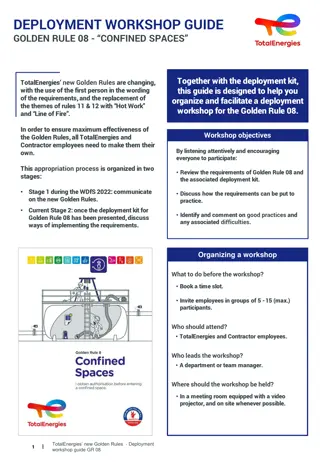
Golden Rule 08 Deployment Workshop Guide: Organizing and Implementing TotalEnergies' New Safety Rules
This guide aims to assist in organizing and facilitating a workshop for TotalEnergies' Golden Rule 08 deployment. It emphasizes the importance of employee participation, practical application of safety requirements, and sharing of experiences to ensure effective adoption of the new rules. The worksh
1 views • 4 slides
Meticulous Research Forecasts Global Electronic Design Automation Market to Reach $17.47 Billion by 2030
Electronic Design Automation Market by Offering (Solutions, Services), Deployment Mode (Cloud-based deployment, On-premise deployment), Tool Type (Design tools, Verification Tools, Simulation Tools), and Geography - Global Forecast to 2030\n
0 views • 2 slides
Understanding UML Deployment Diagrams
UML Deployment Diagrams show the execution architecture of software systems, illustrating how software deployment targets are assigned artifacts to nodes. Nodes represent hardware devices or software environments connected through communication paths, while artifacts are concrete elements deployed o
1 views • 22 slides
Understanding Deployment and Separation Data in Military Healthcare
This information delves into the deployment and separation data related to military service members, focusing on how data changes during deployments and the importance of considering deployment in rate calculations. It also covers the objectives, ownership, and restrictions on the use of this data b
2 views • 18 slides
Power BI Deployment Pipelines - April 2021
Discover the latest in Power BI release management with Deployment Pipelines in April 2021. Learn about the agenda, speaker insights, scenario, steps to follow, issues faced, and the solution provided by Deployment Pipelines for managing organizational content deployment efficiently across multiple
0 views • 15 slides
Military Financial Readiness Guide - Pre-Deployment Essentials
Explore key aspects of financial planning, insurance, special pays, taxes, and more to prepare for deployment. Learn about setting financial goals, creating a spending plan, understanding entitlements, and managing insurance needs. Stay informed on combat zone tax exclusions and legal document requi
0 views • 27 slides
Surge Deployment Guidelines and Standard Operating Procedures
Surge Deployment Guidelines and Standard Operating Procedures outline the principles and processes for deploying specialized personnel to support humanitarian operations in various emergencies. The guidelines aim to ensure equal opportunity, transparent processes, and quality responses among Red Cro
0 views • 12 slides
Streamlining Image Deployment with Windows Deployment Service and MDT
Utilizing Windows Deployment Service and Microsoft Deployment Toolkit (MDT) can enhance the efficiency of large-scale Windows operating system deployments. The transition from sector-based cloning to file-based imaging brings benefits like reduced storage requirements, increased automation, and flex
0 views • 20 slides
Journey to Software Deployment Automation with SCCM at Brockport
Explore Brockport's journey in leveraging SCCM for software deployment, image automation, asset management, and imaging processes. Dive into their environment overview, asset management strategies, pre-SCCM imaging details, and current imaging techniques using UDI. Witness the UDI wizard in action f
0 views • 19 slides
Training Scenario for Sustainment Brigade Deployment Preparation
Adapted training scenario for deploying a sustainment brigade featuring specific unit capabilities and planning tasks for Phase 0 deployment at Fort Hood, TX. Includes analyzing mission specifics, integrating religious support, and executing deployment tasks. Detailed overview of the Atropian scenar
9 views • 7 slides
Medical Recommendations and Preparations for Deployers at Department of the Army, Fort Bliss
General medical recommendations and preparations for DoD/DACivilian and Military deployers at Department of the Army, Fort Bliss, Texas in July 2018. Guidelines include pre-deployment health assessments, fitness standards, vaccination requirements, and documentation needed for deployment. Ensure med
0 views • 25 slides
SBCT Scenario Training for Unit Deployment
SBCT prepares for deployment in Atropia to support the Government of Atropia against Ariana forces. The scenario involves planning, preparation, execution, and assessment tasks for UMT deployment, integrating religious support into the unit plan, and analyzing specific mission requirements. Specific
0 views • 7 slides
Partnership to Advance Clean Energy Deployment (PACE-D) Technical Assistance Program Grid Connectivity & Inspection Procedure
The Partnership to Advance Clean Energy Deployment (PACE-D) Technical Assistance Program, presented by USAID, focuses on grid connectivity and inspection procedures for clean energy deployment. Sessions cover applicable standards, regulations, interconnection tests, net metering systems, and more. R
3 views • 22 slides
WFH-B2O Strategy Deployment Progression
This report outlines the planning and execution of a Work From Home (WFH) to Back to Office (B2O) strategy, focusing on system deployment, asset tracking, and connectivity solutions. It details the successful opportunities, progression distribution, and achievements within a four-week period, emphas
0 views • 15 slides
Challenges Faced in DNSSEC Deployment by Geoff Huston at APNIC June 2016
Geoff Huston addresses the challenges of DNSSEC deployment, discussing turning on validation in Bind configurations, reasons why it may be perceived as difficult, and the importance of DNSSEC in enhancing security within the DNS. Despite concerns about increased resolution time and limited signed na
0 views • 14 slides
Learning Management Systems Market: Government Initiatives and Policies Promotin
Learning Management Systems Market by Offering (Solution, Services), Deployment Mode (Cloud-based Deployment, On-premise Deployment), End User (Education, Corporate) and Geography - Global Forecast to 2030\n
0 views • 4 slides
Understanding CI/CD and Deployment Strategies in Software Development
Continuous Integration (CI) involves frequent code integration, automated testing, and error detection. Continuous Delivery (CD) extends CI by packaging artifacts for end users, while Continuous Deployment automatically deploys software. Explore deployment strategies like Blue/Green, Canary, and A/B
1 views • 16 slides
Exploring DANE, DNSSEC, and TLS in Go6Lab
Delve into the implementation of DANE, DNSSEC, and TLS protocols at Go6Lab, a testing facility affiliated with ISOC/Go6 Institute in Slovenia. The setup includes DNSSEC implementation with PowerDNS and OpenDNSSEC, DANE experimentation with Postfix servers, and verification processes for TLS certific
0 views • 36 slides
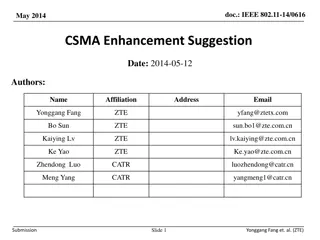
Enhancing CSMA/CA Efficiency in High-Density WLAN Deployment
CSMA/CA mechanism in IEEE 802.11 is efficient for low-density WLAN deployment but lacks effectiveness in high-density scenarios. This submission suggests improving spectrum efficiency by shifting contention in the code domain. The aim is to address the performance and user experience in dense deploy
1 views • 14 slides
Comprehensive Rescue Swimmer Training and Safety Guide
Learn about the essential aspects of rescue swimmer deployment, task organization, communication, and safety in various scenarios. Explore the five phases of rescue swimmer deployment, including preparation, rapid assessment, approach, and deployment strategies. Discover key elements like conducting
0 views • 13 slides
Health and Safety Pre-Deployment Preparation Guidelines
Detailed guidelines for pre-deployment health and safety preparation, including personal health checks, packing lists, training requirements, and hazard communication. Covering aspects such as vaccinations, medications, emergency procedures, and additional training like PPE use and HAZWOPER. Ensurin
0 views • 15 slides
Understanding the Impact of Military Deployment Cycles on Service Members and Families
Explore the effects of military deployment cycles on service members and their families, discussing stressors, stages of deployment, and readjustment behaviors. Gain insight into the demographic and risk characteristics of military families, as well as the challenges faced by both active duty and Gu
0 views • 39 slides
Enhancing WHOIS Updates with DNSSEC, ASPLAIN, and Abuse Contact Implementation
Explore the latest updates in WHOIS, including DNSSEC deployment, ASPLAIN support, and abuse contact policies. Learn about DNSSEC deployment plans, ASPLAIN formats, and recommendations for abuse handling. Stay informed on domain security and network contact protocols.
