Understanding Vulnerability: Meaning, Types, and Factors affecting Vulnerability
This article explores the concept of vulnerability, including its meaning, types (physical and social), and factors that contribute to vulnerability. It discusses the impact of hazardous events on communities, infrastructure, and the environment, and highlights the importance of awareness and prepar
26 views • 31 slides
Historic Investments in Climate Action: Inflation Reduction Act May 2023
The Inflation Reduction Act (IRA) of May 2023 focuses on making significant investments in climate action to reduce U.S. emissions by an estimated 40% by 2030. This act supports disadvantaged communities, the clean energy industry, and aims to drive emissions reductions over the next decade while pa
5 views • 14 slides
Enhancing Cybersecurity with Bluedog VAPT Services
Bluedog Security Monitoring offers essential cybersecurity services, including Vulnerability Assessment and Penetration Testing (VAPT). Their automated VAPT combines External Vulnerability Scanning and WebApp Scanning to provide comprehensive testing solutions that help businesses prioritize risks,
0 views • 16 slides
Understanding Risk Management in Environmental Geography and Disaster Management
Risk management in environmental geography and disaster management involves assessing the potential losses from hazards, evaluating vulnerability and exposure, and implementing strategies to mitigate risks. It includes calculating risk, dealing with risk through acceptance, avoidance, reduction, or
2 views • 10 slides
Understanding Vulnerability Mapping (VM) for Ensuring Free and Fair Elections
This PowerPoint presentation delves into the concept of vulnerability mapping (VM) in the context of election planning, emphasizing the role of District Electoral Officers (DEOs/ROs) in controlling the entire VM process. It outlines pre-poll and poll-day responsibilities, as well as post-poll action
2 views • 36 slides
Comprehensive Guide to Vulnerability Mapping in Election Planning
Explore the significance of Vulnerability Mapping (VM) in empowering vulnerable voters, understand the concept, role of DEO/RO, and the objective of identifying and addressing voter vulnerability. The presentation emphasizes pre-poll and post-poll actions, remedial measures, and timelines, providing
3 views • 42 slides
Vulnerability Mapping (VM).Guidance Plan
Vulnerability Mapping (VM) is crucial in empowering vulnerable voters by identifying and addressing potential threats to their exercise of franchise. This guide explains the concept of vulnerability mapping, its role in ensuring free and fair elections, and the responsibilities of election officials
2 views • 42 slides
Understanding Vulnerability and Health Challenges in Scotland
Scotland's health challenges are highlighted through data on vulnerability markers such as sexual crimes, mental health issues, and rising missing person rates. Primary prevention is identified as a critical area needing attention to address entrenched challenges and societal impacts like the cost o
1 views • 20 slides
Understanding Telecom Security Testing: Vulnerability Assessment & Remediation
Telecom security testing is crucial for safeguarding infrastructure against hacks. Learn about vulnerability assessment, common weaknesses, types of vulnerabilities, severity scoring, and automated tools like Nessus and Nexpose. Explore network, web application, and host-based vulnerability testing
0 views • 18 slides
Effective Workflow for Vulnerability Research in Production Environments
Professional vulnerability research involves finding bugs efficiently through fuzzing techniques. The main goal is to develop a comprehensive workflow and toolset for effective bug discovery and triaging. Ancillary goals focus on determining exploitability, optimizing human and CPU efficiency, and e
0 views • 69 slides
Harm Reduction in Addiction Psychiatry: A Comprehensive Overview
Harm reduction in addiction psychiatry is a client-centered approach that focuses on reducing negative consequences associated with substance use. This philosophy involves practical strategies and principles aimed at promoting safer drug use practices. The historical background traces the evolution
3 views • 40 slides
Leveraging Artifact Dependency Graphs for Software Vulnerability Detection
Explore how LLVM-GitBOM utilizes artifact dependency graphs to detect vulnerabilities in software dependencies. The presentation covers the overview of GitBOM, CVE detection, supply chain vulnerabilities, and the importance of precise build tools in vulnerability scanning. Learn about utilizing gito
0 views • 34 slides
Techniques of Fracture Reduction in Veterinary Medicine
Explore the techniques of fracture reduction in veterinary surgery, including closed reduction and toggling method, explained by Dr. Archana Kumari. Learn about the advantages of closed reduction, indications for treatment, and the step-by-step technique involved in reducing fractures in animals. Di
0 views • 14 slides
Understanding Energy Analysis in Size Reduction Equipments
This comprehensive overview delves into the energy analysis involved in size reduction equipment, exploring topics such as objectives of size reduction units, sieve analysis for particle size distribution, mesh number system, and mathematical models for energy analysis in size reduction units. Dr. J
1 views • 11 slides
Understanding the Vulnerability Index for Small Island Developing States
This article discusses the concept of vulnerability in the context of countries, focusing on Small Island Developing States (SIDS). It explores the differences between vulnerability and poverty, the history of vulnerability index development from SIDS to Least Developed Countries (LDCs), and critiqu
8 views • 44 slides
Integrated Vulnerability Assessment and Human Security for Sustainable Livelihoods in the Solomon Islands
The approach to the Solomon Islands Integrated Vulnerability Assessment (SIIVA) and the Integrated Vulnerability and Adaptation Assessment (IVA) are key methodologies to assess climate change risks and prepare nations for adaptation. The objectives include informing national climate change policies,
0 views • 21 slides
Economic Vulnerability Premium for SIDS - Webinar Insights
Presentation outlines applying Economic Vulnerability Index (EVI) for an Economic Vulnerability Premium in Small Island Developing States (SIDS) during ADF 13 cycle. Details ADF grants availability, grant allocation framework, performance-based allocation system, and modifications needed for SIDS.
