Update on SWAG Protocols and New NICE TA Progress Report
Kate Gregory leads the SWAG Protocols update for March 2024, with advancements in new protocols and NICE TA updates. A comparison of activities from Oct 2023 to Mar 2024 shows progress in issuing, reviewing, and drafting protocols. The latest NICE TA additions include treatments for advanced cancers
5 views • 13 slides
Mastering Business Writing Skills: A Comprehensive Guide
Understanding the essence of business communication, types of communication, essentials of effective communication, smart communication tips, and communication across cultures is vital for professional success. Explore verbal, written, and non-verbal communication methods to enhance your communicati
0 views • 47 slides
Emergency Communication Volunteer Training Overview
Introduction to Emergency Communication course covers a wide range of topics including net operations, net types, example net formats, net missions, and more. Participants will learn about the importance of structured communication networks during emergencies and disaster situations. The training em
1 views • 15 slides
Understanding Consistency Protocols in Distributed Systems
Today's lecture covers consistency protocols in distributed systems, focusing on primary-based protocols and replicated-write protocols. These protocols play a crucial role in ensuring consistency across multiple replicas. One example discussed is the Remote-Write Protocol, which enforces strict con
0 views • 35 slides
Understanding Communication and Sign Language
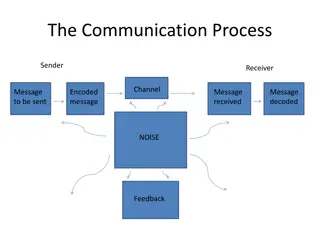
Communication is the vital process of exchanging information, ideas, and emotions through various channels such as speech, signals, and writing. This includes verbal and non-verbal communication, where sign language plays a crucial role. Effective communication depends on the sender, message, channe
1 views • 31 slides
Enhancing Zoonotic Disease Risk Communication in Public Health Emergencies
Explore the significance of adopting a One Health approach to zoonotic disease risk assessment and communication in the context of emergency health situations. The session emphasizes core capacities required by the International Health Regulations (IHR) 2005, effective risk communication processes,
2 views • 13 slides
Effective Communication Skills for Healthcare Professionals
Enhance your communication skills with the Accelerated Preceptorship Communication Session by Desiree Cox. Learn the importance of effective communication, different communication preferences, communication dynamics, non-verbal communication, listening skills, and more. Understand the communication
2 views • 28 slides
Comparison of SPI and I2C Communication in Embedded Systems
SPI and I2C are two common communication protocols used in embedded systems. SPI offers fast and easy point-to-point connections with no addressing needed, while I2C allows connecting multiple peripherals with just two wires. SPI has pros such as fast data transfer but cons like complexity with mult
1 views • 17 slides
Understanding Mobile Communication and Networks in Physics
Utilizing mobile phones for communication has become essential in modern society. This article delves into the technology behind mobile communication, including network infrastructure, codes associated with mobile phones, and communication protocols. Explore how mobile devices connect wirelessly and
6 views • 19 slides
Understanding Emergency Conditions in ERCOT Protocols
ERCOT has defined various levels and communication protocols for Emergency Conditions within the electrical grid system. This includes Emergency Notices, Energy Emergency Alerts, operating plans, outage coordination, and requirements related to voltage support for ensuring system safety and reliabil
6 views • 18 slides
Understanding Computer Communication Networks at Anjuman College
This course focuses on computer communication networks at Anjuman College of Engineering and Technology in Tirupati, covering topics such as basic concepts, network layers, IP addressing, hardware aspects, LAN standards, security, and administration. Students will learn about theoretical and practic
0 views • 72 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Effective Communication Strategies in Business Environments
Explore the various aspects of communication processes within organizations, including sender-receiver dynamics, communication channels, small group networks, upward and downward communication methods, business communication tools, information richness of channels, email and voice mail etiquette, an
0 views • 21 slides
Understanding Internet Transport Layer Services and Protocols
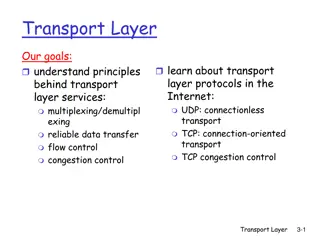
In the realm of networking, exploring the principles of transport layer services is crucial. This involves concepts like multiplexing/demultiplexing, reliable data transfer, flow control, and congestion control, which are facilitated by protocols such as UDP and TCP. The transport layer acts as a br
0 views • 56 slides
Understanding Classroom Communication and Management by Ramkrishna Chakraborty
Communication is a vital process of exchanging information, ideas, and opinions between individuals. In the educational context, effective communication is essential for achieving desired behavior patterns. This article explores the meaning, concept, and types of communication, emphasizing the impor
1 views • 19 slides
Communication Protocols for System Integration
This technical document explores various communication protocols used for system integration, focusing on mailbox communication, interprocessor communication, system communication using IPCC, and BLE communication utilizing different IPCC channels. The document delves into the features, functions, a
1 views • 6 slides
Effective Communication Skills in Business Environment
Understand the importance of communication in organizations, learn about the process of communication, main objectives, types, and patterns of communication. Explore key points such as accuracy in conveying ideas, feedback, and communication channels. Enhance your knowledge on downward, upward, and
0 views • 24 slides
Mastering Effective Communication Skills in Daily Life
Enhance your communication skills with insights from Unit 5 Communication. Learn about different types of communication, speaking skills, effective communication strategies, assertiveness, and more. Understand the nuances of verbal, nonverbal, and paralanguage communication to convey your message cl
