Cryptographic Reductions and Learning in Computational Complexity
This lecture explores the connection between computational complexity and cryptography, focusing on topics like pseudorandom functions, public-key cryptography, and learning from Gaussians. It delves into the implications of cryptographic reductions, lower bounds for learning MLPs, and the existence
3 views • 22 slides
Cryptographic Data Integrity Algorithms
Cryptographic data integrity algorithms ensure data integrity, verifying data received matches what was sent by authorized entities. Cryptographic hash functions play a crucial role in ensuring data integrity through hash values. Applications include message authentication, digital signatures, and v
7 views • 41 slides
Enhancing Cryptographic Key Generation with High-Quality Randomness
This presentation discusses the critical aspect of ensuring high-quality randomness in cryptographic key generation processes. It explores key vulnerabilities and common failure modes, emphasizing the importance of incorporating strong randomness. The content delves into various methods and issues r
2 views • 45 slides
Fill Area Primitives in Computer Graphics
An overview of fill area primitives in computer graphics, including the concept of fill areas, polygon fill areas, and polygon classifications into convex and concave polygons. This module covers the efficient processing of polygons, approximating curved surfaces, and generating wire-frame views of
1 views • 63 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
2 views • 33 slides
Zeroizing Attacks on Cryptographic Multilinear Maps: Overview and Applications
Cryptographic multilinear maps (MMAPs) enable computations on encoded secret data, offering similarities to fully homomorphic encryption (FHE) while providing distinct features. MMAPs find applications in identity-based encryption, non-interactive zero-knowledge proofs, and more. The evolution of MM
2 views • 45 slides
Cryptographic Protocols and Key Exchange
This content delves into the world of cryptographic protocols, discussing the importance of security measures such as symmetric cryptography, hash functions, and public-key cryptography. It explores the field's various studies, goals, Diffie-Hellman key exchange, and the significance of key size in
5 views • 28 slides
Graphics Output Primitives and Coordinate Reference Frames
Graphics output primitives and coordinate reference frames play a crucial role in describing scenes and drawing basic geometric structures in 2D space. These concepts involve defining points, drawing lines, and understanding pixel coordinates within a coordinate system. Absolute and relative coordin
7 views • 35 slides
New Assumptions for Achieving Chosen Ciphertext Security in Cryptography
This research work focuses on presenting new assumptions for achieving chosen ciphertext security in public key encryption. The study aims to clarify the necessary and sufficient assumptions to realize general cryptographic primitives, particularly focusing on CCA secure PKE and KEM. The ultimate go
0 views • 27 slides
Scalable Cryptographic Authentication for High Performance Computing
This work discusses the scalable cryptographic authentication approach developed by Andrew Prout and team for high-performance computing. The LLGrid system architecture, challenges with interactive supercomputing, and utilization of LLGrid for various computing tasks are explored, highlighting the i
0 views • 34 slides
IEEE 802.11-21/1774r0 ARC Clause 6: Overview of Management Primitives
This content delves into Clause 6 of IEEE 802.11-21/1774r0, focusing on the overview of management primitives such as SME, MLME, PLME, and SAP. It discusses the communication between SME and MAC, generic management primitives dealing with MIBs, and MLME SAP Interface services in an abstract manner.
