Modern Threat Modeling & Cloud Systems in OWASP Sacramento
Explore modern threat modeling techniques for cloud systems at OWASP Sacramento's June 2023 event. Agenda includes community topics and more. Membership at Granite City offers workspace perks and access to exclusive events. Learn about threat modeling history and methodologies like STRIDE and PASTA.
1 views • 14 slides
Enhancing Professional Learning Through Active Listening Framework
Explore a comprehensive professional learning resource focusing on inclusion, wellbeing, and equalities for Scotland's educators and learners. The resource includes slides on active listening, interconnectivity, and guidance on how to utilize the material effectively. Dive into the National Model fo
11 views • 24 slides
Machetes Top Brands & Styles Jungle & Survival Machetes
Gear up for your next adventure with Survival Supplies Australia's range of premium machetes. Find high-performance machete knives online for your next adventure.\n\nTop Brands & Styles\nBrowse our range of steel machetes, army machetes, and kukri knives. Our selection includes top brands like Cold
0 views • 2 slides
Understanding Survival Analysis in Medical Studies
Explore the key concepts of survival analysis, such as time-to-event data, censoring, and survivor functions. Learn how survival analysis methods estimate probabilities, compare survival rates between groups, and assess median survival times in medical research.
0 views • 28 slides
Cyber Threat Detection and Network Security Strategies
Threat detection is crucial in analyzing security ecosystems to identify and neutralize malicious activities. Methods like leveraging threat intelligence, behavior analytics, setting intruder traps, and conducting threat hunts are essential for proactive security. Implementing security through obscu
1 views • 51 slides
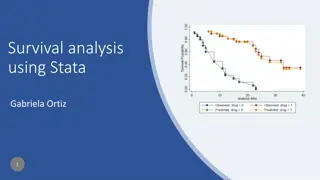
Survival Analysis Using Stata - Overview and Data Examination
This content discusses survival analysis using Stata, covering topics such as survival-time data, exploratory graphs, estimation, models, predictions, diagnostics, testing assumptions, and more. It explains how survival-time data is measured and discusses various examples and scenarios related to su
0 views • 83 slides
Understanding Survival Analysis: Concepts and Techniques
Survival analysis involves studying the time until an event of interest occurs, like death or relapse of a disease. It explores how different factors affect survival time and uses special methods for analysis. Censoring is a common issue where the exact endpoint time is unknown due to subjects being
0 views • 30 slides
The Persistent Threat of Puritan Beliefs to Elizabeth's Reign
The Puritan belief system posed a significant threat to Queen Elizabeth I's reign, challenging the religious settlement she had put in place. Puritans disagreed with key aspects of the Church of England, such as the use of crucifixes and clergy vestments, leading to conflicts and resistance. Elizabe
0 views • 10 slides
Understanding Stereotype Threat and Teacher Response in Education
Stereotype Threat Theory explores the fear of confirming negative stereotypes and its impact on academic performance. Reduction of this threat can lead to improved learning outcomes. Teacher response plays a crucial role in shaping student writing, with various studies highlighting the importance of
0 views • 9 slides
Cancer Survival Rates in Europe: Trends and Disparities
Cancer survival rates in Europe have shown variations across different types of cancer and countries. While overall cancer mortality has increased over the years, some countries have experienced declines in mortality rates. Survival rates for breast cancer between 1995-2014 ranged from 74% to 89%, w
0 views • 17 slides
Breast Cancer Survival Disparities by Molecular Subtypes in the US
Breast cancer molecular subtypes play a crucial role in determining survival outcomes. This study by Nadia Howlader, PhD, from the National Cancer Institute, presented the first nationally representative estimates of breast cancer survival by four main molecular subtypes. The research aimed to under
1 views • 23 slides
Fundamentals of Survival Time Analysis
Understanding survival time analysis involves concepts like probability density functions, cumulative survival functions, the hazard function, and more. This analysis helps estimate and compare survival experiences in different groups, providing valuable insights into predicting outcomes in various
0 views • 34 slides
Behavioral Threat Assessment Tabletop Exercise - College First Year Analysis
Explore a comprehensive behavioral threat assessment tabletop exercise focused on analyzing a college first-year scenario. The exercise includes roles and responsibilities for players, facilitators, evaluators, and observers, guiding participants through phases to familiarize themselves with a stude
0 views • 19 slides
Understanding Cyber Threat Assessment and DBT Methodologies
Comprehensive information on methodologies and approaches useful for cyber threat assessment and Cyber DBT alongside classical DBT methodology as outlined in the NSS-10 document by S.K. Parulkar. The content discusses the importance of threat assessment, differences between physical and cyber threat
4 views • 17 slides
Challenges in Computer Systems Security
Understanding security in computer systems involves achieving goals in the presence of adversaries. However, this task is challenging due to the need to guarantee policies in the face of realistic and open-ended threat models. Issues can arise from problems with policy formulation, assumptions in th
0 views • 16 slides
Enhancing Incident Response Through Threat Intelligence
Explore the importance of threat intelligence in incident response, covering aspects such as understanding adversaries, assessing risks, evaluating threats, and leveraging strategic intelligence. Learn how organizations can benefit from a proactive approach to cybersecurity by utilizing threat intel
1 views • 18 slides
Active Schools Games: Fun Fitness and Sports Challenges Await!
