Cybersecurity:
Safeguarding digital transformation in Facility Management is crucial for empowering FM professionals to automate, reinvent the industry, and rethink value propositions. FM is rapidly digitizing to enhance occupant health, reduce environmental impacts, and provide better operational telemetry. Investments in information for action, secure transactions, management and control, and greater interactivity with prosumers are shaping the future of FM. Digitizing building functional areas such as fire systems, physical access control, HVAC systems, and IT networks is essential for building cybersecurity resilience.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
Cybersecurity: Safeguarding FM s digital transformation Jeffrey Saunders, Director of Research, IFMA and CEO, Nordic Foresight Dr. Erika P rn, Cambridge University Ted Ritter, LMI360
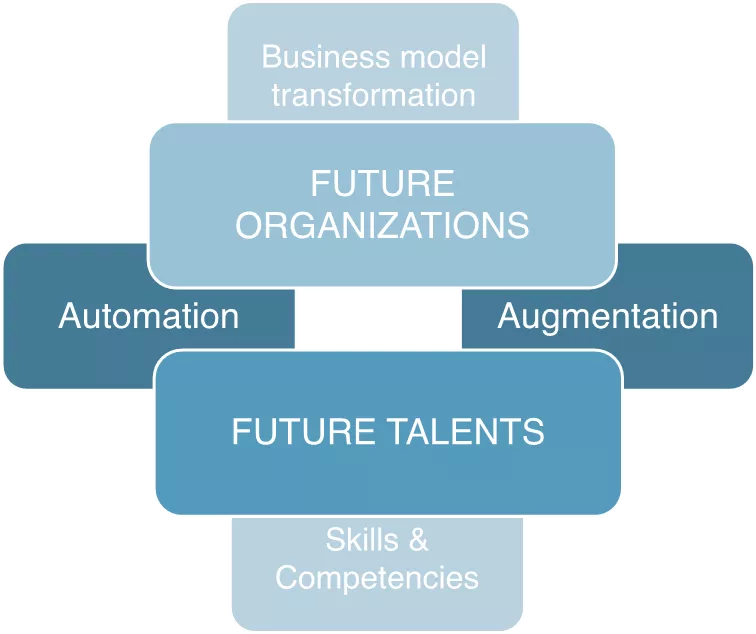
Digital transformation is enabling Facility Managers to: Empowering FM ers to: Automate and augment: Re-invent the industry Substitute products & services Craft new digital businesses Reconfigure delivery models Rethink value propositions
FM is rapidly digitizing to: Improve occupant health & well-being Reduce environmental impacts FM's transformation Provide better operational telemetry Controlling flows into the built environment
While the market is investing into the following areas: Information for action: Ubiquitous sensors and near real-time data collection on people, operations, processes, and buildings enable FM'ers to conduct evermore powerful descriptive, diagnostic, predictive, and prescriptive analytics for more sustainable operations and assets. Faster and more secure transactions: The emergence of identity authentication, the Internet of Things, and distributed ledger technologies enable fast and more secure transactions, large and small, in the built environment. New transaction opportunities could allow alternative ways to time slice assets. Greater management & control: New interfaces and dashboards that enable more sophisticated control over assets in the built environment. Greater interactivity with prosumers: Digital interfaces and emergent grid technologies enable increased interactivity of people with buildings and buildings with neighborhoods. FM ers will increasingly engage with these operating models. Download IFMA s DT study
Digitizing the following building functional areas: Fire Systems Fire Detection Systems (alarms) Fire Protection Systems (sprinklers) Physical Access Systems Physical Security Control Video Surveillance People Count HVAC Systems Ventilation, Chillers, Air Handling, Purification Air Quality, Health A/V and Digital Signage Standard Emergency People Transport Systems Elevators Escalators Moving walkways Voice Communication Systems Standard Emergency Lighting Systems Standard lighting and shades Emergency lighting Voice Communications (wired & wireless) Parking Systems Access EV Charging Utility Systems Gas Water, Boilers, Filtration Electric (including Backup Generators, UPS, Solar, Wind) Building Automation Systems IT Systems Owner Network Property Management Source: Building Cyber Security, 2023
Digitization of FM operations and assets create new: Targets Vectors Means Surfaces Mechanisms for targeting buildings which have become the focus of attacks themselves. This Photo by Unknown Author is licensed under CC BY-SA-NC
World Economic Forum: The Global Risks Report 2023 Alongside a rise in cybercrime, attempts to disrupt critical technology-enabled resources and services will become more common, with attacks anticipated against agriculture and water, financial systems, public security, transport, energy and domestic, space-based and undersea communication infrastructure. World Economic Forum 2023 The Global Risks Report 2023
Cyber security risks are on building owners agendas. They should be on FM s agenda too: 2022 2023
But, we are not prepared Leading obstacles facing facility managers Leading cyber risks facing facility managers Unauthorized access to building control systems Unaware of cyber risks & unsure of responsibility Lack of unified contracting models & commercial relations & Obsolete legacy systems Data manipulation & unauthorized access to systems with confidential information System & Keeping abreast of rapidly evolving technology & threat picture service disruption & long-term interruption Physical damage to buildings systems that could lead to loss of life Balancing building security with accessibility Insurers refusing to cover costs (including P&C) of cyber attack Limited budgets
CDBB VISION BUILT ENVIRONMENT SYSTEM 10
SYSTEM OF SYSTEMS COMPLEX SYSTEM 11
HACKING A BUILDING HACKING A BUILDING HACKING A BUILDING CONTROL SYSTEM HACKING A BUILDING CONTROL SYSTEM
FM AT THE NEXUS OF CHANGE INCREASED PRESSURES ON FM PROFESSIONAL Institutional Pressures To transform digitally To comply with new measures FACILITY MANAGEMENT INDUSTRY Organizational self-interest 13
WHAT IS A CYBER-PHYSICAL ATTACK CYBER-PHYSICAL ATTACKS OF BUILDINGS Cyber-attack is the activity of using code to interfere with the functionality of a computer system for strategic, ambiguous, experimental or political purposes (Nye, 2017). Cyber-physical attacks extend such threats via physical harm, disruption or damage to physical assets leading to health, safety and environment (HSE) consequences in physical world (Peng et al., 2015). Nye J., S. (2016) International Security, Vol. 41, No. 3 (Winter 2016/17), pp. 44 71, DOI: http://dx.doi.org/10.1162/ISEC_a_00266 Peng,Y., Wang,Y., Xiang, C., Liu, X., Wen,Z., and Chen, D., (2015) Cyber-physical attack-oriented industrial control systems (ICS) modeling, analysis and experiment environment, 2015 International Conference on Intelligent Information Hiding and Multimedia Signal Processing, pp. 322- 326, DOI: http://dx.doi.org/10.1109/IIH-MSP.2015.110 14
HOW IS AN ATTACK FORMED? ? HOW IS AN ATTACK FORMED
BLACK HAT: BLACK HAT: EGO, PERSONAL ANIMOSITY , AND ECONOMIC GAIN EGO, PERSONAL ANIMOSITY , AND ECONOMIC GAIN USA, 2014 Power and utilities - Hackers took advantage of a weak password vulnerability where mechanical devices were disconnected from the control Hacktivists system for scheduled maintenance. Poland, 2008- Transport - A 14-year old Polish student, hacked into the tram system which enabled him to change track points in Lodz, Poland. Four trams were derailed, consequently, twelve people Script kiddies were injured. USA, 2001- Petroleum- The network monitoring PC provided a path from the internet, via the company business network onto the Automation network. Making the company vulnerable to the Code Red Worm, used to deface the Automation Web Pages of a large oil company. Cyber insiders Iran, 2012-Petroleum - Iran has been forced to disconnect key oil facilities after suffering a malware attack. The computer virus is believed to have hit the internal computer systems at Cyber terrorists Iran s oil ministry and its national oil company. Spain, 2011- Traffic- Malware detected on the Spainair central computer system was a Trojan. On August 20, 2008 Spanair flight 5022 crashed just after take-off from Madrid-Brajas International Airport killing 154 with 18 survivors. The systems delivering power to the take-off warning system had failed. Trojan is speculated to have played a role in the crash by causing the computer to fail to detect three technical problems with the aircraft. Malware authors
BLACK HAT: BLACK HAT: EGO, PERSONAL ANIMOSITY , AND ECONOMIC GAIN EGO, PERSONAL ANIMOSITY , AND ECONOMIC GAIN USA and Europe, 2014 Energy sector-Dragonfly group operating since 2011, has targeted defence and aviation companies in the U.S. and Canada cyber- espionage. In 2013, the group targeted U.S. and European energy firms. Dragonfly gains entry through these methods: 1. spear phishing emails, malware , watering hole attacks , infecting legitimate software from three different ICS (industrial control systems) equipment manufacturers As of now Dragonfly s main motive seems to be, with a likelihood of sabotage in the future. Organized cyber criminals Canada, 2012 Energy sector- Telvent Canada, Ltd were subject to information theft, where installed malware and stole project files related to OASyS SCADA. Telvent, software and services provider used to monitor large sections of the energy industry. Security experts identify that the digital fingerprints leads to a Chinese hacking group known as the Comment Group . Patriot Hackers Iran, 2010, Nuclear One of the most prolific cyber-physical attacks remains as an exemplified case of government and civilian blurred lines, creating a new forefront of cyber militia and becoming the first proclaimed cyber weapon. Stuxnet malworm shut down uranium enrichment at Natanz for a week from Cyber militia Nov. 16 to 22, 2010. Snapshot of RISI Online Incident Database of cyber-physical hacking examples [available online at http://www.risidata.com/]
