Sales Leadership Management
Marketing channel decisions play a crucial role in the success or failure of products in both B2C and B2B markets. This chapter explores the importance of effective channel management, types of channels, the role of intermediaries in streamlining transactions, and the distinction between marketing c
1 views • 18 slides
Understanding Payment Channels in Cryptocurrency Networks
Explore the concept of payment channels in cryptocurrency networks to address scalability issues and reduce transaction costs. Learn how these channels enable fast and cost-effective transactions by minimizing blockchain usage. Discover the innovative solutions proposed by experts in the field.
3 views • 37 slides
How to Scrape Emails Data from YouTube Channels
Learn to ethically scrape email data from YouTube channels using Python libraries and YouTubes Data API for targeted marketing. \n\nknow me>>\/\/ \/scrape-emails-data-from-youtube-channels.php\n
0 views • 10 slides
How to Scrape Emails Data from YouTube Channels
Learn to ethically scrape email data from YouTube channels using Python libraries and YouTubes Data API for targeted marketing. \n\nknow me>>\/\/ \/scrape-emails-data-from-youtube-channels.php\n
1 views • 10 slides
How to Scrape Emails Data from YouTube Channels (1)
Learn to ethically scrape email data from YouTube channels using Python libraries and YouTubes Data API for targeted marketing. \n\nknow me>>\/\/ \/scrape-emails-data-from-youtube-channels.php\n
1 views • 10 slides
How to Scrape Emails Data from YouTube Channels (1)
Learn to ethically scrape email data from YouTube channels using Python libraries and YouTubes Data API for targeted marketing. \n\nknow me>>\/\/ \/scrape-emails-data-from-youtube-channels.php\n
1 views • 10 slides
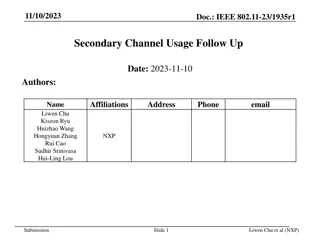
Enhancing Secondary Channel Usage in IEEE 802.11 Standards
This document, IEEE 802.11-23/1935r1, delves into the intricacies of secondary channel usage within the context of IEEE 802.11 standards. Key topics covered include discussions on RU index, BW negotiation in secondary channels, methods to ensure medium synchronization when transitioning back to prim
0 views • 14 slides
Understanding Hydraulics II: Simulation and Analysis in Open Channels
Dive into Hydraulics II to explore complex flow fields, dimensional analysis, pipe network analysis, and design of reticulation systems. Learn about steady and unsteady flows in open channels, Chezy's and Manning's equations, and the different flow regimes in open channels. Gain insights into unifor
5 views • 5 slides
Understanding Telecommunications Transmission Systems
Transmission systems in telecommunications provide circuits between network nodes using channels for bidirectional communication. Channels can range from simple audio circuits to complex satellite systems. Signals can be analog or digital, each with its unique characteristics. Bandwidth is crucial f
0 views • 32 slides
Understanding Distribution Channels in Marketing Management
Distribution channels play a vital role in moving products from producers to consumers efficiently. This involves various middlemen and processes such as physical distribution and logistics. By understanding the types of distribution channels and factors affecting their choice, businesses can enhanc
8 views • 10 slides
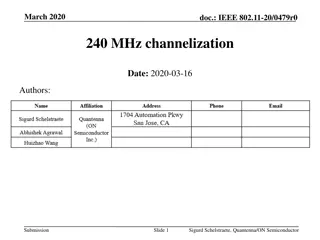
IEEE 802.11-20/0479r0 240 MHz Channelization Options
The document discusses agreements on 240 MHz channelization in IEEE 802.11-20/0479r0, presenting three options: contiguous non-overlapping channels, any combination of three consecutive 80 MHz channels, and puncturing of a 320 MHz channel. Various considerations and questions are raised regarding th
0 views • 12 slides
Understanding International Distribution Channels
In the modern era of large-scale production and specialization, producers face challenges in distributing their goods to consumers. International distribution channels play a crucial role in connecting producers with consumers through various intermediaries. Definitions by Philip Kotler, Richard Bus
1 views • 5 slides
Understanding Human Behavior: Foundations and Factors
Human behavior is a multifaceted subject influenced by genetic makeup, culture, and individual values. It encompasses both overt actions and covert thoughts, a product of the individual and environmental factors. Psychologists study behavior from visible (overt) actions like playing football to inne
0 views • 20 slides
Understanding Side Channels in Software Security
This content delves into the topic of side channels in software security, focusing on the leakage of sensitive information through timing side channels. It discusses the concept of covert channels, reference monitors, limitations of analysis, and prevention strategies to mitigate the risks associate
