Efficient Key Recovery Attack on SIDH
Efficient key recovery attack on Supersingular Isogeny Diffie-Hellman (SIDH) protocol. It explores the vulnerability of the protocol and proposes a concrete solution. The attack leverages auxiliary points to solve the isogeny problem and reveals instances of the common secret key.
5 views • 22 slides
Unlocking the Secret to Healthy Locs: The Power of Wild Growth Hair Oil
Discover the transformative benefits of wild growth hair oil for your locs. Rich in essential nutrients, this potent formula nourishes the scalp, promotes hair growth, and strengthens locs from root to tip. Say goodbye to dryness and breakage as you unlock the secret to healthier, more vibrant locs
2 views • 2 slides
Common Issues and Solutions with Finding Office Product Key after Installation
Let's shout it from the rooftops people: The Office product key is SUPER important! It's like the golden key, the magic ticket, the secret code that unlocks everything fantastic about your Office software. Without your product key, you can say goodbye to accessing all the dazzling features of Word,
8 views • 9 slides
RPO Hiring Services The Secret to Building High-Performance Teams
RPO Hiring Services The Secret to Building High-Performance Teams
1 views • 4 slides
RPO Hiring Services The Secret to Building High-Performance Teams
RPO Hiring Services The Secret to Building High-Performance Teams
0 views • 4 slides
Traffic Analysis and Forensic Investigation Puzzle
In this scenario, Anarchy-R-Us suspects that their employee Ann is a secret agent leaking the company's secret recipe. By analyzing network traffic using Wireshark, specific questions are posed regarding Ann's activities, such as identifying her IM buddy and the contents of transferred files. The in
0 views • 21 slides
Understanding Amity School of Engineering & Technology's Common Language Infrastructure (CLI)
Explore the intricate details of Amity School of Engineering & Technology's CLI, including Common Language Infrastructure, Common Type System, and Common Data Types. Learn about the principles, specifications, and components that enable cross-language development and interoperability within the engi
2 views • 41 slides
Understanding Common Welfare in Narcotics Anonymous
Explore the concept of common welfare in Narcotics Anonymous, where prioritizing the well-being of the group over individual desires leads to unity and growth. Discover how this principle guides members to support each other and the fellowship for mutual recovery and success. Learn how Tradition Fou
0 views • 15 slides
Using Chaos to Send Secret Messages
Chaos is a fundamental concept in creating secret messaging systems using deterministic systems with sensitive initial conditions. By implementing chaotic behavior in electrical circuits known as the "Talker" and "Copycat," messages can be encoded and decoded based on chaotic attractors and synchron
0 views • 21 slides
Sociology and Common Sense: Exploring the Boundaries
Sociology and common sense intersect in intriguing ways, with common sense offering raw material for sociological theories yet lacking the validity and reliability that sociology strives for. While common sense is rooted in tradition and often status quoist, sociology challenges the taken-for-grante
2 views • 11 slides
CNF-FSS and Its Applications: PKC 2022 March 08
Explore the Background, Applications, and Summary of CNF-FSS, focusing on Function Secret Sharing, Distributed Point Function, CNF Key-Sharing, and more. Learn about the efficiency of multiparty sharing and 1-out-of-3 CNF-FSS constructions for certain classes of functions. Discover how CNF Key-Shari
1 views • 33 slides
Understanding Strata Plans and Common Property
In this informational document presented by Shawn M. Smith of Cleveland Doan LLP Strata Lawyers, you will learn about the different types of strata plans, including conventional and bare land plans, as well as the concept of common property and limited common property in strata developments. The doc
0 views • 62 slides
Understanding Bipolar Transistor Configurations for Electronic Circuits
Explore the three common configurations - Common Base, Common Emitter, and Common Collector - for Bipolar Transistors in electronic circuits. Each configuration offers unique characteristics such as voltage gain, current gain, and impedance levels, impacting the signal processing and amplification c
0 views • 27 slides
Advancing Common Business Operations Overview
Advancing Common Business Operations in November 2019 focuses on key targets and enablers such as Business Operations Strategy, Common Back Offices, Global Shared Service Centers, Common Premises, Mutual Recognition, Client Satisfaction Principles, and Costing & Pricing Principles. The project aims
