Cross-Border Injury Claims in Canada_ Navigating Legal Complexities for Fair Compensation(20_03_2024)
Cross-Border Injury Claims in Canada: Navigating Legal Complexities for Fair Compensation\n\nIn the vast landscape of Canadian law, navigating the complexities of cross-border accidents and injuries requires a specialized approach. From out-of-province accidents to cross-border motor vehicle collisi
0 views • 2 slides
Automated Mobile App QoE Diagnosis with Cross-layer Analysis
This work presents the QoE Doctor, a solution for accurate and repeatable QoE measurements and analysis in mobile apps. By introducing UI automation, it enables the replay of user behavior to measure UI layer QoE metrics without modifying app source code. The QoE Doctor also supports multi-layer dia
2 views • 28 slides
Cross-platform C++ Development with CMake and vcpkg
Explore the process of creating cross-platform C++ projects using CMake and vcpkg. Learn about the motivation behind build and meta-build systems, the usage of CMake for project configuration, the significance of cross-platform dependency managers like vcpkg, and how to integrate CMake with vcpkg fo
7 views • 36 slides
Layer 2 Token Marketing Services
Layer-2 token marketing promotes tokens built on scalable layer-2 solutions, highlighting benefits like faster transactions and lower fees. Get connected with our experts today and launch a lucrative \ntoken platform.
0 views • 3 slides
Understanding Ozone Depletion: Causes and Impact
The ozone layer, found in the stratosphere at 15 to 40 km altitude, plays a crucial role in absorbing harmful ultraviolet radiation. However, due to the use of Chlorofluorocarbons (CFCs), the ozone layer has been depleted, leading to the formation of the ozone hole. This depletion is caused by chemi
0 views • 27 slides
Understanding Makefiles in Intermediate Programming
Makefiles are essential for automating the build process in programming projects by defining rules for building target files based on dependencies. By organizing commands and dependencies in a structured manner, Makefiles simplify the build process, reduce errors, and save time. This article covers
0 views • 18 slides
Understanding Multi-Layer Perceptrons in Neural Networks
In this lecture by Dr. Erwin Sitompul at President University, the focus is on Multi-Layer Perceptrons (MLP) in neural networks, discussing their architecture, design considerations, advantages, learning algorithms, and training process. MLPs with hidden layers and sigmoid activation functions enabl
2 views • 17 slides
NASA Platform Layer Updates for the CAELUM (7.0) Release
The National Aeronautics and Space Administration (NASA) discusses platform layer updates for the CAELUM (7.0) release of the Core Flight System in the 2021 Flight Software Workshop. The platform layer consists of the Operating System Abstraction Layer (OSAL) and Platform Support Package (PSP), whic
1 views • 20 slides
Understanding Database Normalization and Functional Dependencies
Database normalization is a crucial process that aims to improve database design by organizing data into higher forms of normality. This helps in reducing redundancy and ensuring data integrity. Functional dependencies play a key role in defining relationships between attributes in a database. By un
0 views • 33 slides
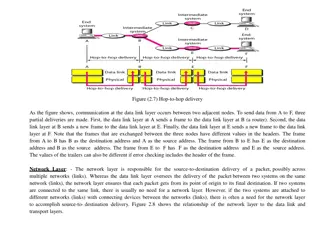
Understanding Communication Layers in Computer Networks
Communication in computer networks is facilitated through different layers such as the data link, network, and transport layers. Each layer has specific responsibilities in ensuring data delivery from one point to another. The data link layer handles communication between adjacent nodes, the network
3 views • 7 slides
Comprehensive RAID Log Presentation and Management Overview
This comprehensive presentation template provides a detailed overview of a RAID log, including risks, issues, threats, assumptions, dependencies, and reliance factors. It offers insights on tracking and managing different aspects of project planning and execution, categorized by risk levels. The bre
0 views • 6 slides
Understanding Boundary Layer and Drag Forces in Fluid Dynamics
Boundary layer module explains the presence of viscous forces near a surface due to fluid flow, leading to laminar or turbulent boundary layers. Flow separation occurs when a boundary layer detaches from a surface, impacting lift and drag forces. Adverse pressure gradients and flow separation phenom
0 views • 19 slides
Understanding Paper and Thin Layer Chromatography (TLC) in Biochemistry
Chromatography techniques are used in laboratories to separate and identify components of mixtures. Paper chromatography is a type where a developing solution travels up a filter paper, separating compounds based on their affinity to the stationary phase. Thin Layer Chromatography (TLC) is a similar
0 views • 22 slides
Understanding the OSI Model and Layered Tasks in Networking