2 views • 13 slides
MIT Foundations of Cryptography Lecture 22
In lecture 22 of MIT's Foundations of Cryptography series, delve into advanced cryptographic concepts and techniques. From modern encryption algorithms to cryptographic protocols, this lecture offers profound insights to enhance your cryptographic knowledge and understanding. Explore cutting-edge to
3 views • 46 slides
Security: An Overview of Cryptographic Techniques
Delve into the realm of cryptography with a comprehensive overview of techniques and protocols for ensuring secure communication channels. Explore the concepts of authentication, confidentiality, integrity, and availability. Uncover the tools and methodologies used in building cryptographic schemes
1 views • 26 slides
Basic Cryptography
Cryptography is a mathematical method used to protect information in modern computing. This course covers cryptographic primitives such as hash functions, symmetric and asymmetric encryption, digital signatures, and their applications. Learn about the importance of cryptographic hash functions, usin
4 views • 19 slides
Synchronization and Scaling Challenges
Study the impact of synchronization on scaling, exploring hardware artifacts and higher-level primitives. Learn how synchronization ensures coordination, the hindrance to scalability, and the overheads that arise. Understand basic hardware artifacts like CAS, TAS, FAI, and synchronization primitives
5 views • 53 slides
OpenGL Primer: Drawing Graphics Primitives and Rendering Polygons
This content covers fundamental concepts of OpenGL, including drawing graphics primitives, rendering polygons as points, outlines, or solids, and working with buffers. It explains the use of OpenGL functions for defining points, lines, triangles, and polygons, along with techniques for adjusting ren
0 views • 34 slides
Efficiency Improvement in L0 Performance Simulation Using Primitives Alignment
In the L0 performance simulation scenario presented, the alignment of primitives from detectors within timeslots plays a crucial role in enhancing trigger efficiency. Timeslot width expansion to accommodate measurement errors and the impact of detector primitive alignment on resolution are discussed
1 views • 10 slides
Cryptographic Signatures: Hash, RSA, and ECDSA Explained
In this content, the concepts of cryptographic signatures are explored, covering topics such as the hash and sign paradigm, the vulnerabilities of plain RSA signatures, RSA-FDH, and ECDSA (used in Bitcoin). The content delves into signature schemes, security definitions, threat models, and formal de
2 views • 38 slides
Cryptographic Hashing
Cryptographic hashing is a key concept in data security, ensuring data integrity and authenticity. Learn about the properties of good cryptographic hashes, the difference between encryption and hashing, and delve into the specifics of SHA-1, its collisions, and processing of original messages. Under
0 views • 39 slides
GPU Programming Primitives for Computer Graphics
This book covers advanced topics in GPU programming for computer graphics, including parallel reduction, prefix scan, programming primitives, linear probing, radix sort, and code optimization. It delves into the motivation behind leveraging thousands of threads on GPUs and addresses various challeng
3 views • 85 slides
Overview of SHM Support Options and Primitives
This content provides an overview of SHM (Shared Memory) support options and primitives, detailing regions, commands, responses, addresses, mappings, utilities, providers, and protocols used in SHM communication. It covers the adaptation of primitives for local communication, the use of native provi
1 views • 24 slides
Investigating Semantic Primitives Using an OWL-based Ontology
The investigation focuses on identifying semantic primitives in English using an OWL-based ontology approach. By analyzing basic concepts and frequent words, the study aims to determine the minimal set of semantic relations essential for logical representation, emphasizing the importance of minimizi
2 views • 22 slides
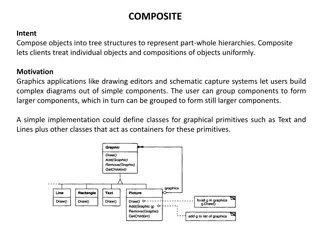
Representing Part-Whole Hierarchies with Composite Pattern
The Composite pattern allows for composing objects into tree structures to represent part-whole hierarchies, enabling clients to treat individual objects and compositions uniformly. This pattern is commonly used in graphics applications for creating complex diagrams out of simple components. By defi
1 views • 43 slides
Cryptographic Complexity of the Worst Functions Unveiled
Delve into the cryptographic complexity of the worst functions with expert insights from Amos Beimel, Yuval Ishai, Ranjit Kumaresan, and Eyal Kushilevitz. Explore the models, security considerations, and advancements in secure computation within information-theoretic frameworks. Understand the chall
2 views • 46 slides
Unclonable Secret Sharing and Quantum Primitives Overview
Explore the concept of unclonable secret sharing, its implications in quantum cryptography, and the advancement of quantum primitives such as quantum key distribution and quantum copy-protection. Discover the potential of unclonable encryption in preventing data copying by cloud servers, and delve i
2 views • 23 slides
IEEE 802.15.8 Architecture for WPANs
Explore the detailed architecture of IEEE 802.15.8 for Wireless Personal Area Networks (WPANs), delving into MAC information flow, service primitives, and management aspects. This document offers insights into the organization of MAC layers, access points, and data primitives for efficient network o
1 views • 14 slides
Idealized Model for Cryptographic Primitives and Indifferentiability Framework
Explore new notions and constructions in public key crypto-systems, leakage resilience, related-key attack PKE, and idealized models for cryptographic primitives such as hash functions, random oracles, and more. Learn about the concept of Ideal NIKE and the Indifferentiability Framework in the conte
6 views • 20 slides
Cryptographic Techniques Overview
This overview explores cryptographic techniques, including cryptography, cryptographic protocols, key distribution, and the essentials of secure communication channels. It discusses the significance of authentication, confidentiality, integrity, and availability in maintaining secure channels. The c
3 views • 61 slides
NIST Cryptographic Standards Update and Project Progress
Learn about the progress and updates on the NIST Cryptographic Standards project, including the status of submissions, first-round candidates, and standardization guidelines for post-quantum cryptographic technology. Stay informed on the latest developments in cryptography from NIST.