GREY HAT: GREY HAT: AMBIGUOUS AMBIGUOUS USA, 2012- Water/waste management- Former employee of The Key Largo Wastewater Treatment District hacked the company resulting in modification and deletion of files. Script Kiddies Venezuela, 2002 -Petroleum- Venezuela s state oil company became embroiled in a bitter strike was extensively sabotaged by an employee who gained, remote access to a program terminal to erase all PLC programs in port facility. Ordinary Citizens Snapshot of RISI Online Incident Database of cyber-physical hacking examples [available online at http://www.risidata.com/]
WHITE HAT: WHITE HAT: IDEALISM, CREATIVITY , RESPECT FOR THE LAW IDEALISM, CREATIVITY , RESPECT FOR THE LAW Canada, 2002- Petroleum- A whitehat hacker simulated attack on a DCS, where network access to the control LAN was to connect to selected DCS operator stations and obtain full administration privileges. This was accomplished through the vulnerabilities in the Windows operating system and a number of Netbios that lacked proper password protection. Hacktivists USA, 2014 Traffic - One of the first hacks on a traffic management incurred on a road sign in San Francisco, where signs were photographed flashing Godzilla Attack! Turn Script Kiddies Back . Snapshot of RISI Online Incident Database of cyber-physical hacking examples [available online at http://www.risidata.com/]
IT AND OT CONVERGENCE IT AND OT CONVERGENCE
DIGITAL TWIN OF ASSETS DIGITAL TWIN OF ASSETS CRITICAL INFRASTRUCTURES CRITICAL INFRASTRUCTURES Single source of Project Information (e.g. Design & Construction data, Asset information, etc.) made available to the RIGHT PEOPLE AT THE RIGHT TIME Built Asset Digitaltwin + Set of structured Data Federated 3D BIM Information
DIGITAL THREAD AND FABRIC DIGITAL THREAD AND FABRIC DIGITISING ASSET LIFECYCLE FOR O&M PURPOSES DIGITISING ASSET LIFECYCLE FOR O&M PURPOSES
DIGITAL FABRIC DIGITAL FABRIC DIGITISING ASSET LIFECYCLE FOR O&M PURPOSES DIGITISING ASSET LIFECYCLE FOR O&M PURPOSES BIM L A E I B FM Systems D K C H F G J HVAC/energy
VULNERABILITIES VULNERABILITIES Unauthorised access to BIM data could jeopardise security of sensitive facilities, such as banks, courts, prisons and defence establishments, and in fact most of the Critical National Infrastructure (Boyes, 2013). Public Buildings Infrastructure (bridges and highways) Military facilities Government facilities Smart residential buildings Manufacturing plants Ports Boyes H. (2013) Resilience and Cyber Security of Technology in the Built Environment The Institution of Engineering and Technology, IET Standards Technical Briefing, London. Available via: https://www.theiet.org/resources/standards/-files/cyber-security.cfm?type=pdf
CYBERSECURITY FRAMEWORKS CYBERSECURITY FRAMEWORKS
IFMA: CYBERSECURITY SURVEY FOR FM FSQCA ANALYSIS
OUR RESEARCH APPROACH DIFFERENT ROUTES SAME OUTCOME COMPLEXITY EQUIFINALITY This Photo by Unknown Author is licensed under CC BY This Photo by Unknown Author is licensed under CC BY-NC-ND 27
RESEARCH DESIGN STRUCTURE Research question What business preparedness configurations lead to negative cybersecurity outcomes with facilities managers? Methodology Cybersecurity preparedness framework and environmental conditions for competitive advantage Measure characteristics of business model configurations. Find generalized patterns of complex causality to develop business preparedness configurations and asset plausible pathways to business success with digital twins. Min. 200 in depth survey responses Purpose Data Analysis Configurational analysis of multiple conjectural causality through fuzzy-set analysis (Ragin, 2008) 28
