CYBERSECURITY AWARENESS MONTH 2023
Join us for Cybersecurity Awareness Month 2023 to learn how to stay safe online. Discover the importance of cybersecurity, find easy ways to protect yourself, and get involved in raising awareness.
6 views • 23 slides
Cybersecurity and Supply Chain Risk Management: Best Practices for Procurement
The best practices for managing cybersecurity and supply chain risks in procurement. This book covers topics such as supply chain attacks, evaluating cybersecurity risks, vendor risk assessment, and implementing effective procurement strategies.
7 views • 23 slides
REWIRE Cybersecurity Skills Alliance
REWIRE Cybersecurity Skills Blueprint and the Skills Intelligence behind it, as well as the key aspects of cybersecurity skills and the proposed categories for future development.
2 views • 21 slides
Instrument human capital cybersecurity mkb bedrijven
This concise instrument helps small and medium-sized businesses in the Netherlands enhance their cybersecurity by leveraging human capital. It provides practical tips and guidance on organizing cybersecurity within the company, focusing on employees (internally) and professionals/suppliers/advisors
1 views • 59 slides
Cybersecurity Industry Call for Innovation (CyberCall)
Submit your innovative project proposal for the CSA Cybersecurity Industry Call for Innovation. Enhance cybersecurity in a rapidly evolving industry.
0 views • 19 slides
Safeguarding Tampa's Business Landscape_ The Crucial Role of Managed Cybersecurity Services
Explore the significance of managed cybersecurity services for Tampa's businesses through our detailed PDF guide. It highlights how investing in sophisticated cybersecurity measures can be a game-changer, offering peace of mind by protecting against data loss, financial fraud, and reputation damage.
1 views • 6 slides
Empowering NNSA Cyber Professionals Through Enterprise Tools and Data Analytics
NNSA's Office of the Chief Information Officer is enhancing their cybersecurity capabilities by leveraging Enterprise Cybersecurity Data Integration architecture and strategic partnerships. This initiative focuses on expanding data sources, enabling correlation, and using resilient engineering for e
0 views • 10 slides
Adversarial Machine Learning in Cybersecurity: Challenges and Defenses
Adversarial Machine Learning (AML) plays a crucial role in cybersecurity as security analysts combat continually evolving attack strategies by malicious adversaries. ML models are increasingly utilized to address the complexity of cyber threats, yet they are susceptible to adversarial attacks. Inves
2 views • 46 slides
Understanding Women's Smoking Behavior: A Pilot Test of Readiness and Motivation Instrument
Conducted with 495 women smokers in public health clinics, the pilot test assessed readiness and motivation to change smoking behavior. Findings highlighted varying stages of readiness and motivation, with a focus on pregnancy enhancing the readiness to quit. The instrument designed accommodates low
2 views • 28 slides
Challenges in Cybersecurity Implementation: A Philippine Perspective
A presentation discussing the challenges in cybersecurity implementation specifically in the context of the Philippines. It covers the PPT framework (People, Process, Technology), classes of security measures based on the Philippines Data Privacy Act, roles and responsibilities, best practices for I
1 views • 18 slides
C2M2 Version 2.1 Cybersecurity Model Overview
The Cybersecurity Capability Maturity Model (C2M2) Version 2.1 provides a comprehensive framework for evaluating and improving cybersecurity capabilities within an organization. It outlines best practices and maturity levels across various domains to enhance cyber resilience and risk management, ser
4 views • 10 slides
Ohio Career Readiness Leaders Network Meetup - October 10, 2023
Join the Ohio Career Readiness Leaders Network Meetup on October 10, 2023, to explore topics such as Career Exploration Continuum, Micro Credentials in Middle School, Student Success Plans, and more. Connect with professionals in the field, share best practices, and stay informed about upcoming even
1 views • 28 slides
Cybersecurity Risk Management in K-12 Education: Challenges and Strategies
Facing a surge in cyberattacks, K-12 schools struggle with limited funds, expertise, and staff for cybersecurity. This leads to vulnerabilities that make them prime targets for hackers. Lack of dedicated cybersecurity resources and training exacerbates the risks, highlighting the urgent need for com
1 views • 47 slides
Which and How of Cybersecurity Frameworks
Navigate the complex landscape of cybersecurity frameworks with expert guidance on identifying the perfect fit for your organization. Explore various frameworks such as IRAP, SOC2, ISO 27001, and learn the advantages of selecting the right one. Understand the importance of compliance, certification,
3 views • 41 slides
Why Partnering with a CISO Recruiter is Essential for Cybersecurity Success
\"Why Partnering with a CISO Recruiter is Essential for Cybersecurity Success\" explores the crucial role of specialized recruiters in finding top-tier cybersecurity leaders. Discover how a CISO recruiter enhances your organization\u2019s security posture by leveraging expertise, extensive networks,
0 views • 9 slides
Industrial Cybersecurity Market Worth $49.53 Billion by 2030
Industrial Cybersecurity Market, Cybersecurity, Network Security, Cloud Security, Cloud computing, Endpoint Security, Threat Management, Industrial Cybersecurity\n
1 views • 4 slides
Empowering Women in Cyber: CyberFirst Girls Competition
Embrace the future of technology and cybersecurity by joining the CyberFirst Girls Competition. Inspire the next generation of women to pursue careers in tech and make a difference in the world of cybersecurity. Explore opportunities, register, and support diversity in the cyber sector. #CyberFirst
0 views • 17 slides
Cybersecurity Career Path Overview
Discover the exciting world of cybersecurity with insights into different roles, resources for learning, career progression, and the importance of cybersecurity in today's digital landscape. Explore job roles like Cybersecurity Engineer, Incident Responder, Data Scientist, and more to build a succes
0 views • 11 slides
ctcLink Project Steering Committee College Readiness Discussion & Approval
The ctcLink Project Steering Committee convenes a meeting to discuss and approve college readiness for the upcoming go-live date. The agenda includes reviewing readiness status, voting on readiness for go-live, and planning next steps for the project. College leadership and voting members of the com
0 views • 28 slides
Enhancing California's Election Cybersecurity Readiness
California has taken significant steps to bolster its election cybersecurity readiness, including rigorous source code reviews, red team testing, and open-ended penetration testing. The state has visited fusion centers, engaged local election officials, upgraded technology infrastructure, and establ
0 views • 6 slides
Cybersecurity Tabletop Exercise Overview
In this cybersecurity tabletop exercise, participants engage in scenario-based discussions and action planning to enhance readiness for cyber incidents. The exercise covers welcome and introductions, agenda review, administrative details, benefits, objectives, and more to improve response capabiliti
0 views • 40 slides
Comprehensive Airport Cybersecurity Quick Guide and Assessment Tool
This project by the National Safe Skies Alliance aims to provide airports with a comprehensive Cybersecurity Quick Guide and Assessment Tool. The guide helps airport managers understand and address cybersecurity issues while the assessment tool evaluates the maturity of their cybersecurity efforts.
0 views • 24 slides
Ensuring Business Security: Cybersecurity Webinar Insights
Explore cybersecurity insights from Ronnie Viera, a seasoned professional in IT and cybersecurity, covering topics such as common threats, cybersecurity basics, and the importance of protecting personal information. Gain valuable knowledge on cybersecurity measures for safeguarding your business aga
0 views • 18 slides
Workshop on Cybersecurity Professionalism & Ethics
Explore the core concepts of professionalism and ethics in cybersecurity through this interactive workshop funded by the National Centers of Academic Excellence in Cybersecurity grant. Topics include defining professionalism, key skills for building professionalism, and understanding ethics in the w
0 views • 16 slides
Logistics and Communications Readiness Review Briefing
This briefing covers various aspects of logistics and communications readiness, including roll call, agenda, logistics readiness overview, FLIPLS details, projects overview, work orders, property book readiness overview, incoming and outgoing lateral transfers, excess equipment status, monthly inven
0 views • 30 slides
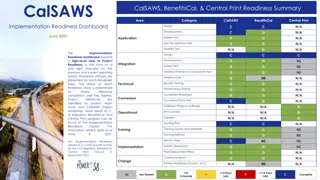
CalSAWS Implementation Readiness Dashboard Summary
The CalSAWS Implementation Readiness Dashboard provides a high-level view of project readiness for CalSAWS, BenefitsCal, and Central Print. It includes status indicators for various readiness areas, key project milestones, and risks. The dashboard reflects data as of June 4, detailing progress in de
0 views • 9 slides
Understanding S-100 Readiness Levels for Product Development
The concept of S-100 Readiness Levels, based on NASA's Technical Readiness Levels, is crucial for progressing ideas from research to regular product use. This framework, introduced by the International Hydrographic Organization, ensures a clear understanding of a specification's readiness for operat
0 views • 9 slides
Cybersecurity Workforce Management: Engage, Empower, Elevate