0 views • 17 slides
Understanding Non-Compete Agreements: Enforceability and Requirements
Non-compete agreements are commonly used in the United States to protect businesses from competition by former employees. To be enforceable, these agreements must meet certain requirements, including independent consideration, protection of legitimate business interests, and reasonableness in scope,
0 views • 26 slides
Introduction to Cryptography: The Science of Secure Communication
Cryptography is the study of methods for sending and receiving secret messages securely. This lecture explores the application of number theory in computer science, focusing on the design of cryptosystems like public key cryptography and the RSA cryptosystem. The goal of cryptography is to ensure th
0 views • 53 slides
Understanding Public-Key Cryptography and Its Applications
Public-Key Cryptography revolutionized secure communication by introducing the concept of using separate keys for encryption and decryption. Initially explored by researchers like Diffie, Hellman, and Merkle in the 70s, it addressed key distribution challenges faced by symmetric cryptography. This m
0 views • 34 slides
Understanding .NET Framework Architecture and Common Language Runtime
This content delves into the intricacies of .NET architecture, highlighting its structure, common language runtime, and key components such as Common Type System (CTS) and Common Language System (CLS). It explains how .NET supports multiple languages, facilitates cross-language interoperability, and
0 views • 13 slides
Understanding Common Stocks: Analysis & Valuation
Common stock represents ownership in a company, entitling shareholders to assets and earnings. Shareholders have rights such as electing the board of directors and limited liability. Common stocks are valued based on future cash flows. There are two main types of stocks: common and preferred. Valuat
0 views • 17 slides
Understanding Common Cause Variation in Sampling and Process Monitoring
Common cause variation is inherent to a process and represents background noise that can obscure signals of special cause variation. Sampling plans and rational subgrouping help estimate and manage common cause variation in quantitative data. Estimating common cause involves assessing variation with
2 views • 11 slides
Understanding CMRR in Differential Amplifiers
Differential input amplifiers, including operational, instrumentation, and difference amplifiers, play a crucial role in amplifying differential signals while rejecting common-mode noise. The Common-Mode Rejection Ratio (CMRR) is a key parameter in these amplifiers, indicating their ability to suppr
0 views • 48 slides
Challenges in Managing Global Common Concerns
Managing common global concerns presents significant challenges, both domestically and internationally. The difficulty lies in taking collective action to oversee shared interests, such as sustainable management of resources, human rights enforcement, climate change mitigation, and biodiversity prot
0 views • 13 slides
Understanding Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
Understanding Public Key Cryptography in Network Security
Explore the concepts of public key cryptography, key distribution challenges, solutions to secret key schemes, and the importance of secure communication in network security. Learn about cryptology, cryptography, cryptanalysis, block ciphers, stream ciphers, and more in this informative content.
0 views • 21 slides
The Importance of Secret Prayer in the Life of Jesus
Discover how Jesus emphasized the significance of secret prayer through instances from the Scriptures where He retreated to solitary places for intimate communion with the Father. These moments of seclusion enabled Him to deepen His relationship with God, teaching us the value of private prayer for
0 views • 26 slides
Unveiling Lily Owens' Struggles in "Secret Life of Bees
Delve into Lily Owens' journey as she navigates a web of lies for self-preservation in "Secret Life of Bees" by Sue Monk Kidd. Witness Lily's desperate attempts to hide her past, protect her newfound sanctuary, and grapple with the fear of losing her newfound family.
0 views • 6 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
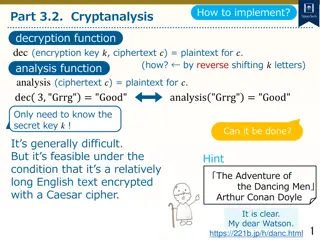
Cryptanalysis and Decryption Techniques for Caesar Cipher
Learn how to decrypt Caesar cipher text using cryptanalysis techniques by analyzing letter frequencies and determining the secret key through character analysis. Explore methods to count character frequencies and find the most common letter to decipher encrypted messages.