The content highlights the OSI model and layered tasks in networking, explaining the functions of each layer in the OSI model such as Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, and Application Layer. It also discusses the interaction between l
1 views • 41 slides
Understanding the Impact of Dirty Data on Quality Improvement
Real-world data often contains errors and inconsistencies, leading to significant costs for businesses. Research activities focus on error correction, object identification, profiling, and data integration to enhance data quality. A principled approach based on data dependencies offers a promising s
0 views • 53 slides
Bedforms in Unidirectional Flow: Characteristics and Formation
Bedforms in unidirectional flow exhibit various characteristics such as sediment layer thicknesses, boundary layer dynamics, presence of ripples and dunes, and the interplay between flow velocity and sediment deposition. These bedforms, including ripples and dunes, form due to interactions between t
3 views • 13 slides
Understanding RARP and Transport Layer in Computer Networking
Exploring Reverse Address Resolution Protocol (RARP) for mapping physical addresses to logical addresses in networking, along with insights on the Transport Layer's role in providing communication services to application processes. Learn about RARP packet formats, encapsulation, and the significance
0 views • 41 slides
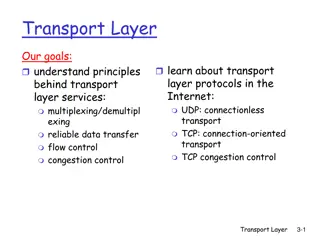
Understanding Internet Transport Layer Services and Protocols
In the realm of networking, exploring the principles of transport layer services is crucial. This involves concepts like multiplexing/demultiplexing, reliable data transfer, flow control, and congestion control, which are facilitated by protocols such as UDP and TCP. The transport layer acts as a br
0 views • 56 slides
Understanding Data Link Layer Communication in Computer Networks
Exploring the data link layer in computer networks, this lecture discusses the node-to-node communication, services provided, such as framing, flow control, error control, and congestion control. Through a series of images, the concept of links and nodes, as well as the responsibilities of the data
0 views • 16 slides
Understanding Data Link Layer in Computer Networking
The Data Link Layer (DLL) is the second layer of the OSI model, responsible for error detection and correction, framing, addressing, synchronization, flow control, and multi-access protocols. It deals with logical link control and media access control, addressing destination hardware, avoiding data
0 views • 49 slides
Enhancements to International Survey of Herbicide Resistant Weeds and Website Overhaul Plan
In 2019, Ian Heap, Director of the International Survey of Herbicide Resistant Weeds (HRAC), is leading an initiative to enhance the survey and overhaul the website to target completion by year-end. The website will undergo a three-tiered redesign focusing on presentation layer, application layer, a
0 views • 11 slides
Comprehensive RAID Log Presentation Template
This comprehensive presentation template includes a RAID log with risks, assumptions, issues, and dependencies structured in a professional layout. Utilize this template to effectively manage project risks and dependencies. The template also features a simple RAID log slide template for a clear over
0 views • 7 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Understanding Data Dependencies in Nested Loops
Studying data dependencies in nested loops is crucial for optimizing code performance. The analysis involves assessing dependencies across loop iterations, iteration numbers, iteration vectors, and loop nests. Dependencies in loop nests are determined by iteration vectors, memory accesses, and write
0 views • 15 slides
Red Cross Shelter Partnership Initiative in Missouri
The Red Cross supports a Faith-Based Organization (FBO) Initiative in Missouri, inviting organizations to assist primarily in sheltering efforts for disaster response in the community. The National Shelter System shows numerous Red Cross shelters in Missouri, with advantages to partnering with the R
0 views • 16 slides
Understanding ZFS: Structure and Operations
Explore the comprehensive structure and operations of ZFS, covering aspects like MOS layer, object-set layer, Dnode, Block Pointer, and TRIM operations. Learn about the meta-object set (MOS), dataset and snapshot layer (DSL), and storage pool allocator (SPA) modules within ZFS. Understand how ZVOLs,
0 views • 10 slides
Understanding the Planetary Boundary Layer in Atmospheric Science
The Planetary Boundary Layer (PBL) plays a crucial role in atmospheric dynamics, divided into surface, mixed, stable, and residual layers. During the day, the mixed layer experiences convective motions due to surface heating, while the stable layer dominates during the night. Understanding these lay
0 views • 18 slides
Statistical Dependencies in Sparse Representations: Exploitation & Applications
