Maximizing Impact: The Role of Rich Snippets in SERPs"User Intent
User intent, also known as search intent, refers to the underlying goal or purpose a user has when performing an online search. It goes beyond the literal interpretation of keywords and focuses on understanding why a person is searching. Recognizing and catering to user intent is crucial for creatin
3 views • 10 slides
Overview of Neck Dissection in Head and Neck Cancer
Neck dissection is a crucial procedure for the prognostic and therapeutic management of head and neck cancers, particularly in cases where cancer has spread to the cervical lymph nodes. This process involves removing all lymph nodes and surrounding structures in the neck region to prevent the spread
8 views • 25 slides
Understanding UML Deployment Diagrams
UML Deployment Diagrams show the execution architecture of software systems, illustrating how software deployment targets are assigned artifacts to nodes. Nodes represent hardware devices or software environments connected through communication paths, while artifacts are concrete elements deployed o
1 views • 22 slides
Understanding Byzantine Fault Tolerance in Distributed Systems
Byzantine fault tolerance is crucial in ensuring the reliability of distributed systems, especially in the presence of malicious nodes. This concept deals with normal faults, crash faults, and the challenging Byzantine faults, where nodes can exhibit deceptive behaviors. The Byzantine Generals Probl
0 views • 29 slides
Understanding Lymph Node Examination in Food Animals
The lymphatic system plays a crucial role in maintaining the body's health by supplying oxygen and nutrients to tissues and removing waste products. Lymph nodes are round masses of lymphoid tissue found along lymphatic vessels, containing lymphocytes within a capsule of connective tissue. Characteri
1 views • 9 slides
Understanding Neck Anatomy: Triangles, Glands, and Lymph Nodes
Explore the intricate anatomy of the neck, including the various triangles, thyroid and parotid gland structures, as well as cervical lymph nodes. Delve into the essentials of neck mass evaluation, differential diagnosis, and management strategies. Enhance your knowledge of head and neck surgery thr
0 views • 53 slides
Exploring Graph-Based Data Science: Opportunities, Challenges, and Techniques
Graph-based data science offers a powerful approach to analyzing data by leveraging graph structures. This involves using graph representation, analysis algorithms, ML/AI techniques, kernels, embeddings, and neural networks. Real-world examples show the utility of data graphs in various domains like
3 views • 37 slides
Understanding Mobile Computing and TCP/IP Protocol Suite
Mobile computing is crucial for continuous internet connectivity regardless of physical location. The TCP/IP protocol suite, consisting of Transmission Control Protocol (TCP) and Internet Protocol (IP), forms the backbone of internet infrastructure. IP addressing and mobility challenges are addresse
1 views • 51 slides
Role of Lymphadenectomy in Genital Malignancies
Pelvic and paraaortic lymph node evaluation is crucial in the surgical staging of gynecological malignancies. The goals of lymph node dissection are to determine disease extent and guide further treatment. Pelvic lymph nodes include common iliac, external and internal iliac, obturator, sacral, and p
0 views • 16 slides
Understanding Redis Cluster Distribution Approach
Redis Cluster offers a pragmatic approach to distribution, connecting all nodes directly with a service channel. Each node communicates using a binary protocol, optimized for bandwidth and speed. Nodes do not proxy queries, and communication involves messages like PING, PONG, and Gossip. Hash slot k
0 views • 17 slides
Understanding Doubly Linked Lists in C Programming
A doubly linked list in C comprises nodes with pointers to the next and previous nodes. Managing two sets of pointers can be complex, but adds flexibility for adding and removing nodes dynamically. This post explores the structure, implementation, and examples of doubly linked lists in C.
