Understanding Parallel and Distributed Computing Systems
In parallel computing, processing elements collaborate to solve problems, while distributed systems appear as a single coherent system to users, made up of independent computers. Contemporary computing systems like mobile devices, IoT devices, and high-end gaming computers incorporate parallel and d
1 views • 11 slides
Enhanced Security in Multiparty Computation
Explore the improved black-box constructions of composable secure computation, focusing on definitions, objectives, and the formalization basics of multiparty computation (MPC). Learn about the motivating security aspects in MPC and the real/ideal paradigm. Discover how MPC security involves compari
1 views • 68 slides
Understanding Parallel and Distributed Systems in Computing
A parallel computer is a collection of processing elements that collaborate to solve problems, while a distributed system comprises independent computers appearing as a single system. Contemporary computing systems, like mobile devices and cloud platforms, utilize parallel and distributed architectu
0 views • 11 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Secure Multiparty Computation for Department of Education Data Sharing
This report discusses the use of Secure Multiparty Computation (SMC) to enable sharing of sensitive Department of Education data across organizational boundaries. The application of SMC allows for joint computation while keeping individual data encrypted, ensuring privacy and security within the Nat
0 views • 15 slides
Advancements in Active Secure Multiparty Computation (MPC)
Delve into the realm of secure multiparty computation under 1-bit leakage, exploring the intersection of DP algorithms, MPC, and the utilization of leakage for enhanced performance. Discover the overhead implications of achieving active security, as well as the evolution of secure computation protoc
0 views • 43 slides
Parallel Chi-square Test for Feature Selection in Categorical Data
The chi-square test is a popular method for feature selection in categorical data with classification labels. By calculating chi-square values in parallel for all features simultaneously, this approach provides a more efficient solution compared to serial computation. The process involves creating c
1 views • 4 slides
Understanding Shift Registers: Introduction and Classification
Explore the world of shift registers, including buffer registers, and different modes of operation like serial in/serial out, serial in/parallel out, parallel in/serial out, and parallel in/parallel out. Learn about the construction, operation, and classification of registers in digital systems.
1 views • 24 slides
Understanding Shift Registers in Sequential Logic Circuits
Shift registers are sequential logic circuits used for storing digital data. They consist of interconnected flip-flops that shift data in a controlled manner. This article explores different types of shift registers such as Serial In - Serial Out, Serial In - Parallel Out, Parallel In - Serial Out,
2 views • 9 slides
Understanding Parallel Circuits in Electronics
Explore topics such as resistors in parallel, voltage distribution, Kirchhoff's current law, resistance calculations, and practical applications in parallel circuits. Dive into problem-solving exercises and grasp concepts like current dividers, total resistance calculations, and power distribution i
0 views • 20 slides
COMET: Code Offload by Migrating Execution - OSDI'12 Summary
The research paper discusses COMET, a system for transparently offloading computation from mobile devices to network resources to improve performance. It outlines the goals of COMET, its design, and evaluation, focusing on distributed shared memory and bridging computation disparity through offloadi
0 views • 31 slides
Understanding Parallel Sorting Algorithms and Amdahl's Law
Exploring the concepts of parallel sorting algorithms, analyzing parallel programs, divide and conquer algorithms, parallel speed-up, estimating running time on multiple processors, and understanding Amdahl's Law in parallel computing. The content covers key measures of run-time, divide and conquer
1 views • 40 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Enhancing Multi-Party Computation Efficiency Through ORAM Techniques