Explore how to exploit statistical dependencies in sparse representations through joint work by Michael Elad, Tomer Faktor, and Yonina Eldar. The research delves into practical pursuit algorithms using the Boltzmann Machine, highlighting motivations, basics, and practical steps for adaptive recovery
0 views • 47 slides
Understanding Transport Layer Security (TLS) and Secure Sockets Layer (SSL)
This content delves into the concepts of Transport Layer Security (TLS) and Secure Sockets Layer (SSL), exploring their origins, application in web security, and protocol stack integration. It covers the TLS/SSL handshake process, key derivation, data transfer mechanisms, and the significance of the
0 views • 26 slides
Understanding UML Package Diagrams and Components in Software Design
UML package diagrams are essential in organizing model elements such as use cases and classes into groups for a better structure in system modeling. They help in providing a high-level overview of requirements and architecture, logically modularizing complex diagrams, and indicating dependencies bet
0 views • 38 slides
Enhancing Cross-Layer Optimizations in Online Services
Research explores cross-layer optimizations between network and compute in online services to improve efficiency. It delves into challenges such as handling large data, network tail latency, and SLA budgets. The OLS software architecture, time-sensitive responses, and split budget strategies are dis
0 views • 29 slides
A Cross-Layer BPaaS Adaptation Framework Overview
This framework addresses the problematic issues of flexibility and cost reduction in Business Processes as a Service (BPaaS) by monitoring and adapting BPaaS in a cross-layer manner. It focuses on handling the entire lifecycle of BPaaS and covers adaptation mechanisms for different layers in the clo
0 views • 17 slides
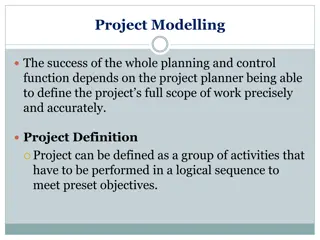
Exploring Project Modelling and Work Breakdown Structures
In project management, precise project definition is crucial for successful planning and control. Project modelling involves utilizing tools like Work Breakdown Structure (WBS) to efficiently define project scopes and hierarchies. By breaking down the project into smaller elements of work, WBS aids
0 views • 37 slides
Understanding ARP, ICMP, and DHCP in TCP/IP Protocol Stack
ARP (Address Resolution Protocol) plays a crucial role in bridging the Layer 2/Layer 3 addressing boundary in the TCP/IP protocol stack, allowing IP to be agnostic about layer 2 addressing while still using layer 2 for packet delivery. Machines ARP for MAC addresses within their local network, where
0 views • 39 slides
Cherishing the Old Rugged Cross
On a hill far away stood an old rugged cross, a symbol of suffering and love. The cherished cross, despised by the world, holds a wondrous attraction for those who believe. Stained with divine blood, it symbolizes forgiveness and sanctification. The lyrics beautifully express the deep connection to
0 views • 9 slides
Software Bug Localization with Markov Logic
Software bug localization techniques like Tarantula focus on finding likely buggy code fragments in a software system by analyzing test results, code coverage, bug history, and code dependencies. The lack of an interface layer in existing techniques leads to handcrafted heuristics, posing a persiste
0 views • 17 slides
Loop Invariant Code Motion in Frequent Paths for Optimization
Loop Invariant Code Motion (LICM) is a key optimization technique that identifies and moves code operations whose operands remain constant within a loop to improve performance. The process involves careful consideration of memory operations and operations not executed every iteration. The assignment
0 views • 20 slides
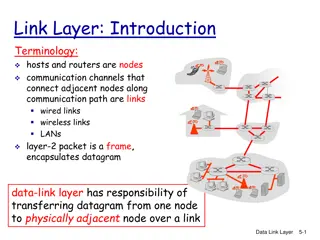
Understanding the Link Layer in Computer Communication and Networks
The link layer, an essential component in computer networks, is implemented at every host through adapters like NICs or Ethernet/802.11 cards. It handles tasks such as frame encapsulation, error checking, and flow control to ensure reliable data transmission between nodes. Link layer services includ
0 views • 64 slides
Understanding Link Layer in Computer Networking
The link layer, also known as the data link layer, plays a crucial role in transferring data between adjacent nodes over communication links. This layer is responsible for framing, access control, reliable delivery, error detection and correction, flow control, and more. It is implemented in network
0 views • 34 slides
Network Configuration Complexity and Verification Tools
The content discusses the challenges of managing complex router configurations involving multiple routing protocols, metrics, and filters. It highlights the importance of using network verification tools to proactively detect errors and policy violations. Various tools such as Tiramisu, Minesweeper,
0 views • 26 slides