The Impact of No Code-Low Code on Startup Innovation
In the vibrant world of startups, innovation is the cornerstone of success. As these businesses aim to carve out their niches, they often face a common hurdle: the extensive resources required for traditional software development. However, the emergence of low code no code (LCNC) platforms is revolu
2 views • 12 slides
Understanding Memory Ordering in Programming
Memory ordering in programming is crucial for developers to understand, as it dictates the sequence of memory operations at different levels - source code, program order, and execution order. Compiler optimizations and reordering of memory accesses can impact how code is executed by the processor, e
1 views • 30 slides
Unit 4: Non-Examination Assessment Overview
The Unit 4 Non-Examination Assessment from 2017 focuses on working as a historian, with tasks including source evaluation and discussion of different historical interpretations. The assessment is marked out of 40 and is worth 20% of the qualification. It assesses knowledge, understanding, source ana
1 views • 14 slides
Improving Code Analysis Workflow with Jenkins, Sonar, and Gerrit
Enhance code analysis processes by analyzing source code before merging, enabling analysis in branches, and triggering Jenkins jobs. Sonar.cloud provides options to analyze branches using Maven build, while the proposal suggests using Jenkins plugin for code review. Addressing challenges with Gerrit
1 views • 12 slides
Understanding Binary Coded Decimal (BCD) and Excess-3 Code
Binary Coded Decimal (BCD) is a binary code used to represent decimal numbers, with the popular 8421 BCD code and its conversion process explained. Additionally, Excess-3 Code, another BCD code, is detailed with an example of finding its code for a given decimal number. Different BCD codes like 4221
0 views • 11 slides
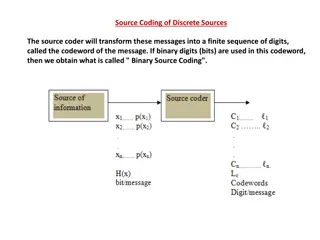
Understanding Source Coding for Discrete Sources
Source coding involves transforming messages into codewords, with considerations for minimizing code length and ensuring unique decodability. Binary source coding and efficiency are key concepts explored in this process. Check out the details and examples provided to deepen your understanding of sou
0 views • 14 slides
How Can Blockchain Technology Be Incorporated into a Bustabit Script
Blockchain technology can be incorporated into Bustabit scripts to ensure transparency by leveraging its decentralized, immutable nature. By decentralizing game logic with smart contracts, all bets and outcomes are recorded on a public, immutable led
1 views • 3 slides
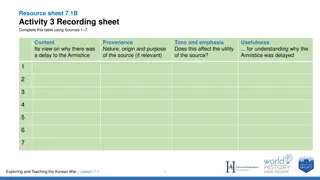
Evaluation of Source Usefulness through Multiple Criteria
In this evaluation task, you will assess the effectiveness of questions based on various criteria such as authorship, type of source, purpose, and relevance of information. By carefully analyzing the source content and rubric, you will provide an overall judgment on the source's utility while evalua
3 views • 10 slides
Download Ready-to-Use Slot Machine Android Source Code
source>>\/\/ \/slot-machine-android-source-code\n
0 views • 7 slides
Exploring Source-Routed Forwarding in SDN-Based WANs
Software-Defined Networking (SDN) in Wide Area Networks (WANs) utilizes source routing methods to address performance concerns related to network convergence time. Challenges such as latency constraints and controller placement impact performance, highlighting the need for efficient path computation
0 views • 24 slides
Customize Your Game with Slot Machine Source Code
Customize your game with slot machine source code and enhance its features. Discover how using customizable source code can help you build engaging and profitable slot machine games.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Build Your App with Slot Machine Android Source Code
Build your app with slot machine Android source code to create engaging, casino-style games. Customize features, boost user engagement, and launch your slot machine app with ease.\n\nSource>>\/\/ \/slot-machine-android-source-code\n\n
0 views • 5 slides
Laplacian Deformation in Engineering and Applied Science
Laplacian deformation is a technique used in non-rigid registration to account for shape variance and improve fitting between source and target shapes. This method involves minimizing the distance and distortion terms to achieve accurate alignment. Intrinsic and extrinsic methods are discussed, wher
0 views • 53 slides
Understanding Single-File Source Code Programs in Java 11
Explore the concept of single-file source code programs in Java 11, where the entire program is contained within a single .java file without external dependencies. Learn how to compile and run these programs both before and after Java 11, and discover the new feature of executing Java programs direc
0 views • 11 slides
Understanding the .NET Architecture Components
The .NET architecture comprises various key components such as the Common Language Specification, Code Manager, Managed Code, Unmanaged Code, and Native Code. These components play crucial roles in the development and execution of applications within the .NET framework. Managed code is executed by t
0 views • 21 slides
Find the Best Slot Machine Source Code for Your Game (1)
Find the best slot machine source code for your game development needs. Discover top-quality options to help you create engaging and successful slot machine games.\n\nSource>>\/\/medium.com\/@aistechnolabspvtltd\/find-the-best-slot-machine-source-cod
0 views • 5 slides
Challenges in Code Search: Understanding, Matching, and Retrieval
Programming can be challenging due to the lack of experience and unfamiliar libraries. Code search engines struggle with representing complex tasks, while information retrieval techniques aim to bridge the gap between source code and natural language queries. The mismatch between high-level intent a
0 views • 21 slides
Software Quality and Source Code Management Best Practices
Effective source code management is crucial for software quality assurance. This involves locking down code, baselining milestones, managing code variants, and ensuring traceability. Software Configuration Management (SCM) is key, encompassing configuration items and core concepts like creating base
0 views • 34 slides
Understanding Delay in the Korean Armistice Negotiations
Sources 1 to 4 provide insights into the reasons behind the delay in reaching an armistice during the Korean War. Source 1 discusses the POW question's impact, Source 2 presents Eisenhower's stance on peace efforts, Source 3 outlines Syngmam Rhee's opposition to a divided Korea, and Source 4 reflect
0 views • 9 slides
The Impact of Open Source Library Automation Systems
Marshall Breeding discusses the rise of open source library automation systems globally, comparing them to proprietary alternatives. He explores the adoption of open source products in the US and their coverage in international library reports, highlighting how libraries of different budgets utilize
0 views • 38 slides
Overview of Off-Site Source Recovery Program Capabilities
The Off-Site Source Recovery Program (OSRP) aids in recovering radioactive sealed sources for national security and public health. OSRP focuses on recovering TRU and non-TRU sources, with over 38,500 sources retrieved globally. Services include source registration, consultancy, and training for vari
0 views • 25 slides
Multi-Label Code Smell Detection with Hybrid Model based on Deep Learning
Code smells indicate code quality problems and the need for refactoring. This paper introduces a hybrid model for multi-label code smell detection using deep learning, achieving better results on Java projects from Github. The model extracts multi-level code representation and applies deep learning
0 views • 10 slides
Awareness and Use of Open Source Software Among Library Professionals in Bangalore City
This study presented by Podili Anjaneyulu, Kaviha B, Sreya Gopinath, and K.G. Jayarama Naik from Bangalore University focuses on identifying the awareness and usage of open source software among library professionals in Bangalore. The study explores different open source software available for libra
0 views • 18 slides
Why Slot Machine Source Code is Key to Fast-Track Game Development
Discover why slot machine source code is essential for fast-tracking game development. Learn how slot machine scripts, PHP slot machine source code, and online casino script full source code free can save time and boost efficiency.\n\nSource>>\/\/ \/
0 views • 4 slides
Understanding Fund-Source Pairings in ConnectCarolina Chartfields
Explore the Fund-Source pairings in the new ConnectCarolina chartfield structure. Learn how to avoid errors by correctly matching Funds and Sources, and understand the interaction between Fund, Source, and Department. Gain insight into the major fund groups and their specific Source ranges for effic
0 views • 17 slides
OpenACC Compiler for CUDA: A Source-to-Source Implementation
An open-source OpenACC compiler designed for NVIDIA GPUs using a source-to-source approach allows for detailed machine-specific optimizations through the mature CUDA compiler. The compiler targets C as the language and leverages the CUDA API, facilitating the generation of executable files.
0 views • 28 slides
PHP Slot Machine Source Code_ Developing High-Performance Slot Games
Discover how to develop high-performance slot games using PHP slot machine source code, including key features, algorithms, and security. Optimize your slot machine script today.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides
Unleash the Power of JavaScript Slot Machine Code for Your Online Casino (1)
Learn how to create captivating online slot machines with JavaScript Slot Machine Code, Casino game code, Casino game HTML code, HTML5 casino games source code, Slot machine JavaScript for your platform.\n\nKnow more>>\/\/ \/javascript-slot-machine-c
0 views • 4 slides
Create Profitable Casino Games with Expert Slot Machine Source Code
Develop successful games with Slot Machine Source Code, php slot machine source code, slot game script, and slot machine script for gaming industries and businesses.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 3 slides
Slot Machine Android Source Code_ Create Your Casino App Today
Discover Slot Machine Android Source Code and develop engaging slot games for Android phones. Start building your casino app with our tips for slot machine Android development.\n\nSource>>\/\/ \/slot-machine-android-source-code\n
0 views • 4 slides
Boost Your Game’s Success with Our Reliable Slot Machine Source Code
Discover premium Slot Machine Source Code to build engaging games. Explore reliable source code slot machine options for ultimate success.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides
Android Source Code for Slot Machines_ Build a Casino Game App in No Time
Discover how Slot Machine Android Source Code simplifies developing slot games for Android phones. Create a winning Android Slot Machine app today!\n\nSource>>\/\/ \/slot-machine-android-source-code\n\n
0 views • 4 slides
Maximize Efficiency_ How Slot Machine Source Code Makes Updates a Breeze
Simplify updates and customization with slot machine source code. Perfect for casino slot game source code, slot game script, and iGaming innovation. Contact AIS Technolabs.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Plumbing Code Appeals and Interpretations Overview
This document provides information on the agenda, upcoming professional development events, Building Code Appeal Board, Appeal Board decisions, Code Interpretation Committee, code interpretations, and final thoughts related to plumbing code appeals and interpretations. It covers the appeal process,
0 views • 8 slides
Unraveling the Mystery of Slot Machine Source Code_ A Developer’s Guide
Learn the intricacies of slot machine source code to develop captivating games. Explore source code slot machine insights with this comprehensive guide.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides
Powerful Slot Machine Source Code for Tailored Casino Games_ AIS Technolabs
Discover powerful slot machine source code, slot machine script, and slot machine code for customizable casino games. Enhance your gaming platform with AIS Technolabs.\n\nSOURCE>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Build Engaging Slot Games with Ready-to-Use Code and Assets
\nLearn to build slot games with slot machine source code, ready-to-use assets, and customizable tools. Discover how to create engaging slot games easily.\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 5 slides
Slot Machine Android Source Code_ The Ultimate Tool for Building a Successful Mobile Slot Game
\nDiscover how Slot Machine Android Source Code can help you create the best android slot machine games. Ideal for developers, startups, and enthusiasts.\n\nSource>>\/\/ \/slot-machine-android-source-code\n
0 views • 4 slides
Unlock the Power of Slot Machine Android Source Code to Build Stunning Android Games
Discover the power of Slot Machine Android Source Code to create engaging slot machine android games and build the best android slot machine apps.\n\nSource>>\/\/ \/slot-machine-android-source-code\n
0 views • 4 slides
Fully Customize Your Slot Machine Game Using Our Robust Source Code
Discover how to fully customize your slot machine game with robust slot machine source code, slot scripts, and tools for the best online slots. Contact us!\n\nSource>>\/\/ \/slot-machine-source-code\n
0 views • 4 slides