IEEE 802.11-20/1956r1 Ranging PHY Security Insights
Gain valuable insights into PHY security measures for IEEE 802.11-20/1956r1, including detection of PHY attacks, feedback mechanisms, and proposed draft changes by Erik Lindskog from Samsung, to enhance network security and reliability.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
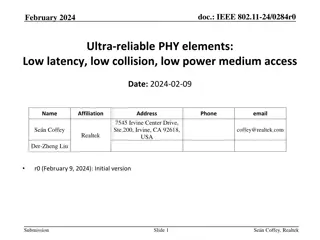
Jan 2021 doc.: IEEE 802.11-20/1956r1 Ranging PHY Security Date: Jan 6, 2021 Authors: Name Erik Lindskog Affiliations Address Samsung Phone email e.lindskog@samsung.com 3655 N 1st St, San Jose, CA 95134, USA Erik Lindskog, Samsung Submission Slide 1
Jan 2021 doc.: IEEE 802.11-20/1956r1 Feedback Protected PHY Security Erik Lindskog, Samsung Submission Slide 2
Jan 2021 doc.: IEEE 802.11-20/1956r1 Detection of PHY attacks We have repetition of LTFs to enable attack on encrypted LTFs. Relies on the peer modem to detect the attack Consider channel metric feedback to detect PHY attacks Utilize reciprocity of channel Feed back a metric of the channel estimate Whole channel estimate, or e.g. Average delay in the channel, i.e. the PS-TOA Enables the originating modem to detect the attack Erik Lindskog, Samsung Submission Slide 3
Jan 2021 doc.: IEEE 802.11-20/1956r1 Attack Scenario Unlikely that the channels are the same Erik Lindskog, Samsung Submission Slide 4
Jan 2021 doc.: IEEE 802.11-20/1956r1 PS-TOA Feedback PHY Attack Detection RSTA ISTA I2R NDP Measure t2 and tp2 R2I NDP Measure t4 and tp4 Feedback t2 and tp2 Compare tp2-t2 with tp4-t4! Feedback t4 and tp4 Compare tp2-t2 with tp4-t4! Forces attacker to attack both links or shift the entire channel estimate. Probably hard to do without triggering detection of the attack! Can be combined with LTF encryption! Erik Lindskog, Samsung Submission Slide 5
Jan 2021 doc.: IEEE 802.11-20/1956r1 Combination with LTF encryption Erik Lindskog, Samsung Submission Slide 6
Jan 2021 doc.: IEEE 802.11-20/1956r1 PHY attacks when the LTFs are encrypted When the LTFs are encrypted, attacks may not be possible with perfect LTF replica Possibly only some of the tones are estimated correctly The attack may only be partial in the time domain Causes unintended distortions of the channel raising the probability of detection Erik Lindskog, Samsung Submission Slide 7
Jan 2021 doc.: IEEE 802.11-20/1956r1 Proposed draft changes Erik Lindskog, Samsung Submission Slide 8
Jan 2021 doc.: IEEE 802.11-20/1956r1 Proposed draft changes Add optional fields in LMR frame to feedback TOA and PSTOA at the same time. Add mechanism to negotiate TOA+PSTOA feedback. Possibly mandate TOA+PSTOA feedback when secure LTFs are negotiated. Erik Lindskog, Samsung Submission Slide 9
Jan 2021 doc.: IEEE 802.11-20/1956r1 Addition of PSTOA field in LMR frame LMR frame: TOA TOD Error TOA Error Category Public Action Dialog Token TOD 6 6 1 1 6 Octets 1 1 Secure LTF Parameters (Optional) AOA Feedback (Optional) PSTOA (Optional) PSTOA Error (Optional) CFO Parameter I2R NDP Target RSSI R2I NDP Tx Power 1 6 Octets 1 9 1 2 13 Add PS-TOA feedback in PHY secure mode as additional protection against attacks! Erik Lindskog, Samsung Submission Slide 10
Jan 2021 doc.: IEEE 802.11-20/1956r1 Negotiation of TOA+_PSTOA Feedback The ISTA can signal both R2I TOA Type and I2R TOA Type = 1, and the RSTA can respond with both fields also set to 1. This trigger PSTOA feedback type in both directions (assuming R2I LMR is negotiated). Propose to in this corner case we can require that both PSTOA and TOA is fed back. Thus, we have a way to negotiate combined PSTOA and TOA feedback without having to add a bit. Or we can add a byte to the Ranging Parameters Field. Or we can use a reserved bit in the Non-TB specific subelement. Erik Lindskog, Samsung Submission Slide 11
Jan 2021 doc.: IEEE 802.11-20/1956r1 Mandate TOA+PSTOA Feedback Do we want to mandate TOA+PSTOA Feedback when secure LTFs are used? Erik Lindskog, Samsung Submission Slide 12
Jan 2021 doc.: IEEE 802.11-20/1956r1 Straw Poll 1 Do you support adding mechanism to negotiate and feed back both TOA and PSTOA? Y/N/A: Erik Lindskog, Samsung Submission Slide 13
Jan 2021 doc.: IEEE 802.11-20/1956r1 Straw Poll 2 Which do you prefer? Opt 1: Using R2I TOA Type and I2R TOA Type = 1 to signal feeding back both TOA and PSTOA Opt 2: Adding a byte to the Ranging Parameters field and using a bit there for negotiation of feeding back both TOA and PSTOA Opt 3: Neither Opt 4: Abstain Erik Lindskog, Samsung Submission Slide 14
Jan 2021 doc.: IEEE 802.11-20/1956r1 Straw Poll 3 Do you support mandating feeding back both TOA and PSTOA when secure LTFs are used? Y/N/A: Erik Lindskog, Samsung Submission Slide 15
Jan 2021 doc.: IEEE 802.11-20/1956r1 Thank You! Submission Slide 16 Erik Lindskog, Samsung