0 views • 22 slides
Network Deployment and Monitoring Overview
Explore key updates on network deployment for Pico2 testbed EOSC, including L3VPN deployment status, site connections, VPN management governance, and the importance of monitoring for cloud deployment. Gain insights into collaboration efforts between GEANT and RENATER, addressing challenges and advan
0 views • 7 slides
Rapid Deployment Standing Team (RDST) for Humanitarian Crisis Response
A comprehensive overview of the Rapid Deployment Standing Team (RDST) initiative launched in October 2019 for swift and effective crisis response. The RDST comprises specialized coordinators and managers to address various aspects of crisis management, including staffing gaps and support services. W
0 views • 5 slides
Evolution of DNSSEC Implementation at Nominet
This content details the evolution of DNSSEC implementation at Nominet, covering key milestones from initial infrastructure deployment in 2008 to the adoption of a new approach in 2016. It discusses the challenges faced, technology used over the years, and the transition to a new DNSSEC approach in
0 views • 8 slides
Automating Deployment Using TeamCity and Octopus Deploy
Explore the benefits of automated deployment with TeamCity and Octopus Deploy, including faster and more frequent deployments, reduced risk, enhanced confidence, and efficient build and packaging processes. Discover how automation can streamline application deployment, eliminate manual errors, and i
0 views • 17 slides
OSCAR Project Proposal for OPNFV
The OSCAR Project is a proposed initiative for OPNFV by Stuart Mackie, focusing on system configuration and reporting deployment for OPNFV platform and virtual infrastructure. The project aims to create templates for building different OPNFV stacks, preload required VNFs, and enable rapid deployment
0 views • 14 slides
Optimizing Firm Fuel Supply Service Deployment in ERCOT
ERCOT is considering a revised approach to providing Firm Fuel Supply Service (FFSS) from individual Generation Resources through an RFP process. The proposal involves setting a minimum Load Serving Limit (LSL) to ensure the deployment of a specific amount of service and allocating FFSS based on sys
0 views • 9 slides
RPKI Deployment and Security Overview
Explore the key concepts of RPKI deployment and security, including preventing prefix/subprefix hijacks, certifying ownership with RPKI, and how RPKI can prevent prefix hijacks. Learn about challenges in deployment and the importance of route origin validation. Understand the risks of insecure deplo
0 views • 24 slides
Modern Strategies for Application Deployment: A Comprehensive Overview
Explore the evolution of deployment processes from historical challenges to modern complexities in a tech-packed session by Geoff Callaghan. Learn about standard Visual Studio deployment, single file applications, ClickOnce, and MSIX technologies, along with the shift towards self-contained and fram
0 views • 22 slides
IT Infrastructure Updates and Deployments Overview
Deployment and upgrade progress of IT infrastructure at LBNL includes wireless network expansion, router replacements with 100G upgrade, 100G tapping evaluation for IDS, DTN deployment for data transfer automation, and video conferencing cart deployment. The updates range from network switches to ro
0 views • 7 slides
SaudiNIC's Experience in Deploying DNSSEC
SaudiNIC embarked on a comprehensive journey to deploy DNSSEC, starting with observing its growth and conducting in-depth studies on pioneer implementations worldwide. The project involved creating a startup team, drafting procedures, conducting workshops, and enabling DNSSEC on various platforms. K
0 views • 16 slides
Understanding DNSSEC: Adding Digital Signatures to DNS Responses
DNSSEC (Domain Name System Security Extensions) allows for the addition of digital signatures to DNS responses, ensuring the authenticity, completeness, and currentness of the data received by a client. By validating the digital signature, clients can trust the response received is genuine and unalt
0 views • 27 slides
ChannelFinder Setup and Deployment Diagrams with RecSync Components
Includes setup and deployment diagrams for ChannelFinder on vclx4, along with details about RecSync components for EPICS module communication. Also covers RecCaster configuration and registration of support components. The documentation further discusses RecReceiver setup, Python integration with Tw
0 views • 8 slides
Evaluation of Ed25519 Cryptography Performance in DNSSEC Validation
Edwards Curve Cryptography, specifically the Ed25519 algorithm, offers faster performance and high crypto density compared to other algorithms. This evaluation study compares key sizes, processing times, and validation support for Ed25519, ECDSA P-256, RSA-2048, and RSA-4096 in DNSSEC validation sce
0 views • 19 slides
Optimizing SCCM Deployment Process With Task Sequences and Image Management
Explore the efficient utilization of SCCM task sequences, image packages, and deployment methods to streamline the deployment process. Learn about custom task sequences, software imaging strategies, and driver import considerations for successful deployments in an enterprise environment.
0 views • 21 slides
Web Development and Deployment Best Practices
Explore the essential steps in web development and deployment including creating development sites, deployment strategies, site maintenance, and revision control. Learn about deploying sites to Dreamhost, handling site maintenance issues, and the importance of revision control systems in collaborati
0 views • 13 slides
Evolution of ARIN: RPKI and DNSSEC Implementation
Explore the transformation at ARIN as it embraces RPKI and DNSSEC technologies. Discover the significance of DNSSEC and RPKI, the changes needed for DNSSEC deployment, and the functionalities of RPKI in securing network resources. Dive into the critical role these technologies play in enhancing rout
0 views • 46 slides
Technology Deployment for Sustainable Development - Innovation and Implementation Strategies
Exploring the crucial aspects of technology deployment for sustainable development, this content delves into innovative solutions, scouting, and deployment processes necessary to address critical issues in the Asia Pacific region. From promoting inclusive access to resources to driving domestic inno
0 views • 17 slides