0 views • 11 slides
Legal Battle: Monkey.See vs. Peach.Inc - Trade Secret Dispute
Monkey.See, a startup founded by Cornelius Heston, faces a legal battle against Peach.Inc and its former engineer Simon Zaius. The lawsuit involves allegations of trade secret misappropriation, unjust enrichment, and patent infringement, leading to a complex legal dispute and substantial damages sou
0 views • 18 slides
Advanced Techniques in Secret Sharing Schemes
Explore the advancements in polynomial secret-sharing schemes and their applications in cryptography. Discover how polynomial schemes provide efficient solutions for sharing secrets among multiple parties while maintaining security. Learn about the construction of polynomial conditional disclosure p
0 views • 16 slides
Dwelling in the Secret Place: Unveiling Wisdom and Trust
Psalm 91 presents profound wisdom, guiding believers to abide in God's protection through intimate communion, concentration, and confession. Embracing the truth that God is their refuge and fortress, the psalmist transitions from a general declaration to a personal confession of trust. This sermon s
0 views • 7 slides
Guide to Common Law Process in Worker's Compensation Cases
Explore key aspects of the common law process in worker's compensation cases, including the definition of an injury and a worker, the difference between statutory and common law claims, employer's duty of care, requirements for pursuing a common law claim, and the typical course of action in such ca
0 views • 35 slides
Understanding Burglary and Arson Laws: Common Law vs. Modern Rules
Burglary and arson laws have evolved from common law principles to modern statutes. In common law, burglary involves breaking and entering a dwelling at night with intent to commit a felony, while arson requires malicious burning of another's dwelling. Modern laws may vary, eliminating some elements
0 views • 6 slides
Advances in Functional Encryption for Secure Data Handling
Explore the evolution from Cryptomania to Obfustopia through Secret-Key Functional Encryption, Public-Key Encryption, and the power of Secret-Key Functional Encryption. Discover the significance of different encryption schemes such as Public-Key Functional Encryption, Secret-Key Functional Encryptio
0 views • 36 slides
Understanding Occupiers Liability Act 1957: Visitors and Duties
The Occupiers Liability Act 1957 and 1984 cover the duty of care owed by occupiers to visitors and non-visitors. The Act defines who is considered an occupier and outlines the common duty of care owed to visitors. Learn about the key statutes, the difference in scope, and the application of the comm
0 views • 15 slides
Understanding Password-Protected Secret Sharing for Enhanced Data Security
Exploring the concept of password-protected secret sharing, this content delves into Shamir's Secret Sharing, ElGamal Public Key Encryption, and the importance of securing sensitive information with robust schemes. It highlights the challenges of offline attacks, properties of secret sharing, and th
0 views • 22 slides
Partial Key Exposure Attacks on BIKE, Rainbow, and NTRU
Explore the vulnerability of PQC candidates to partial key exposure attacks in schemes like BIKE, Rainbow, and NTRU. Learn about leakage resistance, modeling leakage, practical bounds, and secret key decoding methods. Dive into the erasure and error models, analyzing the security of secret keys in v
0 views • 19 slides
Reflections on Secret Discipleship in the Bible
Explore the concept of secret discipleship through the biblical example of Joseph of Arimathea, discussing reasons why one might choose to keep their faith hidden including fear, shame, and love of the world. The message conveyed is that true discipleship involves boldness, confession, and unashamed
0 views • 9 slides
5 Top Reasons Venue for a Birthday Party Gulmohor Banquet Makes Every Birthday Extra Special
Selecting the best venue for a birthday party that people will never forget is the secret to fulfilling a great event, a secret only known by Gulmohar Banquet Hall. A model that is distinguished for good services adaptability of space and versatility
0 views • 3 slides
The Courage of Joseph of Arimathea: A Secret Disciple of Jesus
Joseph of Arimathea, a secret disciple of Jesus, displayed courage and honor by asking for the body of Jesus after His crucifixion, despite potential fears and weaknesses. This act reveals the complexities of faith and the importance of standing up for beliefs even in difficult times.
0 views • 19 slides