0 views • 13 slides
Economic Models of Consensus on Distributed Ledgers in Blockchain Technology
This study delves into Byzantine Fault Tolerance (BFT) protocols in the realm of distributed ledgers, exploring the complexities of achieving consensus in trusted adversarial environments. The research examines the classic problem in computer science where distributed nodes communicate to reach agre
0 views • 34 slides
Byzantine Failures and CAP Theorem Overview
Byzantine failures refer to arbitrary patterns of failures where nodes exhibit inconsistent behavior. This lecture discusses Byzantine agreement and the challenges in reaching consensus with faulty nodes. It explores the minimum number of processes needed for consensus and extends the concepts to ge
1 views • 32 slides
Distributed Consensus Models in Blockchain Networks
Economic and technical aspects of Byzantine Fault Tolerance (BFT) protocols for achieving consensus in distributed ledger systems are explored. The discussion delves into the challenges of maintaining trust in adversarial environments and the strategies employed by non-Byzantine nodes to mitigate un
0 views • 34 slides
Understanding the Modern Generic LinkedList Collection Class
Dive into the modern implementation of the Generic LinkedList Collection class, which allows you to efficiently manage data in a chain of nodes. Learn about creating, adding, removing, and iterating through nodes, offering a versatile way to handle data without the need for manual implementation. Ex
1 views • 28 slides
Expression Tree Construction: Building Fully Parenthesized Expression Trees
In the process of building expression trees, nodes are inserted based on operators and operands, creating a fully parenthesized expression. The construction involves parsing the expression, inserting new nodes as tokens are examined, and linking nodes accordingly. By following the steps for handling
0 views • 17 slides
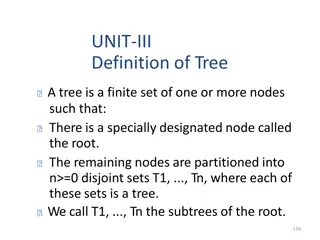
Understanding Trees and Binary Trees in Data Structures
A tree in data structures is a finite set of nodes with a designated root and subtrees, including internal nodes and leaf nodes. Terminology like root, parent nodes, leaves, and levels are explained, along with concepts of height and degree of a tree. Additionally, binary trees are introduced as a s
1 views • 94 slides
Understanding Interconnection Networks Topology
Exploring the topology of interconnection networks helps determine the arrangement of channels and nodes, impacting network cost, performance, latency, energy consumption, and complexity of implementation. Abstract metrics such as degree, hop count, and network diameter play crucial roles in evaluat
1 views • 56 slides
Understanding Centrality Measures in Peer-to-Peer and Social Networks
Centrality measures in networks quantify the importance of nodes based on their influence, accessibility, and role as connectors. Important centrality measures include Degree centrality (based on the number of connections), Closeness centrality (based on short paths to other nodes), and Betweenness
0 views • 27 slides
MRI Assessment Findings for Colon and Rectal Cancer
Baseline MRI assessment findings for colon and rectal cancer staging include detailed descriptions of the primary tumor, its borders, extent, muscularis propria involvement, lymph nodes assessment, vascular deposits, circumferential resection margin, peritoneal deposits, pelvic sidewall lymph nodes
0 views • 7 slides
Understanding the Lymphatic System: Functions and Components
The lymphatic system is a vital network of organs, nodes, ducts, and vessels that maintains fluid balance, aids in immunity, and removes waste from tissues. It works in conjunction with the circulatory system to deliver essential nutrients and oxygen to cells. Key components include the thoracic duc
0 views • 14 slides
Introduction to Linked Lists: An Overview of LinkedIntList
This lesson delves into Linked Lists by introducing the LinkedIntList and its implementation with a chain of linked nodes. Understanding the concept of LinkedIntList, its methods like add, get, indexOf, remove, size, and toString, as well as how it maintains references to its front, is crucial. Thro
0 views • 44 slides
Accelerated Hypergraph Coarsening Procedure on GPU
An accelerated procedure for hypergraph coarsening on the GPU, presented by Lin Cheng, Hyunsu Cho, and Peter Yoon from Trinity College, Hartford, CT, USA. The research covers hypergraph coarsening, implementation challenges, runtime task planning, hypergraph nodes, hypergraph partitioning, image cla
0 views • 38 slides
Exact Byzantine Consensus on Undirected Graphs: Local Broadcast Model
This research focuses on achieving exact Byzantine consensus on undirected graphs under the local broadcast model, where communication is synchronous with known underlying graphs. The model reduces the power of Byzantine nodes and imposes connectivity requirements. The algorithm involves flooding va
0 views • 7 slides
Understanding Overfitting in Data Mining Models
