Unlocking the Secret to Healthy Locs: The Power of Wild Growth Hair Oil
Discover the transformative benefits of wild growth hair oil for your locs. Rich in essential nutrients, this potent formula nourishes the scalp, promotes hair growth, and strengthens locs from root to tip. Say goodbye to dryness and breakage as you unlock the secret to healthier, more vibrant locs
2 views • 2 slides
Phishing and Social Media Scam Protection | Scam Killnet Switch
The best online parental control tool is Scam Killnet Switch; protect your family against phishing and social media scams. Watch out for your family members while they play around on the internet. Your online interactions are kept safe by our cutting-edge technology, which recognises and stops harmf
3 views • 2 slides
מנעולן בנשר
For many years, Nesher has been considered one of the cleanest and most well-kept cities, with a variety of cultural and leisure events.\n\nAt the same time, the topic of house and car break-ins does not escape her either and once in a while you hear stories from relatives about a break-in that took
1 views • 3 slides
Understanding Variables in Research Studies
Variables in research studies play crucial roles in examining relationships and drawing conclusions. They include independent variables that influence outcomes, dependent variables affected by independent ones, moderator variables that strengthen or weaken relationships, intervening variables lying
7 views • 34 slides
Barbara Bush Middle School - Building Renovations and Upgrades
Detailed improvements at Barbara Bush Middle School include fine arts classroom enhancements, band, orchestra, choir, theater, and percussion hall renovations, exterior upgrades, interior updates, kitchen renovations, security system upgrades, and promises kept. The school has made significant renov
0 views • 20 slides
What is TNPSC (Tamil Nadu Public Service Commission)?
Tamil Nadu Public Service Commission(TNPSC) is an independent constitutional body. The Governor of Tamilnadu appoints the Members of this Commission and they can be removed only by the President of India. Per the Constitution of India, it is kept from political and executive influences. \nRead more:
3 views • 5 slides
Best Flower delivery in Killafaddy
Are you looking for the Best Flower delivery in Killafaddy? Then contact Outside Wholesale Flowers. Their commitment to quality and service has earned them the trust of their customers, and our passion for creating stunning arrangements and bouquets has kept them coming back. They are proud to be a
0 views • 6 slides
RPO Hiring Services The Secret to Building High-Performance Teams
RPO Hiring Services The Secret to Building High-Performance Teams
1 views • 4 slides
RPO Hiring Services The Secret to Building High-Performance Teams
RPO Hiring Services The Secret to Building High-Performance Teams
0 views • 4 slides
Traffic Analysis and Forensic Investigation Puzzle
In this scenario, Anarchy-R-Us suspects that their employee Ann is a secret agent leaking the company's secret recipe. By analyzing network traffic using Wireshark, specific questions are posed regarding Ann's activities, such as identifying her IM buddy and the contents of transferred files. The in
0 views • 21 slides
Guidelines on Open Meetings and Public Records for University of South Florida Search Committee
The University of South Florida Search Committee must adhere to Florida's open government laws, Chapter 286 Sunshine Law and Chapter 119 Public Records Law. The Sunshine Law requires all committee meetings to be open with reasonable notice and minutes kept. The public must be allowed to attend and o
0 views • 24 slides
Ethics in Government: Mississippi Ethics Commission Overview
The Mississippi Ethics Commission administers and enforces the Ethics in Government Law, ensuring statements of economic interest are kept, investigating violations, and advising on compliance. Members of public school boards must file statements annually, and a complaint process exists for alleged
0 views • 54 slides
Understanding Clause 44 of Tax Audit Report with CA Abhijit Kelkar
In the Tax Audit Report under the Income Tax Act, Clause 44 has become mandatory from April 2022 onwards. This clause requires detailed reporting of various expenditure and payment details related to GST-registered entities. The provision was kept on hold till March 2022 due to the pandemic, but now
0 views • 25 slides
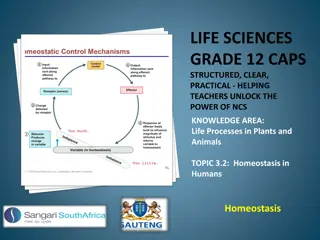
Understanding Homeostasis in Humans: The Key to Maintaining Internal Balance
Homeostasis refers to the body's ability to regulate and maintain a constant internal environment despite external changes. In humans, the tissue fluid plays a crucial role in this process, with factors like pH, water concentration, oxygen levels, temperature, and glucose content needing to be contr
0 views • 80 slides
Using Chaos to Send Secret Messages
Chaos is a fundamental concept in creating secret messaging systems using deterministic systems with sensitive initial conditions. By implementing chaotic behavior in electrical circuits known as the "Talker" and "Copycat," messages can be encoded and decoded based on chaotic attractors and synchron
0 views • 21 slides
CNF-FSS and Its Applications: PKC 2022 March 08
Explore the Background, Applications, and Summary of CNF-FSS, focusing on Function Secret Sharing, Distributed Point Function, CNF Key-Sharing, and more. Learn about the efficiency of multiparty sharing and 1-out-of-3 CNF-FSS constructions for certain classes of functions. Discover how CNF Key-Shari
1 views • 33 slides
Anne Frank: A Story of Courage and Resilience During World War II
Anne Frank, a German Jewish girl, lived in Amsterdam during World War II. Forced into hiding during the Nazi occupation, she kept a diary that later became a valuable account of Jewish life in Europe. Despite the challenges she faced, Anne's story of hope and perseverance continues to inspire genera
0 views • 10 slides
Understanding Florida's Sunshine Law
The Sunshine Law in Florida mandates that meetings of collegial bodies be open to the public, with reasonable notice given and minutes kept. Discussions between body members must occur in public meetings, not via private communication. Third-party involvement should not serve as a means to circumven
0 views • 17 slides
Winter Storm Event Recap and Recovery Efforts in New Braunfels
Throughout the winter storm event in New Braunfels, the city council and utility teams worked tirelessly to address water leaks, outages, and low water pressure issues. The Electric System documented outage statistics, and after extensive efforts, water pressure was restored system-wide. The communi
0 views • 25 slides
Are you looking for Hibachi in Bronxville?
Are you looking for Hibachi in Bronxville? Sushi Ume & Hibachi in Tuckahoe, NY's best-kept secret for gastronomic delights. Dive into the rich flavors of Japan with our expertly crafted sushi selections, and savor the warmth of traditional soup and s
1 views • 6 slides
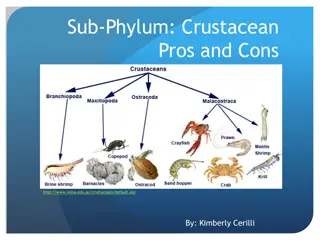
Pros and Cons of Crustaceans: A Detailed Overview
This detailed overview explores the pros and cons of various crustaceans, including Branchiopoda, Canthaxanthin, Remipedia, Cephalocarida, and Maxillopoda. From the potential to be kept as pets to symbiotic relationships and challenges like water flea infestation and venomous species, this content p
0 views • 21 slides
History and Evolution of Tamil Nadu Archives
Tamil Nadu Archives, established in 1806, has evolved over the years from Madras record office to its current form. Initially kept in desks, the growth of records led to the need for a suitable building. Through recommendations and efforts of various individuals, it transformed into the present-day
0 views • 25 slides
Safety Director 101: The Driver Qualification File
The Driver Qualification (DQ) File is a critical element in safety programs, ensuring compliance with Part 391 Qualification of Drivers in the Federal Motor Carrier Safety Regulations. DQ files must be kept up-to-date with quarterly reviews, spot checks, new hire reviews, and policy updates. Buildin
1 views • 25 slides
Understanding Public-Key Cryptography and Its Applications
Public-Key Cryptography revolutionized secure communication by introducing the concept of using separate keys for encryption and decryption. Initially explored by researchers like Diffie, Hellman, and Merkle in the 70s, it addressed key distribution challenges faced by symmetric cryptography. This m
0 views • 34 slides
The Hidden Life of St. Catherine Labouré and the Mystery of the Miraculous Medal
St. Catherine Labouré led a life of solitude that nurtured her asceticism and devotion to Mary Immaculate, ultimately leading to the revelation of the Miraculous Medal. She kept her secret for 46 years, captivating her contemporaries with endless speculation. Despite the mystery surrounding her ide
0 views • 20 slides
Exploring Catholic Social Teaching Values through Interactive Cards
Delve into the realm of Catholic Social Teaching (CST) values with a comprehensive pack of interactive cards designed to inspire social action and trusted guidance. Uncover the Church's Best Kept Secret and engage with scriptural quotes, real stories, moral dilemmas, and more to enhance understandin
0 views • 19 slides
Legal Case Study: Compensation for Breach of Promise
In this legal case study, we examine different scenarios involving breach of promise and the resulting compensation. The study covers promises kept, losses caused by breaches, and the corresponding awards for individuals involved. Various situations are analyzed, from promises kept without mitigatio
0 views • 6 slides
Understanding Public Key Cryptosystems in RSA Encryption
Public key cryptosystems, like RSA, use two keys for encryption and decryption, with one key made public and the other kept secret. This asymmetric system allows secure communication, where the encryption key (E) is used to encrypt messages into ciphertext (C), which can only be decrypted back to th
0 views • 11 slides
The Importance of Secret Prayer in the Life of Jesus
Discover how Jesus emphasized the significance of secret prayer through instances from the Scriptures where He retreated to solitary places for intimate communion with the Father. These moments of seclusion enabled Him to deepen His relationship with God, teaching us the value of private prayer for
0 views • 26 slides
Unveiling Lily Owens' Struggles in "Secret Life of Bees
Delve into Lily Owens' journey as she navigates a web of lies for self-preservation in "Secret Life of Bees" by Sue Monk Kidd. Witness Lily's desperate attempts to hide her past, protect her newfound sanctuary, and grapple with the fear of losing her newfound family.
