Understanding Greedy Algorithms and Minimum Spanning Trees
Greedy algorithms build solutions by considering objects one at a time using simple rules, while Minimum Spanning Trees find the most cost-effective way to connect vertices in a weighted graph. Greedy algorithms can be powerful, but their correctness relies on subtle proofs and careful implementatio
6 views • 61 slides
How do I change my name on a Southwest Airlines ticket?
If a passenger's name on a ticket is misspelled and the adjustment doesn't change who they are, Southwest Airlines will correct it for free. Fees might be charged, though, if the name change entails making a major modification or giving the ticket to someone else. Southwest Airlines Name Change Poli
4 views • 5 slides
The Critical Role of Establishing Detailed Technical Requirements in Software Development
Deciding what to build and establishing detailed technical requirements are crucial steps in software system development. This process involves defining interfaces to people, machines, and other systems, and is essential for the success of the resulting system. Requirements validation criteria, cons
0 views • 47 slides
Understanding Subject-Verb Agreement in English Sentences
Learn about subject-verb agreement in English sentences with singular and plural nouns, first, second, and third person examples, uncountable nouns, and exceptions where plural nouns take singular verbs. Discover how to match the verb form to the subject noun in different scenarios to ensure grammat
2 views • 17 slides
Understanding Software Engineering: Concepts and Characteristics
Software engineering involves the application of scientific principles and methods to develop efficient, reliable software products. The need for software engineering arises due to factors like large software size, scalability, cost concerns, dynamic nature, and quality management. Good software exh
1 views • 25 slides
Managing State School Aid Application (ASSA) for Increased Accuracy
The process for the Application for State School Aid (ASSA) involves submitting data accurately by reviewing and correcting NJ SMART district enrollment reports. District administrators must ensure the correctness of preloaded data in ASSA for final certification. Important guidelines include resolv
0 views • 33 slides
Fully Homomorphic Encryption: Foundations and Applications
Fully Homomorphic Encryption (FHE) allows computations on encrypted data without decrypting, enabling secure outsourcing of computations to untrusted servers. FHE involves key generation, encryption, homomorphic evaluation, and decryption processes. It ensures correctness, security, and compactness
0 views • 31 slides
Understanding Dimensional Analysis in Physics
Dimensional analysis in physics involves defining dimensions of physical quantities, determining dimensionless quantities, checking dimensional consistency of equations, converting units, and exploring the limitations and applications of dimensional analysis. By understanding dimensions and dimensio
0 views • 14 slides
Understanding Rectification of Errors in Accounting
Preparation of trial balance is essential for verifying the accuracy of accounting records, but it is not a conclusive proof of correctness. Rectification of errors is crucial for ensuring the true and fair presentation of a business's financial position. Types of errors include errors of omission,
0 views • 14 slides
Understanding Distribution Design Issues in Databases
When designing a database, decisions regarding fragmentation, correctness rules, allocation alternatives, and information requirements play a critical role in optimizing performance. Factors such as the degree of fragmentation, correctness of fragmentation, and allocation choices impact query execut
2 views • 10 slides
Understanding Departmental Audits in GST
Departmental audits in GST involve the examination of records, returns, and other documents to verify the correctness of turnover declared, taxes paid, refunds claimed, and input tax credit availed. This audit ensures compliance with the provisions of the CGST Act, 2017. Types of audits under GST in
7 views • 27 slides
Enhancing Blackboard Writing Skills for Effective Teaching
Blackboards play a crucial role in education by providing a visual aid that enhances the clarity and understanding of lessons. Maintaining neatness, correctness, and legibility in writing on the blackboard is essential. The size and alignment of letters, highlighting main points, and creating a brie
0 views • 13 slides
Introduction to Real-Time Systems and Real-Time OSes
Real-time systems are defined by the critical nature of timely results, where correctness depends not just on computation but also on when results are produced. Characteristics include timing constraints, deadlines, and different types of tasks categorized based on timing patterns. Understanding sof
0 views • 21 slides
Livestock Evaluation and Cattle Market Priorities
In this visual guide, various aspects of livestock evaluation, focusing on cattle breeding, market priorities, muscle indicators, body parts of a cow, finish indicators, structural evaluation, rib and feeding ability assessment, and balance along with eye appeal considerations are discussed in detai
1 views • 65 slides
