Maximizing Impact: The Role of Rich Snippets in SERPs"User Intent
User intent, also known as search intent, refers to the underlying goal or purpose a user has when performing an online search. It goes beyond the literal interpretation of keywords and focuses on understanding why a person is searching. Recognizing and catering to user intent is crucial for creatin
3 views • 10 slides
Troubleshooting QuickBooks Aborting in Multi-user Mode_ Causes and Solutions
Encountering QuickBooks aborting in multi-user mode can disrupt workflow and cause frustration. Our comprehensive guide delves into the causes and solutions for this issue. From network connectivity issues to corrupted company files, we identify potential culprits and provide step-by-step troublesho
8 views • 3 slides
Improving Multi-Link Power Management Efficiency in IEEE 802.11 Networks
The document discusses challenges with per-link power mode changes in multi-link scenarios in IEEE 802.11 networks, proposing a solution for more efficient power management. It addresses issues such as latency and inefficiencies in signaling for power mode changes, introducing scheduled multi-link p
6 views • 9 slides
Troubleshooting QuickBooks Aborting in Multi-user Mode
This guide will Help you to resolve QuickBooks Aborting in Multi-user Mode error.
2 views • 4 slides
QuickBooks Multi-User Mode Not Working
QuickBooks in multi-user mode not working can cause significant disruptions in business operations. This issue prevents multiple users from accessing the company file simultaneously, leading to delays and reduced productivity. Common causes include network setup problems, firewall restrictions, or c
3 views • 4 slides
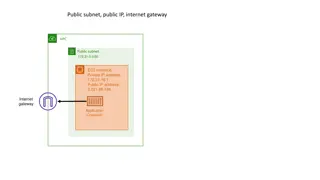
Networking Modes in AWS VPC Environments
Explore different networking modes such as Bridge mode with static mapping, Bridge mode with dynamic mapping, and AWS VPC networking mode in an AWS VPC environment with various configurations and scenarios.
0 views • 18 slides
Understanding Mode-S Radar Operations and Identifiers
This simplified explanation delves into the fundamental principles of radar operations, focusing on Primary and Secondary radar systems, including Mode A/C and Mode S functionalities. It covers radar interrogation, replies, and the significance of radar identifiers (II and SI codes) in managing over
0 views • 19 slides
Parallel Implementation of Multivariate Empirical Mode Decomposition on GPU
Empirical Mode Decomposition (EMD) is a signal processing technique used for separating different oscillation modes in a time series signal. This paper explores the parallel implementation of Multivariate Empirical Mode Decomposition (MEMD) on GPU, discussing numerical steps, implementation details,
1 views • 15 slides
Understanding System Management Mode (SMM) in x86 Processors
System Management Mode (SMM) is a highly privileged mode in x86 processors that provides an isolated environment for critical system operations like power management and hardware control. When the processor enters SMM, it suspends all other tasks and runs proprietary OEM code. Protecting SMM is cruc
1 views • 26 slides
Patch Bundle Mode Walkthrough for Device Configuration
Explore the Patch Bundle Mode walkthrough consisting of flowcharts and pseudo code examples for controlling a device's patch mode, downloading configurations, and changing device modes. The content provides a detailed guide on using commands to initiate patch burst mode, specify I2C addresses, and t
0 views • 4 slides
Implementing Alert Messages and User Input Handling in Java
This tutorial guides you through creating alert messages, handling user input, defining functions, calling functions from the `onCreate` method, and creating an XML file for user data entry validation in Java. Learn how to display alerts for empty user credentials and process user actions accordingl
1 views • 6 slides
Unsupervised Clickstream Clustering for User Behavior Analysis
Understanding user behavior in online services is crucial for businesses. This research focuses on utilizing clickstream data to identify natural clusters of user behavior and extract meaningful insights at scale. By analyzing detailed user logs, the study aims to reveal hidden patterns in user inte
0 views • 19 slides
Efficient User Management System for Health Facilities
Record and manage user details effectively with the new Version 2.0 User Management feature. RNTCP has now registered over 35,000 PHIs, 140,000 Private Health Facilities, 15,000 Private Labs, 31,000 Private Chemists, across 700 Districts and 8,000 TUs in Nikshay. Enhance operations by editing TU pro
0 views • 26 slides
Understanding the Essential Parts of a Camera
The camera consists of crucial components like the body, lens assembly, shutter release button, and mode dial. The body holds everything together, while the lens assembly controls focusing and zoom. The shutter release button triggers image capture, and the mode dial allows you to select different s
0 views • 18 slides
Understanding Agile User Stories in Software Development
Agile user stories play a crucial role in software development by providing short descriptions of features desired by customers in a language they understand. This method allows for agile planning, efficient documentation, and effective communication between development teams and clients. Extracting
0 views • 30 slides
