Understanding IDS/IPS: Enhancing Security with SecurityGen's Advanced Solutions
In the realm of cybersecurity, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play pivotal roles in safeguarding networks against evolving threats. SecurityGen's IDS IPS solutions are designed to monitor network traffic, detect suspicious activities, and prevent potential i
4 views • 1 slides
Buy a fake German ID card Online - geldbe.com
Buy a fake German ID card. Fake IDs are a popular purchase for many people who want to buy alcohol, visit clubs, or participate in activities for which they are not legally old enough. However, obtaining a fake ID can be challenging and people are often unsure who to turn to. Luckily, fakeidscard.co
4 views • 4 slides
Apple Peach TE5000 ELF BAR
\nThe Apple Peach TE5000 ELF BAR delivers the perfect combination of crisp apples and juicy peaches, making for a refreshing and delicious vaping experience. Enjoy the convenience of a disposable electronic vape with no need for charging or refilling. Try the Apple Peach TE5000 today and elevate you
4 views • 5 slides
Lubbock Retail Integration Task Force – LRITF
The Lubbock Retail Integration Task Force (LRITF) discussed various topics including customer choice enrollment, Winter Storm Uri securitization, distribution loss factors, and updates on duplicate addresses and various other updates. The completed action items Q&A provided insight into transitionin
0 views • 11 slides
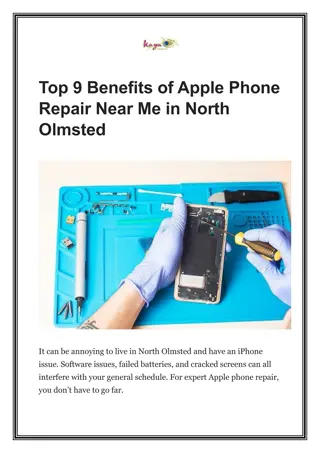
Top 9 Benefits of Apple Phone Repair Near Me in North Olmsted
Making an Apple phone repair near me in North Olmsted a priority will help you support your neighborhood and reduce your environmental effects while providing a quicker, more economical, and more individualized repair experience. Knowing about Apple phone repair near me in North Olmsted, iPhone Mend
0 views • 5 slides
Play On The Best Online Gaming Platform For Online Cricket ID. (1)
\n\nTiger exchange id is among the top providers of betting IDs in India. Here, you can discover a wide range of IDs and receive valuable betting tips. We offer multiple gaming choices including casino games and Teen Patti, hockey, cricket, football, and more. Join now at crownonlinebook for an exci
0 views • 4 slides
The Ultimate Bet Exploring the Best Online Betting IDs in India
The\u00a0best online betting ID in India\u00a0has increased a lot in recent days. India is one of the countries where passion for sports has been growing consistently over the years. The concept has further given rise to the growth of online betting. In fact, online has become one of the prime means
0 views • 4 slides
Understanding Linux User Capabilities and Namespace Management
Linux user namespaces and capabilities play a critical role in managing system security and permissions. Users and groups are assigned unique IDs, and processes are associated with the user's ID. The kernel enforces permission checks based on user IDs and group IDs, allowing root access to bypass ce
0 views • 14 slides
Understanding P&IDs and Symbols in Process Engineering
An insightful primer on P&IDs and symbols for students unfamiliar with EMEC125 and EMEC130 courses. The article delves into the definition of P&IDs as schematic diagrams illustrating the relationship between instruments, controllers, piping, and equipment. It explores the widely understood acronym "
1 views • 32 slides
Evaluation of Apple Inc.'s Business Strategies
Apple Inc., founded by Steve Jobs and Steve Wozniak in 1976, has established itself as a leader in the technology industry. This evaluation explores their business strategies, including cost leadership, product differentiation, innovation, quality focus, and brand loyalty. By focusing on design qual
0 views • 11 slides
Comprehensive Overview of the Intelligence and Development Scales - Second Edition (IDS-2)
The Intelligence and Development Scales - Second Edition (IDS-2), developed by Dr. Jane Yeomans, is a comprehensive assessment tool for individuals aged 5 to 21. It includes cognitive and general development domains, with subtests covering intelligence scales, executive functions, psychomotor skills
0 views • 25 slides
Understanding Security Onion: Network Security Monitoring Tools
Security Onion is a Linux distribution designed for network security monitoring using various tools like Full Packet Capture, Network IDS, Host IDS, and Analysis Tools. It offers capabilities for detecting and responding to security incidents effectively, making it a valuable asset for defensive net
0 views • 17 slides
Patient Safety Issues in Merging Client IDs with FHIR Specifications
Focusing on the potential patient safety risks associated with merging client IDs using FHIR specifications. The discussion highlights challenges, system behaviors, and the impacts on both demographic and health information records. It also presents a scenario illustrating problematic behaviors and
