 filtering facepiece respirators, addressing the need for solutions in sanitizing technologies like ultraviolet light and chlorine dioxide. Various methods under consideration, such as heat and hydrogen peroxide, are explored alongside
0 views • 16 slides
Enhancing Data Center Network Performance through Packet Scheduling and ECN
Explore the advancements in data center network performance improvement through techniques like packet scheduling, Explicit Congestion Notification (ECN), and strict priority for different types of flows. The research discusses the requirements of low latency for short messages and high throughput f
0 views • 48 slides
Understanding Wireshark Filters for Efficient Packet Analysis
Learn how to leverage Wireshark capture filters to customize packet analysis, enhance traffic visibility, and optimize network monitoring. Capture only the data you need, create custom filters, and streamline intrusion detection analysis with Berkeley Packet Filters (BPF). Discover the power of disp
0 views • 17 slides
Considerations on PHY Padding and Packet Extension in 11ax
The document discusses the proposed PHY padding and packet extension for IEEE 802.11ax, focusing on considerations for processing data within SIFS duration and relaxation of LDPC decoding processing time. It outlines the overview of the proposed padding scheme, considerations for LDPC implementation
0 views • 15 slides
Overview of the Urinary System: Functions, Structure, and Importance
The urinary system plays a crucial role in maintaining water and salt balance, regulating pH levels, and excreting waste products like urea and uric acid. Comprising of organs such as the kidneys, ureters, urinary bladder, and urethra, this system ensures the removal of metabolic waste from the body
0 views • 34 slides
Innovative Application Packet for ACE Solutions - Explore the Visual Journey
Dive into the visually captivating world of ACE Solutions with their cutting-edge application packet. From stunning visuals to advanced functionality, this packet showcases the power and versatility of ACE Solutions for modern applications. Discover the seamless navigation, engaging content, and ric
0 views • 59 slides
Understanding Dynamic Loading and Linking in Memory Management
This presentation covers the concepts of dynamic loading and linking in memory management, discussing how programs and data are managed in physical memory, the advantages of dynamic loading, and the process of dynamic linking for system language libraries. The use of stubs for locating memory-reside
0 views • 12 slides
Exploring the Power of Filtering in Signal Processing
Delve into the world of signal processing and filtering as a means of separating desired information from noise. Explore the role of digital filters in processing images and signals. Discover how filtering can achieve noise cancellation in headphones, clean up noisy images, and understand the import
0 views • 29 slides