Amadeus Travel Agent Software
Travelopro implements Amadeus travel agent solutions for your Travel business with GDS and Airline API integrations. With Amadeus travel agent software, it is possible to improve the value of various business operations for both travel suppliers and users. This GDS is among the best for each type of
3 views • 15 slides
Understanding Microprocessor Architecture and Software Design
Microprocessor architecture and software design play crucial roles in the development of microprocessors. This article explores the internal features, software design types, and characteristics of Complex Instruction Set Computer (CISC) and Reduce Instruction Set Computer (RISC) architectures. It de
7 views • 73 slides
Ensuring Reliability of Deep Neural Network Architectures
This study focuses on assuring the reliability of deep neural network architectures against numerical defects, highlighting the importance of addressing issues that lead to unreliable outputs such as NaN or inf. The research emphasizes the widespread and disastrous consequences of numerical defects
0 views • 26 slides
If you are looking for Buyers Agent in McLeods Shoot
If you are looking for Buyers Agent in McLeods Shoot, Chastain Buyers Agency, is your premier choice for Real Estate Buyer\u2019s Agent and Property Buyer's Advocate services in Byron Bay. With years of industry expertise, we specialise in expert property negotiation, auction bidding, and unlocking
0 views • 6 slides
Evolution of IBM System/360 Architecture and Instruction Set Architectures
The IBM System/360 (S/360) mainframe computer system family, introduced in 1964, revolutionized computing by offering forward and backward compatibility, a unified instruction set architecture (ISA), and a balance between scientific and business efficiency. The critical elements of this architecture
0 views • 18 slides
Environmental Hazards Faced by Veterans and Agent Orange Exposure Locations
Veterans may have been exposed to a variety of environmental hazards during their military service, including Agent Orange-related diseases, Gulf War illnesses, radiation-related diseases, traumatic brain injury, and more. Agent Orange exposure locations include Vietnam, C-123 airplanes, Blue Water
1 views • 40 slides
Understanding Shared Memory Architectures and Cache Coherence
Shared memory architectures involve multiple CPUs sharing one memory with a global address space, with challenges like the cache coherence problem. This summary delves into UMA and NUMA architectures, addressing issues like memory latency and bandwidth, as well as the bus-based UMA and NUMA shared m
0 views • 27 slides
Understanding the Contract of Agency in Business Regulatory Framework
A contract of agency establishes the relationship between an agent and a principal, allowing the agent to act on behalf of the principal in dealings with third parties. Essential features include the competence of the principal, agreement between parties, intention of the agent, and free consent. Ag
0 views • 8 slides
Exploring Logical Agents and Architectures in Wumpus World
Explore the use of logical agents in the Wumpus World domain through three agent architectures: reflex agents, model-based agents, and goal-based agents. Understand how these agents operate in the challenging environment of the Wumpus World, where the task is to find the gold, return to starting pos
0 views • 21 slides
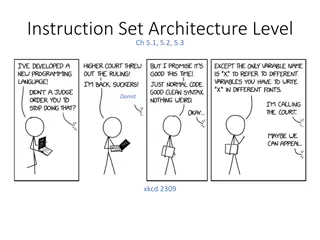
Understanding Instruction Set Architecture and Data Types in Computer Systems
In computer architecture, the Instruction Set Architecture (ISA) level is crucial in defining how a processor executes instructions. This includes the formal defining documents, memory models, registers, and various data types that can be supported. The ISA level specifies the capabilities of a proc
2 views • 13 slides
Understanding Internet Mail Architecture Components
The Internet mail architecture consists of key components including Message User Agents (MUA), Mail Submission Agent (MSA), Message Transfer Agent (MTA), Mail Delivery Agent (MDA), and Message Store (MS). These components work together to facilitate the sending, receiving, and storing of email messa
6 views • 4 slides
Contrasting RISC and CISC Architectures
Contrasting RISC (Reduced Instruction Set Computing) and CISC (Complex Instruction Set Computing) architectures, the images and descriptions elaborate on their advantages and disadvantages, with a focus on multiplying two numbers in memory using a CISC approach. CISC processors aim to complete tasks
0 views • 35 slides
Best Sellers Agent in Abingdon Green
Are you looking for the Best Sellers Agent in Abingdon Green? Then contact Robert Johnson Real Estate. They are your local, experienced real estate agent in Warner Robins, Georgia.Seeking a trusted listing agent, advisor, and guide to navigate today'
0 views • 6 slides
Understanding Shared Memory Architectures and Cache Coherence
Shared memory architectures involve multiple CPUs accessing a common memory, leading to challenges like the cache coherence problem. This article delves into different types of shared memory architectures, such as UMA and NUMA, and explores the cache coherence issue and protocols. It also highlights
2 views • 27 slides
Finesse Agent and Supervisor User Guide
Learn how to use the Finesse Agent and Supervisor interface efficiently. Discover key features such as changing agent states, handling calls, transferring calls, and accessing queue statistics. Log in with your user ID and password to start managing calls and providing exceptional customer service.