Understanding the Use of Brackets in Writing
Brackets serve various functions in writing, such as clarifying quotations, indicating capitalization changes, avoiding confusion in nested parentheses, and adding additional information to direct quotes. They are distinct from parentheses in usage and play a crucial role in maintaining grammatical
0 views • 8 slides
Building Diverse Subjects in Dewey Decimal System
This guide provides a detailed process for adding new topics to the Dewey Decimal System, illustrated with examples such as high explosives, scuba diving, and public speaking for politicians. Users are guided on finding starting numbers, adding instructions, verifying correctness, and contributing t
1 views • 18 slides
Understanding Gale-Shapley Algorithm for Stable Matchings
Exploring the Gale-Shapley Algorithm, this content dives into the process of generating stable matchings, analyzing efficiency, and proving its correctness through claims. Concepts such as perfect matching, blocking pairs, and proof by contradiction are elucidated to showcase the algorithm's reliabi
0 views • 29 slides
Secure Multiparty Computation: Enhancing Privacy in Data Sharing
Secure multiparty computation (SMC) enables parties with private inputs to compute joint functions without revealing individual data, ensuring privacy and correctness. This involves computations on encrypted data using techniques like homomorphic encryption for scenarios like e-voting. SMC serves as
2 views • 27 slides
Understanding Signature Schemes in Cryptography
This content delves into various aspects of signature schemes, focusing on lattice signature schemes, digital signature schemes, Fiat-Shamir signature schemes, and the main idea behind signature schemes. It explores the concepts of correctness and security in digital signatures, the relevance of tra
0 views • 68 slides
Understanding Unlabeled Certificates in Decision Tree Model
Dive into the concept of unlabeled certificates in the decision tree model, exploring their significance in minimizing queries to adjacency matrices for graph properties. Learn about the difference between labeled and unlabeled certificates, their relevance in invariant functions, and the complexiti
1 views • 31 slides
Memory Fence Synthesis and Algorithm Verification
Abstract interpretation is utilized for sequential consistency in memory fence placement. The correctness of algorithms, such as Dekker's Algorithm, is verified by synthesizing minimal fence placements. The goal is to use existing tools to ensure the mutual exclusion of critical sections effectively
0 views • 32 slides
DRFx: A Simple and Efficient Memory Model for Concurrent Programming Languages
State-of-the-art memory model DRFx provides a solution for relaxed data race detection, addressing deficiencies of previous models like DRF0. It ensures safety, debuggability, and compiler correctness while permitting optimizations and halting programs before non-sequential consistency behavior.
3 views • 14 slides
Understanding Data Races in Software Development
The content discusses the challenges posed by data races in software development, particularly in C++ and Java programs. Data races can lead to unsafe software, complicate language specifications, and make it challenging to ensure correctness in concurrent executions. Catch-Fire Semantics in C++ tre
0 views • 90 slides
Understanding Verification Methods in Spring 2022 Tufts University Lectures
Explore the lectures by Joel Grodstein and Scott Taylor at Tufts University focusing on verification methods, including self-checking tests, cycle-by-cycle comparison, and the importance of getting the correct data and timing. The lectures discuss the challenges of ensuring correctness in designs an
0 views • 54 slides
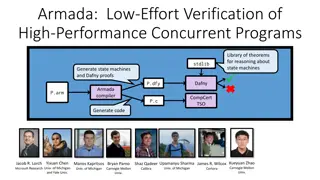
Armada: Low-Effort Verification of High-Performance Concurrent Programs
Armada is a library that enables developers to write high-performance concurrent code with flexibility. It supports automated proof generation for reasoning about state machines and synchronization mechanisms. The tool reduces the proof burden by using a weak-consistency memory model and provides gu
0 views • 17 slides
Software Bugs and Formal Verification in Critical Systems
Software bugs have caused catastrophic events like radiation overdoses and rocket explosions, emphasizing the importance of formal verification in ensuring software correctness. Formal verification uses mathematical models to prove software correctness, offering higher assurance, especially in safet
1 views • 26 slides
Automated and Modular Refinement Reasoning for Concurrent Programs
This research explores automated modular refinement reasoning for concurrent programs, focusing on safety and correctness in operating systems and applications. Projects like Verve and Ironclad aim to achieve end-to-end security through formal verification tools and small trusted computing bases. Th
1 views • 12 slides
Homomorphic Encryption Overview
Homomorphic encryption allows computation on encrypted data without revealing the underlying information. It enables secure delegation of data processing to a server while maintaining privacy. The process involves key generation, encryption, decryption, and evaluation of functions on encrypted data.
0 views • 40 slides
Wander Join: Online Aggregation via Random Walks in Database Workloads
Wander Join is a technique for online aggregation using random walks, addressing challenges in efficiency and correctness in both transactional and analytical database workloads. It allows for complex analytical queries such as TPC-H queries and provides insights into revenue loss due to returned or
0 views • 27 slides
Reconciling Assets Without Losing Your Mind
Learn about the process overview, asset reconciliation, common problems, reconciliation overview, ways to reconcile assets, DIST_LN table entries, how to ensure DIST_LN correctness, and queries related to asset reconciliation.
0 views • 47 slides
Dewey Decimal System Number Building Process
Discover the systematic process of building Dewey Decimal System numbers for music categories. Follow step-by-step guidance, including finding starting numbers, adding instructions, navigating through the system, verifying correctness, and contributing to Dewey Editors.
0 views • 8 slides
Efficient Specification Mining for Trustworthy Software Development
Explore the approach of utilizing code trustworthiness measurements to mine specifications with minimal false positives. Understand the significance of specifications in software projects and how they contribute to debugging, testing, maintenance, refactoring, and documentation. The focus is on gene
0 views • 49 slides
The Intriguing Relationship Between Language and Thought
Explore the fascinating connection between language and thought, delving into questions like whether one shapes the other, the impact of political correctness on our thinking, early experiments on language and cognition, word-finding difficulties, and differing perceptions of the world across langua
0 views • 44 slides
Comprehensive Guide to Show Goat Management and Care
Explore essential aspects of show goat management, covering topics such as facilities and equipment requirements, selection criteria, nutrition guidelines, and more. Learn about creating suitable pens, choosing the right equipment, selecting show-ready goats, providing adequate nutrition, and ensuri
0 views • 14 slides
Understanding Greedy Algorithms in Algorithm Analysis
Greedy algorithms are a simpler approach compared to dynamic programming, focusing on making locally optimal choices in order to achieve a globally optimal solution. While not always yielding the best solution, greedy algorithms can provide optimal solutions for problems with specific characteristic
1 views • 23 slides
Understanding Continuity Analysis of Programs
This content delves into the concept of continuity analysis in programs, focusing on aspects like uncertainty, robustness, and infinitesimal changes in inputs and outputs. It explores the implications of handling uncertainty robustly, the significance of correctness in uncertain environments, and th
0 views • 17 slides
Understanding Durability and Integrity in Data Storage Systems
Durability and integrity are crucial aspects of data storage systems. Durability ensures data survives faults like crashes and power loss, while integrity ensures data correctness in the face of faults. Disk data is durable due to surviving power loss, and has integrity through explicit and complex
0 views • 24 slides
Differential Assertion Checking and Relative Correctness in Software Verification
Differential assertion checking compares two similar programs to identify errors, while relative correctness ensures all assertions pass, highlighting failed assertions. The content discusses the challenges and benefits of these techniques in software verification, with examples of correct and buggy
0 views • 17 slides
Verifying Functional Correctness in Conflict-Free Replicated Data Types
Explore the significance of verifying functional correctness in Conflict-Free Replicated Data Types (CRDTs), focusing on ensuring data consistency and program logic for clients. Learn about the importance of Strong Eventual Consistency (SEC) and the necessity of separate verification with atomic spe
0 views • 33 slides
Interactive Theorem Provers: Ensuring Correctness in Programming
Explore the world of Interactive Theorem Provers, where you can write definitions, proofs, and automatically validate the correctness of your code. Learn about writing definitions in Coq, inductive definitions, and completing exercises to solidify your understanding.
0 views • 10 slides