3 views • 13 slides
Construction of Salsa20 and ChaCha Cryptographic Algorithms
This text discusses the construction and core functions of the Salsa20 and ChaCha cryptographic algorithms, highlighting their design principles, input parameters, and similarities in structure and operation. Salsa20, a family of flow-through cryptographic algorithms, was designed by Daniel J. Berns
2 views • 21 slides
Construction of Cryptographic Algorithms Salsa20 and ChaCha
This discussion delves into the construction of cryptographic algorithms Salsa20 and ChaCha, presenting insights into their designs, functions, and key components. Salsa20, part of the eSTREAM competition, is explored for its flow-through structure while ChaCha's unique composition and core function
0 views • 15 slides
Hardware Description Language Overview: Verilog, HDL, and Primitives Explained
Learn about Hardware Description Language (HDL) and its key components like Verilog and Primitives. Explore how HDL is used to describe digital system hardware, the concepts behind it, and its significance in integrated circuit design.
0 views • 16 slides
Cryptographic Groups and Ideal Models Overview
Explore AGMOS, ideal models, and criticisms in the realm of cryptographic groups. Understand the significance of oblivious sampling and spurious knowledge assumptions in cryptographic design.
0 views • 15 slides
Computer Graphics Output Primitives and Functions Overview
Explore the fundamentals of computer graphics output primitives like lines, points, arcs, circles, rectangles, and more. Learn about point scan conversion, pixel intensity values, and C/C++ implementations for setPixel and getPixel functions in graphic applications. Dive into the world of graphics w
2 views • 99 slides
Graphics Pipeline Rasterization and Drawing Concepts for Rendering
Explore the key concepts of graphics pipeline rasterization, drawing primitives, line algorithms, and polygon rasterization in this informative collection. Learn about visible parts of primitives, shading, pixel generation, and more in the rendering process.
1 views • 24 slides
ECE344 Lab Assignment on Synchronization Primitives and Problems
Explore the ECE344 lab assignment focusing on implementing synchronization primitives like locks and condition variables, solving synchronization problems, and tackling scenarios like mice and cats dining. Dive into the details of operation code and learn about avoiding starvation issues in the syst
3 views • 7 slides
Python Core Data Types Overview: Primitives, Integrals, and Floats
Explore Python's core data types including primitives, integrals (int, bool, float, complex), and floats. Learn about how these types are stored as objects, limitations, and special values. Understand the differences between integers versus floating-point numbers in Python.
2 views • 18 slides
Understanding Cryptographic Hashing and SHA Algorithms
Discover the key concepts of cryptographic hashing, the properties of good cryptographic hashes, and insights into SHA algorithms such as SHA-1, SHA-2, and SHA-3. Learn about collisions, message padding, and the security features of SHA-256.
3 views • 39 slides
Enhancing Wireless Network Security with New Key Exchange Method
Explore the challenges in securing wireless networks, including de-auth attacks and MAC address spoofing. A proposal is discussed for a faster and safer key exchange method, introducing new service primitives for improved security. Learn about the MLME-LINK-SETKEY-REQUEST, MLME-LINK-SETKEY-RESPONSE,
2 views • 15 slides
Understanding Cryptographic Hashing and SHA Algorithms
Explore the concepts of cryptographic hashing, the properties of good cryptographic hashes, and the significance of SHA (Secure Hash Algorithm) in ensuring data integrity and security. Learn about the distinction between encryption and hashing, the practical applications of cryptographic hashing, an
1 views • 38 slides