0 views • 25 slides
Covert Actions and Their Consequences
The chapter discusses foreign covert actions, their limited statutory control, and the President's discretion in carrying them out. It delves into the Bay of Pigs incident, forms of covert actions like propaganda and paramilitary actions, unintended consequences, and the Neutrality Act of 1794. The
1 views • 31 slides
Eisenhower's Cold War Policies and Covert Operations
Eisenhower's Cold War policies focused on Massive Retaliation, Brinkmanship, and Covert Operations. He believed in investing in nuclear weapons and used threats of nuclear capabilities to deter conflicts. The CIA carried out covert operations to overthrow anti-American leaders in different countries
0 views • 10 slides
Covert Visual Search and Effective Oculomotor Range Constraints
The study delves into whether covert visual search is biologically limited by the Effective Oculomotor Range (EOMR), exploring neuropsychological evidence, eye movement studies, and participant measurements. It investigates the impact on visual search tasks, including color, orientation, and conjunc
1 views • 15 slides
Enhancing Spectrum Efficiency with Low Complexity Erasure Codes in IEEE 802.11 Document
This document delves into the implementation of erasure codes for content channels in IEEE 802.11 systems. By utilizing erasure codes, spectrum efficiency can be boosted without significantly increasing the complexity of encoding and decoding processes. The discussion also covers the duplication of
0 views • 20 slides
Covert Actions and Laws: A Historical Overview
Covert actions, unconstrained by domestic laws, have been historically carried out by various entities in different ways. This overview delves into the Intelligence Authorization Act of 1991, limitations imposed by Congress, utilization of private contractors, challenges in enforcement, and relevant
0 views • 74 slides
Insights on 4Music and Box Channels Q3 2018 Audience Behavior
The Q3 2018 data highlights the audience behavior of 4Music and Box Channels, showing that viewers are commercially receptive, influenced by celebrities, and trendsetters who influence the purchase decisions of others. They engage with TV advertising, seek out products seen in ads, and value ads fea
0 views • 7 slides
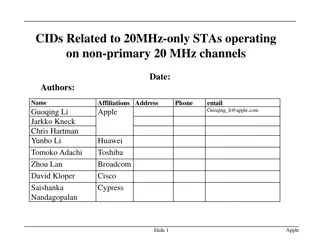
Proposal for Enhancing Operation of 20MHz-Only STAs on Non-Primary Channels
The proposal aims to clarify how 20MHz-only STAs can operate on non-primary 20MHz channels, introducing protocol components and considerations for seamless operation. It suggests allowing optional operation on secondary channels and specifies signaling, behavior norms, and capabilities for optimal p
0 views • 19 slides
Understanding Ion Channels in Cell Communication
Ion channels play a crucial role in cell communication by allowing ions to pass through cell membranes, controlling various cellular functions. Their high transport rate and electrochemical gradient differentiate them from other ion transporter proteins. Ion channels have diverse biological roles, i
0 views • 26 slides
Latest Update on Sci-ECAL MIP Results by Jiaxuan Wang
Jiaxuan Wang presents an update on Sci-ECAL MIP results as of March 8, 2024. The new method for muon energy reconstruction involves multiple fittings to exclude noise hits and obtain the real track and hits. The muon energy is estimated around 0.3049 MeV using new MIP calibration results. Despite pr
0 views • 4 slides
Comprehensive Guide for Rule 40 Submission Template Deck
This guide provides a detailed outline on what to include in a Rule 40 submission template deck, covering aspects such as campaign overview, athlete details, campaign channels and tactics, along with sample creative assets for various channels. It offers insights on campaign name, theme, key messagi
0 views • 8 slides
IEEE 802.11-19-1156/r0: 20MHz Channel Usage Options
This document discusses the utilization of 20MHz channels in IEEE 802.11-19-1156/r0 standard, focusing on high-bandwidth use-cases such as cooperative perception. It addresses the impact of concurrent transmission in adjacent channels, the importance of predetermined sub-channels for efficient servi
0 views • 14 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
Covert Computation: Ensuring Undetectable Engagement
Covert computation aims to conceal the fact that computation is occurring and hide engagement in certain tasks like secure computation, authenticated key exchange, and more. By making messages indistinguishable and utilizing steganographic channels, it becomes possible to keep the activities covert
0 views • 16 slides
Proposal for Improved Channel Access Efficiency in IEEE 802.11 Networks