1 views • 6 slides
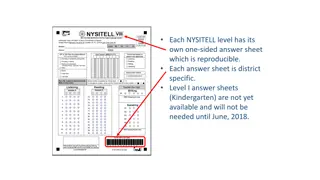
NYSITELL Testing Procedures and FAQs
The NYSITELL testing system includes district-specific answer sheets for each level, with detailed procedures for administering and scoring the tests. FAQs address common questions about student IDs, FTP site access, and the Core FTP Client installation. Learn how to submit answer sheets, handle tem
0 views • 16 slides
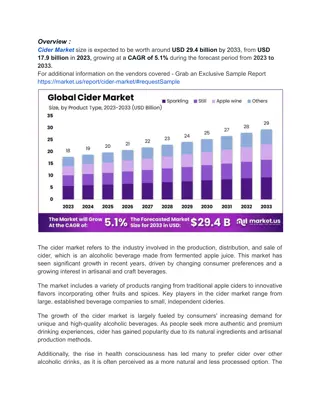
Apple-Based Ciders Maintain Dominance with Over Half of Market Share
Cider Market By Product Type (Sparkling, Still, Apple wine, and Other Product Types), By Source (Apple, Fruit flavored, Perry, and Other vegan sources), By Region and Companies - Industry Segment Outlook, Market Assessment, Competition Scenario, Tren
0 views • 4 slides
Understanding Devices and Network Security Implementation
This content discusses the installation and configuration of network components to enhance organizational security. It covers topics such as intrusion detection systems (IDS), different types of IDS approaches, passive and active responses to intrusions, and using hubs to attach network-based IDS. T
0 views • 13 slides
Unlock the Game Reddy Anna is India's Most Trusted Online Book Cricket ID Provider
Reddy Anna stands out as the premier provider of online book cricket IDs in India, delivering a service that is both reliable and user-friendly. With Reddy Anna Book, enthusiasts can easily access genuine IDs tailored for an exceptional gaming experi
1 views • 4 slides
Understanding Network Security: Hijacking, Denial of Service, and IDS
This content delves into the concepts of spying and hijacking in network security, covering topics such as eavesdropping on packets, injecting packets into streams, denial of service attacks, and defense mechanisms like firewalls and IDS. It explores low-level attacks and defenses, including ARP cac
1 views • 81 slides
In India, Cricbet99 Is The Biggest Online Gaming Site
India's Cricbet99 provider of betting IDs is one of the top in the world. Listed here are a variety of IDs and valuable betting tips. A variety of games are available, including casino games, Teen Patti, hockey, cricket, and football. Get started at
1 views • 4 slides
Guide to Grading and Rating Process for Chess Tournaments
Learn the step-by-step process of submitting tournament results for grading and rating, including generating FIDE-rating and ECF-grading files. Understand the importance of FIDE IDs, updating player information, and handling new players without FIDE IDs. Follow clear instructions on generating and h
1 views • 8 slides
Strategy for Migration of CE & ST Assessee to GSTN
This strategy outlines the process for migration of Central Excise (CE) and Service Tax (ST) assesses to the Goods and Services Tax Network (GSTN). It explains the issuance of provisional IDs, enrollment based on PAN and State, and the handling of multiple registrations under a single PAN. The proce
0 views • 48 slides
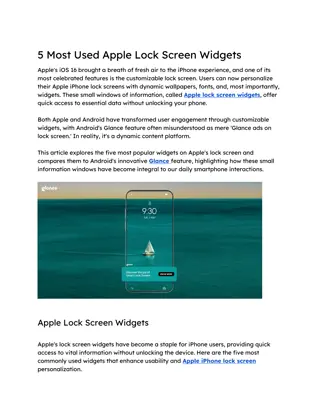
5 Most Used Apple Lock Screen Widgets
Apple's iOS 16 brought a breath of fresh air to the iPhone experience, and one of its most celebrated features is the customizable lock screen. Users can now personalize their Apple iPhone lock screens with dynamic wallpapers, fonts, and, most import
1 views • 4 slides
RMIT and Apple Partnership: Revolutionizing App Development in Australia
RMIT and Apple have joined forces to offer a groundbreaking collaboration in Australia, focusing on app development with Swift programming language. This unique partnership aims to equip students with the skills required to thrive in the flourishing app economy. The significance of the growing app e
0 views • 6 slides
Comprehensive Overview of Distributed Intrusion Detection System (DIDS)
Explore the Distributed Intrusion Detection System (DIDS) introduced by Mohammad Hossein Salehi and Kiumars Talaee. Learn about the significance, working, and different types of IDS within DIDS like HIDS, NIDS, and agent-based IDS. Understand the division, information sources, and roles of client-ba
0 views • 25 slides
Innovative Cryopreservation Techniques and Fire Blight Management in Apple Collections
The provided content discusses cryopreservation techniques for Malus and Prunus collections, focusing on bud segments and injury management. Measures to minimize fire blight in the PGRU apple collection are highlighted, including cryogenic storage of buds and repropagation on specific rootstocks. A
0 views • 8 slides
Enhancing Discovery with OCLC Work IDs
Explore the potential of using OCLC Work IDs for enhancing discovery processes in libraries. Learn about additional use cases and ideas to further develop the integration of OCLC Work IDs, including discovering other editions/formats at different institutions and digital editions in platforms like H
