Understanding IDS/IPS: Enhancing Security with SecurityGen's Advanced Solutions
In the realm of cybersecurity, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play pivotal roles in safeguarding networks against evolving threats. SecurityGen's IDS IPS solutions are designed to monitor network traffic, detect suspicious activities, and prevent potential i
4 views • 1 slides
Understanding the Basic Principles of Distillation
Distillation is a process used to separate components in a liquid mixture based on differences in vapor pressures. This involves techniques like simple, steam, and fractional distillation, as well as understanding binary mixtures, boiling points, vapor pressures, and vapor-liquid equilibria. Raoult'
5 views • 42 slides
Efflorescence and Exsiccation in Chemistry
Efflorescence refers to the process where a substance loses water to form a lower hydrate or becomes anhydrous due to differences in vapor pressures. Hydrates with vapor pressures greater than the atmosphere tend to exhibit efflorescence. The rate of efflorescence increases with temperature. Exsicca
0 views • 103 slides
Physical Vapor Deposition Market
The Global Physical Vapor Deposition Market size is expected to be worth around USD 7 Billion by 2033, from USD 3.2 Billion in 2023, growing at a CAGR of 8.1% during the forecast period from 2024 to 2033.\nClick here for request a sample : \/\/market
1 views • 4 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
Deception Game on Decoy Systems and Honeypots
Deception Game on Decoy Systems and Honeypots explores the use of deception technologies in computer security, focusing on decoy systems like honeypots. It delves into how attackers are lured into fake objects and the monitoring of their behavior to mitigate intrusion. The concept of fake honeypots,
4 views • 25 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
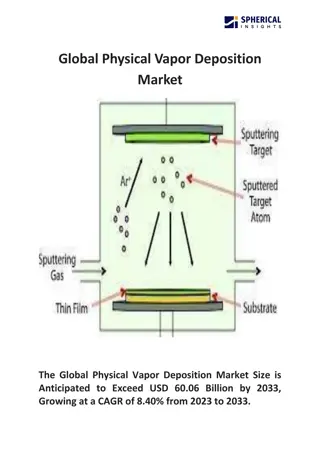
Global Physical Vapor Deposition Market
The Global Physical Vapor Deposition Market Size is Anticipated to Exceed USD 60.06 Billion by 2033, Growing at a CAGR of 8.40% from 2023 to 2033.\n\n
0 views • 8 slides
Colligative Properties in Solutions: Vapor Pressure, Freezing Point Depression, and Osmotic Pressure
Colligative properties such as vapor pressure lowering, freezing point depression, and osmotic pressure are characteristics of solutions that depend on the number of solute particles present. This text explores how these properties are related to the concentration of solute in a solution and how the
0 views • 14 slides
Chemical Vapor Deposition (CVD) Methods for Nanomaterials Characterization
Chemical Vapor Deposition (CVD) is a widely used method in the field of nanomaterial synthesis, particularly for growing nanotubes, nanowires, and nanoparticles. The process involves decomposing a gaseous precursor on a substrate with the help of a catalyst, either predeposited or provided in the ga
3 views • 8 slides
Semantics-Aware Intrusion Detection for Industrial Control Systems by Mer Yksel
Mer Yksel, a PhD candidate at Eindhoven University of Technology, specializes in intrusion detection and data analytics with a focus on industrial control systems. His research covers targeted attacks, threat modeling, protection of ICS networks, and innovative anomaly-based approaches for cybersecu
0 views • 31 slides
Yale Intrusion Alarm System Overview
Yale, a global leader in security solutions, offers the Yale Intrusion Alarm system designed to secure homes and personal belongings. This system features the HSA-6403-PS and HSA-6404-GSM panels with various security elements like sensors, sirens, keypad, and more. Users can easily program and test
0 views • 24 slides
Understanding the Greenhouse Effect and Its Impact
The greenhouse effect is the trapping of the sun's warmth in a planet's lower atmosphere, primarily by greenhouse gases like carbon dioxide and water vapor. These gases absorb and re-emit infrared radiation, which leads to an increase in temperatures. While carbon dioxide and water vapor are signifi
1 views • 13 slides
Overview of Physical Vapor Deposition (PVD) Techniques in Thin Film Deposition
Physical Vapor Deposition (PVD) includes various vacuum techniques for depositing thin films on substrates through physical means. This method involves a dry vacuum process to coat objects with different materials. PVD processes utilize methods like Mechanical, Evaporation, Sputtering, Ion plating,
0 views • 31 slides
Comprehensive Overview of Distributed Intrusion Detection System (DIDS)