The proposal addresses the inefficiencies in utilizing secondary channels in IEEE 802.11 networks, aiming to enhance access to wideband channels (>20 MHz) when the primary channel is busy. It introduces a mechanism for APs and STAs to access available secondary channels while the primary channel is
0 views • 7 slides
IEEE 802.11-24/0070r1 Presentation on Non-Primary Channel Access
This presentation discusses the concept of using secondary channels for PPDU transmission in IEEE 802.11 networks to improve efficiency in large bandwidth scenarios. It covers topics such as channel access, backoff mechanisms, and channel switching thresholds. Design principles emphasize minimal imp
0 views • 15 slides
Understanding Channels of Distribution in Business
Channels of Distribution play a crucial role in the movement of goods and services from manufacturers to end consumers. This involves the allocation and transfer of products through various intermediaries, impacting sales and availability. The types of channels include Direct, Indirect, and Hybrid c
0 views • 20 slides
Understanding Export Distribution Channels and Factors
Explore the complex world of export distribution channels, comparing direct and indirect exporting methods, logistics components, selection criteria for transport modes, and the importance of insurance in international trade. Learn about the advantages and disadvantages of different distribution str
0 views • 15 slides
Understanding Marketing Channels and Their Importance
Marketing channels refer to the various institutions and processes involved in transferring a product from the producer to the consumer. These channels play a crucial role in reducing transaction costs, providing market information, managing risks, and promoting products. Intermediaries such as reta
0 views • 19 slides
Understanding the 4 Ps of Place in Marketing Channels
Place in the marketing mix refers to the distribution channels ensuring product availability. Channels of distribution vary from traditional (wholesalers) to modern (direct sales). Factors influencing channel choice include target market profile, location, product image, ease of delivery, payment ar
0 views • 8 slides
Understanding Spectre and Meltdown Security Flaws
Recent security vulnerabilities named Spectre and Meltdown have surfaced in the realm of computer architecture and hardware implementation. These flaws allow attackers to access sensitive data through covert channels utilizing speculative execution mechanisms. The vulnerabilities exploit the perform
0 views • 12 slides
Understanding Covert Timing Channels in Network Security
Covert timing channels are a method of leaking sensitive information across networks by violating security policies. These channels rely on conveying information through packet arrival patterns rather than the contents of the packets. Military applications, detection by USA government agencies, and
0 views • 26 slides
Multi Division in Networking: Access Methods & Duplexing Techniques
Reviewing the concepts of multi-division in networking, this content delves into the need for multiple control channels, challenges in sharing channels, techniques like ALOHA and CSMA, and the importance of control channels and data channels. It explores access methods for control and data channels,
0 views • 20 slides
Vehicular-to-Pedestrian Channel Models for Improved Road Safety
Protecting vulnerable road users through reliable vehicle-to-pedestrian communications is crucial to reducing accidents. This study emphasizes the need for accurate V2P channel models to enhance communication systems, highlighting the importance of V2P path loss models and comparing V2X channels. Mo
0 views • 18 slides
Enhancing Wireless LAN Throughput with Multiple Primary Channels
This document discusses the need for increasing system throughput in wireless LAN networks due to the growing demand for WLAN traffic. By introducing multiple primary channels, unused resources scattered across various channels can be exploited to improve quality of service and enhance transmission
0 views • 20 slides
Understanding Side Channels and Information Hiding Techniques in Advanced Information Assurance
This content covers various aspects of advanced information assurance, focusing on side channels and information hiding techniques such as digital watermarking, steganography, and covert channels. It discusses the concept of side-channel attacks, types of system and network channels, fault attacks,
0 views • 24 slides
Understanding the Importance of Anonymous Communication in Digital World
Explore the concept of information hiding, including digital watermarking, steganography, covert channels, and anonymous communication. Learn how anonymity can benefit journalists, whistleblowers, activists, executives, and more, while also providing privacy for everyday individuals. Discover the ch
0 views • 56 slides