Understanding Female Genital Mutilation: Improving Healthcare Provision
Delve into the complexities of Female Genital Mutilation (FGM), exploring its global, UK, and Northern Ireland contexts. Understand the health implications, cultural motivations, and legal frameworks surrounding FGM. Discover the vital need for improved healthcare services to support affected popula
0 views • 15 slides
Illegally obtained evidence
Illegally obtained evidence refers to evidence acquired through unlawful means, such as searches without warrants or extraction under duress. The Fruit of the Poisonous Tree doctrine renders evidence inadmissible if derived from illegally obtained evidence. The Exclusionary Rule prohibits the use of
2 views • 30 slides
Enhancing Accessibility with Handrail Installations in the Neighborhood
Installing handrails at 43 South Russell St., prompted by a violation notice, has not only assisted the Retired Archbishop of Kenya during his stay but also accommodated other visitors with mobility challenges. The handrail installation follows a similar model to others in the neighborhood, aiming t
0 views • 5 slides
Understanding Criminal Law and Procedure: Greenvisor's Case
A case study involving embezzlement by Joe Greenvisor, the chief accountant of Nobreath Corporation, sheds light on criminal acts, duties, intent, and societal perspectives on crime. Despite Greenvisor's charitable intentions, his actions constituted a crime under the law. The elements of criminal a
0 views • 47 slides
Understanding Atomicity Violation in Concurrent Programs
Explore the concept of atomicity violation in concurrent programs along with detection techniques to ensure the integrity of critical code blocks. Learn from examples and insights shared by Prof. Moonzoo Kim.
0 views • 23 slides
Understanding Violations of Probation Hearings
This content discusses various aspects related to violations of probation, including ways to address issues that arise in violation of probation hearings, changes in probation conditions without a violation of probation (VOP), loss of jurisdiction implications, credit for jail time served as a condi
0 views • 86 slides
Understanding Domestic Abuse and Supporting Children in Scotland
This presentation provides information on domestic abuse, its impact on children and young people, signs of abuse, and the role of adults in supporting learners in educational settings in Scotland. It highlights the prevalence of domestic abuse, defines what domestic abuse is, explores how children
0 views • 16 slides
Understanding the Harsh Realities of Human Trafficking
Human trafficking is a heinous crime that preys on the vulnerable, particularly women and children, for purposes such as slavery, organ trafficking, sexual exploitation, and forced marriage. Poverty, unemployment, false promises, domestic violence, and natural disasters are key factors that fuel thi
0 views • 15 slides
University of Delaware Civil Rights Training Session Overview
This overview covers the University of Delaware's Civil Rights policies which prohibit discrimination based on various categories. It includes information on reporting obligations for employees regarding incidents of violation, such as sexual harassment and assault. The content emphasizes the import
0 views • 28 slides
Understanding Female Genital Mutilation (FGM) and its Impact
Female Genital Mutilation (FGM) is a harmful practice involving the partial or total removal of external female genitalia. This workshop aims to educate on the types of FGM, its origins, children at risk, health implications, and the legal aspects. Personal stories highlight the psychological effect
0 views • 36 slides
Addressing Disrespect and Abuse in Maternity Care
Maternity care workers face challenges related to disrespect and abuse during facility-based childbirth worldwide. Issues such as physical abuse, non-consented care, non-confidential care, non-dignified care, and discrimination have been documented in various countries. This global problem lacks nor
1 views • 19 slides
Overview of gologit2: Generalized Logistic Regression Models for Ordinal Dependent Variables
gologit2 is an advanced program for estimating generalized logistic regression models, including proportional odds, generalized ordered logit, and partial proportional odds models. It offers features beyond traditional ologit, allowing for less restrictive and more parsimonious modeling of ordinal d
0 views • 27 slides
Disintegration Within the EU: Negative Spillovers and the Refugee Crisis by Tamas Dezso Ziegler
This content discusses the disintegration within the European Union due to negative spillovers and challenges in handling the EU's refugee crisis. It highlights the violation of EU laws, changes in the concept of refugees, human rights breaches, and the spread of toxic demagoguery within the EU legi
0 views • 9 slides
Essential Elements of a Tort in Indian Law