Explore the Distributed Intrusion Detection System (DIDS) introduced by Mohammad Hossein Salehi and Kiumars Talaee. Learn about the significance, working, and different types of IDS within DIDS like HIDS, NIDS, and agent-based IDS. Understand the division, information sources, and roles of client-ba
0 views • 25 slides
A Hybrid Intrusion Detection System Approach for IEEE 802.11 Wireless Networks
This research project explores the development of a hybrid intrusion detection system for IEEE 802.11 wireless networks. The study includes research objectives, background information, experimental results, evaluation, and comparison of existing systems, HWIDS design, conclusions, future work, and r
0 views • 73 slides
Effective Strategies for Virtualizing Intrusion Detection Systems
Explore the benefits of virtualizing intrusion detection systems through microservices, addressing the limitations of traditional monolithic IDS setups. Learn how this approach improves scalability, efficiency, and customization for enhanced security measures in network environments.
0 views • 25 slides
Understanding Earth's Atmosphere Composition and Layers
Earth's atmosphere is primarily composed of nitrogen and oxygen, with other gases like argon, CO2, and water vapor making up the remaining percentage. While the levels of nitrogen and oxygen remain constant, variable gases like water vapor fluctuate based on location and time. CO2 levels have been i
0 views • 53 slides
Mastering Intrusion Detection with Snort: A Comprehensive Guide
Dive into the world of network security with Snort, the powerful intrusion detection system. Learn how to analyze network traffic in real time, create custom configuration files, and defend against zero-day attacks. Explore Snort's versatility, portability, and configurability, and discover advanced
0 views • 5 slides
Understanding IDS and IPS for Network Security
Enhance the security of your network with IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) by monitoring traffic, inspecting data packets, and detecting malicious activities based on known signatures. Learn about different types like HIDS and NIDS, their functions, and tools us
0 views • 7 slides
Understanding Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are software pieces that monitor computer systems to detect unauthorized intrusions and misuse, responding by logging activity, notifying authorities, and taking appropriate countermeasures. IDS help address security challenges, aiming to find and fix serious securi
0 views • 40 slides
Root Causes of Intrusion Detection False Negatives: Methodology and Case Study
This study, presented at IEEE MILCOM 2019 by Eric Ficke, Kristin M. Schweitzer, Raymond M. Bateman, and Shouhuai Xu, delves into the analysis of root causes of intrusion detection false negatives. The researchers explore methodologies and present a case study to illustrate their findings.
0 views • 24 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Anomaly-Based Network Intrusion Detection in Cyber Security
An overview of the importance of network intrusion detection, its relevance to anomaly detection and data mining, the concept of anomaly-based network intrusion detection, and the economic impact of cybercrime. The content also touches on different types of computer attacks and references related to
0 views • 32 slides
Understanding Intrusion Detection and Prevention Systems
Learn about the components and implementation options of intrusion detection and prevention systems, as well as the goals and role of an IDPS in network defense. Discover the capabilities of IDPS, such as assessing network traffic, detecting unauthorized access, and responding to threats. Explore an
0 views • 57 slides
Football Field Complex Remedy Project Overview
The project involves remedial measures for the football field complex at Elmira High School, focusing on soil removal, groundwater monitoring, and vapor intrusion prevention. Excavation, disposal of hazardous waste, and construction of institutional controls are key components. Plans for interim rem
0 views • 15 slides
Long-Term Management of Contaminated Soil and Groundwater in Iwilei District, Honolulu
The Iwilei District in Honolulu, Hawaii, spans 315 acres with multiple landowners and responsible parties. It features commercial and industrial use, including bulk fuel terminals, former MGP site, active/inactive petroleum pipelines, and Dole Cannery. The area has been impacted by petroleum-contami
0 views • 25 slides
Comprehensive Guide to Hacking Techniques & Intrusion Detection
Dive into the world of hacking techniques, intrusion detection, and network protocols with expert Ali Al-Shemery. Learn about host discovery, port scanning, packet crafting, and more using tools like Nmap. Explore the importance of network protocols like TCP, UDP, ICMP, and ARP. Discover the art of
0 views • 50 slides
Understanding Radon and Chemical Soil Gas Vapor Intrusion
This presentation at the 2019 International Radon Symposium in Denver, Colorado explores the association between radon, chemical soil gas, and vapor intrusion. It discusses the challenges in testing, analyzing differences, and the need for supplemental measurements like radon to validate models. The
0 views • 19 slides
Understanding Humidity: Measurement, Classification, and Calculation
Humidity is the amount of water vapor in the air, impacting weather conditions and human comfort. It can be classified as absolute humidity and relative humidity, each playing a crucial role in determining atmospheric moisture levels. The calculation of relative humidity involves comparing the vapor
0 views • 24 slides
Alternative Vapor Intrusion Screening Tools for Environmental Investigations
Estimation of subslab attenuation factors for vapor intrusion investigations is crucial in assessing indoor air quality. This study reviews EPA methods, emphasizing the importance of vapor attenuation in screening indoor air for contaminants. Various experts contributed insights, leading to the deve
0 views • 35 slides
Understanding Client-Side Attacks and Intrusion Detection
Explore client-side attacks, their methodology, and defense strategies in Ali Al-Shemery's comprehensive guide. Discover the evolving challenges of network security and the importance of staying ahead with effective intrusion detection techniques.
0 views • 65 slides
Understanding Intrusion Detection and Security Tools
Explore the world of intrusion detection, access control, and security tools through terminology, systems, classifications, and methods. Learn about intrusion detection systems (IDSs), their terminology, alert systems, classification methods like signature-based and statistical anomaly-based approac
0 views • 39 slides
Understanding Environmental Impacts on Housing: Regulating Pollution Exposure Pathways
Explore the regulatory framework for managing pollutant exposure in homes, highlighting the complexity of exposure pathways and the importance of assessing risks based on toxicity and exposure levels. The discussion covers various exposure pathways such as drinking water, air quality, dermal contact
0 views • 14 slides
Comprehensive Guide to Hacking Techniques and Intrusion Detection
This guide by Ali Al-Shemery provides insights into hacking techniques, intrusion detection, fingerprinting, external and internal footprinting, passive reconnaissance, WHOIS lookups, and various online tools for intelligence gathering during penetration tests. It covers identifying customer externa
0 views • 29 slides
Understanding Colligative Properties in Chemistry
Colligative properties in chemistry depend on the amount and type of solute particles added to a sample, as well as the intermolecular forces at play. They include vapor pressure, boiling point elevation, and freezing point depression. Vapor pressure is the pressure exerted by a vapor on its surroun
0 views • 7 slides
Understanding Atmospheric Pressure, Wind Variations, and Humidity in Weather Systems
The atmosphere is composed of various elements like gaseous molecules, water vapor, and dust particles. Key weather variables include atmospheric pressure, temperature, humidity, wind, cloud cover, and precipitation. Atmospheric pressure is influenced by the weight of air above a point, with average
0 views • 17 slides
Tectonic Controls of the Sevier-Laramide Orogeny
The Sevier-Laramide orogeny was influenced by crustal thickening and gravitational extensional collapse. The tectonic model proposed suggests that conductive heating from subduction weakened the crust, leading to compression, uplift, and lateral growth. Deformation persisted from the Cretaceous to t
0 views • 8 slides
Understanding Colligative Properties and Vapor Pressure in Solutions
Colligative properties are solution properties dependent only on solute concentration, not solute identity. The Van't Hoff factor helps in such equations, especially for ionic compounds. Vapor pressure lowering is a key colligative property where a solute decreases vapor pressure. Raoult's Law expla
0 views • 23 slides
Analysis of Tropospheric Intrusion Evolution in START08 Field Campaign
The study presents the analysis of tropospheric intrusion evolution during the START08 Field Campaign using models such as WACCM and GFS. The primary goals include comparing model output with observations, verifying dynamical transport features, and studying the spatial and temporal evolution of mid
0 views • 26 slides