0 views • 28 slides
Signature-Based IDS Schemes for Heavy Vehicles
This research focuses on developing signature-based Intrusion Detection System (IDS) schemes for heavy vehicles, particularly targeting the Controller Area Network (CAN) bus. The study delves into various attack vectors and payloads that have targeted commercial vehicles over the years, proposing th
0 views • 18 slides
Understanding IDS and IPS for Network Security
Enhance the security of your network with IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) by monitoring traffic, inspecting data packets, and detecting malicious activities based on known signatures. Learn about different types like HIDS and NIDS, their functions, and tools us
0 views • 7 slides
Understanding Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are software pieces that monitor computer systems to detect unauthorized intrusions and misuse, responding by logging activity, notifying authorities, and taking appropriate countermeasures. IDS help address security challenges, aiming to find and fix serious securi
0 views • 40 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Efficient VM Introspection in KVM and Performance Comparison with Xen
Intrusion Detection Systems (IDS) play a crucial role in detecting attacks against servers, but attackers are finding ways to disable them. IDS offloading using virtual machines (VMs) can prevent compromise, providing enhanced security. VM Introspection (VMI) allows monitoring VMs from the outside,
0 views • 32 slides
Migrating Pre-Banner Hardcopy Forms into the Digital Age at Kent State University
Kent State University's Division of Information Technology presents a successful solution for migrating pre-Banner hardcopy forms into a digital format. Discover the process of creating pseudo IDs to handle document indexing without new Banner IDs. Learn about the technology used and the strategic a
0 views • 41 slides
Proposal for Network-Generated Device ID Scheme in IEEE 802.11
A scheme proposing the generation of network-assigned device identifiers for STAs in IEEE 802.11 networks is outlined. The network assigns unique IDs to devices, allowing flexibility in ID formats across different networks. STAs receive and use these IDs for tracking purposes. The process involves c
0 views • 9 slides
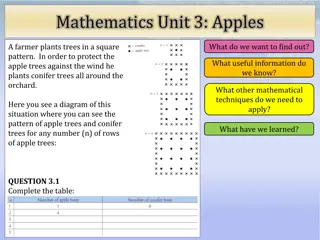
Solving the Apple Tree and Conifer Tree Pattern Puzzle
In this mathematics unit, we explore a scenario where a farmer plants trees in a square pattern, with conifer trees surrounding the apple trees for protection against the wind. The task involves completing a table to understand the pattern for different numbers of rows of apple trees. Through this e
0 views • 15 slides
Enhancing Cloud Security Through Virtual Machine Co-Migration for IDS Offloading
Explore the innovative approach of synchronized co-migration of virtual machines for offloading Intrusion Detection Systems (IDS) in Cloud environments. This method allows IaaS providers to deploy IDS without user cooperation, enabling better monitoring and security in the cloud.
0 views • 10 slides
Apple's Controversial Sweatshops in China Exposed by ABC Documentary
Apple's factories in China, particularly in Shenzhen, have come under scrutiny for their harsh working conditions and low wages. Employees work long hours performing monotonous tasks, with some earning as little as $1.12 an hour. Reports of worker suicides and forced overtime have raised concerns, l
0 views • 14 slides
In India, 99 Exch Is A Leading Provider Of Online Gaming IDs
\n99 Exch is popular in India for its online gaming IDs. Gamers use these IDs to connect, compete, and enjoy various games. The platform offers a fun and engaging experience, making it a favorite among players looking for entertainment. Get started n
4 views • 4 slides
Challenges and Solutions in Article Licensing and Library Availability Management
This collection of images depicts the current challenges faced by IDS systems administrators in managing article licensing information and library availability. The images highlight the complexities involved in maintaining e-journal databases, the manual processes required for updating licenses, and
0 views • 22 slides
The Journey of an Apple: From Tree to Lunchbox
Explore the fascinating journey of an apple from the tree to your lunchbox. From the grower to the packer, each step is crucial in ensuring that the apple reaches you fresh and ready to eat. Discover the roles of different individuals involved, including the picker, grader, forklift operator, truck
0 views • 18 slides
End-to-End IDS Support Services for Total Network Protection
We have the best IDS support services in USA, California, Delware, New York, Canada, and India. We have the expertise and experience to meet your needs. Contact us today to find out how we can help you secure your digital assets.
0 views • 2 slides