The essential elements of a tort under Indian law include a wrongful act, legal damage, and legal remedy. A wrongful act is one that violates another's legal rights, while legal damage refers to harm caused by the wrongful act. The concept of "damnum sine injuria" is also crucial in determining lega
0 views • 7 slides
Neutron-Antineutron Oscillation Sensitivity Study at DUNE
The study at DUNE focuses on discriminating signals for neutron-antineutron oscillation sensitivity, aiming to measure CP violation and explore BSM physics. DUNE uses a Liquid Argon Time Projection Chamber to search for antineutron annihilation in nuclei, branching ratios, and interaction products s
0 views • 10 slides
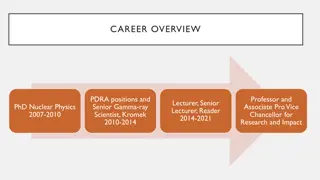
Accomplished Career in Nuclear Physics and Gamma-ray Spectroscopy
Experienced professional with a diverse background in nuclear physics and gamma-ray spectroscopy. Successfully held positions including Senior Gamma-ray Scientist, Professor, Associate Pro Vice Chancellor, and more. Achieved significant milestones such as securing research funding, supervising PhD s
1 views • 4 slides
Understanding Section 1983 Claims and Civil Rights Attorney Fees
Section 1983 of the Civil Rights Act allows individuals to seek redress for violations of their constitutional rights by persons acting under state law. This provision does not create new rights but provides remedies for existing rights. The history of Section 1983 dates back to 1871 and has been in
0 views • 27 slides
Algebraic Solutions for Two-Dimensional Adjoint QCD
Two-dimensional adjoint QCD is explored with a basis-function approach aiming to achieve single-particle states over cluttered multi-particle states. The algebraic solution involves t'Hooft-like integral equations and pseudo-cyclicity considerations to address parton number violation and boundary co
0 views • 22 slides
Appeal of Administrative Decision on Violation of Washoe County Code
Property owner appealing violation findings under Washoe County Code for outdoor storage of commercial vehicles on residential property. Case involves enforcement procedures, penalties, and administrative hearing officer's decision.
1 views • 23 slides
A River by A.K. Ramanujan - Poetic Reflection on Realism and Tragedy
Attipate Krishnaswami Ramanujan's poem "A River" portrays a stark reality of a river in Madurai that dries up, contrasting with poets who only sing of floods. The poem criticizes traditional poetic portrayals while ironically becoming a violation of realism itself. Ramanujan's poignant verses delve
0 views • 17 slides
Legal Scenario Analysis: Liability in a Complex Situation
Tito, Mia, Omar, and Kashawn are involved in a series of incidents post a party, leading to varying degrees of injuries. Tito's red light violation causes a collision with a bicyclist, resulting in a subsequent car accident that leaves Mia severely injured. Omar suffers an allergic reaction to treat
0 views • 19 slides
Understanding the Acceleration of the Universe and the Equivalence Principle Violation in the Horndeski Vector-Tensor Theory
Exploring the implications of the Equivalence Principle Violation after reheating in the context of the accelerated expansion of the universe. The study delves into the Horndeski vector-tensor theory, gravitational waves, and the impact of modified gravity and dark energy. Insights are provided on t
2 views • 20 slides
Enhanced Offender Supervision Through Response & Incentive Matrix
The Response & Incentive Matrix (RIM) aims to provide offenders with fair incentives and violation responses, reducing judicial involvement. It includes tables for incentives and responses based on offender actions. Implementation of RIM leads to consistent actions, immediate rewards, positive behav
0 views • 50 slides
Calculating Damages Under the False Claims Act
The False Claims Act allows the government to recover damages from individuals who defraud them. Damages are typically three times the amount of losses caused by the fraudulent act. Various methods can be used to calculate damages, such as determining the difference between what was paid and what wo
0 views • 17 slides
Cutting-edge Proton EDM Storage Ring Experiment Insights
Detailed overview of the Proton EDM Storage Ring Experiment by William Morse, highlighting challenges in neutron EDM sensitivity, magic momentum phenomenon in electric fields, and advancements in proton EDM experiment sensitivity. Explore the critical parameters related to axion physics, CP-violatio
1 views • 16 slides
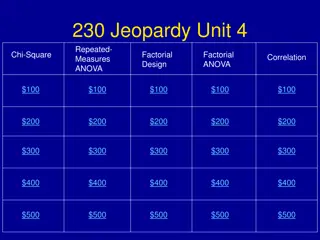
Statistical Analysis Review - An Overview
Explore a diverse range of statistical topics including Chi-Square, Repeated Measures ANOVA, Factorial Design, and Correlation. Learn about scale measurement requirements for Chi-Square, assumptions violation, effect size measures, within-subjects design considerations, and more.