Explore the realm of efficient random access in multi-party computation through the reevaluation of classic schemes and the introduction of new approaches. Discover the potential of ORAM in improving performance and reducing costs in various computational tasks, such as secure multi-party computatio
0 views • 22 slides
Exploring Secure Computation in the Age of Information
Welcome to Secure Computation Lecture 1 by Arpita Patra. The course covers evaluation policies, projects, and references in the realm of secure computation. The content delves into the significance of information security across various sectors, emphasizing the importance of safeguarding sensitive d
0 views • 36 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Linear Communication in Secure Multiparty Computation for Efficient and Fast Processing
The research focuses on achieving perfectly secure multiparty computation (MPC) with linear communication and constant expected time. It explores efficient approaches using a broadcast-hybrid model and P2P communication, aiming to balance speed and efficiency in MPC. The study highlights the importa
0 views • 23 slides
Data-Parallel Finite-State Machines: A Breakthrough Approach
This research discusses a new method for breaking data dependencies in data-parallel finite-state machines. It highlights the importance of FSMs in various algorithms and the need for parallel versions in processing large data sets. The study explores breaking data dependences with enumeration and t
0 views • 19 slides
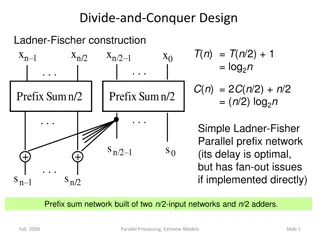
Parallel Prefix Networks in Divide-and-Conquer Algorithms
Explore the construction and comparisons of various parallel prefix networks in divide-and-conquer algorithms, such as Ladner-Fischer, Brent-Kung, and Kogge-Stone. These networks optimize computation efficiency through parallel processing, showcasing different levels of latency, cell complexity, and
1 views • 21 slides
Understanding Parallel Skyline Queries in Distributed Systems
Explore the concept of skyline queries in parallel computing, focusing on non-dominated points in a d-dimensional set. Learn about efficient algorithms, massively parallel models, communication strategies, and the application of broadcast steps. Enhance your knowledge of skyline computation processe
0 views • 27 slides
Secure Computation Challenges and Solutions in Data Mining
Exploring the intersection of secure computation and data mining, this content uncovers key challenges such as improving algorithms, converting programs for secure computation, and addressing parallelizability issues. It highlights the importance of cryptography in ensuring data privacy and presents
0 views • 30 slides
Covert Computation: Ensuring Undetectable Engagement
Covert computation aims to conceal the fact that computation is occurring and hide engagement in certain tasks like secure computation, authenticated key exchange, and more. By making messages indistinguishable and utilizing steganographic channels, it becomes possible to keep the activities covert
0 views • 16 slides
Overview of Turing Machines: Introduction, Tape, and Computation
Turing Machines are fundamental in the theory of computation, capable of recognizing all computable languages. They consist of a Finite State Machine combined with an infinite tape. The tape is initialized with input on the left end, and a TM's computation can either halt by entering special accept
0 views • 29 slides
Computation for Real Estate Sector in Bangalore Branch of ICAI
Practical overview of GST computation for real estate transactions in Bangalore, with details on old rates with ITC and new rate regime effective from April 1, 2019. The content discusses different transactions, conditions for new rates without ITC, and provides insights on the 80:20 computation met
0 views • 39 slides
Parallel Programming Directives and Concepts
Learn about parallel programming directives like Diretiva.parallel and #pragma omp.parallel, which allow code to be executed by multiple threads simultaneously. Explore concepts such as defining parallel regions, setting the number of threads, and utilizing OpenMP directives for parallel for loops.