0 views • 52 slides
Strategic Communications Planning for Educational Leadership
This comprehensive module covers essential aspects of strategic communication planning in educational leadership, focusing on proactive communication, crisis management, rumor control, audience targeting, and communication protocols. Learn from industry experts about building effective communication
0 views • 27 slides
Overview of Identification Protocols in CS255 by Dan Boneh
The lecture in CS255 covers various topics related to identification protocols, including signatures from trapdoor functions, certificates, revocation methods, certificate issuance problems, defense mechanisms like certificate transparency (CT), and moving on to protocols. The talk also explores the
0 views • 43 slides
Towards Practical Generic Zero-Knowledge Protocols
Exploring the evolution of zero-knowledge protocols, this presentation by Claudio Orlandi from Aarhus University delves into the concepts of Zero-Knowledge from Garbled Circuits, Privacy-Free Garbled Circuits, and more. The talk discusses efficient methods for proving statements and touches on relat
0 views • 29 slides
Communication Lower Bounds of Key-Agreement Protocols
Key-agreement protocols play a vital role in secure communication between parties. This document explores lower bounds of key-agreement protocols through density increment arguments, idealization of symmetric primitives, Merkle puzzles, and the impact of communication bits between Alice and Bob. Var
0 views • 10 slides
Understanding Communication Patterns in Microservices Technology
Exploring synchronous and asynchronous communication in microservices, emphasizing the client-to-service communication models, the use of HTTP verbs, and considerations for network performance and security. The content delves into the intricacies of request-response communication, remote procedure c
0 views • 27 slides
EB-5 Ethics and Integrity Protocols Training Overview
This overview provides information on the EB-5 program, Ethics and Integrity Protocols, training objectives, background information, and the EB-5 Reform and Integrity Act of 2022. It covers the purpose, guidelines, and implementation plan of the protocols to ensure transparency and accountability in
0 views • 60 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Green Protocols for Greener Arbitrations
The Green Protocols introduced by AtLAS aim to guide the arbitration community in committing to environmentally sustainable practices. These protocols suggest ways to reduce carbon emissions, energy consumption, waste generation, and unnecessary travel by utilizing electronic communication, video co
0 views • 14 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Challenges in Key Exchange Protocols
Key exchange protocols play a crucial role in ensuring secure communication. This content explores the challenges faced in designing robust key exchange mechanisms, from vulnerabilities in existing protocols like Diffie-Hellman to the complexity of implementing authentication. Despite decades of res
0 views • 51 slides
Understanding Application-layer Protocols in Computer Communication and Networks
Explore Chapter 2 of the course on Computer Communication and Networks, focusing on the application-layer protocols in the client-server paradigm, specific protocols like HTTP and SMTP, client-server architecture, peer-to-peer architecture, and addressing needs in the network application layer.
0 views • 60 slides
Understanding Application Layer Protocols in Communication Networks
Explore the fundamentals of application layer protocols in communication networks, including HTTP, DNS, FTP, and email. Learn about the client-server model, peer-to-peer communication, and the basic workings of TCP sockets. Discover the importance of message syntax, semantics, and processing rules i
0 views • 51 slides
Effective Communication Strategies for Building Relationships in Healthcare Facilities
Successful communication and documentation play a pivotal role in fostering relationships with Hospice and SNF facilities. This comprehensive guide emphasizes the significance of communication protocols, such as signing in, introducing oneself to staff, and leaving detailed notes for interdisciplina
0 views • 9 slides
Scalable Identity and Key Management for Publish-Subscribe Protocols
This research by Prashant Anantharaman from Dartmouth College focuses on scalable identity and key management for publish-subscribe protocols in Energy Delivery Systems. It discusses the architecture, goals, assumptions, and implementation results in the context of PKI vs. Macaroons protocols. The w
0 views • 37 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
Specialization in International Business Communication (SIBC)
Specialization in International Business Communication (SIBC) offered by the Department of Business Communication focuses on the critical role of communication in various business settings, emphasizing skills in language usage, communicative competence, and strategic language application. The progra
0 views • 11 slides
Understanding Network Protocols: TCP, UDP, DHCP, DNS
Explore the fundamentals of key network protocols including TCP, UDP, DHCP, and DNS. Learn about IPv4 and IPv6 addresses, IP address classes, and the roles of these protocols in the TCP/IP suite. Understand the differences between TCP and UDP in terms of connection setup and reliability. Discover th
0 views • 13 slides
Improved Merlin-Arthur Protocols for Fine-Grained Complexity Problems
The text discusses Merlin-Arthur proof systems and protocols for central problems in fine-grained complexity, particularly focusing on the time complexity, completeness, and soundness of these protocols. It also touches on recent interest in these protocols and presents new results in areas such as
0 views • 16 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides
Classical Algorithms from Quantum and Arthur-Merlin Communication Protocols
Explore the Polynomial Method in classical algorithms, focusing on Orthogonal Vectors, All-Pair-Shortest-Path, and Approximate Closest Pair. Learn how the Polynomial Method works through batch evaluation for multi-variable polynomials and fast matrix multiplication. Discover insights on low-rank dec
0 views • 13 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides