Understanding Vulnerability: Meaning, Types, and Factors affecting Vulnerability
This article explores the concept of vulnerability, including its meaning, types (physical and social), and factors that contribute to vulnerability. It discusses the impact of hazardous events on communities, infrastructure, and the environment, and highlights the importance of awareness and prepar
26 views • 31 slides
Understanding Risk Management in Environmental Geography and Disaster Management
Risk management in environmental geography and disaster management involves assessing the potential losses from hazards, evaluating vulnerability and exposure, and implementing strategies to mitigate risks. It includes calculating risk, dealing with risk through acceptance, avoidance, reduction, or
1 views • 10 slides
Comprehensive Guide to Vulnerability Mapping in Election Planning
Explore the significance of Vulnerability Mapping (VM) in empowering vulnerable voters, understand the concept, role of DEO/RO, and the objective of identifying and addressing voter vulnerability. The presentation emphasizes pre-poll and post-poll actions, remedial measures, and timelines, providing
3 views • 42 slides
Understanding Vocational Profiling Tools for Career Progression
Vocational profiling tools help assess individual skills, interests, and needs to support career decisions. Components include dreams, skills, learning styles, and support systems. Effective profiles focus on aspirations, talents, challenges, and solutions, guiding individuals towards suitable emplo
4 views • 9 slides
Vulnerability Mapping (VM).Guidance Plan
Vulnerability Mapping (VM) is crucial in empowering vulnerable voters by identifying and addressing potential threats to their exercise of franchise. This guide explains the concept of vulnerability mapping, its role in ensuring free and fair elections, and the responsibilities of election officials
2 views • 42 slides
Understanding Telecom Security Testing: Vulnerability Assessment & Remediation
Telecom security testing is crucial for safeguarding infrastructure against hacks. Learn about vulnerability assessment, common weaknesses, types of vulnerabilities, severity scoring, and automated tools like Nessus and Nexpose. Explore network, web application, and host-based vulnerability testing
0 views • 18 slides
Exploring Genetics and Genomics in Integrative Biology
Delve into the world of genetics and genomics through the lens of integrative biology, investigating the differences between cell types, the rationale for gene expression profiling, and the analysis of differential gene expression in various diseases. Uncover the significance of gene ontology, co-ex
0 views • 22 slides
Leveraging Artifact Dependency Graphs for Software Vulnerability Detection
Explore how LLVM-GitBOM utilizes artifact dependency graphs to detect vulnerabilities in software dependencies. The presentation covers the overview of GitBOM, CVE detection, supply chain vulnerabilities, and the importance of precise build tools in vulnerability scanning. Learn about utilizing gito
0 views • 34 slides
Importance of Data Collection in Policy-Making for IDP Profiling
Understanding the significance of collecting data for policy-making is crucial, especially in the context of Joint IDP Profiling services. Profiling IDPs through collaborative data collection helps identify displaced individuals or groups, leading to targeted advocacy, protection, assistance, and ev
0 views • 15 slides
Understanding the Vulnerability Index for Small Island Developing States
This article discusses the concept of vulnerability in the context of countries, focusing on Small Island Developing States (SIDS). It explores the differences between vulnerability and poverty, the history of vulnerability index development from SIDS to Least Developed Countries (LDCs), and critiqu
8 views • 44 slides
Integrated Vulnerability Assessment and Human Security for Sustainable Livelihoods in the Solomon Islands
The approach to the Solomon Islands Integrated Vulnerability Assessment (SIIVA) and the Integrated Vulnerability and Adaptation Assessment (IVA) are key methodologies to assess climate change risks and prepare nations for adaptation. The objectives include informing national climate change policies,
0 views • 21 slides
Gene Expression Profiling in Statistical Genetics Summer Institute 2020
This content provides information on the Summer Institutes of Statistical Genetics module, focusing on gene expression profiling. It includes details on the schedule, experimental design, RNA sequencing workflow, modes of bulk RNA sequencing, and RNASeq software. The content discusses crucial steps
0 views • 11 slides
Understanding Real-Time PCR and its Applications
Real-Time PCR, also known as quantitative PCR, is a specialized technique used in molecular biology for gene expression analysis, medical research, disease diagnosis, viral quantification, and more. It enables the real-time visualization and measurement of DNA sequences in a sample, playing a crucia
4 views • 8 slides
Efficient Identification of Memory Chip Errors with On-Die ECC
State-of-the-art memory error mitigations face challenges when dealing with on-die Error-Correcting Codes (ECC). "HARP" introduces a Hybrid Active-Reactive Profiling method to address these challenges by analytically studying the effects of on-die ECC and identifying key issues. Through hybrid profi
1 views • 4 slides
Understanding RESEA Program in Worker Profiling and Reemployment Services
The RESEA program aids in assessing unemployment insurance eligibility and providing reemployment services to claimants. Profiling helps target those at risk of long-term unemployment. Coordination between UI and employment service providers is essential for effective state operations. New initial c
0 views • 24 slides
Economic Vulnerability Premium for SIDS - Webinar Insights
Presentation outlines applying Economic Vulnerability Index (EVI) for an Economic Vulnerability Premium in Small Island Developing States (SIDS) during ADF 13 cycle. Details ADF grants availability, grant allocation framework, performance-based allocation system, and modifications needed for SIDS.
0 views • 14 slides
Gender Considerations in Climate Vulnerability and Risk Assessments for Agriculture
This training workshop explores the intersection of gender, climate vulnerability, and risk assessments in adaptation planning for the agriculture sectors. It delves into how women and men may experience climate change effects differently and discusses ways to ensure gender considerations are includ
0 views • 6 slides
LLVM Line Coverage Profiling Implementation Overview
Line coverage profiling in LLVM is implemented using built-in instrumentation facilities. This approach involves inserting PGO probes, interpreting them as coverage measurements, and generating coverage reports to assess the coverage of a test suite. The process allows for generating profile informa
2 views • 19 slides
Understanding Racial and Identity Profiling Act (RIPA) in California
The Racial and Identity Profiling Act (RIPA) in California requires law enforcement agencies to collect demographic data and other identifying characteristics based on officers' perceptions during pedestrian and traffic stops. The purpose of RIPA is to eliminate racial and identity profiling, improv
3 views • 18 slides
Understanding Profiling in Forensic Psychology
Explore the concept of profiling in forensic psychology, including its techniques, history, and applications in criminal investigations. Learn about the various categories of profiling and the role psychologists play in identifying unknown individuals based on behavioral patterns and characteristics
1 views • 69 slides
Understanding DNA Profiling: Techniques and Applications
DNA profiling, invented by Alec Jeffreys in 1985, is a technique used to distinguish between individuals of the same species based on their DNA. The process involves breaking down cells to release DNA, cutting the DNA into fragments using restriction enzymes, separating and analyzing fragments based
12 views • 23 slides
Understanding Vulnerability and Capacity Issues in Civil Courts
Exploring vulnerability and capacity issues in civil courts, this content delves into the importance of addressing vulnerabilities of parties and witnesses for ensuring fair participation and quality evidence in legal proceedings. Topics covered include factors contributing to vulnerability, the rol
0 views • 21 slides
Coastal Vulnerability Assessment of Curacao, Netherlands Antilles
Conduct a comprehensive Coastal Vulnerability Audit of Curacao, Netherlands Antilles, using the Coastal Vulnerability Audit Tool (CVAT) to assess physical, human, and engineering infrastructure systems, as well as vulnerability, planning, and resiliency action plans. Consider factors such as climati
0 views • 10 slides
The Future of Consumer Profiling and Commercial Communications: Insights from an International Conference
Explore the impact of platform economies, neuromarketing, and AI on commercial communications in the digital age. Learn how VLOPs use data to create user profiles and drive targeted advertising. Delve into the challenges of regulating VLOPs in the evolving landscape of consumer profiling.
0 views • 6 slides
Market-Led Approaches to New Variety Design in Africa
Explore Chapter 4 of "The Business of Plant Breeding" focusing on new variety design and product profiling in Africa. Understand core methods of product profiling, trait prioritization, and setting breeding objectives to meet client needs. Learn how to create new designs, set benchmarks, and make tr
0 views • 45 slides
Effective Data Selection Strategies for Model Building in Profiling Methods Seminar
Learn about the essential steps involved in selecting the right data for building effective models in the field of profiling methods. Understand the key considerations for data collection, formats, sample set determination, and targeting the right population to derive meaningful insights and outcome
0 views • 40 slides
Advancements in Optical Measurements for Ocean Observatories: The Argo Program
The Argo program integrates optical sensing into ocean observatories using profiling floats to gather data from the deep sea. With nearly 1,000,000 profiles to date, the Argo Observing System offers a global, real-time monitoring solution. Utilizing optics on profiling floats has enabled observation
0 views • 12 slides
Reimagining Vulnerability: Rethinking the Body and Human Dignity
The notion of vulnerability is explored within the framework of the human body and dignity, challenging traditional concepts of autonomy and independence. Scholars like Martha Nussbaum and Fineman provide insights on the universal nature of vulnerability and advocate for a shift towards recognizing
0 views • 21 slides
Understanding Risks and Vulnerability in Risk Assessment
This module focuses on understanding risks, vulnerability, and conducting risk assessments in disaster risk management. It covers terminologies such as threats, hazards, vulnerability, and exposure, essential for prioritizing risks and initiating risk reduction measures.
0 views • 24 slides
Profiling, Travel Bans, and Legal Rights Overview
Profiling individuals based on their characteristics for making decisions raises legal and ethical concerns, particularly when involving race, ethnicity, or religion. This excerpt highlights a case involving profiling during air travel, leading to wrongful detainment and questioning of individuals w
0 views • 49 slides
Gamifying Vulnerability Reporting for Coordinated Disclosure at Microsoft Security Response Center
Christa Anderson, a Senior Security Program Manager at Microsoft's Security Response Center, discusses the importance of gamifying vulnerability report data to encourage coordinated disclosure. The MSRC Top 100, announced at Black Hat USA, plays a crucial role in the public credit strategy by recogn
0 views • 13 slides
Continuous Asphalt Mixture Compaction Assessment Using Density Profiling System
Development of a comprehensive work plan for the assessment of asphalt mixture compaction using the Density Profiling System (DPS). The project aims to create a master database of field and lab measurements, refine protocols for dielectric value-density relationships, propose changes for sensor bias
0 views • 11 slides
Basics of Hypothesis Testing in Gene Expression Profiling
The lecture covers the essential aspects of hypothesis testing in gene expression profiling, emphasizing experimental design, confounding factors, normalization of samples, linear modeling, gene-level contrasts, t-tests, ANOVA, and significance assessment techniques. Practical insights are shared on
0 views • 9 slides
Semi-Supervised User Profiling with Heterogeneous Graph Attention Networks
Utilizing heterogeneous graph attention networks, this study addresses the limitations of existing user profiling methods by integrating multiple data types and capturing rich interactions in user data. The approach tackles critical problems in representation learning, information propagation, and m
0 views • 15 slides
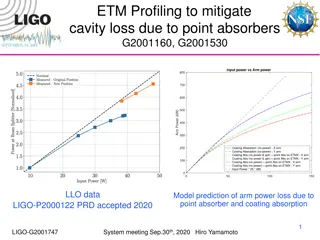
ETM Profiling for Cavity Loss Mitigation Due to Absorbers
The ETM profiling aims to mitigate cavity loss caused by point absorbers through input power analysis versus arm power. The study includes data on coating absorption, arm power loss predictions, and optimization strategies such as polishing and mirror surface design. The effect of new coatings is co
0 views • 48 slides
Enhancing Nuclear Security Through Creative Vulnerability Assessment
Creative and effective vulnerability assessment and testing are essential in nuclear security to identify weaknesses and improve defense systems against intelligent adversaries. The need for in-depth assessment and realistic testing is emphasized to uncover vulnerabilities that adversaries may explo
0 views • 8 slides
Managing Performance Issues with VS2010 Profiling & Load Testing
Explore the basics of web performance tests and load tests using Visual Studio 2010 Profiling and Load Testing. Learn how to identify and address performance issues, establish performance baselines, and catch problems early in the development cycle. Discover best practices for enhancing application
0 views • 60 slides
Understanding Vulnerability in Research Populations
Vulnerability in research populations refers to being exposed to harm without the ability to protect oneself adequately. Factors contributing to vulnerability include intrinsic limitations like decision-making capacity and situational influences such as political or economic circumstances. Different
0 views • 22 slides
Exploring Vulnerability and Power Dynamics in Imperial Rome: Phaedrus' Perspective
Delve into the intricate relationship between constructions of vulnerability in imperial Latin texts and the material reality of vulnerability in ancient Rome. Discover how cultural perceptions of male citizen invulnerability rely on affirming vulnerability in others. Uncover the strengths of vulner
0 views • 10 slides
Challenges and Lessons Learned in CSU Millennium to Alma Migration
The migration from CSU Millennium to Alma presented various data profiling challenges and migration points, such as data cleanup recommendations, handling of electronic resources, post-migration cataloging issues, and unique complications in managing Alma instances across campuses. Lessons include t
0 views • 8 slides