Evolution of Data Storage and Processing Technologies
Moore's Law, illustrated through examples in processor capacity and travel efficiency, showcases the rapid advancements in technology. From expensive and limited storage options to cheap and abundant data storage, the journey has been transformative. Additionally, data security laws and breach notification regulations highlight the importance of safeguarding information in this digital age.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
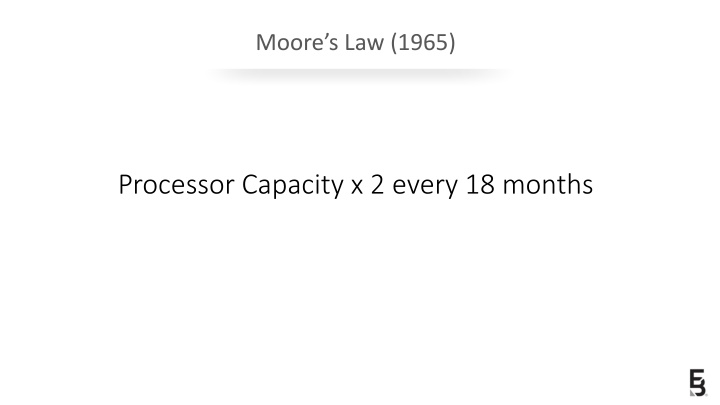
Moores Law (1965) Processor Capacity x 2 every 18 months
Moores Law applied to travel 2005 NY - Paris $0.01 <1 second 1978 NY Paris $900 7 hrs.
Data Storage 1 GB App. $10 FB Purchases its 1st 1 GB Hard Drive - $5K Microsoft: 1 TB free with office 365 2001 2010 1956 1995 2008 2014 Google gives 2 GB free with Gmail Account IBM 5 mb hard drive 1 GB App. $0.15
IBMs 305 RAMAC 50 24 discs 5 mb total storage 16 sq. ft $35,000/mo.
= .
Data Storage 1 GB App. $10 FB Purchases its 1st 1 GB Hard Drive - $5K Microsoft: 1 TB free with office 365 2001 2010 1956 1995 2008 2014 Google gives 2 GB free with Gmail Account IBM 5 mb hard drive 1 GB App. $0.15
Digital Packrats Cheap Data Storage + Cheap processing power = Packrat Paradise
State Data Security laws 47 States and 4 U.S. Jurisdictions Kentucky most recent 7/1/14 Timing requirements to notify resident consumers Notice without unreasonable delay - 45 days Notify AG, law enforcement, consumer protection agencies and credit reporting agencies timing to notify regulators & credit reporting agencies 48 hours; fourteen days; before notice to residents Some states require specific notice content
Security Breach Notification Laws State State Citation Citation State Citation Alaska Stat. 45.48.010 et seq. KRS 365.732, KRS 61.931 to 61.934 Alaska Kentucky Arizona Ariz. Rev. Stat. 44-7501 Louisiana La. Rev. Stat. 51:3071 et seq., 40:1300.111 to .116 Arkansas Ark. Code 4-110-101 et seq. California Cal. Civ. Code 1798.29, 1798.80 et seq. Maine Me. Rev. Stat. tit. 10 1347 et seq. Md. Code Com. Law 14-3501 et seq., Md. State Govt. Code 10- 1301 to -1308 Maryland Colorado Colo. Rev. Stat. 6-1-716 Connecticut Conn. Gen Stat. 36a-701b Delaware Del. Code tit. 6, 12B-101 et seq. Mass. Gen. Laws 93H-1 et seq. Massachusetts Florida Fla. Stat. 501.171, 282.0041, 282.318(2)(i) Michigan Mich. Comp. Laws 445.63, 445.72 Minnesota Minn. Stat. 325E.61, 325E.64 Georgia Ga. Code 10-1-910, -911, -912; 46-5-214 Miss. Code 75-24-29 Mississippi Mo. Rev. Stat. 407.1500 Missouri Hawaii Haw. Rev. Stat. 487N-1 et seq. Idaho Idaho Stat. 28-51-104 to -107 Montana Mont. Code 2-6-504, 30-14- 1701 et seq. Illinois 815 ILCS 530/1 to 530/25 Nebraska Neb. Rev. Stat. 87-801, -802, - 803, -804, -805, -806, -807 Indiana Ind. Code 4-1-11 et seq. ., 24-4.9 et seq. Nevada Nev. Rev. Stat. 603A.010 et seq., 242.183 Iowa Code 715C.1, 715C.2 Iowa Kansas Kan. Stat. 50-7a01 et seq.
Security Breach Notification Laws State Citation State Citation Texas Tex. Bus. & Com. Code 521.002, 521.053, Tex. Ed. Code 37.007(b)(5) New Hampshire N.H. Rev. Stat. 359-C:19, -C:20, - C:21 New Jersey N.J. Stat. 56:8-161, -163 Utah Utah Code 13-44-101 et seq. New York N.Y. Gen. Bus. Law 899-aa, N.Y. State Tech. Law 208 Vermont Vt. Stat. tit. 9 2430, 2435 Va. Code 18.2-186.6, 32.1- 127.1:05 Virginia North Carolina N.C. Gen. Stat 75-61, 75-65 North Dakota N.D. Cent. Code 51-30-01 et seq. Washington Wash. Rev. Code 19.255.010, 42.56.590 Ohio Ohio Rev. Code 1347.12, 1349.19, 1349.191, 1349. 192 W.V. Code 46A-2A-101 et seq. West Virginia Wisconsin Wis. Stat. 134.98 Oklahoma Okla. Stat. 74-3113.1, 24-161 to - 166 Wyo. Stat. 40-12-501 et seq. Wyoming Oregon Rev. Stat. 646A.600 to .628 Oregon D.C. Code 28- 3851 et seq. District of Columbia Guam 9 GCA 48-10 et seq. Pennsylvania 73 Pa. Stat. 2301 et seq. Rhode Island R.I. Gen. Laws 11-49.2-1 et seq. 10 Laws of Puerto Rico 4051 et seq. Puerto Rico S.C. Code 39-1-90, 2013 H.B. 3248 South Carolina V.I. Code tit. 14, 2208 Virgin Islands Tennessee Tenn. Code 47-18-2107
Massachusetts Data Security law Asserts Broad Jurisdiction PII on one resident
Massachusetts Data Security law Enforcement Out of State 7/23/14: Women & Infant s Hosp. RI 12,000 Mass. patients $150,000
Massachusetts Data Security law Data Protections Standards 201 CMR 17 Comprehensive Security Program Requires encryption
Federal Laws Congressional Research Paper http://fas.org/sgp/crs/secrecy/RL34120.pdf
Federal Laws Health Insurance Portability and Accountability Act (HIPAA) Health Information Technology for Economic and Clinical Health Act (HITECH) Fair and Accurate Credit Transactions Act (FACTA) Gramm-Leach-Bliley Act Identity Theft Enforcement and Restitution Act (ITERA) Sarbanes-Oxley
Federal Laws Similar notification procedures as found in state laws
Federal Laws Generally apply to Unsecured data E.G. HIPAA applies to Unsecured PHI
Federal Laws Unsecured = Not secured by technology or methodology that renders PHI unreadable
Federal Laws Unsecured = Unencrypted