0 views • 17 slides
Variations in Computer Architectures: RISC, CISC, and ISA Explained
Delve into the realm of computer architectures with a detailed exploration of Reduced Instruction Set Computing (RISC), Complex Instruction Set Computing (CISC), and Instruction Set Architecture (ISA) variations explained by Prof. Kavita Bala and Prof. Hakim Weatherspoon at Cornell University. Explo
0 views • 55 slides
Efficient Resource Management for Multi-Agent System Execution on Parallel Architectures with OpenCL
This research focuses on efficiently managing memory and computing resources for executing multi-agent systems on parallel architectures using OpenCL. The study presents a hybrid approach involving population-level molecular virtual chemistry and individual-level virtual cells. The work enhances a p
1 views • 33 slides
Introduction to PRAM Architectures and Algorithms
This content covers Parallel Random Access Machine (PRAM) architectures, algorithms, and performance evaluation. It discusses shared memory models, PRAM processors, network models, and provides definitions related to parallel computation. Insight from experts Joseph F. JaJa and Uzi Vishkin is includ
0 views • 27 slides
NTN Indication and UE Location in 5G and IoT Architectures
Background information on the inclusion of indication of country of UE location in network messages for PLMN selection in 5G and IoT architectures. Discussions on the necessity, impact, and decisions regarding this indication, along with ongoing proposals and requirements. Consideration of factors s
0 views • 5 slides
Framework for Developing Verified Assemblers for ELF Format
This research paper discusses the importance of verified assemblers in the context of verified compilation, focusing on the development of verified assemblers for the ELF format for multiple architectures like X86, RISC-V, and ARM. The framework aims to be configurable, extensible, and general to su
0 views • 32 slides
Research Insights on Future Internet Architectures
This survey explores key research topics in designing future internet architectures, focusing on innovations, content/data-oriented paradigms, mobility challenges, cloud-computing architectures, security considerations, and experimental testbeds. The study emphasizes the need for collaborative proje
0 views • 43 slides
Understanding Agent Orange Exposure and Associated Diseases
Agent Orange was a tactical herbicide used by the U.S. military during the Vietnam War, leading to long-term health issues for exposed veterans. The VA provides free health exams and benefits for eligible veterans and their families affected by diseases like diabetes, cancer, and neurological disord
0 views • 15 slides
Exploring Instruction Level Parallel Architectures in Embedded Computer Architecture
Delve into the intricacies of Instruction Level Parallel Architectures, including topics such as Out-Of-Order execution, Hardware speculation, Branch prediction, and more. Understand the concept of Speculation in Hardware-based execution and the role of Reorder Buffer in managing instruction results
0 views • 51 slides
Kaseya Fundamentals Workshop - Agent Procedures and Variables Overview
Discover the key aspects of Agent Procedures and Variables in Kaseya Fundamentals Workshop, including Managed Variables, Global Variables, and Public Variables. Explore examples of Agent Procedures and learn about Application Deployment, Windows Registry Modification, and more. Gain insights into Pr
0 views • 23 slides
FPGA Acceleration of DNA Sequence Mapping using Multithreaded Architectures
Introduction to the use of FPGA for hardware acceleration of multithreaded architectures targeting DNA sequence mapping, implementation of FHAST tool, FM-Index string matching algorithm, and evaluation of results.