PDSCH Demodulation Parameters & Requirements Discussion
This document covers the discussion on PDSCH demodulation parameters and requirements for UE demodulation and CSI reporting in FR2 DL 256QAM, specifically focusing on static channel mode, TDL-D channel mode, and TDL-A channel mode. The document also explores rank options, channel bandwidth, PRB allo
0 views • 9 slides
Understanding CMRR in Differential Amplifiers
Differential input amplifiers, including operational, instrumentation, and difference amplifiers, play a crucial role in amplifying differential signals while rejecting common-mode noise. The Common-Mode Rejection Ratio (CMRR) is a key parameter in these amplifiers, indicating their ability to suppr
0 views • 48 slides
Understanding Transit Modes: A Comparative Analysis by Watkins, LaMondia, and Brakewood
This study delves into defining transit modes, exploring different families of transit modes, and comparing mode selection in the US. The materials developed by K. Watkins, J. LaMondia, and C. Brakewood provide insights into transit mode characteristics like right-of-way systems, technology types, a
0 views • 43 slides
Understanding Input and Output Limitations in Op Amps
Explore the various input and output limitations in TI Precision Labs Op Amps as presented by Ian Williams and prepared by Art Kay and Ian Williams. Delve into common mode voltage, voltage swing, data sheet parameters translation, input and output stages, examples of common mode voltage, and potenti
0 views • 15 slides
IEEE 802.11-20/0760r0 Multi-Link Power Save Mode Extension
This document discusses the extension of dynamic SM power save mode to multi-link scenarios in IEEE 802.11-20/0760r0. By allowing non-AP STAs to control power consumption efficiently in multi-link operations, benefits such as higher peak throughput and increased reliability can be achieved. The dyna
0 views • 9 slides
Understanding User Mode, Kernel Mode, Interrupts, and System Calls in Computer Architecture
In modern computers following Von Newman Architecture, programs and data are stored in RAM. The CPU, RAM, ROM, and devices communicate via address and data buses. The system operates in both kernel and user modes, where kernel mode allows full system control, while user mode restricts access for sec
0 views • 29 slides
Understanding Real-time Debug Techniques for Embedded Development
Real-time debugging in embedded systems involves different modes like stop mode and real-time mode, each offering unique capabilities for accessing memory, registers, and handling interrupts. This technique allows developers to examine and modify memory contents while the processor is running, enabl
0 views • 32 slides
IEEE 802.11-24/0797r0 Operating Mode Request
This document proposes an Operating Mode Request mechanism for STAs within the IEEE 802.11 standard. It allows a STA to request another STA to change its operating mode, such as bandwidth and number of spatial streams. The proposal outlines the reasons for making such requests and the acceptance/den
0 views • 10 slides
Enhancing Power Efficiency in IEEE 802.11 Multi-Link SM Power Save Mode
The document discusses how Multi-Link Operation (MLO) in IEEE 802.11be can improve throughput and reduce latency but may increase power consumption for non-AP devices. It introduces the concept of Multi-Link SM Power Save mode to optimize power usage by activating multiple links only when necessary,
0 views • 10 slides
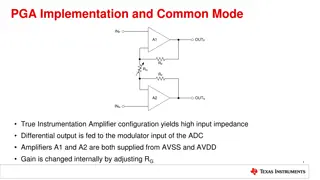
Understanding PGA Implementation and Common Mode Voltage in Instrumentation Amplifiers
The PGA implementation in instrumentation amplifiers allows for high input impedance and precise gain adjustment through internal settings. Common mode voltage plays a crucial role in ensuring proper amplifier operation, with limitations and potential violations impacting signal integrity. Examples
0 views • 5 slides
User Interface Design Principles in Human-Computer Interaction
User interface design principles are crucial in Human-Computer Interaction. This content highlights key principles such as aesthetics, anticipation, autonomy, and color consideration for users with color blindness. It emphasizes the importance of user testing, user autonomy, and providing essential
0 views • 24 slides
3GPP TSG-RAN4 Meeting #97e Summary
During the 3GPP TSG-RAN4 Meeting #97e, discussions on Multi-RAT Dual Connectivity and Carrier Aggregation enhancements were held. A Work Item (WF) focusing on Idle mode Carrier Aggregation (CA) measurement Radio Resource Management (RRM) requirements was addressed. The meeting included topics such a
0 views • 17 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Comparative Analysis of MHD-Kinetic Codes for Large Aspect Ratio Equilibrium
The study presents a benchmark comparison of HMGC, HYMAGYC, and MEGA codes focusing on their hybrid MHD-kinetic nature in large aspect ratio equilibriums. The analysis explores the relative stability of two types of EPMs at varying nH values, concluding with results on mode frequencies and growth ra
0 views • 9 slides
Exploring Melodic Features of Mode in Polyphony
Dive into a workshop on digital musicology at McGill University, where experts such as Claire Arthur, Julie Cumming, and Peter Schubert discuss assessing melodic features of mode in polyphony. The event, titled "À La Mode," took place on April 27th, 2018, under the CIRMMT Workshop.