Overfitting is a common issue in data mining models where the model performs exceptionally well on the training data but fails to generalize to new data. This content discusses how overfitting can occur, its impact on model performance, and strategies to mitigate it. Through examples and visualizati
0 views • 30 slides
Understanding Sentinel Lymph Nodes in Endometrial & Vulval Cancer
Exploration of sentinel lymph node (SLN) practices across SWAGGER preliminary data and guidelines for endometrial cancer, featuring insights from Exeter, Cheltenham, and Bristol cases. Additionally, BGCS guidelines for sentinel nodes in vulval cancer are discussed, emphasizing techniques for detecti
0 views • 23 slides
Understanding the Lymphatic System in Cattle: Nodes, Circulation, and Function
The lymphatic system in cattle plays a crucial role in maintaining overall health. It consists of lymph nodes located in various regions of the body such as the head, neck, abdomen, and hind limbs. These lymph nodes produce lymphocytes and help in filtering foreign bodies. Lymph fluid, similar to bl
0 views • 39 slides
Understanding Network Metrics Through Centrality Analysis
This presentation introduces network metrics as tools to describe network characteristics and answer important questions. Using centrality metrics as an example, participants learn how to identify the most important nodes in a network based on different criteria such as degree centrality and closene
0 views • 15 slides
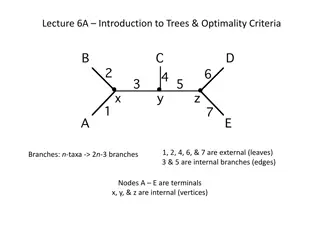
Understanding Trees and Optimality Criteria
In this lecture, you will delve into the world of trees and optimality criteria. Explore concepts like external and internal branches, terminal nodes, and vertices. Discover the Newick format for tree representation, the rooting of trees, and free rotations around nodes. Dive into the growth of tree
0 views • 15 slides
User Interface Design Principles in Human-Computer Interaction
User interface design principles are crucial in Human-Computer Interaction. This content highlights key principles such as aesthetics, anticipation, autonomy, and color consideration for users with color blindness. It emphasizes the importance of user testing, user autonomy, and providing essential
0 views • 24 slides
Understanding Standing Waves in Physics
Standing waves in physics are periodic waves that result from the interference of reflected and inverted waves, creating nodes and antinodes along a medium. These standing wave patterns can be observed in vibrating strings, such as guitar strings, where specific frequencies produce distinct harmonic
0 views • 29 slides
Understanding Trees: Introduction and Definitions
Moving on from lists, trees represent a collection of elements where each node may have zero or more successors, known as children. The tree structure includes terminology such as branches, siblings, leaves, ancestors, and descendants. Nodes in a tree have attributes like depth and height, with bina
0 views • 8 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Virtual Network Mapping: A Graph Pattern Matching Approach
Virtual Network Mapping (VNM) involves deploying virtual network requests in data center networks in response to real-time demands. It facilitates the deployment of virtual networks on physical machines by mapping virtual nodes and links onto substrate nodes and paths, ensuring constraints are met.
0 views • 15 slides
Understanding Graph Databases and Neo4j
Graph databases offer a flexible way to manage data by representing relationships between nodes. Neo4j is a popular graph database system that uses Cypher for querying. This guide provides insights into graph database concepts, advantages, and getting started with Neo4j, including creating nodes and
0 views • 39 slides
Understanding Return Dispositions and Remote Returns Process in Warehousing
Explore the concept of return dispositions like NRFI, RFI, UNS, and UNSNWT in warehouse management, along with insights into Remote Returns Process (RRP) nodes and Non-RRP nodes. Learn about Regular Returns, LPNs, and the choice between consolidating returns with LPNs for efficiency. Understand the
0 views • 11 slides
Deployment Viewpoint for MOIMS Services in SEA Reference Architecture
Identification of physical nodes and their connections, functional deployments showcasing interoperable interfaces between nodes, and classification of space and earth user nodes in the context of MOIMS services for the SEA reference architecture.
0 views • 17 slides
Enhancing Energy Efficiency with Personalized HVAC Control System
Personalized HVAC Control System aims to optimize energy usage by sensing human comfort parameters, implementing control algorithms, and coordinating room nodes effectively. Motivated by high energy consumption in buildings, the system addresses user behavior towards thermostat settings to reduce en
0 views • 15 slides
Administrator Deletes User - User Management System Storyboard
An administrator navigates through a user list, selects a user for deletion, confirms the action, and successfully removes the user from the system. The process involves interacting with user details, confirming the deletion, and updating the user list accordingly in a structured manner.
0 views • 4 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides