Computer Peripherals and Interfacing
Computer peripherals are external devices that enhance the functionality of a computer. They include input devices like keyboards and mice, output devices like printers and monitors, and storage devices like hard disk drives and solid-state drives. Interfacing circuits connect these peripherals to t
1 views • 6 slides
Ascon: The Lightweight Cryptography Standard for IoT
The November 2023 document IEEE 802.11-23/2069r2 discusses the importance of secure data storage and communication in IoT devices due to the increasing number of connected devices and potential security threats. It introduces Ascon as a lightweight cryptography standard selected by NIST for protecti
0 views • 26 slides
Lightweight Cryptography Standard for IoT - November 2023 IEEE Presentation
IEEE 802.11-23/2069r1 presents Ascon as a lightweight cryptography standard for IoT devices. With the increasing number of connected devices, protecting data on IoT devices becomes crucial. NIST selects Ascon to safeguard small devices, offering authenticated encryption and hashing efficiently. Asco
2 views • 26 slides
Understanding Network Devices and Connectivity
Network devices play a crucial role in connecting computers and printers to networks, facilitating fast and secure data transfer. These devices, such as network interface cards and WiFi cards, help devices communicate effectively on the same or different networks. MAC addresses uniquely identify dev
6 views • 31 slides
Real Time Location Systems Market to be Worth $36.6 Billion by 2030
Meticulous Research\u00ae\u2014a leading global market research company, published a research report titled, \u2018Real Time Location Systems Market by Offering (Hardware, Software, Services), Technology (RFID, BLE, UWB, NB-IoT), Deployment, Location, Application (Asset Tracking, Sensing & Monitorin
1 views • 4 slides
The Future of Healthcare: BLE App Development for Remote Patient Monitoring
As a leading provider of BLE app development solutions in Ahmedabad, Theta Technolabs is committed to pushing the boundaries of innovation and excellence in healthcare technology. With its expertise in developing robust, user-friendly apps and its focus on meeting the unique needs of the healthcare
2 views • 4 slides
Understanding Bluetooth Low Energy Addresses in IEEE 802.11-21/1535r0
The document explores the features of resolvable addresses in Bluetooth Low Energy (BLE) within the IEEE 802.11-21/1535r0 standard. It discusses the two types of addresses in BLE, Public and Random, and their usage. The emphasis is on Random addresses due to their popularity and privacy features. Th
2 views • 11 slides
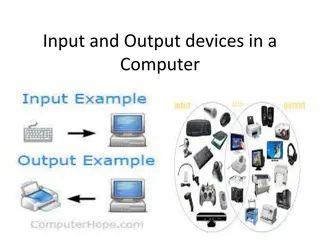
Understanding Input and Output Devices in Computing
In computing, input and output devices play a crucial role in enabling communication between users and computers. Input devices are used to enter data into a computer, while output devices display or provide the results of processed information. Common input devices include keyboards, mice, and joys
0 views • 17 slides
Understanding Basic Input/Output Operations in Computer Organization
Basic Input/Output Operations are essential functions in computer systems that involve transferring data between processors and external devices like keyboards and displays. This task requires synchronization mechanisms due to differences in processing speeds. The process involves reading characters
0 views • 11 slides
Understanding Electronic Components and Input/Output Devices
Explore the world of electronic components, input devices, and output devices through energy changes and symbol representations. Learn about LEDs, resistors, and energy conversions in a hands-on manner. Discover the role of various devices like microphones, solar cells, loudspeakers, and diodes in c
0 views • 24 slides
Understanding Computer Peripheral Devices: Definition, Examples, and Types
Learn about computer peripheral devices, which enhance a computer system's functionality. Examples include mice, keyboards, monitors, printers, and scanners. These devices can be categorized into input, output, and storage devices, each serving a specific purpose to expand the capabilities of your c
2 views • 13 slides
Understanding Programmable Logic Devices (PLD) in Digital Electronics
Programmable Logic Devices (PLDs) are versatile electronic components used to create reconfigurable digital circuits, distinct from fixed-function integrated circuits. PLDs require programming before use, enabling customization for specific functions. This article explores PLDs, digital electronic s
0 views • 10 slides
Automotive Grade 10 Joining Methods: Locking Devices Overview
Automotive Grade 10 explores joining methods using locking devices to prevent nuts from loosening due to movement and vibration. Friction-locking devices include lock nuts, stiff nuts, and special washers. Positive-locking devices tighten nuts securely with slotted nuts, crowned nuts, tab washers, a
1 views • 7 slides
STM32WB BLE SW Application Sequencer Architecture Overview
The STM32WB BLE SW Application Sequencer is a specialized framework that optimizes while loop bare-metal implementations to avoid race conditions, especially in low power modes. It is not intended to compete with standard operating systems but rather with bare-metal implementations. The sequencer al
2 views • 14 slides
Understanding Input and Output Devices in a Computer
Input devices play a crucial role in sending data to a computer, allowing users to communicate instructions for processing, display, storage, and transmission. Key input devices include keyboards and mice, each serving specific functions and enhancing data collection and accuracy. Discover the advan
0 views • 17 slides
Perceptions of Medical Students on Point-of-Care Ultrasound Devices
This study evaluates medical students' perceptions of SonoSite Edge II and Butterfly iQ ultrasound devices for enhancing learning experiences in ultrasound and medicine. The research involved first-year medical students using both devices and providing feedback through pre- and post-session surveys.