0 views • 22 slides
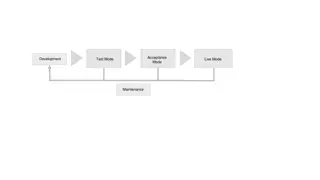
Development Lifecycle Overview - Roles, Systems, and Revisions
Explore the comprehensive development lifecycle encompassing acceptance mode, test mode, live mode, and maintenance. Dive into roles and organization structures, application versions, project resources, connectors, and system configurations. Witness the evolution of live and acceptance versions, alo
0 views • 4 slides
Understanding Gated Mode Systems in Particle Detectors
Delve into the intricate details of Gated Mode systems, focusing on aspects such as theory, sensitivity areas, switcher principles, and readout processes without compromising data integrity. Explore the challenges and strategies involved in implementing Gated Mode technology effectively in DEPFET de
0 views • 26 slides
Understanding Immediate Mode GUI: Theory, Implementation, and Example
Graphical User Interface (GUI) is a key element in software development, facilitating user interaction and displaying information. This content delves into GUI theory, discussing its architecture, implementation methods, object-oriented approach, and the concept of immediate mode GUI. It also showca
1 views • 21 slides
IEEE 802.11-18/0677r0: Speak-Only-When-Spoken-To Mode in Wireless Networking
This document discusses the implementation of a speak-only-when-spoken-to mode in IEEE 802.11-18/0677r0 for managing various devices within wireless networks. It highlights the benefits of this mode for maintaining throughput efficiency and coexistence, especially in scenarios involving 11b-only dev
0 views • 7 slides
Administrator Deletes User - User Management System Storyboard
An administrator navigates through a user list, selects a user for deletion, confirms the action, and successfully removes the user from the system. The process involves interacting with user details, confirming the deletion, and updating the user list accordingly in a structured manner.
0 views • 4 slides
Understanding mean, median, and mode in statistics
In statistics, the mean represents the average value, the median is the middle value that divides a dataset into two halves, and the mode is the most frequent value. This guide explains how to calculate these statistical measures and provides examples. Additionally, it demonstrates how to estimate t
0 views • 11 slides
Simplifying IMMW Adoption through DL-Only Mode in mmWave Technology
Promoting the adoption of Integrated Multi-band and Multi-Wavelength (IMMW) technology through the implementation of a DL-only mode in mmWave devices. This approach addresses challenges such as coverage mismatch, power consumption, and cost, potentially increasing the number of IMMW user devices and
0 views • 12 slides
Understanding Servo Torque Mode Training by Jim
Dive into the world of servo torque mode training with Jim as your guide. Explore the principles, applications, and settings involved in torque control mode for various machines like printing presses and winding machines. Learn about internal and analog torque command inputs, torque limits, and more
0 views • 15 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides
Evolution of Vertica - Eon Mode Vertica Overview
Explore the advancement of Vertica from Enterprise Mode to AWS Eon Mode, offering fast, scalable, and open architecture SQL databases. Learn about the simplified provisioning and data loading process in Eon Mode Vertica using EC2 instances with storage and an S3 bucket.
0 views • 17 slides