0 views • 51 slides
Regulatory Compliance and Education Insights - August 2022
Explore enforcement, education data, licensee education initiatives, complaints analysis, and violation breakdowns in various industries including liquor, cannabis, tobacco, and vapor for August 2022. Dive into the number of licenses issued, complaints received, education contacts made, and top educ
0 views • 28 slides
Ethics and Physician-Assisted Suicide
Physician-assisted suicide raises complex ethical dilemmas, with arguments from both moral and legal points of view. The case study of Charlie, a homeless man whose organs could save others but would require his death, exemplifies the consequentialist perspective on intentional killing. The debate r
0 views • 12 slides
Technical Foul Violations in Basketball with Descriptions and Images
Explore various technical foul violations in basketball, including holding, misconduct, illegal procedures, delay of game, interference, and more. Each violation is detailed with a description and accompanied by an image for better understanding. Stay informed about the common infractions that lead
1 views • 18 slides
Necessity Test in a Democratic Society: Balancing Public vs Private Interests
The necessity test in a democratic society involves balancing public interests such as security, morality, and environment against private interests. The test determines whether an infringement is necessary and legitimate, or unnecessary and a violation. Different categories like security-related ca
0 views • 36 slides
Exploring CP Violation in Low-Energy QCD: New Physics Perspectives
Investigating CP violation in low-energy QCD, this presentation by Sean Tulin from the University of Michigan delves into the sensitivities of decays to new physics, focusing on CP violation beyond the Standard Model and the potential existence of new weakly-coupled light forces hiding under QCD. Di
0 views • 37 slides
Dress Code Rules for Visitors of Ohio Inmates: Guidelines and Recommendations
Ohio prisons enforce a strict dress code for visitors to maintain order, safety, and security. Failure to comply may result in denied entry. It is advisable to bring spare clothing in case of dress code violation. Visitors must adhere to guidelines regarding undergarments, visible clothing areas, an
0 views • 18 slides
Understanding Sexual Harassment: Key Behaviors and Actions
Sexual harassment encompasses various behaviors such as unwanted touching, name-calling, making inappropriate gestures, and more, which can lead to feelings of discomfort and violation of personal boundaries. It is essential to recognize and address these actions to promote a safe and respectful env
0 views • 11 slides
Challenges and Solutions in Win32 Multithreading
Tackling complex problems in Win32 multithreading involves dealing with locking issues, such as insufficient lock protection and lock order violation. Central to this are the essential locking disciplines that are difficult to enforce in practice. Tools like EspC Concurrency Toolset help analyze and
0 views • 16 slides
Cell Phone Policy Review: Recommendations for Roanoke City Public Schools
Research indicates a high usage of cell phones among teenagers during school hours, prompting the need for policy updates. Suggestions include implementing logical consequences for phone use, such as restrictions during instruction time. Violation consequences range from verbal warnings to involving
0 views • 9 slides
Boil Water Advisories Notification Operating Board Summary
In April 2, 2015, a Boil Water Advisories Notification Operating Board was discussed. The SPU Drinking Water System and a 10-year Regional TCR Summary were also reviewed, highlighting various locations and data trends from 2005 to 2014. Details about TCR Compliance Flow Chart, Timing for Tier 1 Acut
0 views • 6 slides
Design Solutions for Routing under Constraints by Alexander Nadel
Alexander Nadel from Intel presents design solutions for routing under constraints, addressing challenges in formalization, scalability, decision strategies, conflict analysis, and violation resolution in industrial router design. The approach involves problem formalization, SAT encoding, net restar
0 views • 42 slides
Understanding Code Execution Graphs and Superblocks in Software Analysis
Explore the concepts of Static Execution Graphs, Dynamic Execution Graphs, Superblocks, hot-path detection, and memory arithmetic in software analysis. Learn about the grouping of blocks, violation tracking, control dependencies, and code behaviors across time through these graphical representations
0 views • 9 slides
Insights into Mass Hierarchy Determination in Long-Baseline Neutrino Experiments
Combining appearance probabilities of electron and anti-electron neutrinos in long-baseline experiments can help determine the mass hierarchy, with ongoing experiments collecting significant data by 2020. Analyses point to CP violation possibilities, with updates expected in Neutrino2016. The capabi
0 views • 6 slides
Hybrid Tracking of Cross-Thread Dependences in Parallel Programs
Dynamic analysis techniques are explored in this research for error detection and performance enhancement in parallel programs. The study combines pessimistic and optimistic tracking of cross-thread dependences to address issues like data race detection and atomicity violation. The proposed hybrid t
0 views • 68 slides