0 views • 14 slides
Understanding Theories and Models of Disaster
Works on disaster traditionally focus on natural triggers and human responses, but older views are considered incomplete. The Pressure-Release Model (PAR) explains vulnerability and risk reduction, highlighting underlying causes and unsafe conditions. Root causes such as economic, demographic, and p
0 views • 17 slides
Gender Considerations in Climate Vulnerability and Risk Assessments for Agriculture
This training workshop explores the intersection of gender, climate vulnerability, and risk assessments in adaptation planning for the agriculture sectors. It delves into how women and men may experience climate change effects differently and discusses ways to ensure gender considerations are includ
0 views • 6 slides
Understanding Vulnerability and Capacity Issues in Civil Courts
Exploring vulnerability and capacity issues in civil courts, this content delves into the importance of addressing vulnerabilities of parties and witnesses for ensuring fair participation and quality evidence in legal proceedings. Topics covered include factors contributing to vulnerability, the rol
0 views • 21 slides
Volkswagen Trust Climate Pollution Reduction Grants Missouri Community Kickoff
Volkswagen Trust Climate Pollution Reduction Grants are part of the Inflation Reduction Act, aiming to reduce greenhouse gas emissions. The grant breakdown includes $250 million for planning grants and $4.6 billion for plan implementation. Missouri's Department of Natural Resources is leading the pl
2 views • 18 slides
Methylene Blue Reduction Test for Milk Quality Assessment
The Methylene Blue Reduction (MBR) test is utilized to assess the quality of milk based on the reduction of color imparted by a dye. The disappearance of color indicates the presence of bacteria in milk. This test involves adding methylene blue dye to milk samples, observing the color change, and me
1 views • 20 slides
Understanding Oxidation-Reduction Reactions in Chemistry
Explore the concept of oxidation and reduction in chemistry, which are fundamental processes that occur simultaneously in oxidation-reduction reactions. Learn about the role of oxygen, different types of oxidation reactions beyond burning, such as bleaching stains, and the concept of reduction invol
0 views • 34 slides
Coastal Vulnerability Assessment of Curacao, Netherlands Antilles
Conduct a comprehensive Coastal Vulnerability Audit of Curacao, Netherlands Antilles, using the Coastal Vulnerability Audit Tool (CVAT) to assess physical, human, and engineering infrastructure systems, as well as vulnerability, planning, and resiliency action plans. Consider factors such as climati
0 views • 10 slides
Maritime Emissions Reduction Strategies and Policy Instruments Overview
Assessment of the Expert Groups' reports on maritime emissions reduction strategies, emphasizing the need for multiple policy instruments targeting new ships, existing ships, and operational aspects. Discusses the negative side effects of flexible policies and the importance of imposing requirements
1 views • 23 slides
Nevada Class-Size Reduction Program Overview
The Nevada State Board of Education implemented the Class-Size Reduction Act to reduce pupil-to-teacher ratios in early grades. Research shows mixed results on the effects of class-size reduction, with studies from various states highlighting different outcomes. The history of class-size reduction r
1 views • 14 slides
Electrochemical Reduction of CO2 on Copper and Mixed Metal Oxides
Different methods for CO2 reduction have been studied, with electrochemical reduction showing promise due to its use of electricity from nonconventional sources. Research on copper's unique characteristics for producing various CO2 reduction products has led to investigations into optimizing activit
0 views • 30 slides
Reimagining Vulnerability: Rethinking the Body and Human Dignity
The notion of vulnerability is explored within the framework of the human body and dignity, challenging traditional concepts of autonomy and independence. Scholars like Martha Nussbaum and Fineman provide insights on the universal nature of vulnerability and advocate for a shift towards recognizing
0 views • 21 slides
Understanding Risks and Vulnerability in Risk Assessment
This module focuses on understanding risks, vulnerability, and conducting risk assessments in disaster risk management. It covers terminologies such as threats, hazards, vulnerability, and exposure, essential for prioritizing risks and initiating risk reduction measures.