0 views • 6 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Legal Battle: Monkey.See vs. Peach.Inc - Trade Secret Dispute
Monkey.See, a startup founded by Cornelius Heston, faces a legal battle against Peach.Inc and its former engineer Simon Zaius. The lawsuit involves allegations of trade secret misappropriation, unjust enrichment, and patent infringement, leading to a complex legal dispute and substantial damages sou
0 views • 18 slides
Advanced Techniques in Secret Sharing Schemes
Explore the advancements in polynomial secret-sharing schemes and their applications in cryptography. Discover how polynomial schemes provide efficient solutions for sharing secrets among multiple parties while maintaining security. Learn about the construction of polynomial conditional disclosure p
0 views • 16 slides
Dwelling in the Secret Place: Unveiling Wisdom and Trust
Psalm 91 presents profound wisdom, guiding believers to abide in God's protection through intimate communion, concentration, and confession. Embracing the truth that God is their refuge and fortress, the psalmist transitions from a general declaration to a personal confession of trust. This sermon s
0 views • 7 slides
Advances in Functional Encryption for Secure Data Handling
Explore the evolution from Cryptomania to Obfustopia through Secret-Key Functional Encryption, Public-Key Encryption, and the power of Secret-Key Functional Encryption. Discover the significance of different encryption schemes such as Public-Key Functional Encryption, Secret-Key Functional Encryptio
0 views • 36 slides
Understanding Password-Protected Secret Sharing for Enhanced Data Security
Exploring the concept of password-protected secret sharing, this content delves into Shamir's Secret Sharing, ElGamal Public Key Encryption, and the importance of securing sensitive information with robust schemes. It highlights the challenges of offline attacks, properties of secret sharing, and th
0 views • 22 slides
Partial Key Exposure Attacks on BIKE, Rainbow, and NTRU
Explore the vulnerability of PQC candidates to partial key exposure attacks in schemes like BIKE, Rainbow, and NTRU. Learn about leakage resistance, modeling leakage, practical bounds, and secret key decoding methods. Dive into the erasure and error models, analyzing the security of secret keys in v
0 views • 19 slides
Reflections on Secret Discipleship in the Bible
Explore the concept of secret discipleship through the biblical example of Joseph of Arimathea, discussing reasons why one might choose to keep their faith hidden including fear, shame, and love of the world. The message conveyed is that true discipleship involves boldness, confession, and unashamed
0 views • 9 slides
5 Top Reasons Venue for a Birthday Party Gulmohor Banquet Makes Every Birthday Extra Special
Selecting the best venue for a birthday party that people will never forget is the secret to fulfilling a great event, a secret only known by Gulmohar Banquet Hall. A model that is distinguished for good services adaptability of space and versatility
0 views • 3 slides
The Courage of Joseph of Arimathea: A Secret Disciple of Jesus
Joseph of Arimathea, a secret disciple of Jesus, displayed courage and honor by asking for the body of Jesus after His crucifixion, despite potential fears and weaknesses. This act reveals the complexities of faith and the importance of standing up for beliefs even in difficult times.
0 views • 19 slides