0 views • 20 slides
Advanced ORC Architectures for Waste Heat Recovery at IIT Madras
Presentation of a novel Trans-critical Regenerative Series Two-Stage Organic Rankine Cycle (TR-STORC) by researchers Anandu Surendran and Satyanarayanan Seshadri at the 5th International Seminar on ORC Power Systems in Athens. The TR-STORC layout combines supercritical evaporation in the high-pressu
0 views • 21 slides
Embedded Computer Architecture - Instruction Level Parallel Architectures Overview
This material provides an in-depth look into Instruction Level Parallel (ILP) architectures, covering topics such as hazards, out-of-order execution, branch prediction, and multiple issue architectures. It compares Single-Issue RISC with Superscalar and VLIW architectures, discussing their differenc
0 views • 49 slides
How to Organize a Faces of Agent Orange Town Hall Meeting
Set up a successful Faces of Agent Orange town hall meeting by following these steps: Contact Mokie Porter for coordination, gather a team, choose a central location with proper accommodations, select a suitable date and time, and secure speakers and moderators knowledgeable in Agent Orange. Ensure
0 views • 22 slides
Enhancing Healthcare Data Sharing with Service-Oriented Architectures
This paper explores how Service-Oriented Architectures (SOA) can be integrated with the HL7 Clinical Document Architecture to facilitate the sharing of Summary Care Records between healthcare information systems. It highlights the benefits of a federated architecture based on SOA and coding standard
0 views • 51 slides
Analysis of Transactional Memory Techniques in Multi-Core Architectures
Emerging multi-core architectures have led to the adoption of Transactional Memory (TM) as a new synchronization method. This study delves into the challenges of TM, examining the consequences of transaction aborts, the need for spare aborts, and evaluating measures to enhance transaction processing
0 views • 23 slides
Understanding OpenMP Programming on NUMA Architectures
In NUMA architectures, data placement and thread binding significantly impact application performance. OpenMP plays a crucial role in managing thread creation/termination and variable sharing in parallel regions. Programmers must consider NUMA architecture when optimizing for performance. This invol
0 views • 18 slides
Understanding Computer Systems and Operating System Architectures
An exploration of computer systems and operating system architectures, covering topics such as CPU modes, monolithic and layered architectures, microkernel architecture, Linux and Windows kernel architectures, as well as devices and their terminology. The content delves into the roles, structures, a
0 views • 57 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Energy-Efficient Query Processing on Embedded CPU-GPU Architectures
This study explores the energy efficiency of query processing on embedded CPU-GPU architectures, focusing on the utilization of embedded GPUs and the potential for co-processing with CPUs. The research evaluates the performance and power consumption of different processing approaches, considering th
0 views • 22 slides
Programming Agents with JADE for Multi-Agent Systems Overview
This overview delves into the setup of JADE framework for developing multi-agent systems. It covers essential components, setting up the development environment, installing JADE and Eclipse, and a book trading example. The content explores the power of Java technology, Eclipse as an extensible devel
0 views • 51 slides
Agent Delivery and Curbside Voting: County Election Administration Training Conference Overview
The Agent Delivery and Curbside Voting training conference for the 2022 County Election Administration focuses on facilitating voting for individuals in specific circumstances such as those in residential facilities or healthcare facilities. The conference covers important topics like the agent deli
0 views • 9 slides
Exploring Efficient Hardware Architectures for Deep Neural Network Processing
Discover new hardware architectures designed for efficient deep neural network processing, including SCNN accelerators for compressed-sparse Convolutional Neural Networks. Learn about convolution operations, memory size versus access energy, dataflow decisions for reuse, and Planar Tiled-Input Stati
0 views • 23 slides
Intelligent Trading Agent for Power Trading in Wholesale Market
Department of Telecommunications' master thesis explores the development of the CrocodileAgent, an intelligent software agent designed to minimize negative impacts on power market balancing. The thesis delves into the evolution of the energy market, the concept of smart grids, and the significance o
0 views • 12 slides
Registered Agents Requirement for Business Entities in Colorado
Colorado law requires every domestic and foreign business entity operating in the state to maintain a registered agent. This agent can be an individual, a domestic entity, or a foreign entity with a place of business in Colorado. The registered agent is authorized to receive legal documents and noti
0 views • 9 slides
Performance Comparison of 40G NFV Environments
This study compares the performance of 40G NFV environments focusing on packet processing architectures and virtual switches. It explores host architectures, NFV related work, evaluation of combinations of PM and VM architectures with different vswitches, and the impact of packet processing architec
0 views • 24 slides