0 views • 24 slides
DC's Incarceration Reduction Amendment Act Overview
The DC's Incarceration Reduction Amendment Act (IRAA) provides a mechanism for individuals under the age of 25 at the time of offense, who have served at least 15 years in prison, to petition for sentence reduction or release. This Act is based on key US Supreme Court cases relating to the Eighth Am
0 views • 7 slides
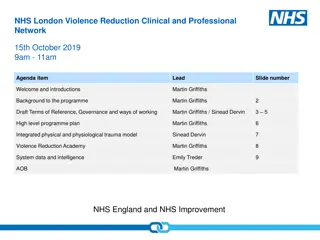
NHSL Violence Reduction Clinical & Professional Network Overview
The NHSL Violence Reduction Clinical & Professional Network aims to address the high number of violent incidents in London through a public health approach. Led by Martin Griffiths, the network provides a forum for clinicians and professionals to share expertise, offer strategic leadership, and supp
0 views • 9 slides
Gamifying Vulnerability Reporting for Coordinated Disclosure at Microsoft Security Response Center
Christa Anderson, a Senior Security Program Manager at Microsoft's Security Response Center, discusses the importance of gamifying vulnerability report data to encourage coordinated disclosure. The MSRC Top 100, announced at Black Hat USA, plays a crucial role in the public credit strategy by recogn
0 views • 13 slides
Utilizing Harm Reduction for Addressing Addiction in New River Valley
In this presentation, Michael E. Kilkenny discusses the importance of harm reduction as a public health tool in combating addiction issues in the New River Valley. The talk highlights the benefits of harm reduction, components of successful implementation, and measures of program success. It also ad
0 views • 20 slides
Development and Evaluation of Harm Reduction Acceptance Scales
Development of scales to measure the acceptance of harm reduction is crucial for understanding public attitudes towards harm reduction strategies. This project focuses on creating valid and reliable scales through a systematic process involving item development, data collection, analysis, and refine
0 views • 15 slides
Integrating Climate Change Adaptation in Disaster Risk Reduction Module 1
Welcome to the e-Learning module on integrating climate change adaptation in disaster risk reduction. This module covers concepts in disaster risk reduction and climate change adaptation. It is part of a package that includes five modules focusing on vulnerability, disaster risk reduction, climate c
0 views • 29 slides
Enhancing Nuclear Security Through Creative Vulnerability Assessment
Creative and effective vulnerability assessment and testing are essential in nuclear security to identify weaknesses and improve defense systems against intelligent adversaries. The need for in-depth assessment and realistic testing is emphasized to uncover vulnerabilities that adversaries may explo
0 views • 8 slides
Understanding Vulnerability in Research Populations
Vulnerability in research populations refers to being exposed to harm without the ability to protect oneself adequately. Factors contributing to vulnerability include intrinsic limitations like decision-making capacity and situational influences such as political or economic circumstances. Different
0 views • 22 slides
Exploring Vulnerability and Power Dynamics in Imperial Rome: Phaedrus' Perspective
Delve into the intricate relationship between constructions of vulnerability in imperial Latin texts and the material reality of vulnerability in ancient Rome. Discover how cultural perceptions of male citizen invulnerability rely on affirming vulnerability in others. Uncover the strengths of vulner
0 views • 10 slides
Enhancing Disaster Risk Reduction in the Philippines
The Philippine Disaster Risk Reduction and Management Act of 2010, also known as Republic Act 10121, replaced PD 1566 and introduced a proactive approach to disaster management, focusing on risk reduction and building community resilience. The new law aims to transform and reform disaster response b
0 views • 26 slides
Integrated Reduction Technique for Double Precision Accumulator
An integrated reduction technique for a double precision accumulator is discussed in the research paper by Krishna Nagar, Yan Zhang, and Jason Bakos from the University of South Carolina. The paper addresses issues related to double precision accumulation in kernels targeted for acceleration, presen
1 views • 25 slides