FUZZY SET QUALITATIVE COMPARATIVE ANALYSIS WHY USE FSQCA? Seek causal pathways to the same outcomes, which may be achieved with various combinations of conditions. Causation must be understood in terms of necessary and sufficient conditions. Causal connections (causal complexity) are analysed to explain the pathways to a particular outcome. For example: What are the pathways for FM awareness configuration that lead to negative cybersecurity outcomes (i.e. number of breaches)? The same negative outcome (i.e. breached facility systems) can have multiple pathways (equifinality). 29
FSQCA CRISP VERSUS FUZZY SET Outcome: Scores high Outcome: Scores high Cause: Studies a lot Cause: Studies a lot CASE 1 CASE 2 CASE 3 CASE 1 CASE 2 QCA fsQCA Cause: High IQ score 30
RESEARCH AGENDA 2023 FM CYBERSEC. PREPAREDNESS ARCHETYPES AND OUTCOMES Problem Statement It is unclear what are the cybersecurity outcomes of FM service providers with different approaches to security preparedness. Therefore, quantitative survey will be used to identify which archetypes result in negative outcomes from cybersecurity breaches. Investigate FM cybersecurity preparedness by conducting a mass survey and quantitative analysis of outcomes from archetypes. Aim Definition of FM cybersecurity preparedness archetypes OB1 Objectives Descriptive statistics on negative cybersecurity outcomes OB2 Median cost of negative cybersecurity outcomes OB3 31
RESEARCH STATUS PROJECTED RESEARCH JOURNEY 2023 Qualitative Phase 1 Phase 2 Phase 3 Final report and presentation on findings Build configurations of FM preparedness Data collection of surveys 32
SURVEY DESIGN CONFIGURATIONS OF FM CYBERSECURITY PREPAREDNESS Asset Types Perception of criticality Preparedness and awareness Overall performance Entrepreneurial orientation Technological turbulence Outcomes Types of breaches Scale of damage Configuration characteristics 33
SURVEY DESIGN CONFIGURATIONS OF FM PREPAREDNESS Asset Types Perception of criticality Preparedness and awareness Starts with: Starts with: Starts with: Understanding the types of assets that are vulnerable to cyber breaches. Identifying level of criticality for different services in the asset. Understanding what the preparedness and knowledge of cybersecurity frameworks and standards. Key Questions: Key Questions: Which of the following sectors best represents the industry your facility(ies) serves? Please rank the following immediate threats facing your facility(ies)? Which of the following would be perceived as critical cybersecurity risks affecting your organisation? Key Questions: Which organisations' frameworks, if any, do you use to assess and manage the cyber security risk to your organization? 34
SURVEY DESIGN CONFIGURATIONS OF RESPONSIVENESS Overall performance Entrepreneurial orientation Technological turbulence Starts with: Starts with: Starts with: Understanding what is the overall business performance have they experienced any negative growth. Identifying ability to respond to competitors in the market and how much do they lead or follow their competitors. Understanding how well organisation responds to technological change in the market and how quickly they adopt new technology. Key Questions: Please evaluate the overall performance of your business. Please focus on customer (end-user) satisfaction relative to your major competitors over the past year? Key Questions: Key Questions: Please indicate the extent to which you agree or disagree with the following statements about your firm s entrepreneurial orientation.? Please indicate to what extent you agree or disagree with the statements on technology change in FM industry? 35
SURVEY DESIGN CONFIGURATIONS OF NEGATIVE OUTCOMES Types of breaches Scale of damage Starts with: Starts with: Understanding the types of breaches that have been knowingly identified, not all breaches will be recorded or identified. Identifying level of damage and disruption to services with cybersecurity incidents and breaches. Key Questions: How damaging to the organisation was the incident? Which of the following impacts of a cyber breach has your organization experienced? Key Questions: As far as you know, has your organization ever experienced a cyber security incident? 36