3 views • 10 slides
Guide to Creating Access from Wired to Wireless Devices Using Airborne AP Ethernet Bridge
Explore a comprehensive guide on setting up access from wired to wireless devices using Airborne AP Ethernet Role Bridge. Learn how to connect a PLC and a wireless laptop to the same network, configure settings for both devices, and successfully ping between the devices. Follow step-by-step instruct
2 views • 7 slides
Understanding BLE Security in EECS 582 - Spring 2015
Delve into the realm of Bluetooth Low Energy (BLE) security as covered in EECS 582 during the Spring of 2015. Explore topics including BLE refresher, attacks, improvements, authentication, and privacy. Gain insights into the BLE layers, connection establishment, encryption methods, and more to enhan
0 views • 16 slides
Understanding Computer Hardware: Key Input Devices and Pointing Devices
Explore essential computer hardware components such as keyboards, mice, and pointing devices. Learn about the different types of keyboards including ergonomic and laser keyboards, as well as various mouse types like wireless, cabled, and optical mice. Discover how pointing devices like touch screens
0 views • 18 slides
Overview of Computer Input and Output Devices
Input devices of a computer system consist of external components like keyboard, mouse, light pen, joystick, scanner, microphone, and more, that provide information and instructions to the computer. On the other hand, output devices transfer information from the computer's CPU to the user through de
0 views • 11 slides
Understanding Input and Output Devices in Computers
Input devices like keyboards, mice, joysticks, light pens, scanners, and more play a crucial role in interacting with computers. This chapter explores the functions and features of various input devices used in computing, such as keyboards for data input, mice for cursor control, and joysticks for C
0 views • 12 slides
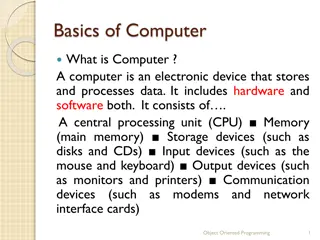
Understanding Basics of Computer Systems
A computer is an electronic device that stores and processes data using hardware and software components. It consists of a CPU, memory, storage devices, input/output devices, and communication devices. The CPU includes a Control Unit and Arithmetic Logic Unit, and the memory stores data in bytes. St
0 views • 57 slides
Intro to Poetic Devices in "The Raven
Explore the use of poetic devices in Edgar Allan Poe's "The Raven" with a focus on end rhyme, internal rhyme, rhyme scheme, personification, and more. Learn to identify and analyze these devices as they influence the understanding and impact of the poem's stanzas. Engage in a practical exercise to a
0 views • 43 slides
Ultra Low Power Features for Active Devices in IEEE 802.11-24
This presentation discusses ultra low power features for active devices in IEEE 802.11-24, focusing on solutions for RF-harvesting AMP-only and AMP-assisted devices. It covers capabilities requirements, device solutions, and implementations such as constant envelope waveform, control and sensing cap
0 views • 14 slides
Understanding the Role of NCUTCD in Traffic Control Management
The National Committee on Uniform Traffic Control Devices (NCUTCD) plays a crucial role in setting standards and guidelines for traffic control devices. Established in 1980, it advises the Federal Highway Administration (FHWA) on the Manual on Uniform Traffic Control Devices (MUTCD), facilitating re
0 views • 34 slides
Security Concerns and Future Challenges of Internet Connected Devices in Budva, Montenegro
With the increasing number of Internet-connected devices and IoT, the security concerns are escalating. In the past, communication was restricted to servers and terminals, but now everyone is connected globally. The future poses even greater risks with IoT becoming prevalent. Reasons for concern inc
0 views • 17 slides
STM32WB BLE Secure Connections Overview
This detailed content provides insights into the secure connections in STM32WB BLE devices, covering aspects such as BLE security methods, encryption techniques, pairing processes, key distribution, and security modes and levels. It emphasizes the use of Long Term Keys (LTK), Diffie-Hellman key exch
0 views • 12 slides
Energy Harvesting Operation Procedures for AMP Devices in WLAN
This submission delves into the operation procedures of AMP devices in WLAN setups, focusing on energy harvesting techniques for various power sources like solar and RF. It details the operation procedures for devices with and without energy storage, highlighting configurations for day and night use
0 views • 8 slides
Exploring Rhetorical and Stylistic Devices in Speeches
Delve into the world of rhetorical and stylistic devices used in speeches, such as repetition, imagery, and devices of comparison like simile, metaphor, analogy, and juxtaposition. Understand how these devices enhance the impact and effectiveness of communication, with examples ranging from politica
0 views • 10 slides
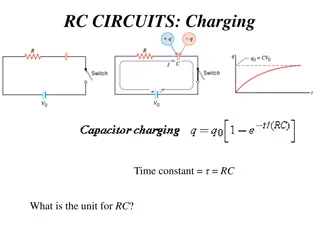
Applications of RC Circuits in Electronics and Biomedical Devices
RC circuits play a crucial role in various applications such as camera flashes, timing devices in automobiles, and heart pacemakers. These circuits involve charging and discharging a capacitor through a resistor, controlling voltage pulses for precise timing. In devices like camera flashes, the flas
0 views • 7 slides
Holistic Approach to IoT Communication: Connecting to BLE Devices
Explore a comprehensive approach to problem-based education in ICT through international collaboration under pandemic conditions. Discover the process of connecting to Bluetooth Low Energy (BLE) devices using devices like FiPy with ESP32 Pycom, and iNode Care Sensor PHT. Learn about Bluetooth method
0 views • 17 slides
Wireless Office Docking Model for Multiple Devices
This document outlines a usage model for office docking involving wireless connections between mobile devices and various peripheral devices such as monitors, hard drives, printers, and more. It describes scenarios for single and multiple devices in both home and office settings, emphasizing the nee
0 views • 5 slides
Efficient Buffer Replacement Algorithms for NAND Flash Storage Devices
NAND flash storage devices are increasingly replacing traditional HDDs in modern computing systems due to their technical advantages such as low latency, low power consumption, and shock resistance. However, as flash density increases, challenges like decreased lifetimes due to random writes persist
0 views • 20 slides
Adapting Linear Hashing for Flash Memory Constrained Embedded Devices
This research explores the adaptation of linear hashing for improved data handling on flash memory-constrained embedded devices. Motivated by the increasing data collection by IoT devices, the study focuses on implementing database structures like a linear hash table for efficient data processing. T
0 views • 67 slides
Understanding I/O Systems and Devices
I/O systems and devices play a crucial role in computer operations. They can be categorized into block devices and character devices based on their functionalities. Block devices store information in fixed-size blocks with addresses, while character devices handle character streams. Some devices, li
0 views • 19 slides
Embedded Systems: Introduction to Input and Output Devices
This material explores the essential concepts related to input and output (I/O) devices in embedded systems. It covers examples of I/O devices, such as keyboards, mice, and disk drives, along with the digital interface between these devices and the CPU. Specific focus is given to the 8251 UART as an
0 views • 55 slides
Gait Device Selection for Children with Lumbar Level Myelomeningocele
This presentation discusses the considerations and choices of gait devices for children with lumbar level myelomeningocele. It covers the specific needs of pediatric patients, benefits and drawbacks of various devices, funding requirements, and clinical application through case studies. The material
0 views • 31 slides
Impact of Networked Devices on MSME Growth in Developing Countries
This study explores how access to business-relevant information through networked devices enhances internal efficiency and business growth for urban MSMEs in low and middle-income countries. It investigates the impact of ubiquitous mobile devices on MSME growth in national development, moving toward
0 views • 14 slides
Combatting Counterfeit and Substandard ICT Devices: IMEI Ecosystem & Its Role
The conference held in Geneva, Switzerland in November 2014 addressed the critical issue of combatting counterfeit and substandard ICT devices, focusing on the IMEI ecosystem and its significance in preventing the use of counterfeit devices. James Moran, Security Director at GSM Association, highlig
0 views • 12 slides
Introduction to Bluetooth Low Energy (BLE) Technology
Bluetooth Low Energy (BLE) is a wireless protocol that enables direct connections between devices such as phones and health trackers. It is a lightweight subset of classic Bluetooth, offering advantages like low power consumption and faster throughput. BLE devices typically have two roles: periphera
0 views • 19 slides