Explore the intricacies of Cybersecurity Workforce Management through engaging, empowering, and elevating your team. Discover the goals, challenges, and executive orders driving the cybersecurity workforce landscape, along with strategies to enhance workforce capabilities. Unveil the essence of pers
0 views • 27 slides
Cybersecurity and Computer Science Education Projects at UH Maui College
UH Maui College, supported by NSF, conducts various cybersecurity and computer science education initiatives led by Debasish Bhattacharya. The projects aim to enhance cybersecurity education, curriculum development, and workforce training, catering to a diverse student population. The college has re
0 views • 16 slides
Shovel-Ready Projects Initiative for Cybersecurity Innovation in Canada
This proposal outlines the launch of the Shovel-Ready Projects Initiative aimed at advancing cybersecurity innovation and talent development in Canada. The program, led by the National Cybersecurity Centre (NCC), seeks to fund eligible projects that enhance cybersecurity capabilities through researc
0 views • 19 slides
Enhancing Cybersecurity for Improved Insurability and Risk Management
In this resource, cybersecurity experts provide insights on improving cybersecurity insurability and minimizing rates. The content covers topics such as the cyber risk landscape, cyber insurance landscape, ransom payments, and ways to enhance cybersecurity measures. Key points include assessing info
1 views • 21 slides
Enhancing Education Accountability in North Dakota: The Choice Ready Initiative
The Choice Ready initiative in North Dakota aims to measure high schools' effectiveness in preparing students for success post-graduation. By focusing on metrics such as student readiness in essential skills, post-secondary readiness, workforce readiness, and military readiness, the initiative provi
0 views • 16 slides
Ethics in Cybersecurity: Evolution, Challenges, and Solutions
Explore the evolution of cybersecurity, from the days of firewalls to modern cybersecurity threats like viruses and ransomware. Understand the importance of ethics in cybersecurity, as it plays a vital role in building strong defense mechanisms to secure personal and enterprise data effectively.
0 views • 18 slides
IRIS H2020 Project - Enhancing Cybersecurity for SMART CITIES
The IRIS H2020 project is dedicated to enhancing cybersecurity for SMART CITIES by developing a framework that supports European CERT and CSIRT networks in detecting, sharing, and responding to cybersecurity threats in IoT and AI-driven ICT systems. The project aims to minimize the impact of cyberse
0 views • 5 slides
Defense Industrial Base (DIB) Cybersecurity Training Overview
This training module focuses on the importance of cybersecurity in the Defense Industrial Base (DIB) sector, particularly highlighting the Cybersecurity Maturity Model Certification (CMMC) and its implications for organizations seeking certification. The content includes insights on incident reporti
0 views • 10 slides
Cybersecurity Strategy in Japan - Roles of NISC and Basic Act Overview
The National Center of Incident Readiness and Strategy for Cybersecurity (NISC) plays a crucial role in Japan's cybersecurity landscape, integrating policies and handling cyber attacks 24/7. The Basic Act on Cybersecurity, enforced since January 2015, establishes a clear legislative framework and or
0 views • 12 slides
College & Career Readiness
Beth Bender, Ph.D., Associate Superintendent of College and Career Readiness, presented on creating a big picture of college and career readiness, immediate goals, and the role of high school counselors. The session included discussions on utilizing partnerships, setting long-term goals, and a trans
0 views • 10 slides
Understanding CYBEX - Cybersecurity Information Exchange Techniques
CYBEX introduces a new cybersecurity paradigm focusing on identifying weaknesses, minimizing vulnerabilities, and sharing attack heuristics within trusted communities. It emphasizes the importance of information exchange, policy, and identity assurance in combating cyber threats. The model aims to s
0 views • 14 slides
Shadow: Scalable and Deterministic Network Experimentation in Cybersecurity
The presentation discusses the concept of deterministic experimentation in cybersecurity, emphasizing the importance of experimental control and scalability in large distributed systems like Tor. It introduces Shadow, a network simulator designed to achieve repeatable and realistic experiments for r
0 views • 15 slides
Framework Roadmap Overview - July 2018
The Framework Roadmap draft highlights key areas of development relevant to the Framework, including Confidence Mechanisms, Cyber Attack Lifecycle, Cybersecurity Workforce, Cyber Supply Chain Risk Management, Federal Agency Cybersecurity Alignment, Governance and Enterprise Risk Management, Identity
0 views • 7 slides