0 views • 39 slides
Fides: A System for Verifiable Computation Using Smart Contracts
Fides presents a system for verifiable computation using smart contracts, focusing on blockchain basics, Ethereum, smart contracts, and outsourcing computation. It explores key components of blockchain, Ethereum's decentralized computing platform, properties of smart contracts, and the concept of ve
0 views • 25 slides
Understanding Parallel Software in Advanced Computer Architecture II
Exploring the challenges of parallel software, the lecture delves into identifying and expressing parallelism, utilizing parallel hardware effectively, and debugging parallel algorithms. It discusses functional parallelism, automatic extraction of parallelism, and finding parallelism in various appl
0 views • 86 slides
Insights into Secure Computation with Minimal Interaction
This paper revisits the concept of secure computation with minimal interaction, focusing on the challenges and possibilities of achieving secure multiparty computation in 2 rounds. Specifically exploring scenarios with 3 and 4 parties, the study delves into the reasons for choosing n=3, n=4, and t=1
0 views • 23 slides
Mastering Parallel Structure in Business Communication
Understanding and implementing parallel structure in business communication is essential for clear, effective, and professional writing. Explore the nuances of parallelism, such as using correlative conjunctions like "not only...but also," to ensure consistency and coherence in your written work. Le
0 views • 21 slides
Overview of Income Computation and Disclosure Standards (ICDS)
The Income-tax Act, 1961 introduced Income Computation and Disclosure Standards (ICDS) to be followed by certain assesses for computation of income. ICDS applies to taxpayers using the mercantile system of accounting from the Assessment Year 2016-17 onwards. Non-compliance with ICDS can lead to Best
0 views • 49 slides
Blackbox Verifiable Computation Scheme Overview
This summarized content discusses the concept of blackbox verifiable computation, focusing on the challenges faced by clients and servers, the role of helper oracles, positive results utilizing homomorphic encryption, and background information on Random Self Reducible (RSR) functions. The protocol
0 views • 20 slides
Overview of Nested Data Parallelism in Haskell
The paper by Simon Peyton Jones, Manuel Chakravarty, Gabriele Keller, and Roman Leshchinskiy explores nested data parallelism in Haskell, focusing on harnessing multicore processors. It discusses the challenges of parallel programming, comparing sequential and parallel computational fabrics. The evo
0 views • 55 slides
Parallel Computation for Matrix Multiplication
Matrix multiplication is a fundamental operation with diverse applications across scientific research. Parallel computation for matrix multiplication involves distributing the computational workload over multiple processors, improving efficiency. Different algorithms have been developed for multiply
0 views • 36 slides
Communication Steps for Parallel Query Processing: Insights from MPC Model
Revealing the intricacies of parallel query processing on big data, this content explores various computation models such as MapReduce, MUD, and MRC. It delves into the MPC model in detail, showcasing the tradeoffs between space exponent and computation rounds. The study uncovers lower bounds on spa
0 views • 25 slides
Distributed Machine Learning and Graph Processing Overview
Big Data encompasses vast amounts of data from sources like Flickr, Facebook, and YouTube, requiring efficient processing systems. This lecture explores the shift towards using high-level parallel abstractions, such as MapReduce and Hadoop, to design and implement Big Learning systems. Data-parallel
0 views • 61 slides
Parallel Approaches for Multiobjective Optimization in CMPE538
This lecture provides a comprehensive overview of parallel approaches for multiobjective optimization in CMPE538. It discusses the design and implementation aspects of algorithms on various parallel and distributed architectures. Multiobjective optimization problems, often NP-hard and time-consuming
0 views • 20 slides
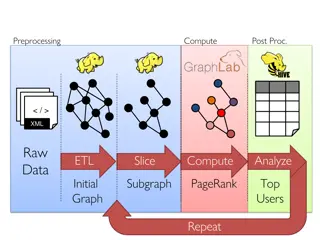
Data Processing and Analysis for Graph-Based Algorithms
This content delves into the preprocessing, computing, post-processing, and analysis of raw XML data for graph-based algorithms. It covers topics such as data ETL, graph analytics, PageRank computation, and identifying top users. Various tools and frameworks like GraphX, Spark, Giraph, and GraphLab
0 views • 8 slides
Understanding OpenMP Barriers and Locks in Parallel Programming
Exploring the concepts of OpenMP barriers and locks in parallel programming, this discussion covers the importance of synchronization through barriers, the use of lock variables for finer control over synchronization, and examples like the Dining Philosophers problem. Learn how these primitives faci
0 views • 22 slides
Understanding Parallel Processing Fundamentals
This overview delves into the basics of parallel computing, covering parallel memory architectures, programming models, design issues, and parallelizing serial programs. Parallel computing involves leveraging multiple compute resources simultaneously to enhance computational efficiency and solve pro
0 views • 35 slides
Introduction to Charm++ Programming Framework
Charm++ is a generalized approach to parallel programming that offers an alternative to traditional parallel programming languages like MPI, UPC, and GA. It emphasizes overdecomposition, migratability, and asynchrony to enhance parallel program performance and efficiency. The framework uses indexed
0 views • 43 slides