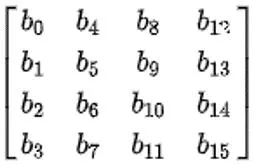Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds, and final round. Key expansion is crucial in generating round keys for each encryption round. AddRoundKey, SubBytes, ShiftRows, and MixColumns are essential operations in AES encryption.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
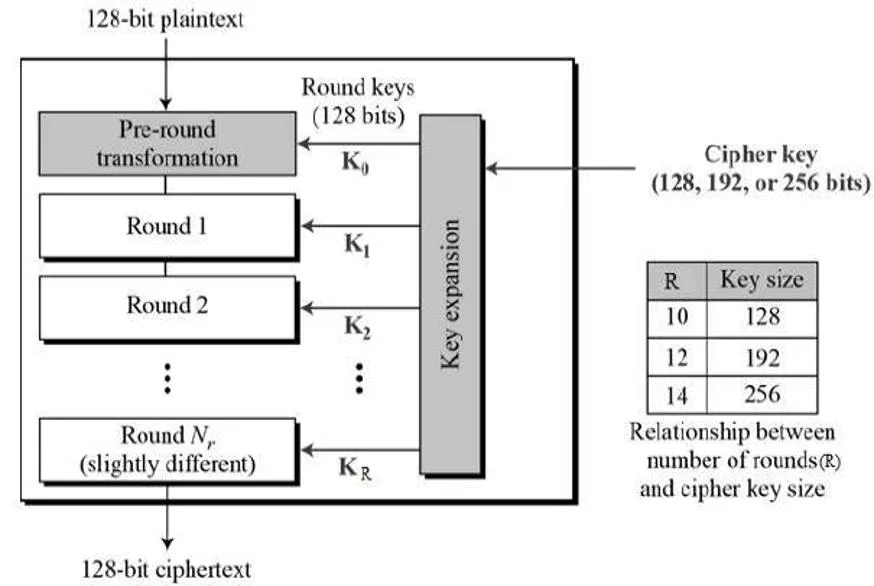
Mustansiriyah University Faculty of Engineering Advanced Encryption Standard Course name: Data Encryption Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Block Cipher Class: Third Year Block Cipher The Advanced Encryption Standard (AES), also called Rijndael, is a symmetric block cipher with a block length of 128 bits and support for key lengths of 128, 192, and 256 bits. It was published by NIST (National Institute of Standards and Technology) in 2001. Here, we assume a key length of 128 bits, which is likely to be the one most commonly implemented. 1
Mustansiriyah University Faculty of Engineering Advanced Encryption Standard Course name: Data Encryption Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Block Cipher Class: Third Year AES Block Cipher The AES Algorithm: AES operates on a 4 4 column-wise order array of bytes, called the state. For instance, if there are 16 bytes, these bytes are represented as this two-dimensional array: The key size used for an AES cipher specifies the number of transformation rounds that convert the plaintext into the ciphertext . The number of rounds are as follows: 10 rounds for 128-bit keys. 12 rounds for 192-bit keys. 14 rounds for 256-bit keys. Each round consists of several processing steps, including one that depends on the encryption key itself. A set of reverse rounds are applied to transform ciphertext back into the original plaintext using the same encryption key. 2
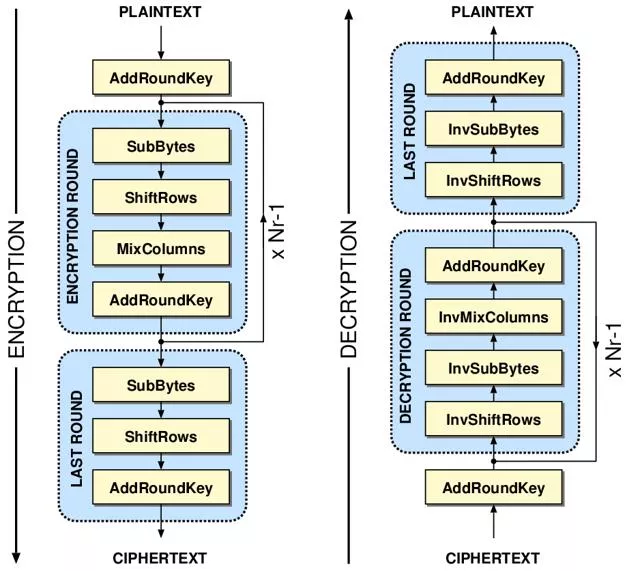
Mustansiriyah University Faculty of Engineering Advanced Encryption Standard Course name: Data Encryption Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Block Cipher Class: Third Year AES Block Cipher The AES Encryption Algorithm: The AES algorithm can be broken into three phases: the initial round, the main rounds, and the final round. All of the phases use the same sub-operations in different combinations as follows: Initial Round AddRoundKey Main Rounds (1,2 Nr-1) SubBytes ShiftRows MixColumns AddRoundKey Final Round (Nr) SubBytes ShiftRows AddRoundKey Note that in the above figure, KeyExpansion: round keys are derived from the cipher key using key expansion algorithm. AES requires a separate 128-bit round key block for each round plus one more. 3
Mustansiriyah University Faculty of Engineering Advanced Encryption Standard Course name: Data Encryption Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Block Cipher Class: Third Year AES Block Cipher AddRoundKey: In this operation, the 128 bits of State are bitwise XORed with the 128 bits of the round key. Here is an example where the first matrix is State, and the second matrix is the round key. e.g. = 4
Mustansiriyah University Faculty of Engineering Advanced Encryption Standard Course name: Data Encryption Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Block Cipher Class: Third Year AES Block Cipher SubBytes: A nonlinear substitution step where each entry (byte) of the current state matrix is substituted by a corresponding entry in the AES S-Box. For instance: byte (6E) is substituted by the entry of the S-Box in row 6 and column E, i.e., by (9F). (The byte input is broken into two 4-bit halves. The first half determines the row and the second half determines the column). e.g.: state = S_box(State) = 5
Mustansiriyah University Faculty of Engineering Advanced Encryption Standard Course name: Data Encryption Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Block Cipher Class: Third Year AES Encryption Cipher ShiftRows: A transposition step where the four rows of the state are shifted cyclically to the left by offsets of 0, 1, 2, and 3. e.g.: e.g.: 6
Mustansiriyah University Faculty of Engineering Advanced Encryption Standard Course name: Data Encryption Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Block Cipher Class: Third Year AES Block Cipher MixColumns: a linear mixing operation which multiplies fixed matrix against current State Matrix: Unlike standard matrix multiplication, MixColumns performs matrix multiplication as per Galois Field (28). e.g.: 7
Mustansiriyah University Faculty of Engineering Advanced Encryption Standard Course name: Data Encryption Computer Engineering Dep. Lecturer: Fatimah Al-Ubaidy Block Cipher Class: Third Year AES Block Cipher The AES Decryption Algorithm: AddRoundKey: Add Roundkey transformation is identical to the forward add round key transformation, because the XOR operation is its own inverse. Inverse SubBytes: This operation can be performed using the inverse S-Box. It is read identically to the S-Box matrix. InvShiftRows: Inverse Shift Rows performs the circular shifts in the opposite direction for each of the last three rows, with a one-byte circular right shift for the second row, and so on. InvMixColumns: The inverse mix column transformation is defined by the following matrix multiplication in Galois Field (28): 8