Join the exciting Active Schools Games featuring Starlight Steps to Fitness (Beginner), Starlight Steps to Fitness (Advanced), and Starlight Sports Challenges Game. Roll the dice, complete challenges, earn points, and race to the finish line in these engaging fitness and sports activities. Choose op
0 views • 8 slides
Thyroid Cancer Survival Trends in Europe: Eurocare-5 Study
A population-based study on thyroid cancer survival rates in Europe over 25 years reveals insights by sex, country, age, period, and histological type. The study shows increased incidence but stable mortality trends, with varying survival rates based on region, gender, and histology types like papil
0 views • 14 slides
Enhancing Learning Through Active Engagement: Strategies and Insights
Explore the concept of active learning with Swati Ramani, Director of Faculty Development & Curriculum Management at the Southern California University of Health Sciences. Discover the practical applications of active learning, key learning outcomes, and strategies for effective implementation. Dive
1 views • 19 slides
Comprehensive Training on Campus Threat Assessment Teams
Explore the advanced training curriculum developed by experts Marisa Randazzo, Ph.D., and Gene Deisinger, Ph.D., for Virginia Campus Threat Assessment Teams. The training covers areas like threat assessment processes, case management, legal updates, and challenges in team implementation. Participant
0 views • 92 slides
Impact of Cut-Point Selection on IO Survival Estimates
Using KEYNOTE-024 as a case study, this presentation examines the impact of cut-point selection on long-term survival estimates from piecewise modeling in immuno-oncology therapies. It explores the uncertainty in IO survival extrapolations and the use of piecewise survival models as a flexible alter
0 views • 22 slides
Mobile App Security Threat Modeling and Mitigation
Explore mobile app security threats, learn how to conduct threat modeling exercises, and implement mitigation strategies. Discover built-in security features, threat modeling technologies, and common threats like malware and code injection. Enhance your understanding of app security constraints and
0 views • 63 slides
Pennsylvania School Threat Assessment: Keeping Schools Safe
Pennsylvania schools have implemented a Threat Assessment Team to ensure the safety and security of students, staff, and community members. The team follows specific guidelines and procedures to assess and address threats, involving key stakeholders and promoting collaboration among multidisciplinar
0 views • 37 slides
Understanding Stereotype Threat in Education
Stereotype threat is a phenomenon where individuals from marginalized groups experience anxiety due to negative stereotypes about their abilities. This can impact their performance and self-perception. Various groups, such as African-Americans, Latinos, females in STEM, elderly individuals, Roma, an
0 views • 42 slides
Threat Assessment Tabletop Exercise Overview
Conducting a tabletop exercise focused on threat assessment in a school setting. The exercise agenda includes welcome, introductions, exercise goals, objectives, participants' roles, exercise structure, and rules. The goals are to test preparedness for potential threats, coordinate plans effectively
0 views • 33 slides
Understanding Threat Modeling and Offensive Security
Threat modeling in offensive security involves determining potential threat scenarios that could compromise a system, understanding the system from an attacker's perspective, and devising defensive strategies. It helps confirm security implementations, identify gaps, monitor shortcomings, vulnerabil
0 views • 31 slides
Understanding Threat Assessment in Conservation: Direct, Stress, and Indirect Threats
Within threat assessment for conservation, different types of threats are identified and categorized, including direct threats which are human-induced actions directly affecting conservation targets, stressors which result from biophysical impacts of actions on targets, and indirect threats contribu
0 views • 24 slides
Pennsylvania School Threat Assessment Procedures and Guidance
Ongoing concerns about school safety led to legislation in 2019, requiring schools in Pennsylvania to establish threat assessment teams. This presentation provides an overview of the statute, threat levels, team responsibilities, procedures, and resources for school staff, parents, and guardians to
0 views • 25 slides
Conducting Threat Assessments Through the Atrocity Prevention Lens
