Takeout Food In Orlando
Takeout food in Orlando. It's known for being live\u00adly, teeming with zest and a host of food on the\u00ad go to cater to any palate. Looking for high-end tre\u00adats, food from around the globe, or just some good old comfort food? Orlando's got you cove\u00adred. From real-deal Me\u00adxican ta
1 views • 4 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
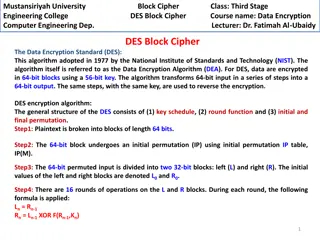
Understanding DES Block Cipher in Computer Engineering at Mustansiriyah University
Data Encryption Standard (DES) is a widely used algorithm for encrypting data in 64-bit blocks with a 56-bit key. This course at Mustansiriyah University covers the key components of DES, including the key schedule, round function, and initial/final permutation. Students learn about the encryption p
1 views • 8 slides
Evolution of Cryptography: From Ancient Techniques to Modern Security Mechanisms
Explore the evolution of cryptography from ancient techniques like the Caesar Cipher to modern security mechanisms like SSL, SSH, and IPSec. Learn how cryptography plays a crucial role in ensuring confidentiality, integrity, authentication, non-repudiation, and availability in network security. Disc
1 views • 62 slides
ADFGVX Cipher: Encryption and Decryption Techniques
Discover the ADFGVX cipher, a historical encryption method used to secure messages during World War I. Learn about Fritz Nebel and Gino Painvin, who played significant roles in its development. Explore the Polybius Square invented by Polybius in the 2nd century BC for converting letters to numbers.
0 views • 14 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
0 views • 4 slides
Optimizing MIH SA Establishment for Single Radio Handover
This presentation discusses the optimization of MIH (Media Independent Handover) Security Association (SA) establishment for single radio handover. It covers the key points and methods proposed for enhancing the communication between Mobile Node (MN) and Top Point of Service (TPoS) using cipher suit
3 views • 6 slides
Are you looking for a Tobacco Shop in Pine Cove?
Are you looking for a Tobacco Shop in Pine Cove? The Cigar Box & Lounge is your ultimate destination for premium tobacco products and a luxurious smoking experience in Fern Valley.Our cigar shop and tobacco shop offer an extensive selection of high-q
0 views • 6 slides
Understanding Small-State Noncryptographic Pseudorandom Number Generators
Explore the design and testing of small-state noncryptographic pseudorandom number generators, including definitions, rules of thumb, chisquare tests, existing and new generators, and more. Learn about block cipher encryption, hash functions, pseudorandom number generation, reversible mixing, and re
0 views • 46 slides
Understanding Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
0 views • 44 slides
Understanding Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
Understanding Encryption: Keys, Algorithms, and Applications
Encryption plays a crucial role in securing data transmission and storage. It involves using keys and algorithms to convert plaintext information into a cipher that can only be deciphered with the correct key. This article explores different encryption methods, such as private and public key encrypt
0 views • 62 slides
Key Principles in Cryptography: Kerckhoff's and Key Space
Understanding fundamental principles in cryptography, including Kerckhoff's principle, key space requirements, and the importance of secure private-key encryption. Exploring the Shift Cipher's security, key space size considerations, and the need for heuristic constructions for proving scheme securi
0 views • 51 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
0 views • 37 slides
COVE Repeater Association: Serving Amateur Operators in Central Texas
COVE Repeater Association serves Copperas Cove and operators across Coryell, Bell, Burnet, and Lampasas Counties. They offer various activities, monthly meetings, social events, and National Field Day events. The club operates VHF and UHF repeaters, with both analog and digital capabilities. Helpful
0 views • 8 slides
If you are looking for Roof cleaning in Half Moon Bay
If you are looking for Roof cleaning in Half Moon Bay, Brown's Water Blasting and Softwashing in Farm Cove, Auckland, prides itself on its exceptional customer service. Whether you need a one-off service or regular maintenance, we will work with you
0 views • 6 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
The 48 Hour Investment Process at Cove Street Capital
Explore the investment philosophy and process at Cove Street Capital through the lens of Principal and Portfolio Manager Ben Claremon. Learn about fundamental value investing, key investment questions, and why it matters to job seekers in investment management.
0 views • 52 slides
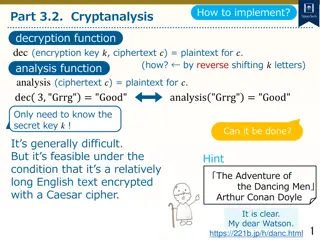
Understanding Cryptanalysis: Key Concepts and Techniques
Cryptanalysis is a fundamental aspect of cryptography that involves decoding encrypted communications and messages. This topic delves into the basic cryptographic tools, such as the Caesar cipher, and explores how encryption and decryption functions work. By understanding cryptanalysis, you can anal
0 views • 12 slides
Cryptanalysis and Decryption Techniques for Caesar Cipher
Learn how to decrypt Caesar cipher text using cryptanalysis techniques by analyzing letter frequencies and determining the secret key through character analysis. Explore methods to count character frequencies and find the most common letter to decipher encrypted messages.