This module from the GLOBAL CENTRE FOR THE RESPONSIBILITY TO PROTECT focuses on conducting threat assessments through an atrocity prevention lens. It covers risk identification, situational awareness in field settings, information collection methods, addressing vulnerabilities of women and children,
0 views • 20 slides
Bomb Threat Preparedness Guidelines for Shifa International Hospital
The Shifa International Hospital emphasizes the importance of maintaining a secure environment for employees, patients, and visitors in the event of a bomb threat. This presentation covers the types of bomb threats, steps to follow in case of a bomb threat, and provides guidance on handling telephon
0 views • 14 slides
High School Students Behavioral Threat Assessment Tabletop Exercise Analysis
Conduct a tabletop exercise analyzing the behavioral threat assessment of two high school students. Explore roles and responsibilities, exercise itinerary, goal, and purpose to enhance threat assessment team preparedness and response. Utilize simulated scenarios to simulate real-world events for opt
0 views • 23 slides
Examining Stereotype Threat in Engineering Education
Exploring the experiences of female engineering students facing stereotype threat, this critical theoretical framework study sheds light on the challenges that impact their academic journey. Through narrative inquiry methodology, the research focuses on white female students to understand how stereo
0 views • 37 slides
Understanding Survival Analysis: Hazard Function and Cox Regression
Survival analysis examines hazards, such as the risk of events occurring over time. The Hazard Function and Cox Regression are essential concepts in this field. The Hazard Function assesses the risk of an event in a short time interval, while Cox Regression, named after Sir David Cox, estimates the
0 views • 20 slides
Evolution of Survival Sample Size Methods and Considerations in Survival Analysis
Survival analysis sample size determination is crucial for estimating the expected duration of time to an event accurately. Over time, methods have evolved from simple approximations to more complex models, offering greater flexibility and accuracy in study design. Considerations such as expected su
0 views • 9 slides
Introduction to Survival Analysis in Epidemiological Research
In epidemiology, survival analysis is used to analyze time-to-event outcomes like time until death or disease occurrence. It evaluates the effect of treatments on outcomes and considers both event occurrence and timing. This involves various methods such as the Kaplan-Meier estimator, hazard analysi
0 views • 20 slides
Thymic Neuroendocrine Tumors: Demographics, Treatment, and Survival Study
This study presents an analysis of thymic neuroendocrine tumors (TNET) focusing on demographics, treatment, and survival outcomes. Conducted as a retrospective cohort study using the NCDB data from 2004 to 2015, the study aimed to examine the characteristics of TNET in terms of demographics, clinica
0 views • 16 slides
Understanding Survival Analysis in Clinical Trials
Survival analysis plays a crucial role in analyzing data from randomized clinical trials, observational studies, and experiments. It involves estimating the survival function, conducting the log-rank test, and identifying when to use this analytical approach. Elements of survival experiments, standa
0 views • 73 slides
Understanding Active/Active SQL Clusters for High Availability
Discover the importance of Active/Active SQL clusters for ensuring 24/7 availability of your database servers. Learn about the benefits, setup process, and the high availability solution it offers for the entire server instance. Follow a detailed step-by-step guide for setting up SQL Active/Active c
0 views • 18 slides
School Safety and Threat Assessment Program Overview
Fact-based Threat Assessment for Safe and Supportive School Programs involves identifying, inquiring, assessing, and managing potentially dangerous situations. It aims to distinguish between those making threats and those posing real risks, without profiling or labeling individuals. Understanding th
0 views • 20 slides
Impact of Stereotypes on Perceived Facial Threat in Women Offenders
Facial expressions play a significant role in understanding emotions, but stereotypes can influence how people perceive facial affect. This study examines how reading tabloid articles about crimes committed by dark and light-skinned women offenders affects the perceived facial threat. Using a 2x2 fa
0 views • 9 slides