0 views • 11 slides
Masons Cove Elementary School - A Community-Focused Educational Environment
Masons Cove Elementary School, situated in a rural area touching Botetourt County, Craig County, and Montgomery County, fosters a welcoming and safe school culture. With 200 students, the school boasts a supportive community, dedicated staff, and engaging learning experiences. Small group instructio
0 views • 10 slides
Cove Street Capital Podcast Season 1 Wrap-Up
Season 1 of the Cove Street Capital podcast concludes with insights from Ben Claremon, Principal & Portfolio Manager. The outro highlights key themes, company stats, recurring lessons, and a sneak peek into Season 2. Cove Street Capital emphasizes the importance of vision, resilience, and empowering
0 views • 20 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Exploration of Cryptography and Secure Communication Methods
Delve into the concepts of cryptography, data hiding, and secure communication methods such as Diffie-Hellman key exchange. Discover how Bob safely sends a ring to Alice, the use of Caesar cipher method, and the importance of mathematical principles in ensuring secure communication protocols. Learn
0 views • 22 slides
Introduction to Cryptology in Algebra 2 Classroom
Engage students in a high school Algebra 2 class by exploring cryptology concepts such as coding, hexadecimal systems, substitution ciphers, and the Vigenere cipher. The lesson plan includes activities like solving puzzles, introducing binary systems, converting to hexadecimal, and writing messages
0 views • 16 slides
Interactive Addition Practice for Missing Addends at Willow Cove Elementary
Engage students in improving their addition skills through a series of interactive slides featuring missing addends. With colorful visuals and simple equations to solve, this resource by Jim Goble provides an effective way for students to practice and master addition concepts. Perfect for young lear
0 views • 91 slides
Fun Spy Challenges for Beavers - Crack the Codes!
Dive into exciting spy missions with a group of clever beavers! Decode secret messages using various encryption techniques such as switching codes, letter grouping, Pig Pen cipher, Morse code, and Caesar cipher. Test your spy skills as you unravel each challenge to reveal hidden messages. Unleash yo
0 views • 6 slides
Luxury Villa with Stunning Sea Views and Wellness Facilities on Korcula Island
Villa Magic is a luxurious 6-room villa located in the peaceful cove of Grscica on the island of Korcula. The villa offers top-notch amenities including a heated swimming pool, sauna, wellness facilities, and beautiful terraces with sea views. With 6 bedrooms, en-suite bathrooms, 2 kitchens, a livin
0 views • 7 slides
Understanding Encryption and its Importance in Everyday Life
Encryption is a crucial process that transforms messages into secret codes, ensuring only intended recipients can decipher them. This review delves into the significance of encryption for online activities, cracking different cipher methods, and recognizing security flaws. Discover how computational
0 views • 9 slides
Cove School District Annual Meeting 2024 Information
Provide information about Cove School District's Title I-A program for parents, explaining requirements, rights of parents and guardians, curriculum, assessments, and family involvement. Details on the Title I-A program, parent/guardian rights under ESSA, program components, school data analysis, an
0 views • 12 slides
Fundamentals of Cryptography and Network Security
Explore the basics of cryptography, including classical encryption techniques, terminology definitions, types of encryption operations, cryptanalysis objectives and attacks, and the concept of cipher strength. Uncover the principles and methods behind encryption and decryption, key distinctions betw
0 views • 52 slides
Best service for Paving in Lane Cove North
Greenlands Landscaping & Property Maintenance serves the Best service for Paving in Lane Cove North. Their comprehensive range of services includes landscaping, outdoor maintenance, horticulture, weed control, pressure cleaning, gutter and drain clea
0 views • 6 slides
Best House Moves in Lane Cove North
If you want the Best House Moves in Lane Cove North, visit Big League Removals & Storage. They provide local and interstate moving services all over Australia. They are synonymous with quality residential and commercial moving solutions. With a team
1 views • 6 slides
Best Exterior Painting in Sandalfoot Cove
If you\u2019re looking for an Exterior Painting in Sandalfoot Cove, contact MM2B Projects. They are committed to delivering high-quality construction services to their clients. They specialize in various construction projects, including residential,
0 views • 6 slides
Unlock the Challenges in Cipher Cove: A STEM Adventure
Explore Cipher Cove and tackle five cryptographic challenges involving different ciphers such as Caesar Shift, Pigpen, Transposition, Substitution, and Periodic Table. Put your problem-solving skills to the test by deciphering hidden clues and codes to progress through each challenge and ultimately
0 views • 6 slides
Best Asian food in Admiral's Cove
If you\u2019re looking for Asian food in Admiral's Cove, contact Golden Pavilion Restaurant. Their menu features many mouth-watering Asian food dishes, including amazing specials like their award-winning house specialty Egg Roll, Dim Sum, and Siu Mai
0 views • 6 slides
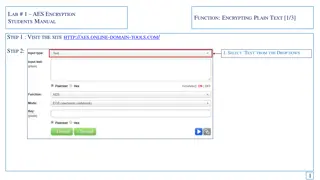
Guide to AES Encryption for Students - Encrypting and Decrypting Text
This manual provides a step-by-step guide on AES encryption for students. Learn how to encrypt plain text using a secure key, generate cipher text, and then decrypt it back to the original message. Follow the instructions on a specific website, enter your text, select encryption options, and save th
0 views • 6 slides
Best Nails in The Cove
If you\u2019re looking for a Nails in The Cove, contact The Wow Studio. Their licensed staff is professional and welcoming. Their space is comfortable, and they make sanitation one of their top priorities. They aim to make their guests feel happy and
0 views • 6 slides
Understanding Loops and ASCII Values in Python
Learn about while loops, fencepost loops, and sentinel loops in Python programming. Explore how ASCII values are assigned to characters and how to manipulate them. Practice a Caesar cipher program to encrypt messages and discover common pitfalls in loop structures. Gain insights into the importance
1 views • 22 slides